D
Deleted member 178
Thread author
Hi,
Ok, if you bought a copy of Webroot SA, you already knows that you can run it alongside another antivirus/suite without conflicts; it is called a "companion AV"
But for that , we need to tweak a bit both of them, so there is my quick guide:
The other Antivirus
depending the product, the settings are different but all of them have the same kind of options:
Exclusions/Whitelist
important step, you must exclude WRSA.exe from the protection of your other AV, so WSA will not trigger a monitoring from it, so less resources used. You do it generally in these fields:
1- Antivirus scans (exclude WRSA.exe)
2- Real-time scans/modules (exclude WRSA.exe)
3- HIPS/Behavior Blocker/Sandbox : add/trust/allow WRSA.exe
4- Firewall (add/trust/allow WRSA.exe, Webroot is cloud, means it need to connect to internet)
Webroot SA
Webroot SA is very simple to use, so you don't have to be a super-geek to set it up, so we will do it to perform as a companion AV.
Now we open Webroot's GUI and go to settings:
A- Settings:
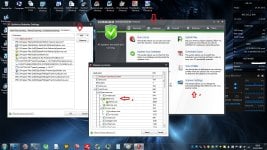
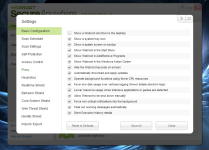
1- Basic configuration
[attachment=2030]
we will check if these boxes are ticked:
- operate background functions using fewer CPU resources (your main AV may be greedy on resources so we will operate WSA with minimum consumption)
- Favor Low disk usage over verbose logging (i like to save the life duration of my HDD )
)
- Lower resource usage when intensive applications or games are detected (no need to explain why )
)
- Force non-critical notifications into the background (to avoid useless popups)
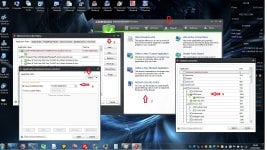
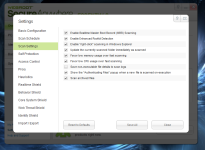
2- Scan Settings
[attachment=2031]
we can tick all boxes. some of them depend of your personal taste.
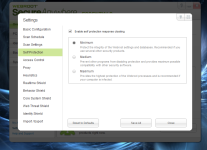
3- Self protection
[attachment=2032]
the important part : Enable self protection response cloacking -> minimum (it is explained why there)
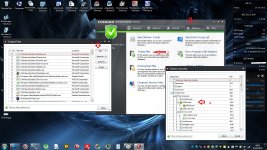
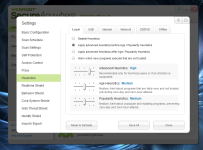
4- Heuristics
[attachment=2033]
I selected High for all "Advanced Heuristics" , personal choice, it may generates more False positives but you can let it as Medium. this field is really depending of your taste, feel free to do as you wish
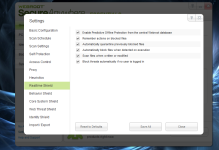
5- Real-time Shield
[attachment=2034]
you can untick scan files when written or modified, WSA will react only on executed files.
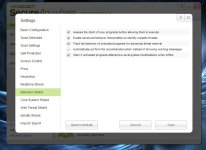
6- Behavior Shield
[attachment=2035]
tick all except automatically perform the recommended action... ( i like to know what is authorized on my system)
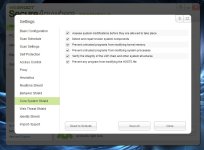
7- Core System Shield
[attachment=2036]
tick all, if your other product have a feature that modify the HOSTs file, you can untick, "prevent any program from modifying the Host file" but i suggest you to tick it after the modification is done.
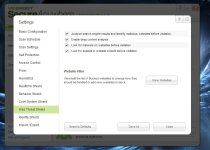
8- Webshield
[attachment=2037]
Tick all
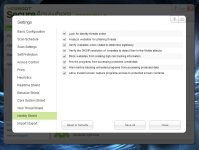
9- Identity Shields
[attachment=2038]
Tick all
Click "Save All" , WE ARE DONE for the settings tab but not finished the setup ^^
but not finished the setup ^^
B- PC Security
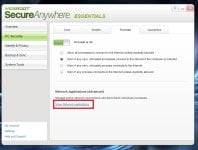
1- Firewall
[attachment=2039]
enable, it ! some says hey i have a firewall already ! it will conflict !
In fact not, Webroot is not a "traditionnal firewall" , it works differently, it is more a "malware firewall" or outbound connection monitor, it functions as an "additional firewall layer" (if i can say that)
note: Win8 users will not have the possibility to choose a setting.
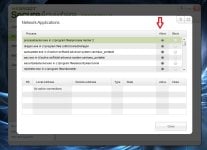
- network Application -> view network application
[attachment=2040]
check that your other product is allowed.
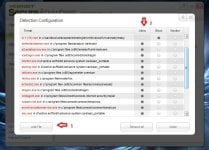
2- Quarantine
- Detection configuration -> configure
[attachment=2041]
yes it is weird but it is one of the exclusions place...
add every executable of your other security product (example for Comodo IS : cfp.exe, cmdagent.exe, cavscan.exe,etc...)
C- System Tool
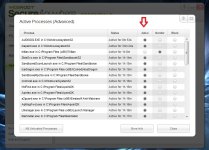
1- Control Active Processes -> Start
[attachment=2042]
check that all exe of your other product are "allowed" (if monitored their efficiency may be reduced)
WE ARE FINISHED.
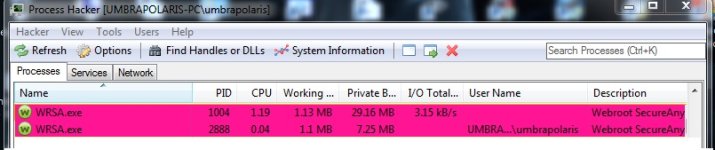
normally Webroot SA should run now with a low CPU & RAM (less than 10mb Working Set on idle.
[attachment=2043]
Edit: i may add other changes if the case is needed.
Edit 2 : procedure to add Webroot to exclusions of various security products will be added by others members and me on the following posts , thanks
note: Thanks to Jim (Webroot Community Leader) to gave me some feedbacks and corrections to the guide.
Ok, if you bought a copy of Webroot SA, you already knows that you can run it alongside another antivirus/suite without conflicts; it is called a "companion AV"
But for that , we need to tweak a bit both of them, so there is my quick guide:
The other Antivirus
depending the product, the settings are different but all of them have the same kind of options:
Exclusions/Whitelist
important step, you must exclude WRSA.exe from the protection of your other AV, so WSA will not trigger a monitoring from it, so less resources used. You do it generally in these fields:
1- Antivirus scans (exclude WRSA.exe)
2- Real-time scans/modules (exclude WRSA.exe)
3- HIPS/Behavior Blocker/Sandbox : add/trust/allow WRSA.exe
4- Firewall (add/trust/allow WRSA.exe, Webroot is cloud, means it need to connect to internet)
Webroot SA
Webroot SA is very simple to use, so you don't have to be a super-geek to set it up, so we will do it to perform as a companion AV.
Now we open Webroot's GUI and go to settings:
A- Settings:
1- Basic configuration
[attachment=2030]
we will check if these boxes are ticked:
- operate background functions using fewer CPU resources (your main AV may be greedy on resources so we will operate WSA with minimum consumption)
- Favor Low disk usage over verbose logging (i like to save the life duration of my HDD
- Lower resource usage when intensive applications or games are detected (no need to explain why
- Force non-critical notifications into the background (to avoid useless popups)
2- Scan Settings
[attachment=2031]
we can tick all boxes. some of them depend of your personal taste.
3- Self protection
[attachment=2032]
the important part : Enable self protection response cloacking -> minimum (it is explained why there)
4- Heuristics
[attachment=2033]
I selected High for all "Advanced Heuristics" , personal choice, it may generates more False positives but you can let it as Medium. this field is really depending of your taste, feel free to do as you wish
5- Real-time Shield
[attachment=2034]
you can untick scan files when written or modified, WSA will react only on executed files.
6- Behavior Shield
[attachment=2035]
tick all except automatically perform the recommended action... ( i like to know what is authorized on my system)
7- Core System Shield
[attachment=2036]
tick all, if your other product have a feature that modify the HOSTs file, you can untick, "prevent any program from modifying the Host file" but i suggest you to tick it after the modification is done.
8- Webshield
[attachment=2037]
Tick all
9- Identity Shields
[attachment=2038]
Tick all
Click "Save All" , WE ARE DONE for the settings tab
B- PC Security
1- Firewall
[attachment=2039]
enable, it ! some says hey i have a firewall already ! it will conflict !
In fact not, Webroot is not a "traditionnal firewall" , it works differently, it is more a "malware firewall" or outbound connection monitor, it functions as an "additional firewall layer" (if i can say that)
note: Win8 users will not have the possibility to choose a setting.
- network Application -> view network application
[attachment=2040]
check that your other product is allowed.
2- Quarantine
- Detection configuration -> configure
[attachment=2041]
yes it is weird but it is one of the exclusions place...
add every executable of your other security product (example for Comodo IS : cfp.exe, cmdagent.exe, cavscan.exe,etc...)
Jim (Webroot Community Leader said:Quarantine section is not necessary. Webroot maintains a global listing of good files in addition to bad ones and unknown ones. Third-party antivirus software is included in this list. It takes less time for WSA to ask the cloud if the software in question is good, bad, or unknown than it does for you to manually tell it to flag all of those files as good. Additionally, the third-party software is probably going to update a lot, being that it's antivirus software (most-likely old-school definitions based stuff too). When it updates, those files change, and for all real purposes they are new files. The original whitelisting action you would have taken would have whitelisted a certain set of files locally, but it wouldn't account for updates. However, our cloud-based whitelisting does that automatically, which is why you notice no ill effects.
C- System Tool
1- Control Active Processes -> Start
[attachment=2042]
check that all exe of your other product are "allowed" (if monitored their efficiency may be reduced)
Jim (Webroot Community Leader said:On Step C, I'd caution that you want to know for sure what you're telling it to Allow. If you see programs you use all the time in that list and you are positive they are not threats, you can toss them into the Allow column. However, there are two things to consider about this:
1. Don't just go by the name. Some threats will name themselves something convincing in an effort to evade manual detection (think "windows.exe" or even real file names like "smss.exe").
2. Uncertainty should raise suspicion. Obscure names can be bad stuff too. If you see something like aphwef876.exe (I just hit random keys there like a polymorphic infection would rename itself), and it's sitting in a Monitor or Block status, there's a good chance that's an infection.
While some users are tech-savvy enough to be able to investigate entries that are unjustifiably set to Monitor and decide to Allow them, other users who are less tech-savvy would be wise to either A) leave those in Monitor status in case they are later flagged as Bad and need to be automatically rolled back to before WSA first saw them or B) contact Support to determine if such movement to Allow is justified. B is preferred, because any time you ask Support about a file that we are currently marking as Unknown, it prompts us to look at that file right away and determine it. That doesn't just help you - that helps everyone with WSA installed, which is pretty cool when you think about it.
WE ARE FINISHED.
normally Webroot SA should run now with a low CPU & RAM (less than 10mb Working Set on idle.
[attachment=2043]
Edit: i may add other changes if the case is needed.
Edit 2 : procedure to add Webroot to exclusions of various security products will be added by others members and me on the following posts , thanks
note: Thanks to Jim (Webroot Community Leader) to gave me some feedbacks and corrections to the guide.
Attachments
-
 basic.png161.5 KB · Views: 1,142
basic.png161.5 KB · Views: 1,142 -
 scan settings.png152.6 KB · Views: 987
scan settings.png152.6 KB · Views: 987 -
 self protection.png173.6 KB · Views: 1,019
self protection.png173.6 KB · Views: 1,019 -
 Heuristic.png168.5 KB · Views: 967
Heuristic.png168.5 KB · Views: 967 -
 RT shield.png165.2 KB · Views: 1,135
RT shield.png165.2 KB · Views: 1,135 -
 Behavior Shield.jpg89.7 KB · Views: 1,018
Behavior Shield.jpg89.7 KB · Views: 1,018 -
 Core Shield.jpg91.6 KB · Views: 941
Core Shield.jpg91.6 KB · Views: 941 -
 Web Shield.jpg92.3 KB · Views: 976
Web Shield.jpg92.3 KB · Views: 976 -
 Identity Shield.jpg96.8 KB · Views: 939
Identity Shield.jpg96.8 KB · Views: 939 -
 Firewall.jpg91.3 KB · Views: 951
Firewall.jpg91.3 KB · Views: 951 -
 network apps.jpg93.4 KB · Views: 1,034
network apps.jpg93.4 KB · Views: 1,034 -
 detection.jpg138.5 KB · Views: 949
detection.jpg138.5 KB · Views: 949 -
 Processes.jpg136.9 KB · Views: 883
Processes.jpg136.9 KB · Views: 883 -
 wsa.jpg59 KB · Views: 902
wsa.jpg59 KB · Views: 902