- Jul 28, 2016
- 950
Hey FrFc1908, I'm in charge of the operation of Huorong Internet Security. I noticed that you're encountering the issue constantly when trying to perform scans with HIS. Sorry about noticing this thread this late.
Would you mind providing the following information for us in order to try locating the issue please?
1. The OS version information.
2. The basic environment information, like CPU, memory, etc.
3. Does the environment has any 3rd party security software installed alongside with Huorong?
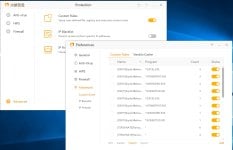
4. Check if there's any dump files in Huorong components folder (should be %programfiles%\Huorong\Sysdiag\bin\*.dmp for a default installation).
5. The screenshot when the hang occurs.
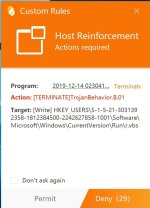
6. Notice if Hipsdaemon.exe still alive when the hang occurs. If yes, please checkout it's CPU usage (this will give us some clue that the scan is actually running or not).
Look forward to hearing from you.
Thanks for you feedback. Have a good one.
Hi thanks tot your answer , but I am sorry to say that I do not use huorong anymore , I now have qihoo 360 ts running. But when I had huorong running I did run of all gsidw wisevector. I have the latest win 10 x64 , Intel core i5 4th gen , 4gb ram and Intel pro ssd