Hi Dan,
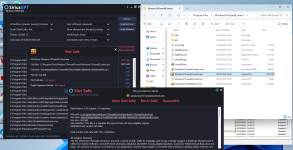
I ran a scan using SiriusGPT on my virtual machine, and it flagged two applications as unsafe. The reason given was the absence of a digital signature or publisher information which is similar to how Cyberlock WhiteCloud works.
Applications Initially Marked as Unsafe:
1. SpyTheSpy.exe
To test whether this change was stored in memory, I shut down SiriusGPT and performed another scan. The applications were still running but were not marked as unsafe—suggesting the safe status was retained.
My Question:
Where is the data stored for applications that are manually marked as safe?
Is it saved somewhere other than the local whitelis.dbt?
It would be helpful to view and manage these entries similar to how we use Cyberlock which shows a list of trusted applications.
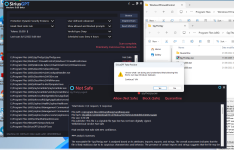
I ran a scan using SiriusGPT on my virtual machine, and it flagged two applications as unsafe. The reason given was the absence of a digital signature or publisher information which is similar to how Cyberlock WhiteCloud works.
Applications Initially Marked as Unsafe:
1. SpyTheSpy.exe
- Location: C:\Program Files (x86)\SpyTheSpy\
- Purpose: Runs in the background to monitor new file installations. Both the installer and executable are safe.
- Publisher: MediaChance - SpyTheSpy
This is an old utility, but it's lightweight and useful for tracking newly installed applications.
- Location: C:\Program Files\Windows11FirewallControl
- Purpose: Acts as a simple firewall layer on top of Windows Defender Firewall. Both the installer and executable are safe.
- Publisher: GitHub - Windows11FirewallControl
To test whether this change was stored in memory, I shut down SiriusGPT and performed another scan. The applications were still running but were not marked as unsafe—suggesting the safe status was retained.
My Question:
Where is the data stored for applications that are manually marked as safe?
Is it saved somewhere other than the local whitelis.dbt?
It would be helpful to view and manage these entries similar to how we use Cyberlock which shows a list of trusted applications.