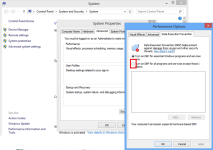
So, the VoodooShield developer made a test I wrote about in the post #24. It is good to know that
meterpreter remote session cannot be established using
Metasploit with EternalBlue & DoublePulsar exploits, when the target computer is protected with
VoodooShield 'ALWAYS ON' mode or
NVT ERP with rundll32.exe on the list of vulnerable executables.
Good work @NastyBrother.

Yet, I am not sure what DLL injection was stopped in the video. It looks like that was not EternalBlue. If that was DoublePulsar, then how it is related to the analysis:
Analyzing the DOUBLEPULSAR Kernel DLL Injection Technique | Countercept , where the injection using rundll32.exe is not mentioned at all? So, maybe VoodooShield blocks only the meterpreter payload?
Anyway, it is a very good result, for developers and people who use VoodooShield or NVT ERP.

The bad news is, that any of tested security programs, could not stop EternalBlue (and probably DoublePulsar) exploit. I said 'bad news' not to depreciate the excellent security programs,
but to stress how nasty are EternalBlue & DoublePulsar exploits.
. I read somewhere that the worm uses the heapspray method. But, I think that remote heapspray may be a challenge for some anti-exploits.