I know this is a super simplistic example of stopping an infection before the malicious process can even infect, reaching ring zero, assuming it's created to do so, and this is also my layman's way of setting up my security approach in dealing with malicious content that may find it's way onto my device, which is to prevent it from even launching in the first place:
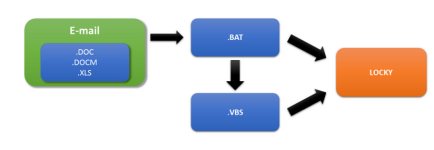
In recent months, there has been a significant increase in the number of networks and users affected by ransomware known as Locky, discusses ESET's Diego Perez.
www.welivesecurity.com
Let's say AV fails to detect it as malicious, well then the next steps could be as follows:
- My brain needs to determine if I think it's safe to open. Yes or No. If No, then I delete it and all is over. if Yes, then step 2.
- I click on the attachment.
- SRP will stop it, because it is setup to block scripts with, among other types, .BAT or .VBS extensions. No harm done.
- If I'm really being stupid and I decide to disable SRP to launch it, then OSArmor will block, giving me more details in that the .BAT script is attempting to launch the asddddd.exe payload. Well hopefully I'm smart enough (I know I would be
 ) to keep this attempt blocked.
) to keep this attempt blocked.
Again, this is very simple and perhaps I haven't even described the process accurately enough, but I perceive several steps in blocking the malware before it gets a firm foothold in ring 0, and of course more importantly, no infection occurs.
BTW, this "example case" also supports the assertions made in this thread that it is the user's fault when they get infected.
It is also just one example of why I will never fully depend on AV in my security setup , because it is not 100% reliable.



