L
Lucent Warrior
Thread author
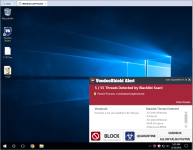
This short video is a demonstration of a Ransomware attack for those unaware of what they are,
and or what they do, and why it is necessary to make regular backups of your personal files.
Note the detection of the sample VT 5/57.
Also Note it bypassed Smartscreen & UAC.
Sample courtesy of @_CyberGhosT_ , thank you for the great catch.
and or what they do, and why it is necessary to make regular backups of your personal files.
Note the detection of the sample VT 5/57.
Also Note it bypassed Smartscreen & UAC.
Sample courtesy of @_CyberGhosT_ , thank you for the great catch.
Last edited by a moderator: