silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,736
- 123,873
- 8,399
KeePass 1.40 has been released today!
You can get it here: Download KeePass 1.40.
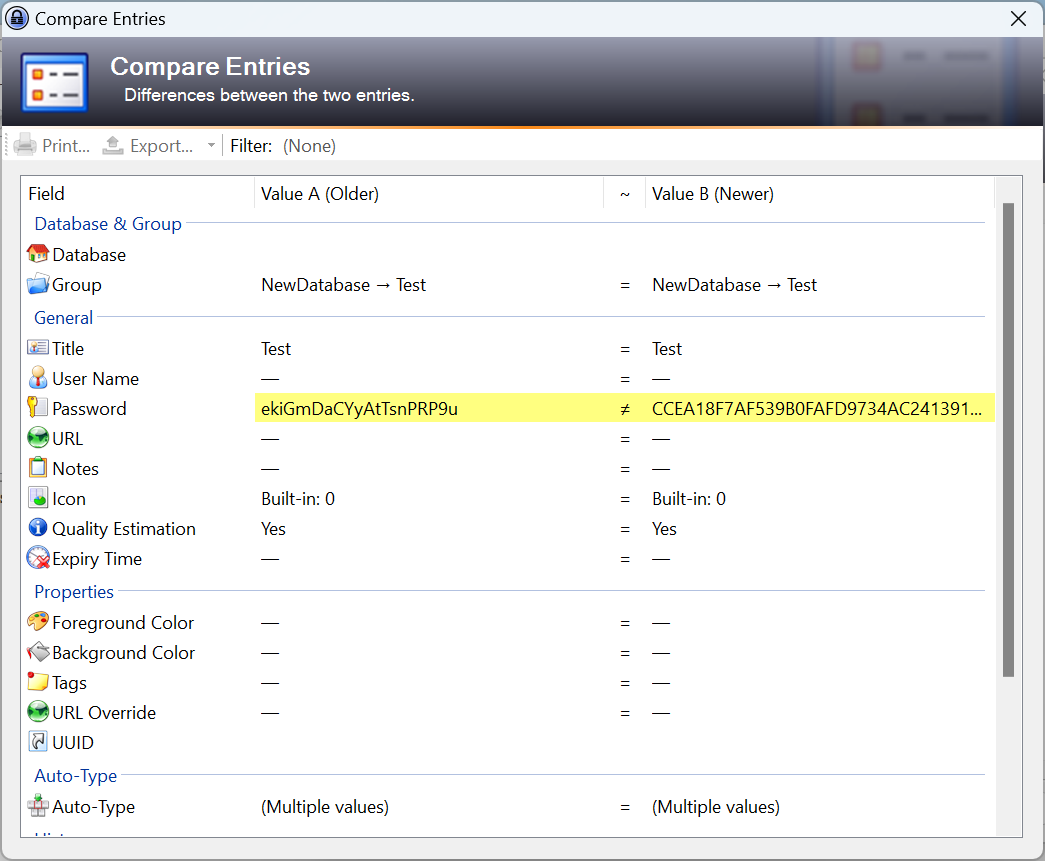
This is a stable release. It is recommended to upgrade from any previous 1.x version to 1.40. KeePass 1.40 is 100% backward compatible with previous versions.
KeePass 1.40 mainly features performance improvements and user interface enhancements, and various other minor new features and improvements.
Hashes and signatures for integrity checking are available, and program binaries are digitally signed (Authenticode). New translations are available, too.
For a comparison of the current KeePass 1.40 and 2.49, see: Editions Comparison.
Changes from 1.39 to 1.40:
New Features:
Improvements:
- On most Windows systems, AES-KDF is now about 3 times as fast as before.
- Added database file information dialog that is displayed when creating a new database.
- When double-clicking the title cell of an entry in the main entry list while holding down the Shift key, the title is now copied to the clipboard.
Bugfixes:
- Improved default configuration file.
- Various CHM file improvements.
- Upgraded to Boost libraries version 1.78.0.
- Installer: improved file overwriting.
- Upgraded installer.
- Various code optimizations.
- Minor other improvements.
- (None).