Hello, friends of MalwareTips! I was curious about Keepass's ability to keep my passwords safe primarily when entering my account credentials, and decided to look into a couple non-default settings. The two functions I checked out are secure desktop and two-channel auto-type obfuscation. I will compare these to Keepass's default data entry methods: default master password entry, copying username and password then pasting, and default auto-type.
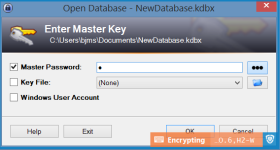
The first of the two functions is Keepass's secure desktop. This non-default setting suppresses applications and programs that are running on your computer when you enter your master key at startup. Your desktop is greyed out, and you are greeted with a normal box to type in your master password. Once entered, the greyed out desktop goes away and you may enjoy regular computer usage again. You may read more about its weaknesses, limitations, and compatibilities here. http://keepass.info/help/kb/sec_desk.html
This can be enabled by going through Tools > Options > Enter master key on secure desktop.

This is what it looks like when enabled.

Next on our adventure is Keepass's two-channel auto-type obfuscation! What this does is when auto-typing your credentials in a form the program randomly pastes and types in your credentials. This is much better than the alternatives like copying and pasting and the default auto-type. This option is enabled on an account by account basis. More indepth information may be read here. http://keepass.info/help/v2/autotype_obfuscation.html
Enable it by right clicking on an account > Edit/View Entry > Auto-Type > Two-channel auto-type obfuscation.

Next, is the setup. I put Keepass 2.29 up against five keyloggers: Actual Keylogger, Any Keylogger, Award Keylogger Pro, Elite Keylogger, Kidlogger, and Spyrix Personal Monitor. Unfortunately, I did not write down what versions the Keyloggers were. I tested these in VirtualBox's virtual machine environment with Windows 8.1 64-bit. I tested Keepass against one keylogger at a time, and when I finished testing the keylogger I loaded a clean virtual machine.
This paragraph focuses on the key to the table below. The colors are from the point of view if you were using Keepass. The text describes what the keylogger did. Red means that the keylogger was able to capture the credentials entered. Orange means that the keylogger captured a small portion of the username and password that is in a random order. So, if my username is Michael123, keyloggers will capture something like hc32M. Lastly, the green color signifies that the keylogger did not capture any information.

Conclusion
Overall, the default ways to enter username and passwords from Keepass should not be trusted. Users should switch to the secure desktop, and use two-channel auto-type obfuscation whenever they can. Copying and pasting your credentials should never be used. With regards to the two-channel auto-type obfuscation, weaker passwords are easier to find out because part of the password is revealed to the keylogger. The longer your password is, less is revealed when using two-channel auto-type obfuscation.
The first of the two functions is Keepass's secure desktop. This non-default setting suppresses applications and programs that are running on your computer when you enter your master key at startup. Your desktop is greyed out, and you are greeted with a normal box to type in your master password. Once entered, the greyed out desktop goes away and you may enjoy regular computer usage again. You may read more about its weaknesses, limitations, and compatibilities here. http://keepass.info/help/kb/sec_desk.html
This can be enabled by going through Tools > Options > Enter master key on secure desktop.

This is what it looks like when enabled.

Next on our adventure is Keepass's two-channel auto-type obfuscation! What this does is when auto-typing your credentials in a form the program randomly pastes and types in your credentials. This is much better than the alternatives like copying and pasting and the default auto-type. This option is enabled on an account by account basis. More indepth information may be read here. http://keepass.info/help/v2/autotype_obfuscation.html
Enable it by right clicking on an account > Edit/View Entry > Auto-Type > Two-channel auto-type obfuscation.

Next, is the setup. I put Keepass 2.29 up against five keyloggers: Actual Keylogger, Any Keylogger, Award Keylogger Pro, Elite Keylogger, Kidlogger, and Spyrix Personal Monitor. Unfortunately, I did not write down what versions the Keyloggers were. I tested these in VirtualBox's virtual machine environment with Windows 8.1 64-bit. I tested Keepass against one keylogger at a time, and when I finished testing the keylogger I loaded a clean virtual machine.
This paragraph focuses on the key to the table below. The colors are from the point of view if you were using Keepass. The text describes what the keylogger did. Red means that the keylogger was able to capture the credentials entered. Orange means that the keylogger captured a small portion of the username and password that is in a random order. So, if my username is Michael123, keyloggers will capture something like hc32M. Lastly, the green color signifies that the keylogger did not capture any information.

Conclusion
Overall, the default ways to enter username and passwords from Keepass should not be trusted. Users should switch to the secure desktop, and use two-channel auto-type obfuscation whenever they can. Copying and pasting your credentials should never be used. With regards to the two-channel auto-type obfuscation, weaker passwords are easier to find out because part of the password is revealed to the keylogger. The longer your password is, less is revealed when using two-channel auto-type obfuscation.
Last edited: