- Oct 9, 2016
- 6,193
FI, those using the Eloston Ungoogled Chromium v81.xxxxxx the "Extensions Toolbar Menu" flag is already there. Just enable it.
Enable next setting in experiments. Will come in Chrome 84.0 in July. Now already in Edge Chromium.Also if someone need: The command line switch for that is:
Code:--ssl-version-min=tls1.2
Site to verify the setting: https://clienttest.ssllabs.com:8443/ssltest/viewMyClient.html
Web browsers uses a lot of battery when they are run on mobile devices such as laptops. While it helps to use content blockers and other extensions to remove or block elements that may draw additional power, it is still problematic from a user perspective.
Google has run experiments in the past couple of months in its Chrome web browser to find out if the throttling of JavaScript in background tabs has an effect on the battery usage of the web browser.
Chromium engineers decided to analyze "the work done by popular sites in the background" and determined that "a lot of work was done from JavaScript timers"at were not "valuable to the user" often.
The idea was born to reduce the number of wake ups from JavaScript timers in background tabs in the web browser to find out if that would improve battery life.
Currently, JavaScript wake ups are limited to 1 wake up per second in stable versions of the Chrome web browser.
chrome://flags in the web browser's address bar.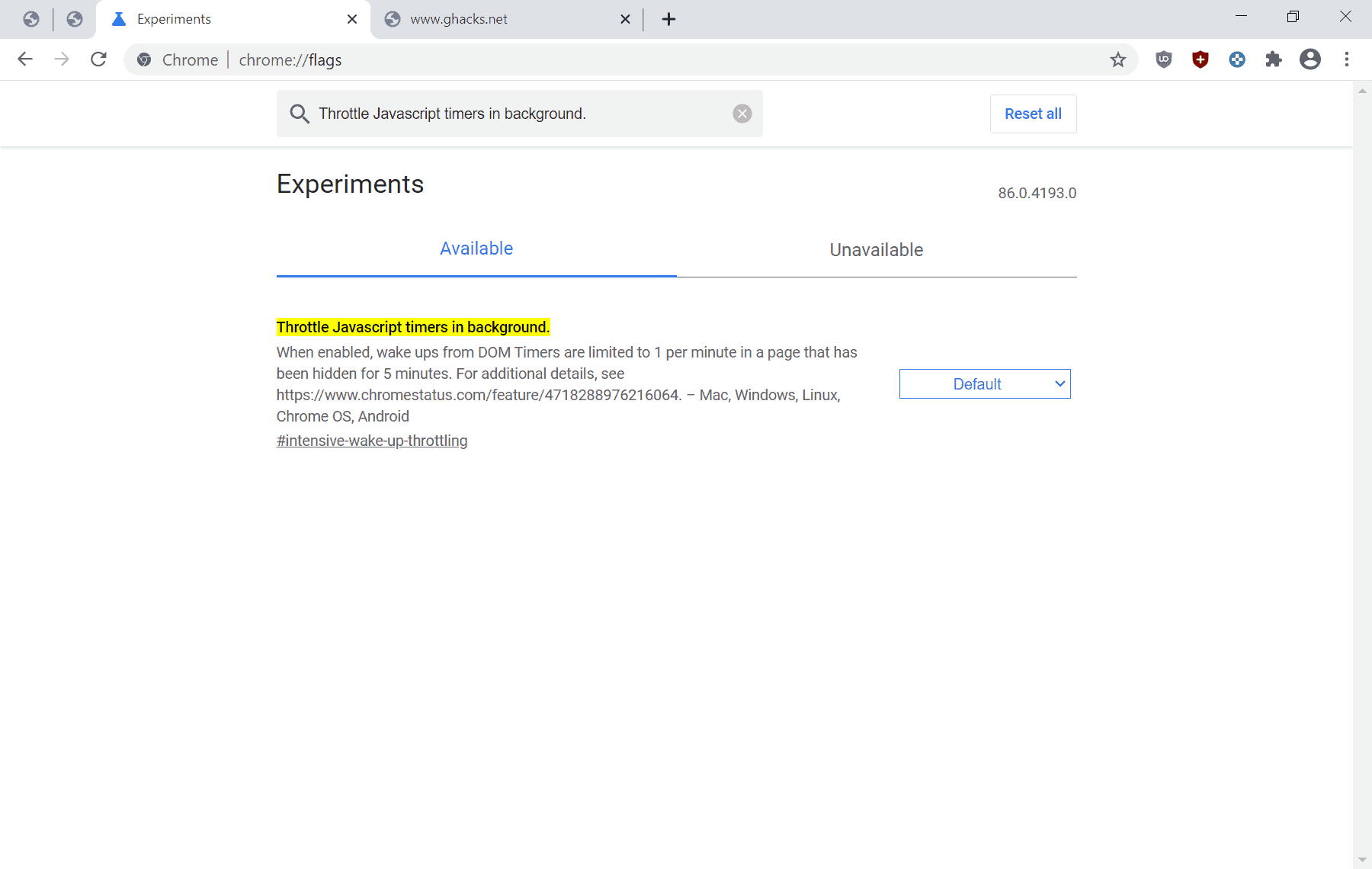
chrome://flags/#extensions-toolbar-menuchrome://flags/#post-quantum-cecpq2

I was under impression, it is better to have it disabled.Heavy ad privacy mitigations - enabled
It disables the browser's defense mechanism and is intended only for developers and site owners.
Disables privacy mitigations for the heavy ad intervention. This makes the intervention deterministic.This is intended to be used for debugging only.
Disabled #heavy-ad-privacy-mitigations
Disabled #tab-hover-cards
Enabled #block-insecure-private-network-requests
Enabled #disallow-doc-written-script-loads
Enabled #dns-httpssvc
Enabled #enable-heavy-ad-intervention
Enabled #enable-parallel-downloading
Enabled #enable-quic
Enabled #enable-webrtc-hide-local-ips-with-mdns
Enabled #omnibox-default-typed-navigations-to-https
Enabled #quiet-notification-prompts
Enabled #safe-browsing-enhanced-protection-message-in-interstitials
Enabled #turn-off-streaming-media-caching-always
Enabled #use-sync-sandboxLooks like Chrome already does this in 89.A new flag in Chrome v89 which you can enable. Chrome will try HTTPS first if you type an incomplete URL
chrome://flags/#omnibox-default-typed-navigations-to-https
Source:
- Chrome prefers HTTPS over HTTP when the user does not specify the protocol in the address bar.
Its visual flag only , its been there for ''long'' time as far as i know & lastly there is no warning as there mostly is when it might cause problems.... so i suppose its pretty ok to turn it onIs this flag ok and safe to enable now in Google Chrome last version?
You can now enable Windows 11 design in Google Chrome 96

You can now enable Windows 11 design in Google Chrome 96
Chrome 96 is now available for everyone and it comes with a new experimental flag that will make the browser appear more like native apps on Windows 11. As you know, this new generation of Windows focuses on rounded corners, subtle design improvements, and Mica material (a new transparency...www.windowslatest.com
Why?Update: The writer of that blog post Mayank Parmar, wrote to me that it's better to avoid that flag.


