@Windows_Security
Thoughts about using Isolate additional origins, if know-how is possible?
Disabled by default;
Chrome 75.x
Thoughts about using Isolate additional origins, if know-how is possible?
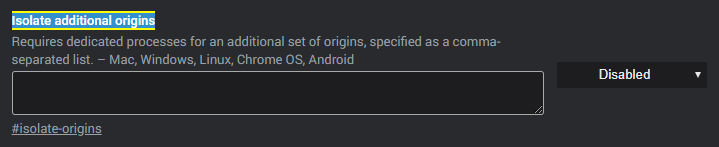
chrome://flags/#isolate-originsRequires dedicated processes for an additional set of origins, specified as a comma-separated list. – Mac, Windows, Linux, Chrome OS, Android
Disabled by default;
Chrome 75.x