- Apr 30, 2021
- 11
Hello
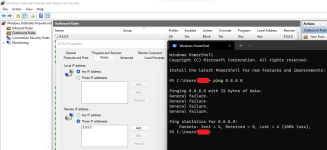
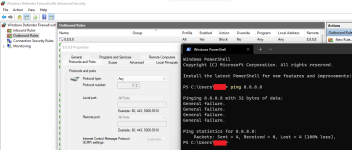
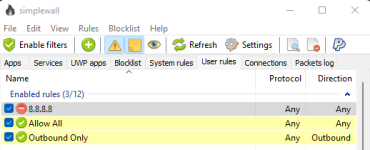
I have noticed recently that my computer is connected to shady foreign IP Addresses
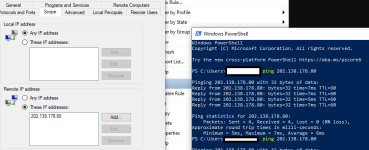
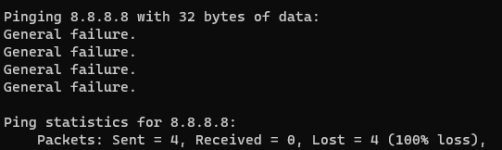
I tried blocking said IP addresses with Windows Firewall but to no effect, I am still connected
-I tested this via the ping (IP address) command in cmd
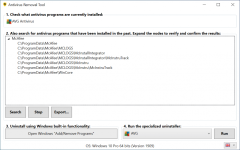
Is there any software that I can use to block IP addresses effectively?
Or will using a VPN fix this?
Note: I am currently using Evorim Free Firewall. I prefer to use it, albeit its block IP function also does not work.
I have noticed recently that my computer is connected to shady foreign IP Addresses
I tried blocking said IP addresses with Windows Firewall but to no effect, I am still connected
-I tested this via the ping (IP address) command in cmd
Is there any software that I can use to block IP addresses effectively?
Or will using a VPN fix this?
Note: I am currently using Evorim Free Firewall. I prefer to use it, albeit its block IP function also does not work.