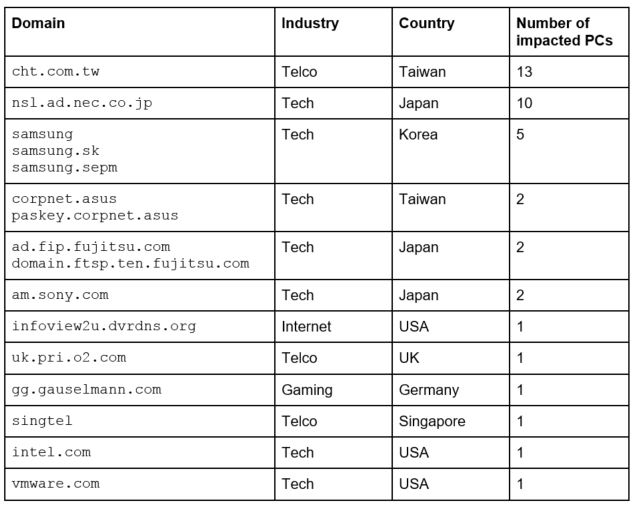
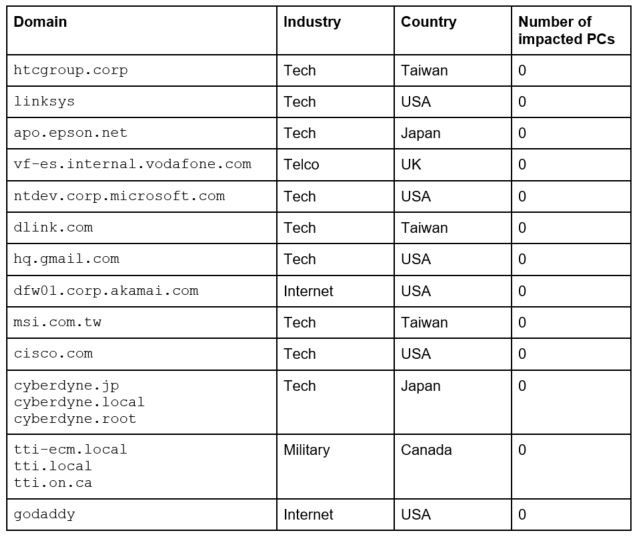
Second stage malware could have infected 100's of corporations.
I wonder if the malware is from North Korea, instead of China. I have seen plenty of documentaries on NK and noticed they use old software. Why execute in old 32 bit systems? Targets include Samsung and Sony.
I wonder if the malware is from North Korea, instead of China. I have seen plenty of documentaries on NK and noticed they use old software. Why execute in old 32 bit systems? Targets include Samsung and Sony.