Yes, it can fail for some files. To be sure, one has to always perform a manual scan on the MSI sample and if detected then allow Defender to make actions. I noticed, that this can be sometimes necessary also after unpacking the MSI sample with Windows built-in unpacker.I think that will defeat the point of having "Real-time protection".
App Review Microsoft Defender vs Magniber
- Thread starter cruelsister
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It is advised to take all reviews with a grain of salt. In extreme cases some reviews use dramatization for entertainment purposes.
- Content created by
- cruelsister
The Defender's horror of testing many MSI samples.
I tried to test 76 MSI samples packed in one archive.

Edit (no subfolders).
There is a kinda solution:
When downloading files from OneDrive, they are checked by the online service (not by Defender installed on the computer).
I tried to test 76 MSI samples packed in one archive.
- Unpacking the archive with enabled real-time protection failed.
- I disabled real-time protection and unpacked the archive into a separate folder. After enabling the real-time protection and performing the manual scan of this folder, Defender worked hard for many minutes. I saw several alerts and started the Defender actions without much progress.
- After half an hour, I restarted the system, but this did not help too.
- Finally, I gave up.
Edit (no subfolders).
There is a kinda solution:
- Disable real-time protection and unpack samples to the folder (no subfolders).
- Upload this folder to OneDrive.
- Download the folder from OneDrive (online) to the disk.
When downloading files from OneDrive, they are checked by the online service (not by Defender installed on the computer).
Last edited:
The Defender's horror of testing many MSI samples.
Edit.
There is a kinda solution:
- Disable real-time protection and unpack samples to the folder.
- Upload this folder to OneDrive.
- Download the folder from OneDrive (online) to the disk.
Good grief, I'd be too lazy to embark on this kind of song and dance. Good thing I'm not a malware tester
I was talking to former MT member "McMcBrad" about it, and he told me that this behavior of MD related to MSI files is nothing new, and it's been like this since the days of Microsoft Security Essentials.
He said:
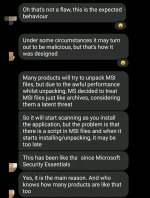
So yes, that's how it is and may not change unless Microsoft sees a lot of MSI malware hurting their Enterprise customers.
So, as Andy said, if you're suspicious of a MSI file, then scan it prior to running to make sure it's safe.
He said:

So yes, that's how it is and may not change unless Microsoft sees a lot of MSI malware hurting their Enterprise customers.
So, as Andy said, if you're suspicious of a MSI file, then scan it prior to running to make sure it's safe.
I would like to notice that the tested samples were probably actively distributed in a short time and replaced by other samples after a few hours or maybe a day. We do not know the protection of most AVs against the Magniber in this period (active period) - there were signals from other sources that protection was generally poor (with a few exceptions).
By using VirusTotal we can usually know the detections from the period when most of these samples were already dead (replaced in the wild by other samples). In other words, we know how the United States in XXI century is protected against the Persian army of Darius the Great. But, this can give us only a little information on how the United States is protected against ISIS.
By using VirusTotal we can usually know the detections from the period when most of these samples were already dead (replaced in the wild by other samples). In other words, we know how the United States in XXI century is protected against the Persian army of Darius the Great. But, this can give us only a little information on how the United States is protected against ISIS.
Last edited:
F
ForgottenSeer 94943
Well, it is not a movie. I believe the video achieved its purpose.With this quality you don't even need to post, in full 2022 at 480p?
All of these discussions must be seen in not only in terms of specifics of the subject at hand, e.g. Magniber, other specific malware cases, etc. but also in the much broader context, i.e. how likely is an encounter with one of these for the home user? In the end, it doesn't matter since most people won't.This has already turned into a war between the defenders of WD and the haters, time to change the personal disk
I just sit back and enjoy the back and forth, taking what I find valuable and leaving the rest.
I did not notice any haters.This has already turned into a war between the defenders of WD and the haters, time to change the personal disk
Most of the objections are valid for Defender and some for many AVs too.
The differences in opinions are related to the impact on users' security. There is no available data to confirm who is closer to the truth.
Nor did I.I did not notice any haters.
Some more information about the CPL variant (translated from the Korean language):
See more (use the translate feature):

 blog.alyac.co.kr
blog.alyac.co.kr
The ESRC has on several occasions called for caution against Magniber ransomware, which is being circulated through typosquatting. Typosquatting is when a user enters a domain address incorrectly or misspelles, registers the relevant domain in advance, and then uses that domain to attack with relatively few targets.
And recently, Magniber ransomware has been circulating to a large number of unspecified users by hacking into ad servers, requiring the extra attention of users. The attack was primarily carried out through ad servers embedded in websites that provide services such as watching videos or downloading files in an unlawful manner. Homepages that operate in an unlawful manner are exposed in a variety of ways because they earn income from illegal advertising.
In the course of using the services on these websites, users may intentionally or inadvertently click on advertisements to access the ad server. Every time a user clicks on an ad, the ad page is randomly accessed, and if the user connects to a hacked ad server, a file with the name Antivirus.Upgrade.Database.Cloud in the user's browser is automatically downloaded.
See more (use the translate feature):

해킹된 광고 서버를 통해 불특정 다수에게 유포중인 매그니베르 랜섬웨어 주의!
안녕하세요? 이스트시큐리티 시큐리티대응센터(이하 ESRC)입니다. ESRC는 여러차례 타이포스쿼팅 방식을 통해 유포되는 매그니베르 랜섬웨어에 대해 주의를 당부한 바 있습니다. 타이포스쿼팅이란 사용자가 도..
 blog.alyac.co.kr
blog.alyac.co.kr
Giwisin - a more sophisticated and more targeted brother of Magniber MSI ransomware.
https://asec.ahnlab.com/en/37483/
For now, the Magniber and Giwisin target mostly the countries around Korea, but this can change in the future due to the high efficiency of the MSI attack vector.
The cases of Gwisin ransomware attacking Korean companies are recently on the rise. It is being distributed to target specific companies. It is similar to Magniber in that it operates in the MSI installer form. Yet unlike Magniber which targets random individuals, Gwisin does not perform malicious behaviors on its own, requiring a special value for the execution argument. The value is used as key information to run the DLL file included in the MSI.
As such, the file alone does not perform ransomware activities on security products of various sandbox environments, making it difficult to detect Gwisin. The ransomware’s internal DLL operates by being injected into a normal Windows process. The process is different for each infected company.
https://asec.ahnlab.com/en/37483/
For now, the Magniber and Giwisin target mostly the countries around Korea, but this can change in the future due to the high efficiency of the MSI attack vector.
Last edited:
@cruelsister,
Do you recall if Controlled Folder Access blocked Magniber from deleting shadow volume copies? The video can suggest that it protected shadow copies, but we cannot be sure:
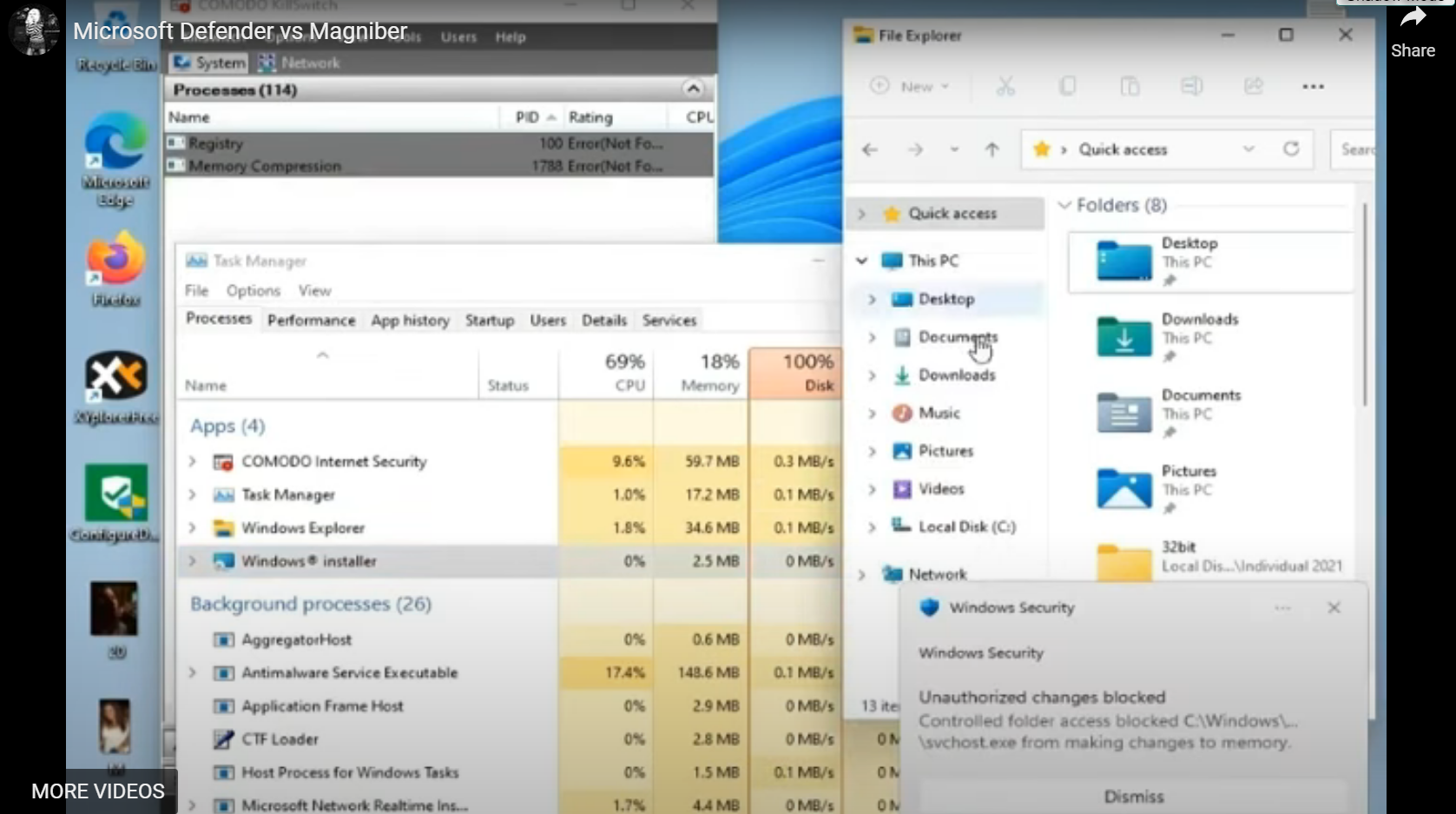
Do you recall if Controlled Folder Access blocked Magniber from deleting shadow volume copies? The video can suggest that it protected shadow copies, but we cannot be sure:
Last edited:
So, as Andy said, if you're suspicious of a MSI file, then scan it prior to running to make sure it's safe.
Makes sense, I guess using Andy's suggested method from his post #73?
Simply after downloading/unpacking the sample, one has to manually perform Defender's scan on this sample and follow the Defender alert to clean the threat.
You can use another sample that is undetected even with this manual scan:
33211a8202f4ad33f01cd90c6b1f51068a84ace5dd85a891efe5e6c210b0e7ef.msi
cruelsister
Level 43
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Controlled Folder is shown to be active at 2:14. As to Shadow copies, a similar variant was shown to delete (vssadmin) them at the 1:30 mark of the AppCheck Overview video (and at 2:08 of that same video WF was shown to be disabled by the malware). And although it wasn't asked, at 1:16 of the Defender and VirusTotal video UAC alerted to Task manager starting which is only done with UAC at Max. UAC did not, however alert to the malware.
F
ForgottenSeer 95367
There is always the notion that Microsoft does not do enough to secure Windows users. Incompetence? Negligence? Willful disregard? Disorganization? Or whatever other negative terminology one wishes to apply to a situation like TrustedInstaller and Magniber. There are similar cases or instances where the same can be said of any security software provider.This has already turned into a war between the defenders of WD and the haters, time to change the personal disk
I'm just surprised that so many people think the security problems associated with msiexec are new ones.
The words bashing and hating are two of the most abused words online. When people feel strongly about a product, when any criticism of that product is levied, the claims of hating and bashing soon follow. Unfortunately, such behavior is part of the online territory.I did not notice any haters.
I just sit back and enjoy the back and forth, taking what I find valuable and leaving the rest.
oldschool,
you are an esteemed member of this forum, and I for one would like to see you post more of your opinions rather than just just sitting back
Edit
please don't take this as a demand, it's just I value your opinions
I do not see any haters. Different opinions and approaches are important, it brings us forward.This has already turned into a war between the defenders of WD and the haters, time to change the personal disk
Very kind of you to say, but the reason I don't post more in these more technical malware threads is that I don't test malware nor do I possess much of the tech knowledge that goes with it.oldschool,
you are an esteemed member of this forum, and I for one would like to see you post more of your opinions rather than just just sitting back
Edit
please don't take this as a demand, it's just I value your opinions
I believe this question has been asked and answered somewhere in this forum but I'll ask it again as my memory betrays me, an individual would not be attacked by multiple malware as in the test presented by cruelsister I assume, that is probably done for expediency but if they were taken on one at a time would the security soft and the machine have a better chance at success?
You may also like...
-
App Review Microsoft Defender Antivirus feat AI Defender
- Started by Shadowra
- Replies: 13
-
App Review AVG vs Symantec Antivirus: This One Cleaned Better
- Started by Khushal
- Replies: 57
-
App Review Kaspersky Premium vs McAfee Advanced
- Started by Shadowra
- Replies: 87
-
App Review iDefender Free (Presentation & Reviews)
- Started by Shadowra
- Replies: 14
-
App Review iDefender Pro (Présentation & Reviews)
- Started by Shadowra
- Replies: 8


