NoVirusThanks EXE Radar Pro turns Freeware
- Thread starter Welldone
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
AtlBo - thanks
I pasted that command into Google and its something to do with Windows and reliant on a host of other processes. I will try what you have suggested and see what happens from there.
All i know is that something prevents KTS from updating the database when the PC logs off and I am sure it is an EXE Radar Pro setting or missing "accepted" command line
I pasted that command into Google and its something to do with Windows and reliant on a host of other processes. I will try what you have suggested and see what happens from there.
All i know is that something prevents KTS from updating the database when the PC logs off and I am sure it is an EXE Radar Pro setting or missing "accepted" command line
- Dec 29, 2014
- 1,717
Yes, I wasn't sure if the part of the command that changes on W10 systems with this command was the OneCore or if it was the ShellRefresh part. I think the second one is probably better to try. Anyway, a wrong attempt at a wildcard could only by a one in a trillion freak accident cause any sort of disruption on a system. So at least, experimenting with them is really quite safe...just a matter of will the pop ups stop...pleeeease...
I have only run into a few commands in NVT ERP that gave me a hard time wildcarding. There are some Google ones for Chrome and then there are some for Taskhost. I would really like to monitor Taskhost tasks, but not sure I'll be able to. Still working on that one.
On Kaspersky...are you running NVT OSArmor with ERP? I think there have been a few unalerted blocks from OSArmor reported so far. Hope this isn't one of those. If ERP is the culprit, the block event should show up in the log. You can try there. I suspect your problem may be associated with LogonUI.exe and or WinLogon.exe or WinInit.exe. Maybe you could check to see if all three of these are being allowed by ERP in the WhiteList Applications. If ERP attempts to alert during the period when the PC starts to go to sleep mode or during log off, basically everything else will be shut down. No chance of even seeing the alert. That could be what is happening with Kas...or it could be alerting about the very Kas activity itself too...
I have only run into a few commands in NVT ERP that gave me a hard time wildcarding. There are some Google ones for Chrome and then there are some for Taskhost. I would really like to monitor Taskhost tasks, but not sure I'll be able to. Still working on that one.
On Kaspersky...are you running NVT OSArmor with ERP? I think there have been a few unalerted blocks from OSArmor reported so far. Hope this isn't one of those. If ERP is the culprit, the block event should show up in the log. You can try there. I suspect your problem may be associated with LogonUI.exe and or WinLogon.exe or WinInit.exe. Maybe you could check to see if all three of these are being allowed by ERP in the WhiteList Applications. If ERP attempts to alert during the period when the PC starts to go to sleep mode or during log off, basically everything else will be shut down. No chance of even seeing the alert. That could be what is happening with Kas...or it could be alerting about the very Kas activity itself too...
Last edited:
Yes, I wasn't sure if the part of the command that changes on W10 systems with this command was the OneCore or if it was the ShellRefresh part. I think the second one is probably better to try. Anyway, a wrong attempt at a wildcard could only by a one in a trillion freak accident cause any sort of disruption on a system. So at least, experimenting with them is really quite safe...just a matter of will the pop ups stop...pleeeease...
I have only run into a few commands in NVT ERP that gave me a hard time wildcarding. There are some Google ones for Chrome and then there are some for Taskhost. I would really like to monitor Taskhost tasks, but not sure I'll be able to. Still working on that one.
On Kaspersky...are you running NVT OSArmor with ERP? I think there have been a few unalerted blocks from OSArmor reported so far. Hope this isn't one of those. If ERP is the culprit, the block event should show up in the log. You can try there. I suspect your problem may be associated with LogonUI.exe and or WinLogon.exe or WinInit.exe. Maybe you could check to see if all three of these are being allowed by ERP in the WhiteList Applications. If ERP attempts to alert during the period when the PC starts to go to sleep mode or during log off, basically everything else will be shut down. No chance of even seeing the alert. That could be what is happening with Kas...or it could be alerting about the very Kas activity itself too...
Yes both OSArmor and ERP.
LoginUI.exe is there in the whitelist, so is WinLogon.exe and WinInit.exe which is what I would have thought as I whitelisted the Windows folder processes
- Dec 29, 2014
- 1,717
Maybe Kas uses a .tmp dropper or something for the update. That would get ERP's attention. I guess OSArmor could cause the same problem if you didn't see an alert or it was too late to exlcude, etc.
I just noticed something very strange on this main system I use .
.
Where is the Program Data Folder LOL? I just checked and it's in the most recent backup the system. How is the system even running? W764 btw if anyone has seen anything like this before. Just noticed it fetching the NVT logs path, which is here:
C:\ProgramData\NoVirusThanks\EXE Radar Pro\Logs
Look around the time of the last failed attempt by Kas and see if NVT records a block.
EDIT: LOL, I have run for so many years with hidden files unhidden I didn't even realize Program Data is a hidden folder. Google is the friend yes. That's what I get for feeling confidence to hide the hideable...
I just noticed something very strange on this main system I use
Where is the Program Data Folder LOL? I just checked and it's in the most recent backup the system. How is the system even running? W764 btw if anyone has seen anything like this before. Just noticed it fetching the NVT logs path, which is here:
C:\ProgramData\NoVirusThanks\EXE Radar Pro\Logs
Look around the time of the last failed attempt by Kas and see if NVT records a block.
EDIT: LOL, I have run for so many years with hidden files unhidden I didn't even realize Program Data is a hidden folder. Google is the friend yes. That's what I get for feeling confidence to hide the hideable...
Last edited:
- Jul 3, 2015
- 8,153
The new version of ERP is out (beta of course)
New Antiexecutable: NoVirusThanks EXE Radar Pro
New Antiexecutable: NoVirusThanks EXE Radar Pro
There's a thread on this forum as well
EXE Radar Pro v4 (Beta)
EXE Radar Pro v4 (Beta)
- Dec 29, 2014
- 1,717
@shmu26...what do you think? You are the ever trustworthy one. Haven't looked yet myself other than the reading.
3.1 is so powerful. I mean every time a vulnerable alert shows up, I get the opportunity to see the command line. That's powerful..
3.1 is so powerful. I mean every time a vulnerable alert shows up, I get the opportunity to see the command line. That's powerful..
- Jul 3, 2015
- 8,153
I didn't try out this version of ERP 4 yet either, it came out after my bedtime (also, I want to read other people's comments first, lol)@shmu26...what do you think? You are the ever trustworthy one. Haven't looked yet myself other than the reading.
3.1 is so powerful. I mean every time a vulnerable alert shows up, I get the opportunity to see the command line. That's powerful..
But it promises several major improvements.
1 much more flexible handling of vulns
2 much more granular control of application execution
3 optimized for standard user accounts, and modernized for windows 10
4 non-dependent on hash value, so you don't have to redo your vuln list and other special lists after every major Windows update.
D
Deleted member 178
discussion about ERP v4 should be continued here: EXE Radar Pro v4 (Beta)
mods should close this thread since it is obsolete and redundant.
mods should close this thread since it is obsolete and redundant.
- Jan 9, 2013
- 1,457
Maybe Kas uses a .tmp dropper or something for the update. That would get ERP's attention. I guess OSArmor could cause the same problem if you didn't see an alert or it was too late to exlcude, etc.
I just noticed something very strange on this main system I use.
View attachment 181251
Where is the Program Data Folder LOL? I just checked and it's in the most recent backup the system. How is the system even running? W764 btw if anyone has seen anything like this before. Just noticed it fetching the NVT logs path, which is here:
C:\ProgramData\NoVirusThanks\EXE Radar Pro\Logs
Look around the time of the last failed attempt by Kas and see if NVT records a block.
EDIT: LOL, I have run for so many years with hidden files unhidden I didn't even realize Program Data is a hidden folder. Google is the friend yes. That's what I get for feeling confidence to hide the hideable...
I was about to say it is hidden but I guess you figured that out already
- Dec 29, 2014
- 1,717
mods should close this thread since it is obsolete and redundant.
Don't think this is redundant since it's about a different version of the program and the other thread is dedicated specifically to v4. All the information pertains to v3.x in this thread, which seems appropriate, and I doubt everyone will be retiring 3.x...
- Jul 3, 2015
- 8,153
I was for the first version but it was not compatible with windows secure boot on my system so I dropped out of the beta testing at the first stage, and could not get back in for the second stage...Oh OK. I thought you were a beta tester for ERP 4..
I made a number of comments on ERP4 on the other forum.
Hi,
This process flags up whenever I start-up/re-start my PC even though I have whitelisted the process and command line.:
Command Line : "C:\WINDOWS\system32\rundll32.exe" "C:\Program Files (x86)\Stardock\Fences\FencesMenu64.dll",StartFences
MD5 Hash : 731A783A36A8E69A6434D19D98B12A09
Process : C:\WINDOWS\system32\rundll32.exe
Parent: [8084]C:\WINDOWS\Explorer.EXE
How do I change this to a wild card type entry ?
EDIT : something must have gone astray at some point as it seems to be working OK now
Thanks
Andy
This process flags up whenever I start-up/re-start my PC even though I have whitelisted the process and command line.:
Command Line : "C:\WINDOWS\system32\rundll32.exe" "C:\Program Files (x86)\Stardock\Fences\FencesMenu64.dll",StartFences
MD5 Hash : 731A783A36A8E69A6434D19D98B12A09
Process : C:\WINDOWS\system32\rundll32.exe
Parent: [8084]C:\WINDOWS\Explorer.EXE
How do I change this to a wild card type entry ?
EDIT : something must have gone astray at some point as it seems to be working OK now
Thanks
Andy
Last edited:
- Dec 29, 2014
- 1,717
@AMD1, are you sure that's all of the command line? Did you right click the command line to view it? Use the view/edit right click option if you can't see all of it in the c-l whitelist. nm I see your edit for this...
I have a question about a command line I found that I have whitelisted. Anyone run across this command line?
"C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\USERPATH\AppData\Local\Temp\gv1_oqvb.cmdline"
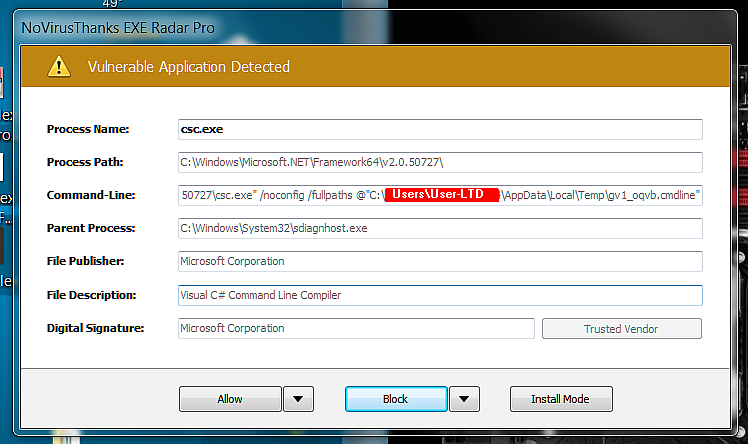
Is this MS and if so why is it using sdiagnhost.exe to start a VB script with csc.exe? What?
I have a question about a command line I found that I have whitelisted. Anyone run across this command line?
"C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\USERPATH\AppData\Local\Temp\gv1_oqvb.cmdline"
Is this MS and if so why is it using sdiagnhost.exe to start a VB script with csc.exe? What?
5
509322
@AMD1, are you sure that's all of the command line? Did you right click the command line to view it? Use the view/edit right click option if you can't see all of it in the c-l whitelist. nm I see your edit for this...
I have a question about a command line I found that I have whitelisted. Anyone run across this command line?
"C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\USERPATH\AppData\Local\Temp\gv1_oqvb.cmdline"
View attachment 183296
Is this MS and if so why is it using sdiagnhost.exe to start a VB script with csc.exe? What?
Yes, it is Microsoft. No, VBScript is not involved. sdiagnhost.exe as does csc.exe runs during Automatic Maintenance (although csc.exe might no longer run during Automatic Maintenance on Windows 10 1709) and also sometimes when the Network Troubleshooter is run. It could also be associated with a scheduled task.
Just look at gv1_oqvb.cmdline by renaming its file extension .cmdline to .txt and opening it in Notepad. If that file is no longer there, find one with extension .cmdline to see what it is. That's a start to give you an idea. Figure it out.
- Dec 29, 2014
- 1,717
ERP 3.1 settings are reverting on a PC . Happens between boots. Anyone run into this before? Settings go back to defaulst (rules stay but can be auto-added during boot since defaults allow MS and program processes) and password is dropped. Even the window size doesn't stay as it was set when using the settings last. I widen the GUI to see the program better. Seems to hold on this other PC. I have tried uninstalling and reinstalling ERP.
Last edited:
D
Deleted member 178
let me guess, you are on SUA when it happens?ERP 3.1 settings are reverting on a PC . Happens between boots. Anyone run into this before? Settings go back to defaulst (rules stay but can be auto-added during boot since defaults allow MS and program processes) and password is dropped. Even the window size doesn't stay as it was set when using the settings were last open. I wident the GUI to see the program better. They seemsto hold on this other PC. I have tried uninstalling and reinstalling ERP.
- Apr 1, 2017
- 1,808
- Status
- Not open for further replies.
Similar threads
- Replies
- 119
- Views
- 9,477
- Replies
- 2
- Views
- 493