Right, your spot on here, if their history paints the picture, and I believe it doesAnother tool from NVT which will be abandoned after a short period of active development.
NoVirusThanks OSArmor
- Thread starter Evjl's Rain
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Set OSA service to delayed start, and that will stop happening.There are no popups nothing blocked in log.
I still get slow boot with latest test16 version, I have noticed that Privatefirewall service pfsvc.exe doesn't startup automatically on boot if OSArmorDevSvc.exe is set to startup automatically, if I disable or set to manual OSArmorDevSvc.exe then Privatefirewall service pfsvc.exe is starting automatically on boot like it should. So OSArmor prevents Privatefirewall service to startup that's why I get slow boot.
How to set OSA service to delayed start on XP?Set OSA service to delayed start, and that will stop happening.
Looks like i need to create a batch file in Startup folder.
On XP check out Starter Delayer and Glarysoft's Quick Startup. I used both on XP.
Creating a batch file for OSArmorDevSvc in startup folder fix slow boot. I set OSArmorDevSvc to manual startup and delay 1sec in batch file, now my boot time 16sec @NoVirusThanks should fix this service conflict.
@Antimalware18
That means before release officially the v1.4 we need to do that things.
@Umbra
Not for now, but we can add support for blocking loading of DLLs.
@shmu26
Yes, that can be done.
@AtlBo
We can add these two options:
- Disable important actions (Configurator, Exclusions Helper, Open Custom Block-Rules, Show of Main Window, etc) if user is not an Administrator
- Disable important actions (Configurator, Exclusions Helper, Open Custom Block-Rules, Show of Main Window, etc) if user is not in the Administrators group
So SUA users can't do anything on OSA.
What do you think?
@Stas
Interesting, can you try this:
1) Add this line to the exclusions:
2) Save the exclusions and reboot the PC
3) If the boot time is fast, try to reboot like 5 times to see if it is always fast.
Probably what you need is to exclude Privatefirewall folder in OSA exclusions.
Just guessing of course, but may be worth a try.
Then remove that line from exclusions.
That means before release officially the v1.4 we need to do that things.
@Umbra
Does dlls can be blocked? (especially system.management.automation.dll)?
Not for now, but we can add support for blocking loading of DLLs.
@shmu26
Feature suggestion: let the user choose between 3 pre-set configurations:
1 medium security
2 high security
3 paranoid security
Or whatever you want to call them...
OSA has so many options that it is hard for the average user to know what is good for him. So that's where pre-set configs are very helpful.
Yes, that can be done.
@AtlBo
However, is there a way to have a choice in configuration between home single system user, where user can make choices, or networked (either single user or network administrator), where choices are only available to the administrator?
We can add these two options:
- Disable important actions (Configurator, Exclusions Helper, Open Custom Block-Rules, Show of Main Window, etc) if user is not an Administrator
- Disable important actions (Configurator, Exclusions Helper, Open Custom Block-Rules, Show of Main Window, etc) if user is not in the Administrators group
So SUA users can't do anything on OSA.
What do you think?
@Stas
Interesting, can you try this:
1) Add this line to the exclusions:
Code:
[%PROCESS%: C:\*]2) Save the exclusions and reboot the PC
3) If the boot time is fast, try to reboot like 5 times to see if it is always fast.
Probably what you need is to exclude Privatefirewall folder in OSA exclusions.
Just guessing of course, but may be worth a try.
Then remove that line from exclusions.
I already try this before I put Privatefirewall folder to exclusions and it didn't help.@Stas
Interesting, can you try this:
1) Add this line to the exclusions:
2) Save the exclusions and reboot the PCCode:[%PROCESS%: C:\*]
3) If the boot time is fast, try to reboot like 5 times to see if it is always fast.
Probably what you need is to exclude Privatefirewall folder in OSA exclusions.
Just guessing of course, but may be worth a try.
Then remove that line from exclusions.
Code:
[%PROCESS%: C:\Program Files\Privacyware\Privatefirewall 7.0\*]I just try exclude C:\* didn't work still boots slow, the only thing that helps is setting OSArmorDevSvc to manual startup and creating a batch file in startup folder to delay OSArmorDevSvc, now boot is very fast 16sec and Privatefirewall service starts properly.
Can you create option to delay OSArmorDevSvc startup by like 5sec and make it off by default. That might help Privatefirewall service to boot properly.
We can add these two options:
- Disable important actions (Configurator, Exclusions Helper, Open Custom Block-Rules, Show of Main Window, etc) if user is not an Administrator
- Disable important actions (Configurator, Exclusions Helper, Open Custom Block-Rules, Show of Main Window, etc) if user is not in the Administrators group
So SUA users can't do anything on OSA.
What do you think?
Good, yes, exactly what I was thinking, although I didn't know whether it was practical or not
Think I am having kind of a grand image of an app for managing deployment, updates, settings, and exclusions. Seems akin to me to climbing the highest mountain so to speak to be able to provide this for a security app I guess.
This app just does so much with so few FPS.
Last edited:
Here is a new v1.4 (pre-release) (test17):
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test17.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Block execution of .wsh scripts
+ Block execution of .reg scripts (unchecked by default)
+ Enabled by default "Block execution of .vbs scripts"
+ Improved internal rules
+ Fixed false positives
To install this pre-release, first uninstall the old one.
@Stas
Have you tried also to exclude OSArmor on Privatefirewall?
You should enable all "Allow" options for OSArmorDevSvc.exe, OSArmorDevUI.exe, OSArmorDevCfg.exe.
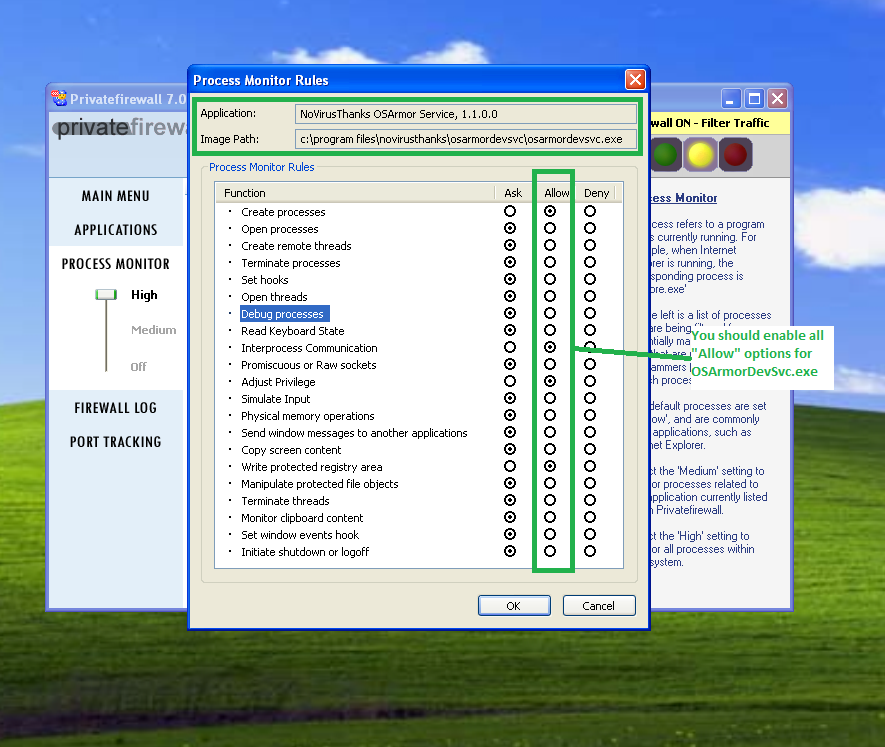
@Stas
Questions:
1) What theme do you use on XP?
2) Do you have XP SP2?
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test17.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Block execution of .wsh scripts
+ Block execution of .reg scripts (unchecked by default)
+ Enabled by default "Block execution of .vbs scripts"
+ Improved internal rules
+ Fixed false positives
To install this pre-release, first uninstall the old one.
@Stas
Have you tried also to exclude OSArmor on Privatefirewall?
You should enable all "Allow" options for OSArmorDevSvc.exe, OSArmorDevUI.exe, OSArmorDevCfg.exe.
@Stas
Questions:
1) What theme do you use on XP?
2) Do you have XP SP2?
Last edited:
D
Deleted member 178
Would be nice because some malware only needs dlls to run.@Umbra
Not for now, but we can add support for blocking loading of DLLs.
F
ForgottenSeer 58943
Here is a new v1.4 (pre-release) (test17):
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test17.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Block execution of .wsh scripts
+ Block execution of .reg scripts (unchecked by default)
+ Enabled by default "Block execution of .vbs scripts"
+ Improved internal rules
+ Fixed false positives
This version doesn't like Bullguards Network Probe.
Date/Time: 1/9/2018 12:06:44 AM
Process: [8560]C:\Program Files\BullGuard Ltd\BullGuard\Files32\BgProbe.exe
Parent: [8376]C:\Windows\SysWOW64\wbem\WMIC.exe
Rule: BlockProcessesFromWMIC
Rule Name: Block any process executed from wmic.exe
Command Line: /probe 17179615231
Signer: BullGuard Ltd
Parent Signer:
I use Royale Remixed Theme 1.47 Large size (120 dpi) setting because this PC connected to TV. I already try to allow all rules for all OSArmor .exe files, try rebooting with enable training doesn't help, I try to disable process monitor & detection system anomaly disable doesn't help. Here I make a few screenshots. When you tested did you check to see if Privatefirewall service started on boot because after slow boot Privatefirewall GUI is started but Privatefirewall service not started.
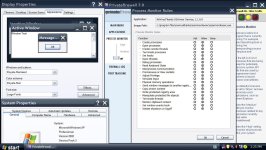
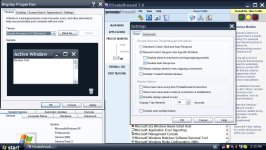
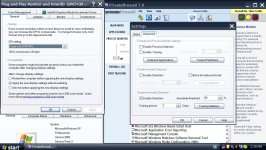
I have some free time now, do you mind if I jump on board and help test ?Here is a new v1.4 (pre-release) (test17):
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test17.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Block execution of .wsh scripts
+ Block execution of .reg scripts (unchecked by default)
+ Enabled by default "Block execution of .vbs scripts"
+ Improved internal rules
+ Fixed false positives
To install this pre-release, first uninstall the old one.
@Stas
Have you tried also to exclude OSArmor on Privatefirewall?
You should enable all "Allow" options for OSArmorDevSvc.exe, OSArmorDevUI.exe, OSArmorDevCfg.exe.
View attachment 177789
@Stas
Questions:
1) What theme do you use on XP?
2) Do you have XP SP2?
@_CyberGhosT_: The dev made it an open beta. Why not just go ahead and do it?
Last edited:
@NoVirusThanks
The "ask" popups or the easy whistling option will be available in the final release?
The "ask" popups or the easy whistling option will be available in the final release?
What would the difference security wise be between using an standard user account vs an administrator account with UAC password required for elevation set in the registry, with OSArmor set to block regedit and gpedit from being accessed?
There are many posts on this topic, see for example:What would the difference security wise be between using an standard user account vs an administrator account with UAC password required for elevation set in the registry, with OSArmor set to block regedit and gpedit from being accessed?
Q&A - Importance of "Standard User" Windows account vs "Administrator" account ?
You are safer when using OSArmor on the admin account, but much safer when using OSArmor on SUA.
Last edited:
You may also like...
-
On Sale! Avast Premium Security 1 Device 1 Year 9.99€
- Started by Brownie2019
- Replies: 0
-
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
Privacy News Windows 11 24H2/25H2 Flaw Keeps Task Manager Running After You Close It
- Started by Brownie2019
- Replies: 5