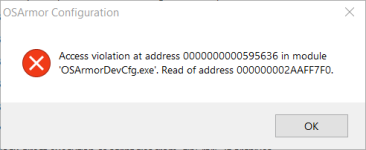
I ran OSA with VoodooShield for a couple of days with no issues but took Andy's advice and stopped using them together. I've just upgraded to Windows 10 and will let it settle in before I add any security apps.

I read recently heard that technically a banana is a herb
As I recall VS has both.Learning/training, it is all the same thing. Different apps call it by different names
both fruit and both anti-executables
I read recently heard that technically a banana is a herb
Last edited: