We have officially released OSArmor v1.4.3:
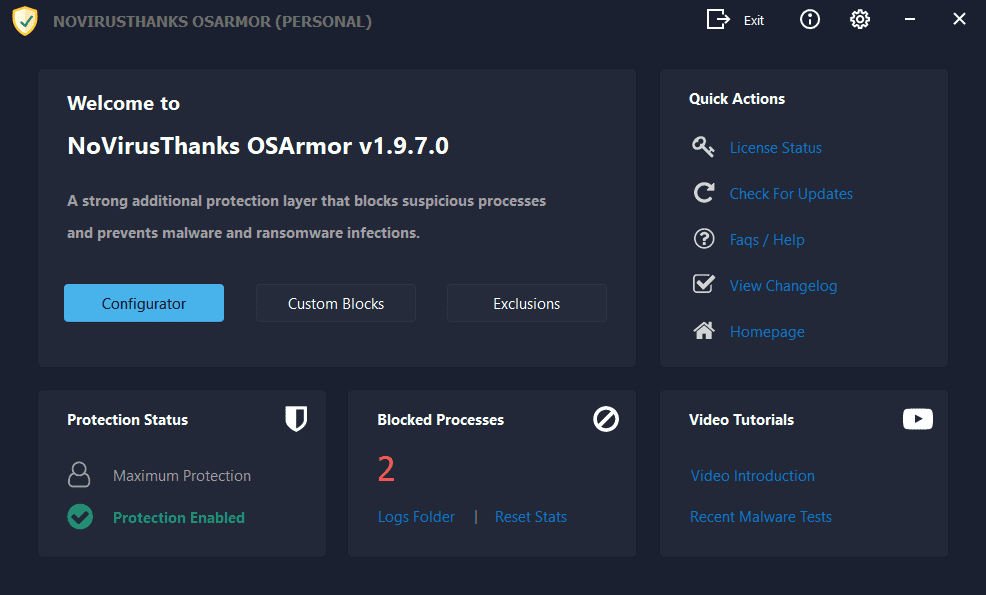
Here is the changelog:
[24-Mar-2019] v1.4.3.0
+ Disallow the UI from being respawned when the PC is rebooting or shutting down
+ Support %PROCESSMD5HASH% in CustomBlock.db and Exclusions.db
+ Improved Block processes with known fake extensions (i.e .pdf.exe)
+ Enabled by default: Prevent msiexec.exe from loading MSI files maskes as PNG files
+ Improved Block suspicious Explorer.exe process behaviors
+ Improved internal rules to block suspicious process activities
+ Improved parsing of command-line string
+ Updated the Help File (Help.txt) with Q22
+ Fixed some false positives
+ Minor improvements
Let me know if you find any issue or FPs.

Prevent Malware & Ransomware Infections on Windows PC | OSArmor
OSArmor is a Windows application that focuses on preventing malware and ransomware infections by blocking malware delivery methods and suspicious processes behaviors.
www.novirusthanks.org
Here is the changelog:
[24-Mar-2019] v1.4.3.0
+ Disallow the UI from being respawned when the PC is rebooting or shutting down
+ Support %PROCESSMD5HASH% in CustomBlock.db and Exclusions.db
+ Improved Block processes with known fake extensions (i.e .pdf.exe)
+ Enabled by default: Prevent msiexec.exe from loading MSI files maskes as PNG files
+ Improved Block suspicious Explorer.exe process behaviors
+ Improved internal rules to block suspicious process activities
+ Improved parsing of command-line string
+ Updated the Help File (Help.txt) with Q22
+ Fixed some false positives
+ Minor improvements
Let me know if you find any issue or FPs.