5
509322
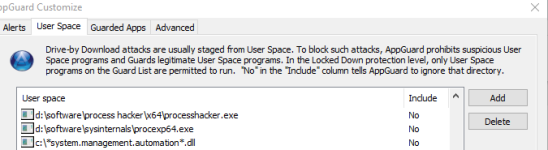
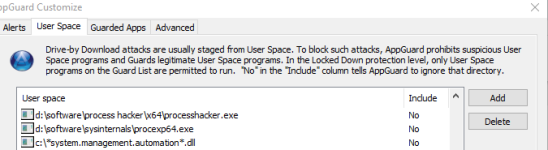
Deep in the heart, I would like to disable the PowerShell library system.management.automation.dll.
PROS:
- After blocking this library the PowerShell 3+ is dead.
- One can copy PowerShell executables to another folder with another filename and it still will be dead.
- One can compile an application that uses PowerShell functions directly from this library (not using PowerShell executables) and this also will fail.
CONS:
- There is no good Windows built-in mechanism to block this DLL in Windows Home and Pro.
- One could use SRP with DLL checking but this will break Edge and can slow down the system.
- Microsoft announced that PowerShell will replace CMD, and CMD is commonly used by some system scheduled tasks and 3-rd party programs.
- The scheduled task sdiagnhost.exe can often trigger troubleshooter scripts TS_WERQueue.ps1, TS_DiagnosticHistory.ps1, and the library of functions CL_Utility.ps1
- Some popular applications use PowerShell like: Chocolatey, K-lite codec pack, etc.
- PowerShell can be used by hardware vendors to update their software.
So, blocking the PowerShell library system.management.automation.dll can be recommended to advanced users.
I would not recommend it on computers of average users.
- Microsoft is only replacing the CMD console with PowerShell console; cmd.exe is still going to execute the command line function on Windows.
Last edited by a moderator: