Hello
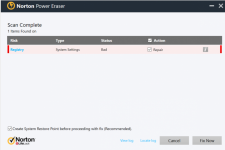
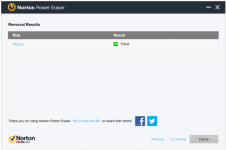
NPE detected a threat on my PC.
I'm wondering if it is a false positive or a malware ?
____________________________
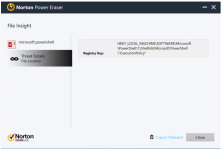
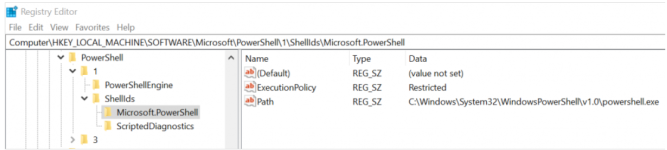
Registry Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell\"ExecutionPolicy"
____________________________
File Thumbprint - SHA:
Not Available
____________________________
NPE detected a threat on my PC.
I'm wondering if it is a false positive or a malware ?
____________________________
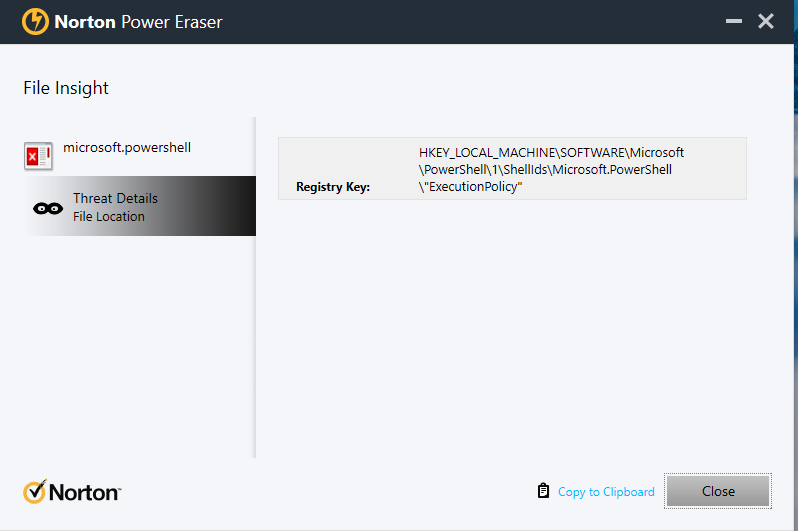
Registry Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell\"ExecutionPolicy"
____________________________
File Thumbprint - SHA:
Not Available
____________________________