You know, this is going to be a new topicsmartscreen on Windows 7 is only for IE; if you never use IE , no need to enable it.
nsm0220 updated Security Configuration for 2017
- Thread starter nsm0220
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
Nice config here!
You can replace Adblock plus with uBlock Origin, that does much more than ad-blocking (malware and badware URL blocking, privacy filters etc).
Zemana Anti-malware can be a great addition to your on-demand scanners list, against or along your MBAM.
You can replace Adblock plus with uBlock Origin, that does much more than ad-blocking (malware and badware URL blocking, privacy filters etc).
Zemana Anti-malware can be a great addition to your on-demand scanners list, against or along your MBAM.
Well, then that shouldn't be called malware testing. You're just checking the safety of unknown files.btw people i like to point that in a very rarely once in a blue moon that i test malware,i test if my mom is not sure about a file.
Nice config here!
You can replace Adblock plus with uBlock Origin, that does much more than ad-blocking (malware and badware URL blocking, privacy filters etc).
Zemana Anti-malware can be a great addition to your on-demand scanners list, against or along your Malwarebytes Anti-Malware.
I agree, i also switched to uBlock from Adblock, and i must say it was really a nice addition. Did my homework, did some basic tests and i am very pleased with the results.
UBO does decent blocking of badware and some malware domains. But even after enabling all blocking lists, it won't provide superb blocking like the famous AV URL blocking addons. It's that something will be better than nothing and UBO is rich with many other blocking options. Definitely his GData IS should do good blocking first.I agree, i also switched to uBlock from Adblock, and i must say it was really a nice addition. Did my homework, did some basic tests and i am very pleased with the results.
Now we have a new topic to battle this out: Poll - Should you disable smartscreen on windows 7 if you don't use IE?smartscreen on Windows 7 is only for IE; if you never use IE , no need to enable it.
Yes I saw thatIf I recall correctly, he runs malware samples sanboxed in Sandboxie.
I'm not making the argument that Sandboxie is sufficient, but instead just pointing out a detail in his security configuration.
All malware is nasty and SBIE is not the same as a Virtual Machine.i only test the nasty malware in a VM but for malware not doesn't cause harm to system 32 and running in a Sandboxie it be my host pc.
I guess it is just my opinion and those who test samples in the HUB.
Nevertheless we want to stress this point for the members here that this should always be done in a virtual environment.
Yes I saw that
All malware is nasty and SBIE is not the same as a Virtual Machine.
I guess it is just my opinion and those who test samples in the HUB.
Nevertheless we want to stress this point for the members here that this should always be done in a virtual environment.
Or, if possible (costly and space hungry), an even better environment, an isolated network with real PCs
Yes this would be the optimal testing enviromentOr, if possible (costly and space hungry), an even better environment, an isolated network with real PCs
@nsm0220 you need to have a look at this post:
So you should test malware in a better secure environment that provides high level of virtualization (software based / hardware assisted virtualization, latter is better) and total containment. Though the quoted post doesn't exactly warn about potential escapes from sandboxie (in Windows 7 64bit), it isn't fully isolated and can be vulnerable.
Sandboxie virtualizes the file system and registry in order to build the sandbox, but this does not make it a virtualization product as such. The aim is isolation and containment, not system virtualization as it would be with full virtualization or light virtualization products we have as alternatives.
And even otherwise, the dreadful samples that can escape sandboxie in anyway can prove to be even deadlier to your host system. Why risk when you have free and safer alternatives?
And I confirmed this issue on other forums as well. The PatchGuard protection can be excluded via a kernel tweak in x64 Windows 7 but the issue remains apparently (info).Sandboxie is fundamentally less secure by itself on a Windows Vista / 7 (x64 bit) platform due to PatchGuard, which renders Sandboxie incapable of guaranteeing the prevention of services outside the sandboxed environment from connecting to services inside. The x32 bit version isn't hindered by PatchGuard because it doesn't exist on the previous, popular Windows XP, thus it can guarantee isolation.
So you should test malware in a better secure environment that provides high level of virtualization (software based / hardware assisted virtualization, latter is better) and total containment. Though the quoted post doesn't exactly warn about potential escapes from sandboxie (in Windows 7 64bit), it isn't fully isolated and can be vulnerable.
Sandboxie virtualizes the file system and registry in order to build the sandbox, but this does not make it a virtualization product as such. The aim is isolation and containment, not system virtualization as it would be with full virtualization or light virtualization products we have as alternatives.
And even otherwise, the dreadful samples that can escape sandboxie in anyway can prove to be even deadlier to your host system. Why risk when you have free and safer alternatives?
Last edited:
@nsm0220 you need to have a look at this post:
And I confirmed this issue on other forums as well. The PatchGuard protection can be excluded via a kernel tweak in x64 Windows 7 but the issue remains apparently (info).
So you should test malware in a better secure environment that provides high level of virtualization (software based / hardware assisted virtualization, latter is better) and total containment. Though the quoted post doesn't exactly warn about potential escapes from sandboxie (in Windows 7 64bit), it isn't fully isolated and can be vulnerable.
Sandboxie virtualizes the file system and registry in order to build the sandbox, but this does not make it a virtualization product as such. The aim is isolation and containment, not system virtualization as it would be with full virtualization or light virtualization products.
And even otherwise, the dreadful samples that can escape sandboxie in anyway can prove to be even deadlier to your host system. Why risk when you have free and safer alternatives?
Very nicely explained! And also very true!
If you use Firefox to store and manage your passwords, then using a Master Password is a must.
Speaking of malware, sandboxes, safe environments (copy&paste):
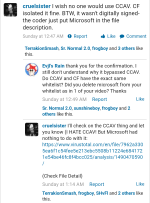
Evjl's Rain found a malware which bypassed comodo. Submitted 28 minutes ago
Parsh Could you share the setup details in short? Did it not get sb'ed or is it about something else
Evjl's Rain I was testing CCAV in all default settings. The malware has the signature: Microsoft Corporation. All rights reserved => whitelisted by comodo. It was neither detected nor sandboxed. Running in full permission. It was a spyware
https://www.hybrid-analysis.com/sam...da5b0d065d668db3f6dd331d357?environmentId=100
Evjl's Rain found a malware which bypassed comodo. Submitted 28 minutes ago
Parsh Could you share the setup details in short? Did it not get sb'ed or is it about something else
Evjl's Rain I was testing CCAV in all default settings. The malware has the signature: Microsoft Corporation. All rights reserved => whitelisted by comodo. It was neither detected nor sandboxed. Running in full permission. It was a spyware
https://www.hybrid-analysis.com/sam...da5b0d065d668db3f6dd331d357?environmentId=100
Im glad i dint use Comodo for my config.Speaking of malware, sandboxes, safe environments (copy&paste):
Evjl's Rain found a malware which bypassed comodo. Submitted 28 minutes ago
Parsh Could you share the setup details in short? Did it not get sb'ed or is it about something else
Evjl's Rain I was testing CCAV in all default settings. The malware has the signature: Microsoft Corporation. All rights reserved => whitelisted by comodo. It was neither detected nor sandboxed. Running in full permission. It was a spyware
https://www.hybrid-analysis.com/sam...da5b0d065d668db3f6dd331d357?environmentId=100
Not really i use Hitman Alert.Do you use SBIE all the time for the Web browsers?
Well i had to say goodbye to Malwarebytes after their latest version was a RAM hog,but i did find a replacement Toolwiz Time Freeze 2017.I also turn on the UAC as well but only don't dim my desktop.
Last edited:
good choice for gdata. in attention to details about proactive detection gdata is one of the best, their software is really good considering their size of company with other security company's.
- Status
- Not open for further replies.
You may also like...
-
Security News eScan confirms update server breached to push malicious update
- Started by andytan
- Replies: 43
-
Scams & Phishing News Malicious extensions in Chrome Web store steal user credentials
- Started by Brownie2019
- Replies: 1
-
Security News If you have a Samsung phone, look out for the next security update, it is massive
- Started by Gandalf_The_Grey
- Replies: 1
-
Advanced Plus Security Aries91's Security Configuration 2026
- Started by aries91
- Replies: 14
-
Technology Microsoft: Some Windows PCs fail to shut down after January update
- Started by Brownie2019
- Replies: 23