Basic Security ParaXY's Windows 10 desktop Config
- Thread starter ParaXY
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
i usually mark everything from system32 safe (right after clean install and/or scanning with zemana and eek)
I appreciate that but I'm trying to understand what and why these processes are trying to do. ie: WHY are they connecting to the internet.
you can google the processes. i googled what "SearchProtocolHost.exe" and found this response from the moderator at bc forums:
SearchProtocolHost.exe is part of the Windows Indexing Search Service. The process is constantly indexing files for faster searches and is designed to do this when the system is idle. These are common processes/services related to Windows Indexing Search which can contribute to slow performance....many users do not need this feature so it can be disabled.
ref: SearchProtocolHost.exe?? - Am I infected? What do I do?
SearchProtocolHost.exe is part of the Windows Indexing Search Service. The process is constantly indexing files for faster searches and is designed to do this when the system is idle. These are common processes/services related to Windows Indexing Search which can contribute to slow performance....many users do not need this feature so it can be disabled.
ref: SearchProtocolHost.exe?? - Am I infected? What do I do?
you can google the processes. i googled what "SearchProtocolHost.exe" and found this response from the moderator at bc forums:
SearchProtocolHost.exe is part of the Windows Indexing Search Service. The process is constantly indexing files for faster searches and is designed to do this when the system is idle. These are common processes/services related to Windows Indexing Search which can contribute to slow performance....many users do not need this feature so it can be disabled.
ref: SearchProtocolHost.exe?? - Am I infected? What do I do?
Ok but why would SearchProtocolHost.exe need internet access when indexing my local files? I have loads of these being blocked in my firewall logs.
For C:\windows\system32\consent.exe, this one needs an internet connection when you get the UAC prompt so it can check OCSP/CRL to see if a certificate is valid or has been revoked. This is worthwhile so I let it through the firewall.
For C:\windows\system32\backgroundtaskhost.exe: This is a .NET Common Language Runtime (CLR) assembly. Again, why does it need internet access?
For C:\windows\system32\sihclient.exe: Seems like SIH is for "Silent Install Helper". It starts background installation of Windows updates, as planned in advanced update options. So I allowed this through the firewall (TCP/443 only).
And the last one: C:\windows\system32\rundll32.exe. Does this need internet access? I know this is needed to run DLLs but does it need to connect to the internet?
I'm curious to hear how other forum members lock down their C:\Users folder from malware/virii...preferably with AppLocker.
Today I have denied both my SUA and Admin account from being able to run any executables, scripts, DLLs or Windows Installer Files in AppLocker.
Since I have all my software already installed, this change in AppLocker config works just fine (with one exception: uTorrent needs an exception to run).
The problem comes when you have to install NEW software. Even if I install my software from E:\SoftwareInstalls it unpacks the program into the users temp folder in C:\Users. So what I did was create a separate deny rule as follows:
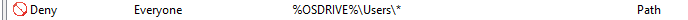
And when I need to install new software I change this Deny rule into an Allow rule temporarily or for the duration of the software install and then set it to Deny again.
Is there a better way to do this? My thinking is that blocking anything from running in C:\Users is a good idea from a security point of view albeit with some inconvenience.
Today I have denied both my SUA and Admin account from being able to run any executables, scripts, DLLs or Windows Installer Files in AppLocker.
Since I have all my software already installed, this change in AppLocker config works just fine (with one exception: uTorrent needs an exception to run).
The problem comes when you have to install NEW software. Even if I install my software from E:\SoftwareInstalls it unpacks the program into the users temp folder in C:\Users. So what I did was create a separate deny rule as follows:
And when I need to install new software I change this Deny rule into an Allow rule temporarily or for the duration of the software install and then set it to Deny again.
Is there a better way to do this? My thinking is that blocking anything from running in C:\Users is a good idea from a security point of view albeit with some inconvenience.
I've updated my config to reflect the recent changes I have made. I no longer use AppLocker and it has been completely removed from my system.
I bought a license for AppGuard and now use that instead. AppGuard is running in "Locked Down" mode and I have added my non-system drives to the User Space. I've also added PDF Xchange Editor and uTorrent to the Guarded Apps list.
I've been running my Windows 10 Enterprise 1703 build now for a few months now and am very pleased with this setup. I can honestly say this is the best Windows build/config I have ever had. It's stable, secure and the performance is excellent. What I also like about AppGuard over AppLocker is that it is really simple to put the software into install mode to install updates or new software. Doing this is far more convenient and quicker than AppLocker IMHO.
I'm also loving WFC for managing the Windows Firewall. The log viewer is excellent.
So thank you to the forum bringing AppGuard to my attention and a huge thank you to @Lockdown and the support of Blue Ridge Networks for all the help and assistance I have received.
I bought a license for AppGuard and now use that instead. AppGuard is running in "Locked Down" mode and I have added my non-system drives to the User Space. I've also added PDF Xchange Editor and uTorrent to the Guarded Apps list.
I've been running my Windows 10 Enterprise 1703 build now for a few months now and am very pleased with this setup. I can honestly say this is the best Windows build/config I have ever had. It's stable, secure and the performance is excellent. What I also like about AppGuard over AppLocker is that it is really simple to put the software into install mode to install updates or new software. Doing this is far more convenient and quicker than AppLocker IMHO.
I'm also loving WFC for managing the Windows Firewall. The log viewer is excellent.
So thank you to the forum bringing AppGuard to my attention and a huge thank you to @Lockdown and the support of Blue Ridge Networks for all the help and assistance I have received.
D
Deleted member 178
Appguard is in another league than the rest, glad you like it.
I'll be honest here, I am still very much in the early stages of fully understanding AppGuard
...
For C:\windows\system32\sihclient.exe: Seems like SIH is for "Silent Install Helper". It starts background installation of Windows updates, as planned in advanced update options. So I allowed this through the firewall (TCP/443 only).
...
It is not "Silent Install Helper" but 'Server-Initiated Healing'.
This proces should be invoked by 2 tasks in Task Scheduler:
Task Scheduler >> Task Scheduler Library >> Microsoft >> Windows >> Windows Update >> sih (and also sihboot)
Here is the short info:
This daily task launches the SIH client (server-initiated healing) to detect and fix system components that are vital to automatic updating of Windows and Microsoft software installed on the machine. This task can go online, evaluate applicability of healing actions, download necessary payloads to execute the actions, and execute healing actions.
Update to my security config:
I've stopped using the built-in Windows Firewall and have uninstalled Binisoft Windows Firewall Control.
I've since purchased the Network/Cloud Edition of the Sphinx Windows 10 Firewall Control. To say this firewall is powerful is an understatement! The amount of control you have is amazing. I'm still busy setting it up (there is a steep learning curve) but it's amazing to see how much telemetry and other traffic is going out of your machine without your knowledge when you use the built-in firewall. The Sphinx firewall reveals ALL that is going on with your machine.
When I have completed setup of my rules and finished learning this product I'm sure I will be posting more about this firewall
I've stopped using the built-in Windows Firewall and have uninstalled Binisoft Windows Firewall Control.
I've since purchased the Network/Cloud Edition of the Sphinx Windows 10 Firewall Control. To say this firewall is powerful is an understatement! The amount of control you have is amazing. I'm still busy setting it up (there is a steep learning curve) but it's amazing to see how much telemetry and other traffic is going out of your machine without your knowledge when you use the built-in firewall. The Sphinx firewall reveals ALL that is going on with your machine.
When I have completed setup of my rules and finished learning this product I'm sure I will be posting more about this firewall
I've been using the Sphinx firewall for a couple weeks now and all I can say is "WOW", this is a great piece of software. There's a fairly steep learning curve but its not that difficult to learn and its well worth the time. I've completely disabled the built-in Windows firewall service so I rely solely on the Spinx firewall to protect my system.
You just can't believe how much stuff this firewall blocks (if configured to do so) with regards to telemetry. As a test I installed Wireshark on my machine after I had finished locking it down with Sphinx and all my other WIndows 10 tweaks. I also watched some YouTube videos on Wireshark and Windows 10 just to get an idea of what other people found.
One guy did an install of Windows 10 with all the defaults and used a local account to login to the machine with. He then let Wireshark run for 15min and Wireshark captured over 500 000 packets!! The machine was "idle" with no apps running and he wasn't doing anything on the machine except capturing packets with Wireshark.
He then did another test with a clean Windows 10 build with ALL the privacy options set in "Settings" and let Wireshark capture the packets again for 15min. This time he captured 1600 packets!
I then did the same thing on my machine. I let Wireshark capture packets for 15min but I had no applications running or apps running in the system tray. I wanted to see how "chatty" my locked down install of Windows 10 was with the Sphinx firewall and all my tweaks.
The end result was, Wireshark captured just over 900 packets!!
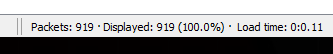
Most of the traffic captured was ARP, broadcasting on the LAN, ICMPv6 and STP with my switch. There were a few DNS requests for client.wns.windows.com but the actual connection (not DNS) was blocked by the firewall. Whats sneaky is that it tried 3 times in that 15min to connect to different IPs for that domain!
I've yet to install Windows Updates via my WSUS server with the built-in Windows firewall service stopped/disabled but I was able to install an update from the machine catalog without any issues.
All in all, very happy with the Sphinx firewall and am glad I bought it and invested some time setting it up. I think my machine is as private as I can make it and have blocked all connections to Microsoft for telemetry. (I don't use the hosts file at all to block domains as I know MS can bypass these entries, Sphinx can't be bypassed).
You just can't believe how much stuff this firewall blocks (if configured to do so) with regards to telemetry. As a test I installed Wireshark on my machine after I had finished locking it down with Sphinx and all my other WIndows 10 tweaks. I also watched some YouTube videos on Wireshark and Windows 10 just to get an idea of what other people found.
One guy did an install of Windows 10 with all the defaults and used a local account to login to the machine with. He then let Wireshark run for 15min and Wireshark captured over 500 000 packets!! The machine was "idle" with no apps running and he wasn't doing anything on the machine except capturing packets with Wireshark.
He then did another test with a clean Windows 10 build with ALL the privacy options set in "Settings" and let Wireshark capture the packets again for 15min. This time he captured 1600 packets!
I then did the same thing on my machine. I let Wireshark capture packets for 15min but I had no applications running or apps running in the system tray. I wanted to see how "chatty" my locked down install of Windows 10 was with the Sphinx firewall and all my tweaks.
The end result was, Wireshark captured just over 900 packets!!
Most of the traffic captured was ARP, broadcasting on the LAN, ICMPv6 and STP with my switch. There were a few DNS requests for client.wns.windows.com but the actual connection (not DNS) was blocked by the firewall. Whats sneaky is that it tried 3 times in that 15min to connect to different IPs for that domain!
I've yet to install Windows Updates via my WSUS server with the built-in Windows firewall service stopped/disabled but I was able to install an update from the machine catalog without any issues.
All in all, very happy with the Sphinx firewall and am glad I bought it and invested some time setting it up. I think my machine is as private as I can make it and have blocked all connections to Microsoft for telemetry. (I don't use the hosts file at all to block domains as I know MS can bypass these entries, Sphinx can't be bypassed).
You may also like...
-
Advice Request COMODO blocks Windows Updates with error 0x80070005
- Started by TheMalwareMaster
- Replies: 217
-
Advanced Plus Security Divine_Barakah's PC Security Config 2026
- Started by Divine_Barakah
- Replies: 20
-
Andy Ful's Software + Microsoft Defender + Malwarebytes Antimalware... How my PC Responds.
- Started by annaegorov
- Replies: 19
-
Technology Microsoft: Windows bug blocks Microsoft 365 desktop app installs
- Started by Brownie2019
- Replies: 3
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18