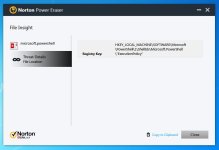
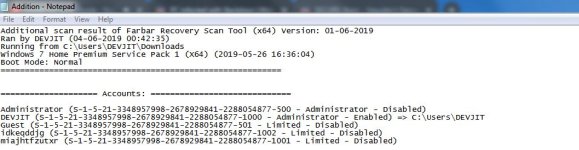
I am normally a very careful user and don't download unknown things from the Internet. This morning when I started up my PC, it booted straight into minimal SAFE MODE and after a few moments restarted automatically in NORMAL MODE. Everything seemed to be fine except for the fact that ESET INTERNET SECURITY refused to start. I had to uninstall using the ESET Removal Tool and then install ESET IS again. I made sure to update it and run a full scan and it found this threat and deleted it.(LINK BELOW). I ran Norton Power Eraser and it detected a change in Powershell policy. I fixed that. Malwarebytes detected disabled security center and a fake trojan. I removed the trojan. But even after all this I still feel that my PC is not fully clean since Farbar found two disabled limited user accounts with funny names. I don't know how the malware got there but I will be extremely grateful if someone could help me out with this.
Here is the VT link for the malwares which infected my PC
VirusTotal
Here is the VT link for the malwares which infected my PC
Attachments
Last edited: