- Oct 9, 2016
- 6,140
DNS Filters Compared
In this test, I will compare these 6 free and public DNS providers that are supposed to filter access to malicious domains:
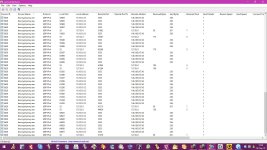
Openphish is a popular database of malicious domains, so a great place to start. From the 10 domains tested (full dump on pastebin), these are the results:
With this test, I tried to see how quickly those providers were to update their database with new domains. The dump of the tests are on pastebin as well (yeah, I screwed up my math and tested 12 domains instead of 10). Results:
In this 3rd test, I got domains that were blacklisted this month, but not today. That gives a good idea on how long they keep bad domains on their list. The results:
This last test probably wasn't very fair, since the domains Krebs mentions on his blog post are not part of any blacklist, so none of the providers blocked them, except for CleanBrowsing. They blocked 100% of the typo squatting .cm domains, along with cardmafia and some other bad domains.
Conclusion
DNS can be an important part of your security and act as a first line of defense against phishing and other malicious activity. CleanBrowsing was the #1 provider in my tests , followed by Quad9 and OpenDNS in second (they did well in different areas). Note that I used the free version of OpenDNS and if you are an enterprise client, their Cisco Umbrella could/would probably do better. CleanBrowsing has different filters to block adult content, but I tested it with their .9 IP address that only blocks malicious domains.
On the sad side, It seems that both Comodo, Norton and Yandex are stuck in time and not updated anymore. So based on my tests, would not recommend to use them if you are looking for any type of security filtering at the DNS layer.
For the whole article please read below link
Phishing Protection — Comparing DNS Security Filters
In this test, I will compare these 6 free and public DNS providers that are supposed to filter access to malicious domains:
- Quad9: 9.9.9.9
- OpenDNS: 208.67.222.123 (used their free version)
- CleanBrowsing: 185.228.168.9
- Norton ConnectSafe (Malware, Phishing and Scam sites): 199.85.126.10
- Comodo Secure: 8.26.56.26
- Yandex Safe: 77.88.8.88
- 10 domains from the Openphish database. Mix of old and new bad stuff.
- 10 domains added *today* to Phishtank. Real time bad stuff.
- 10 domains added within the last week to Phishtank. Old bad stuff.
- 10 domains from some of the latest Krebs blog posts. Bad stuff.
Openphish is a popular database of malicious domains, so a great place to start. From the 10 domains tested (full dump on pastebin), these are the results:
- Quad9 and CleanBrowsing: 100% accuracy. They blocked all domains.
- Norton: 20% accuracy. Blocked 2 domains related to fake facebook logins.
- OpenDNS, Comodo, Yandex: Blocked 0 domains.
With this test, I tried to see how quickly those providers were to update their database with new domains. The dump of the tests are on pastebin as well (yeah, I screwed up my math and tested 12 domains instead of 10). Results:
- CleanBrowsing: 91% of accuracy. Only missed 1.
- Quad9: 50% of accuracy
- OpenDNS, Yandex, Comodo, Norton: 16% of accuracy. Blocked 2 domains only.
In this 3rd test, I got domains that were blacklisted this month, but not today. That gives a good idea on how long they keep bad domains on their list. The results:
- CleanBrowsing: 100% accuracy
- OpenDNS: 60% accuracy
- Norton: 30% accuracy
- Quad9: 20% accuracy
- Yandex: 10%, Comodo 0%.
This last test probably wasn't very fair, since the domains Krebs mentions on his blog post are not part of any blacklist, so none of the providers blocked them, except for CleanBrowsing. They blocked 100% of the typo squatting .cm domains, along with cardmafia and some other bad domains.
Conclusion
DNS can be an important part of your security and act as a first line of defense against phishing and other malicious activity. CleanBrowsing was the #1 provider in my tests , followed by Quad9 and OpenDNS in second (they did well in different areas). Note that I used the free version of OpenDNS and if you are an enterprise client, their Cisco Umbrella could/would probably do better. CleanBrowsing has different filters to block adult content, but I tested it with their .9 IP address that only blocks malicious domains.
On the sad side, It seems that both Comodo, Norton and Yandex are stuck in time and not updated anymore. So based on my tests, would not recommend to use them if you are looking for any type of security filtering at the DNS layer.
For the whole article please read below link
Phishing Protection — Comparing DNS Security Filters