Welcome to this guide on how to put Kaspersky in high performance, Prevetion-First mode.
In this guide we will discuss:
In this guide we will discuss:
- What's Prevention-First Approach
- How this approach differs from containment
- Why it is recommended
- How to enable it with Kaspersky
- What's the performance impact of Kaspersky when using this mode
In addition to the forum rules that apply to each topic, I would kindly ask members not to engage in discussions related to speculations, geographical region/5,9,14 eyes and other topics not related to the technical specifications of Kaspersky.
If such comments are posted, I am kindly asking readers not to engage in any way (liking, quoting, replying). This thread must be purely technical.
Other products and technologies must be discussed only in relation to Kaspersky's protection abilities or performance impact.
No company, product, approach or defence can block 100% of all attacks at all times.
This guide contains tips related to system hardening. System hardening may in some situations cause issues. System hardening is to be deployed and managed by people who know how to react when problems arise.
This guide is not in any way incentivised by Kaspersky.
Performance impact is measured on a system with 11th Gen Intel(R) Core(TM) i5-1135G7 @ 2.40GHz 2.42 GHz, 16 GB DDR4 RAM, Average Samsung NVME SSD with read speed of 560MB. On other systems different metrics may be observed.
Some comments and views will be supported by evidence, for others, evidence may not be provided. You are responsible for Googling and double-checking any statements you believe may be false or inaccurate.
If certain setting groups are not mentioned in this guide, it means there is nothing to modify or mention there.
If such comments are posted, I am kindly asking readers not to engage in any way (liking, quoting, replying). This thread must be purely technical.
Other products and technologies must be discussed only in relation to Kaspersky's protection abilities or performance impact.
No company, product, approach or defence can block 100% of all attacks at all times.
This guide contains tips related to system hardening. System hardening may in some situations cause issues. System hardening is to be deployed and managed by people who know how to react when problems arise.
This guide is not in any way incentivised by Kaspersky.
Performance impact is measured on a system with 11th Gen Intel(R) Core(TM) i5-1135G7 @ 2.40GHz 2.42 GHz, 16 GB DDR4 RAM, Average Samsung NVME SSD with read speed of 560MB. On other systems different metrics may be observed.
Some comments and views will be supported by evidence, for others, evidence may not be provided. You are responsible for Googling and double-checking any statements you believe may be false or inaccurate.
If certain setting groups are not mentioned in this guide, it means there is nothing to modify or mention there.
Cybersecurity is centread around the CIA triad - confidentiality, integrity and availability of information. Confidentiality manages who can access information. Integrity manages who can modify it. Availability ensures that information can be accessed when needed.
Any attempt that goes against the CIA triad is a threat and there are various technologies aimed at blocking threats.
Some of them are oriented towards identification of malicious code - antivirus scanning, behavioural blocking, machine learning, heuristics, generic detection and many others.
Another set of technologies such as sandboxing and default-deny are oriented towards preventon of dangerous actions, without anything in particular (such as ransomware) having being identified.
This guide is centred around permissions-managment and default-deny.
Any attempt that goes against the CIA triad is a threat and there are various technologies aimed at blocking threats.
Some of them are oriented towards identification of malicious code - antivirus scanning, behavioural blocking, machine learning, heuristics, generic detection and many others.
Another set of technologies such as sandboxing and default-deny are oriented towards preventon of dangerous actions, without anything in particular (such as ransomware) having being identified.
This guide is centred around permissions-managment and default-deny.
Whilst sandboxing is oriented towards virtualising resources (creating fake copies of operating system, hardware and files), Host-Based Intrusion Prevention systems such as Kaspersky Intrusion Prevention manage permissions to access, modify and delete real resources. This approach is lighter on performance and doesn't compromise security severely.
The end goal of mitigating damage from unknown, undetected malicious code is still maintained.
The end goal of mitigating damage from unknown, undetected malicious code is still maintained.
With so many criminals working non-stop to evade detection, methods oriented towards identification code can't keep up and can't cover all threats at all times. Attackers can easily obtain copies of pretty much any security product and via trial and error can discover vector that is poorly covered. Even methods such as cloud detonation have multiple evasion methods.
More information can be found on the CheckPoint Cloud Detonation Evasion Page. Majority of technologies and even gateways can be "fooled" just by putting a file in a password-protected archive.
More information can be found on the CheckPoint Cloud Detonation Evasion Page. Majority of technologies and even gateways can be "fooled" just by putting a file in a password-protected archive.
Now we'll discuss how to decrease Kaspersky's standard antivirus and other non-core activities whilst boosting its prevention abilities.
First, we'll decrease the impact of standard antivirus. In this approach, we need antivirus only to detect known threats.
To do that, we will apply the following settings to standard antivirus:
First, we'll decrease the impact of standard antivirus. In this approach, we need antivirus only to detect known threats.
To do that, we will apply the following settings to standard antivirus:
We are enabling scan by extension and turning off heuristics. This removes the performance impact of the parser that must be used to detect the true file type and the emulator that will run instructions in a virtual environment.
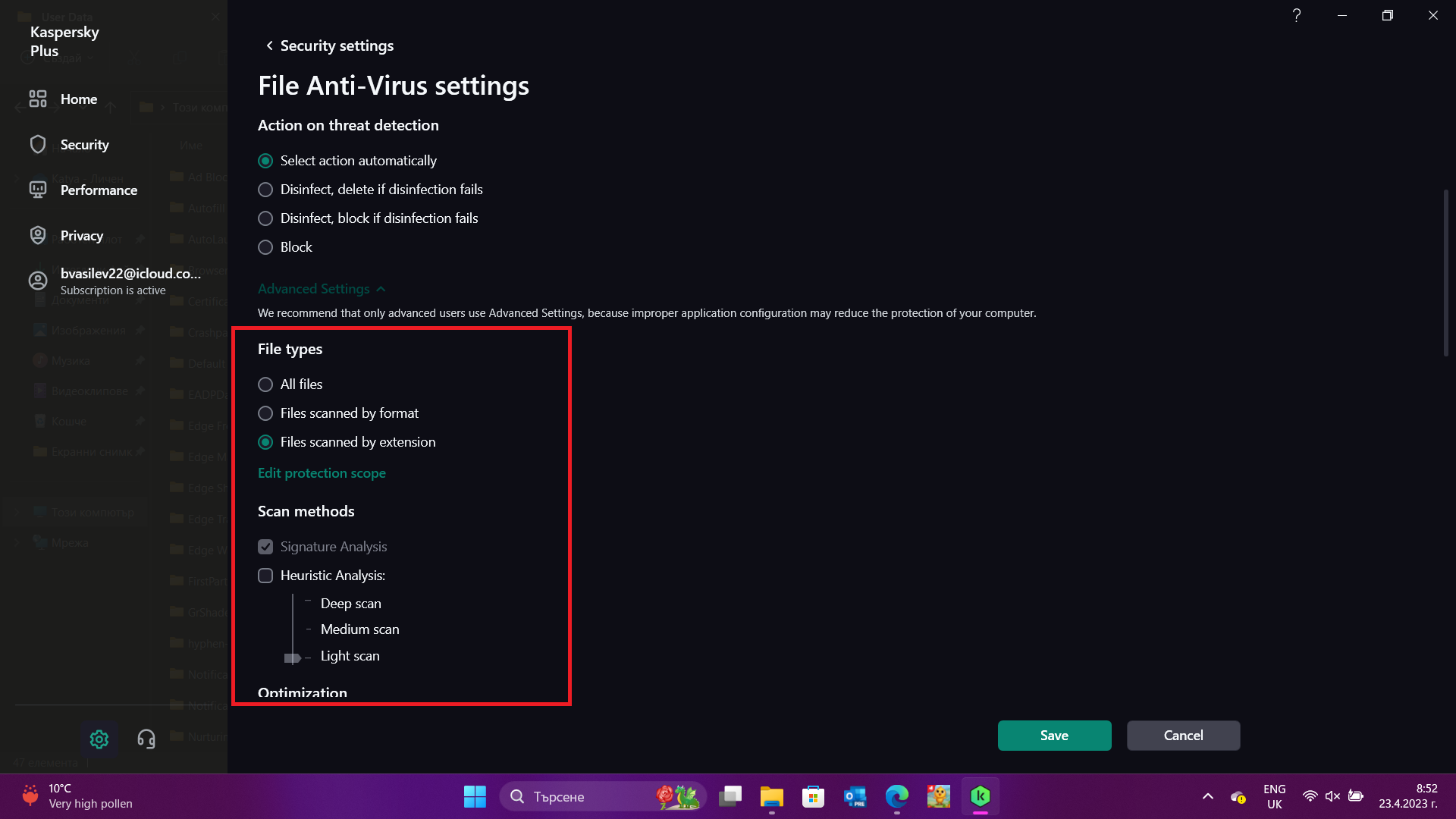
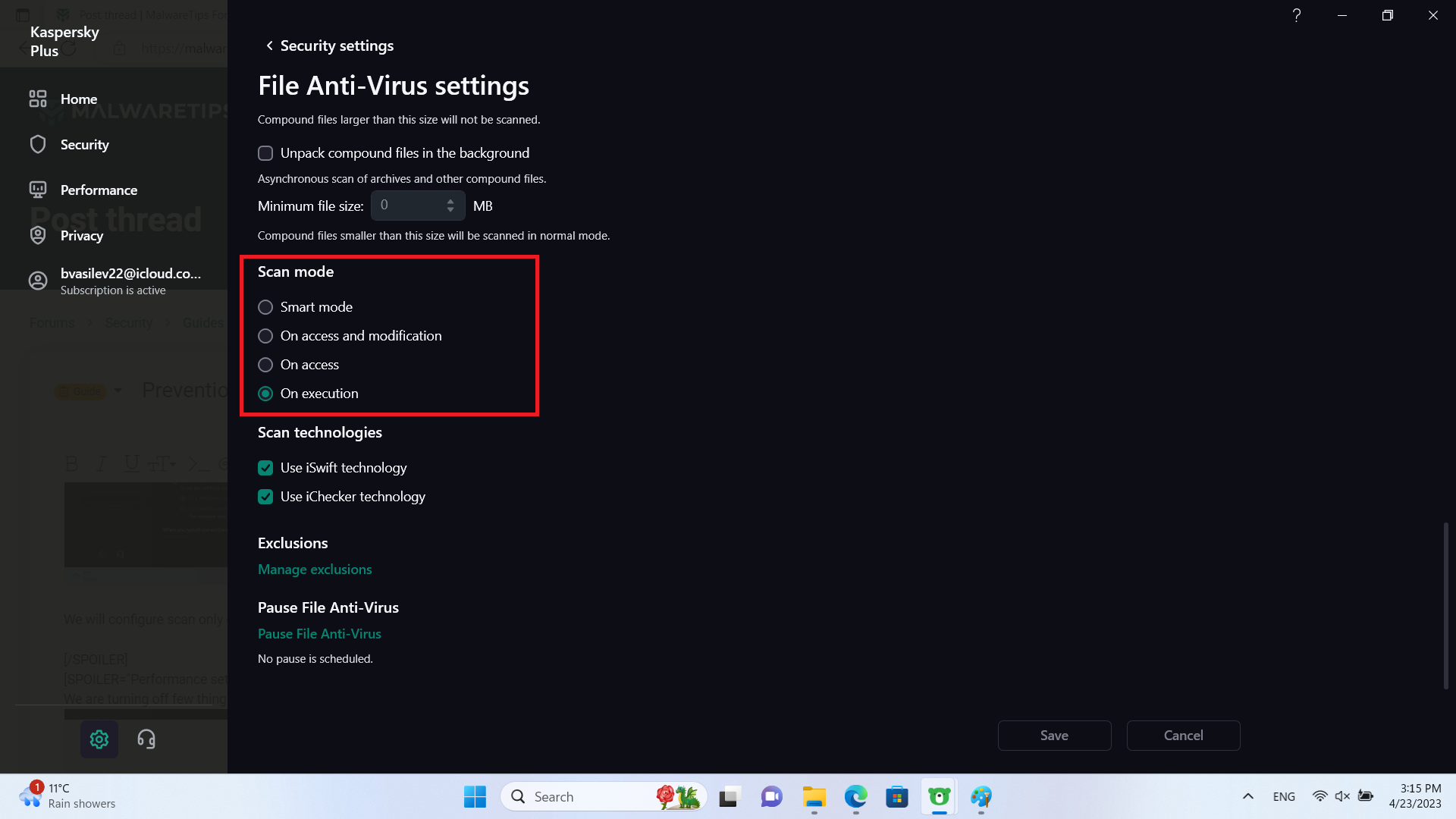
We will configure scan only on-access as well.
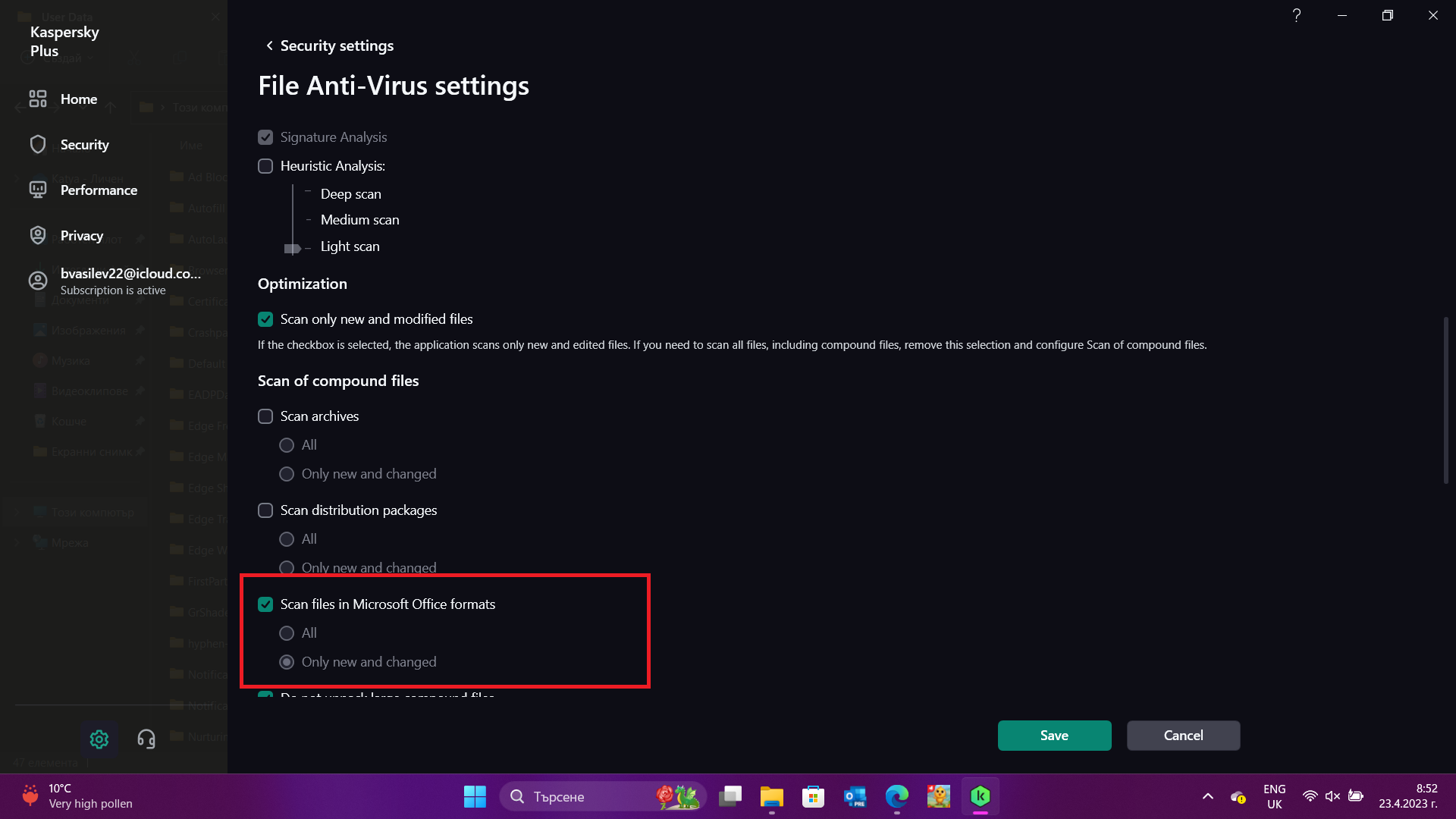
Making sure scanning of office formats is enabled.
We will configure scan only on-access as well.
Making sure scanning of office formats is enabled.
Under web antivirus, we will disable heuristics analysis as well.
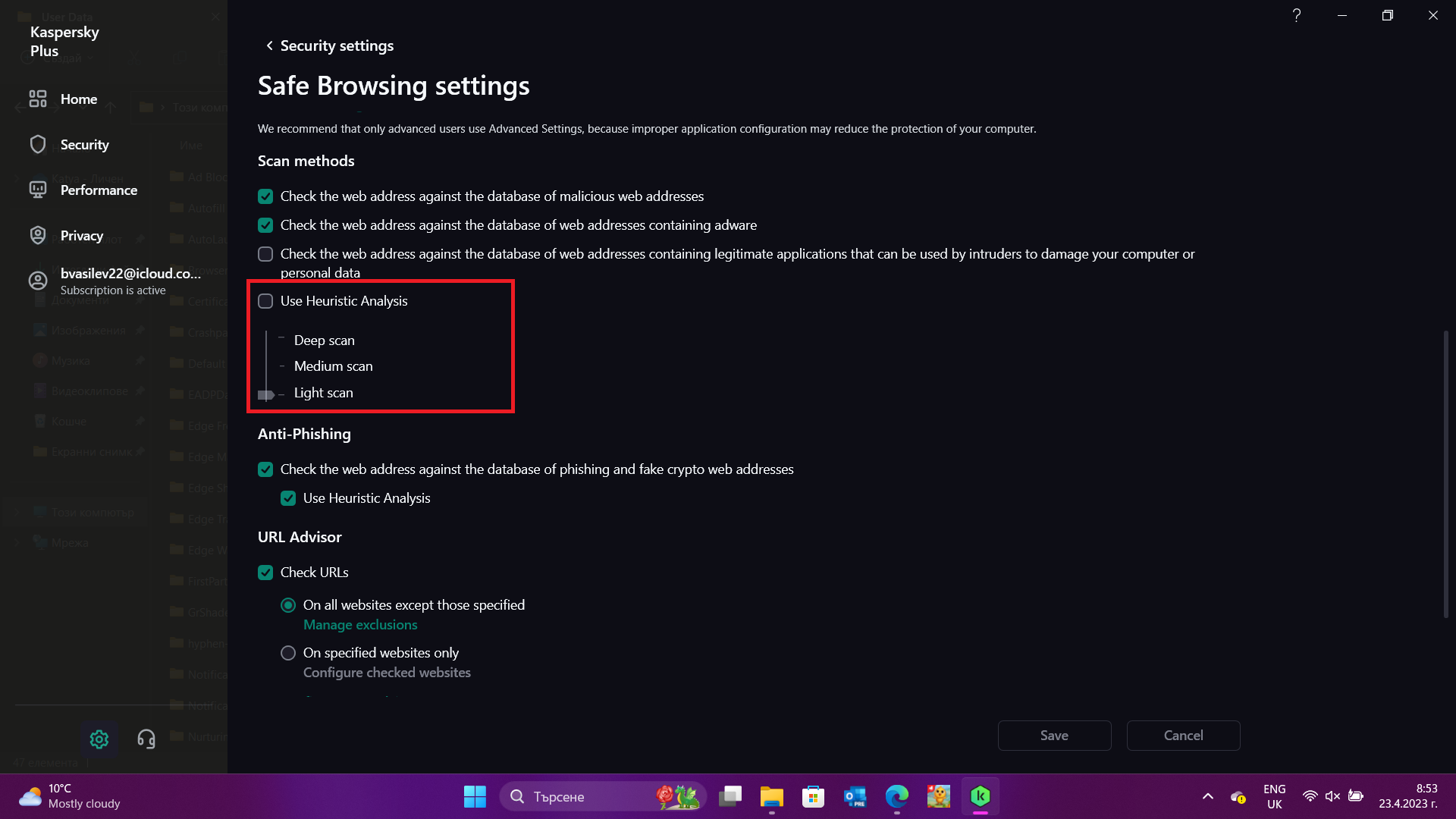
We'll still leave antiphishing heuristics on though. These should detect attemts to impersonate companies/brands by checking the text for spelling mistakes, checking the logos and other logics. The prevention of damage from malicious code does not apply to phishing attacks and they continue being a problem.
A little bit further down the Safe browsing settings, we'll disable this:
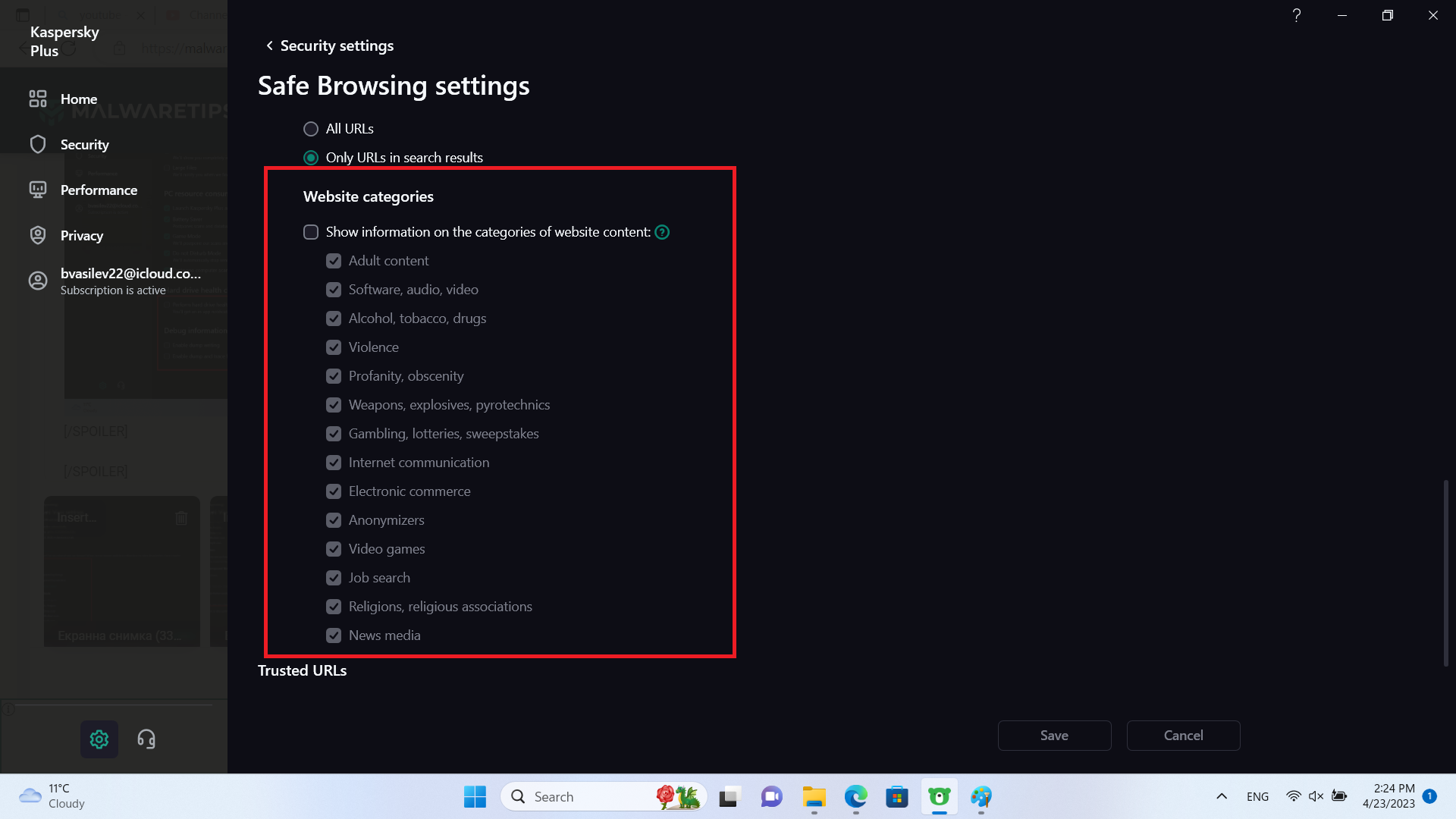
We'll still leave antiphishing heuristics on though. These should detect attemts to impersonate companies/brands by checking the text for spelling mistakes, checking the logos and other logics. The prevention of damage from malicious code does not apply to phishing attacks and they continue being a problem.
A little bit further down the Safe browsing settings, we'll disable this:
Nothing to modify here but:
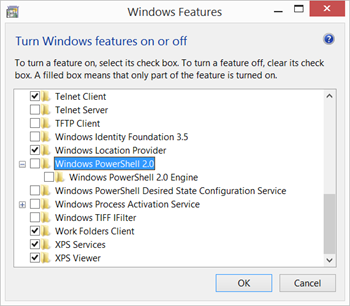
It is important to note that the default PowerShell 5.1 built-in to Windows 11 could be downgraded to a less secure version 2 that offers decreased scanning.
In the process of bypassing AMSI, attackers frequently call PowerShell 1.
Further on in the guide, we'll block the execution of PowerShell completely and will also prevent unknown code from launching child processes (they can easily drop portable powershell and launch an attack).
Installing the latest PowerShell can be performed via this command:
It is important to note that the default PowerShell 5.1 built-in to Windows 11 could be downgraded to a less secure version 2 that offers decreased scanning.
In the process of bypassing AMSI, attackers frequently call PowerShell 1.
Further on in the guide, we'll block the execution of PowerShell completely and will also prevent unknown code from launching child processes (they can easily drop portable powershell and launch an attack).
Installing the latest PowerShell can be performed via this command:
Users not in a need of executing complicated scripts (which is probably above 90%) can skip updating PowerShell.winget install --id Microsoft.Powershell --source winget
We are turning this off, it is non-core module.
We are turning off the scanning of encrypted connections. I initially thought about turning off the injection of scripts, but it did not make any difference in terms of impact.
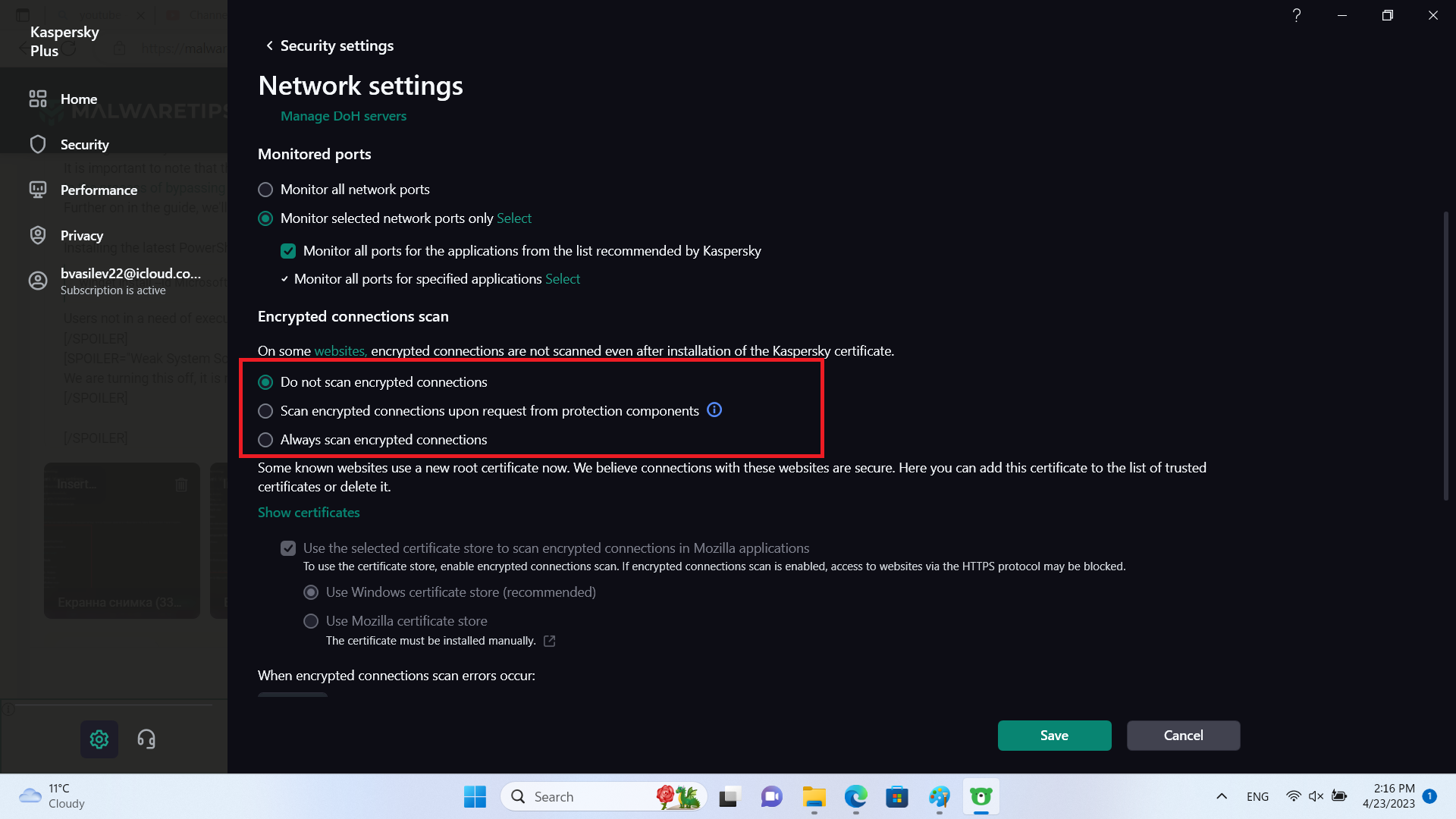
We are turning off few things here as they diverge from the core protection.
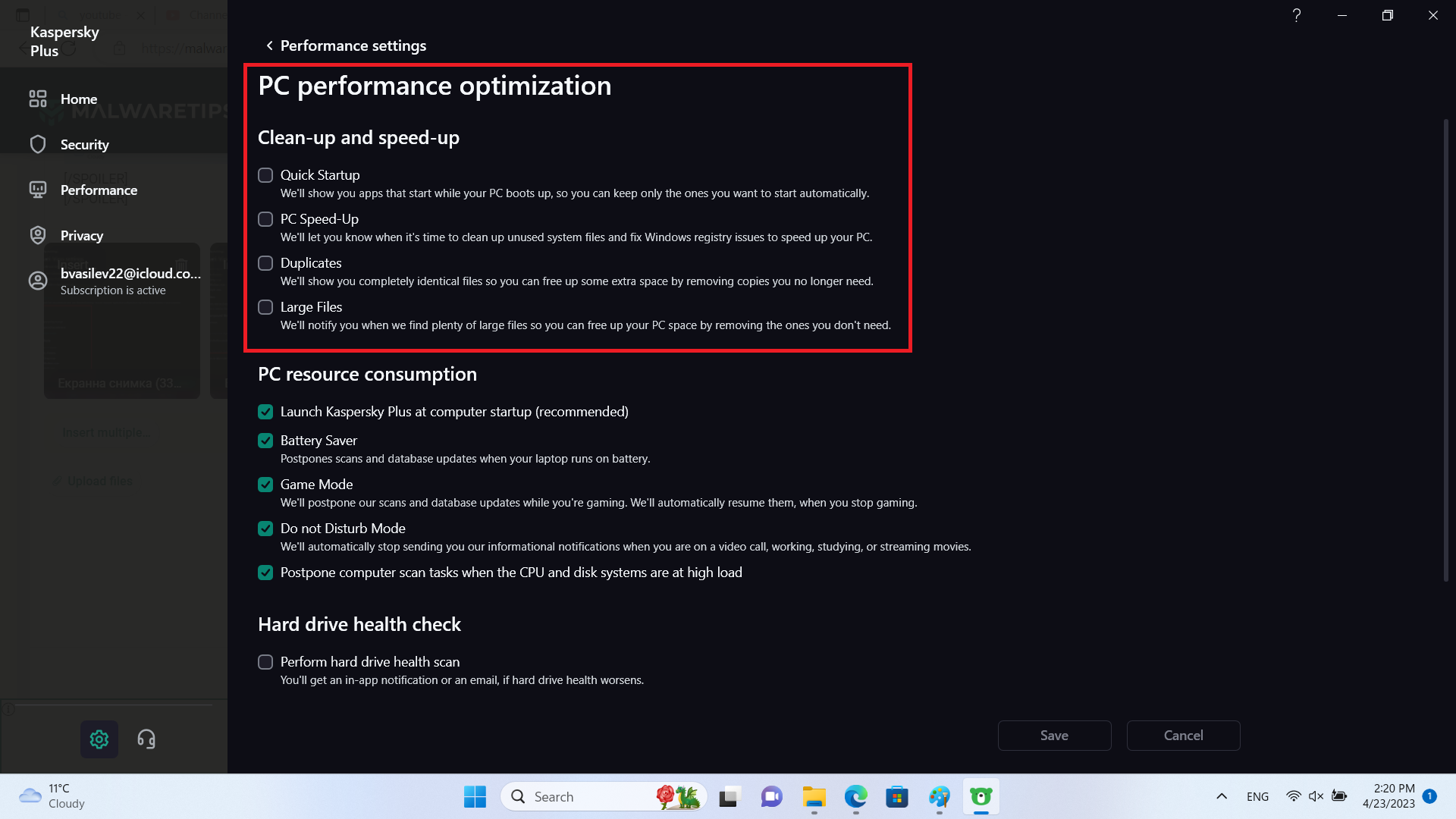
This is not needed, we will disable everything there.
This is not needed, we will disable it.
To reiterate again, this is Host-Based Intrusion Prevention or smart HIPS. It is not network-based intrusion prevention that inspects traffic for signs of bots, exploits, laterral movement and others. Kaspersky blocks connection to infected hosts via other components.
Intrusion Prevention assigns trust to every object (script, program) individually and does not suffer issues where trust is assigned to the script interpretor, and all scripts can do whatever they decide.
For example, 5 *.bat files and 5 *.vbs scripts will have individual trust levels, based on the reputation Kaspersky has assigned to them. I tried many different Intrusion Prevention settings but a lot of them generated a sheer number of alerts & events. The most quiet and acceptable setups are 2 and displayed below:
Complete default-deny:
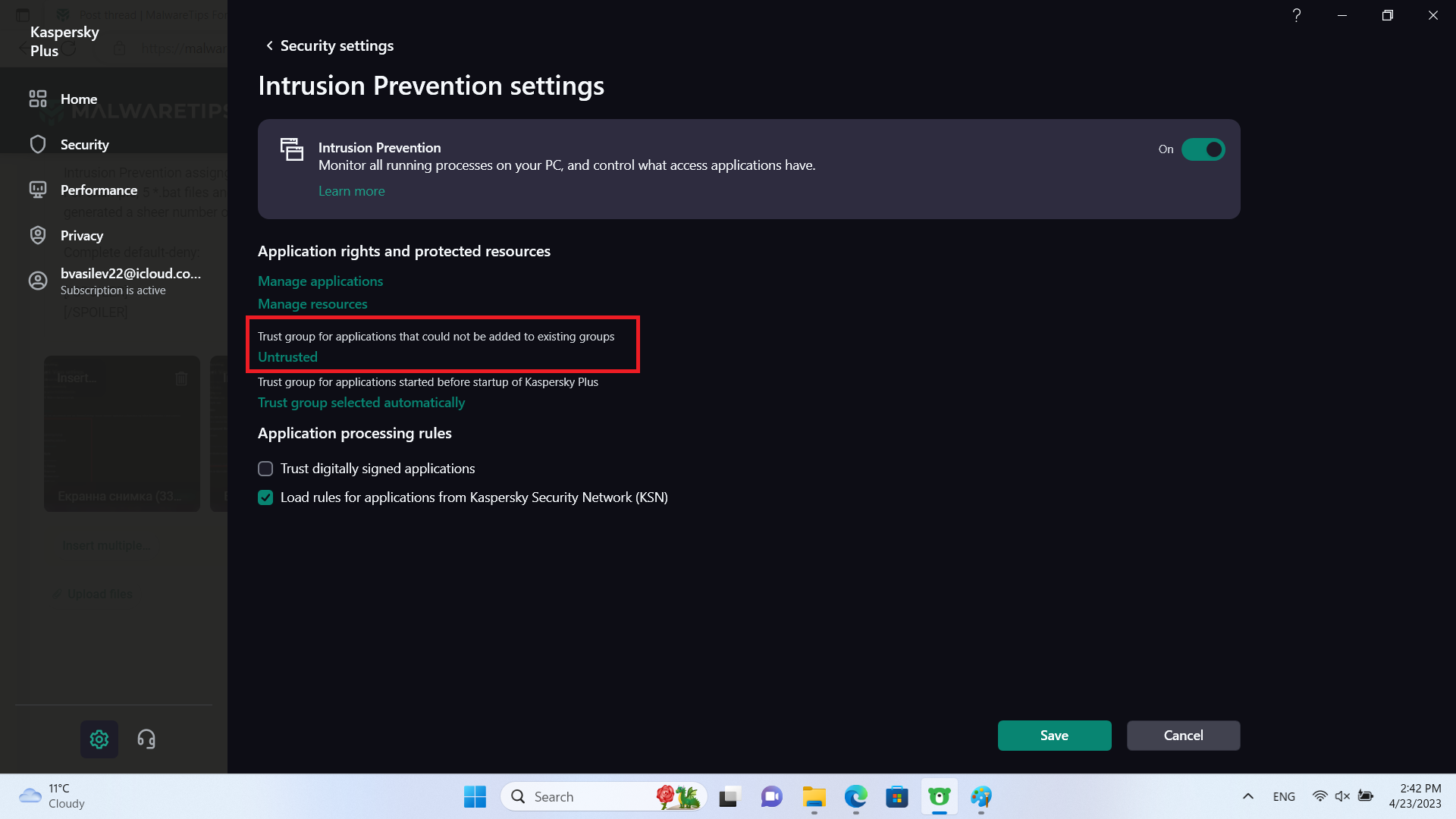
In this setup, it is impossible to execute code that has not undergone prior checks.
High-Restricted:
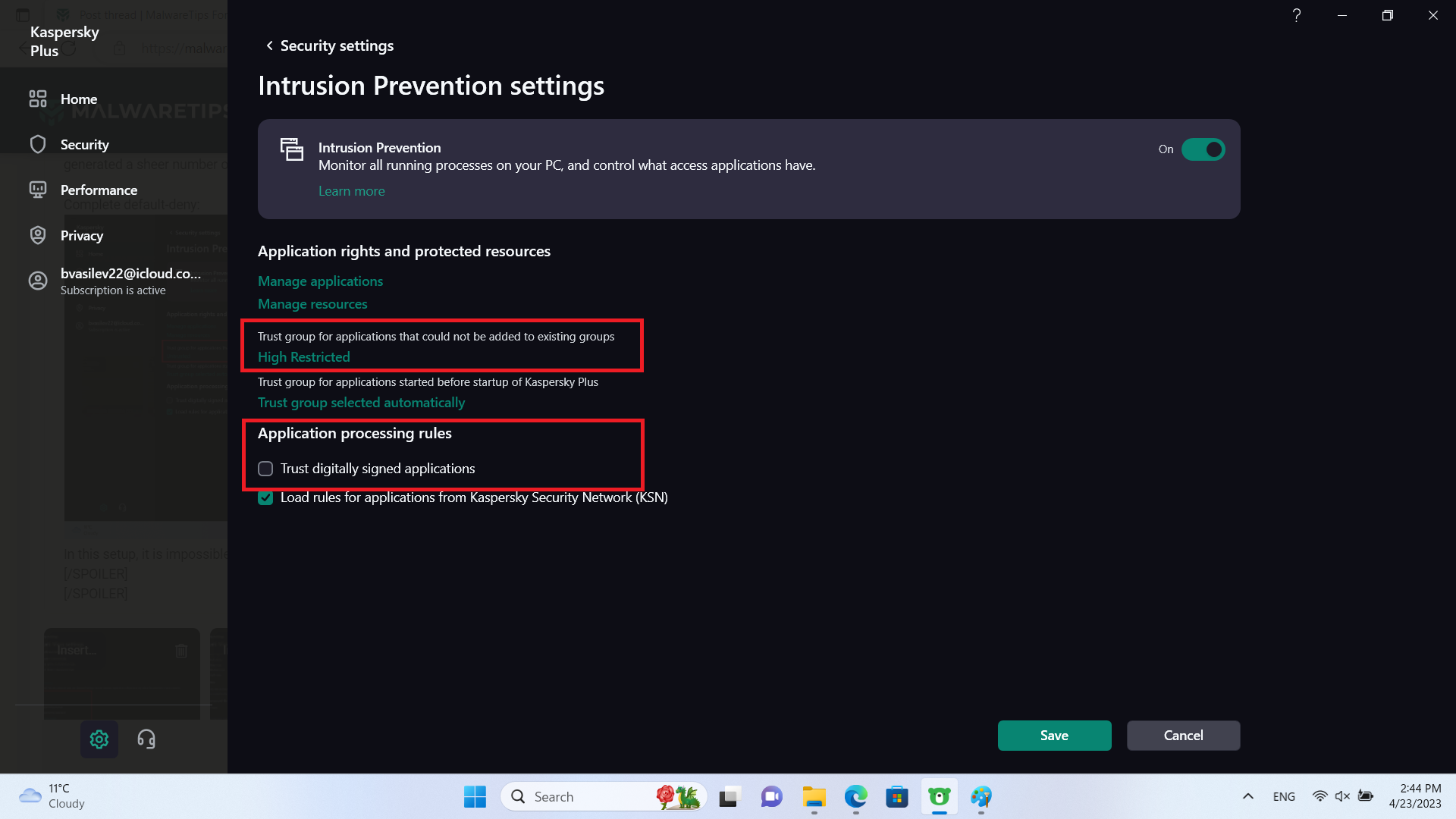
In this setup, code that has not undergone prior checks will be severely restricted.
Notice in both setups, I have unchecked "Trust digitally signed applications".
This will prevent code signing abuse
For more information on signed malware, I recommend looking here:
 www.trendmicro.com
www.trendmicro.com
Moving on, we will protect browser passwords and more crucially, session cookies from being accessed by anything else, apart from the browser itself.
For example, only Edge will have access to the Edge data folder.
To do this, we'll create a subgroup of trusted (under manage applications)
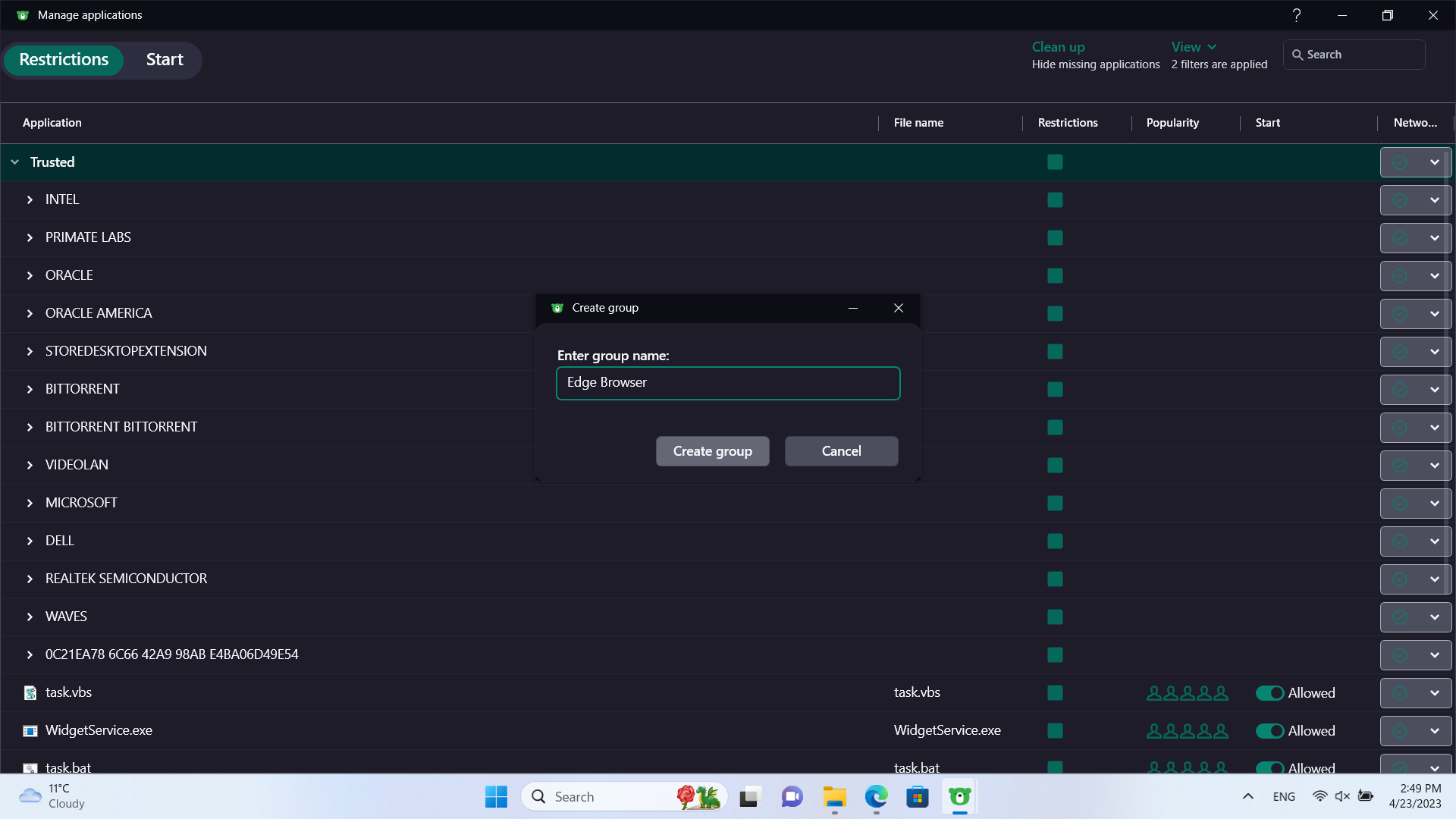
Under this group, we'll add the following:
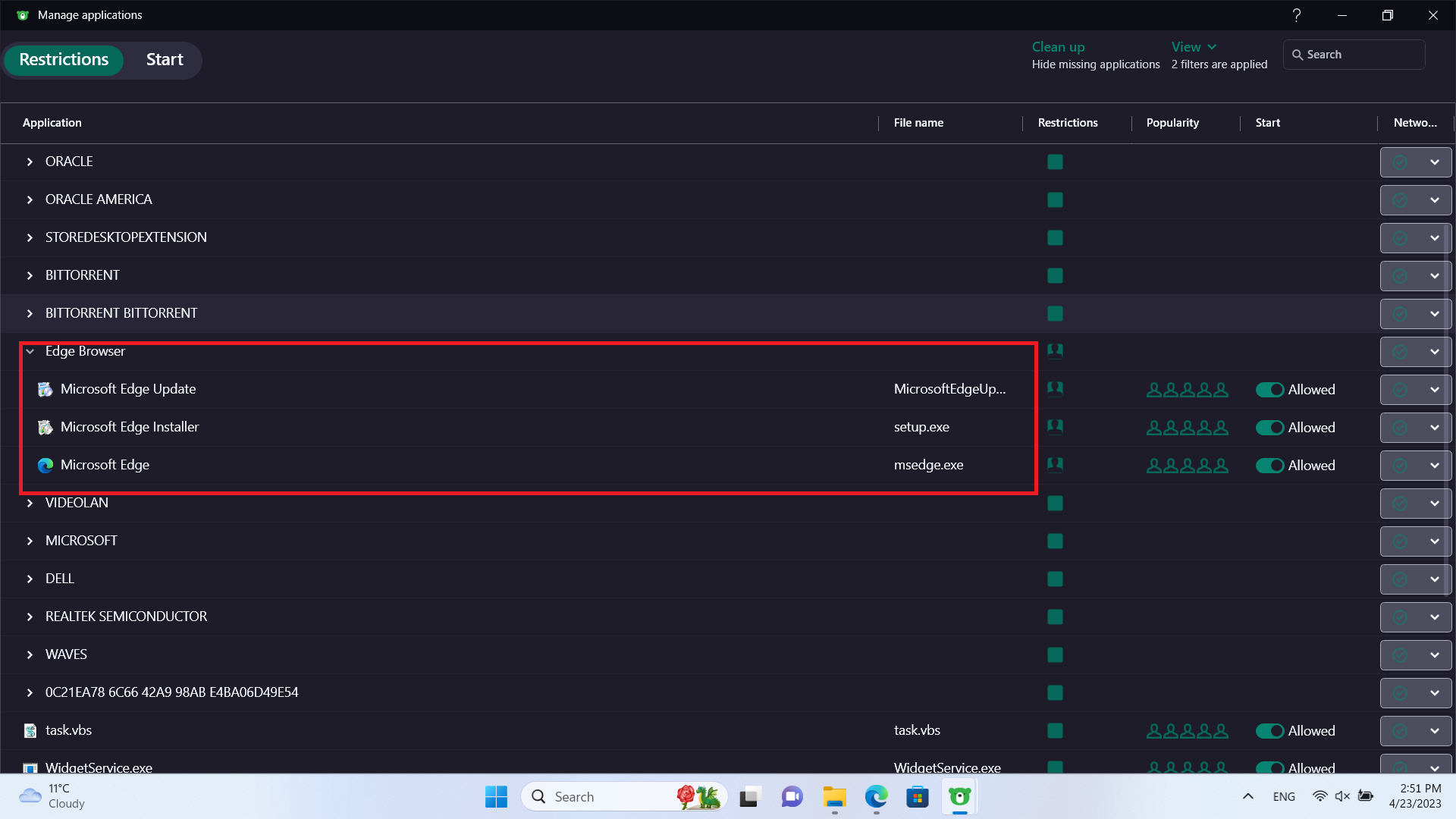
Next, we under resources to add the Edge repository located at:
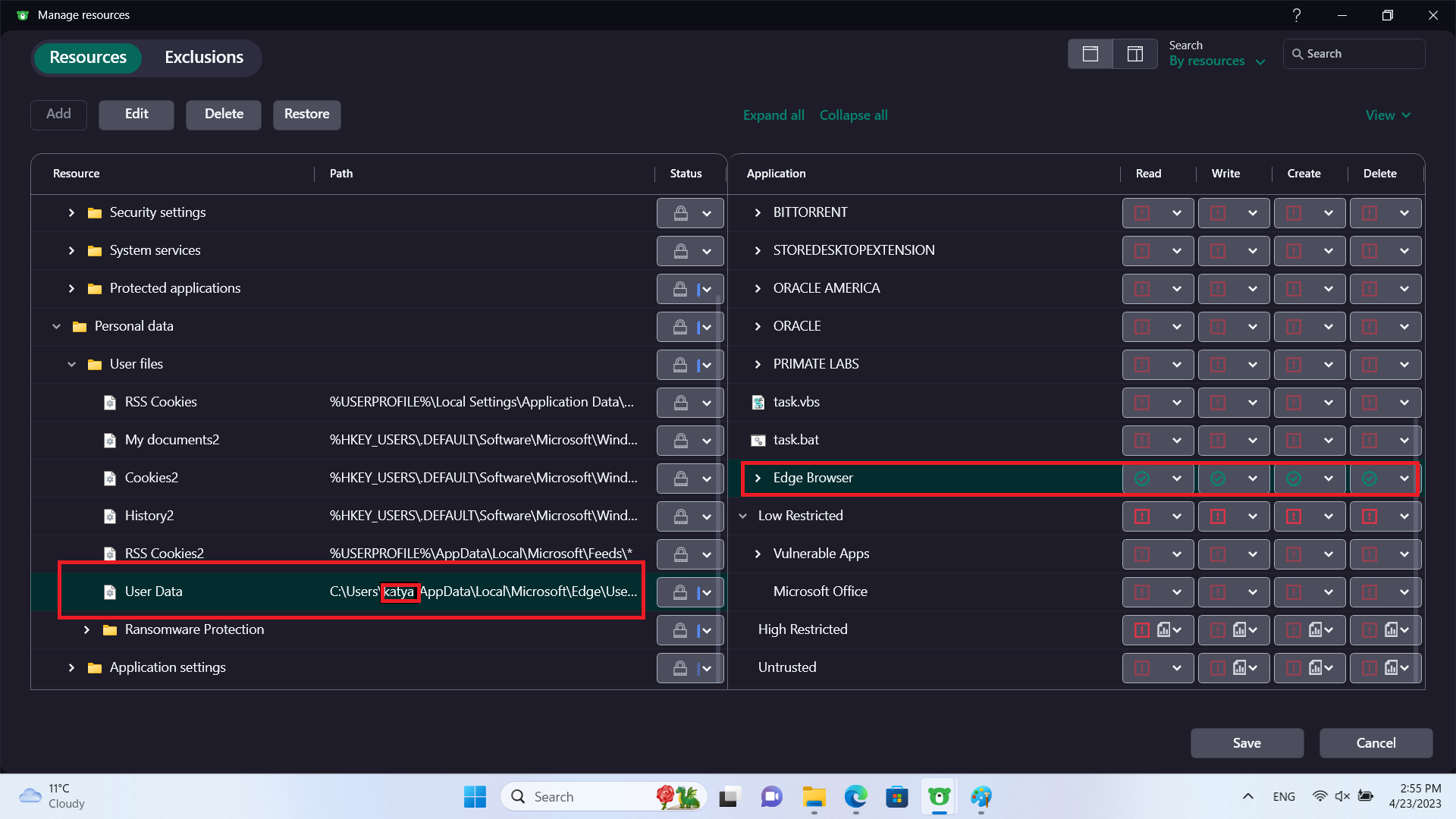
As shown above, we allow access to this directory for the Edge executables and block access by anything else, even if it is trusted.
This may prevent cleaners from accessing/deleting history and cookies. I advise against the usage of such software, browsers have cleaning abilities built-in.
Frequently, the space cleaned by such apps is less than the space they occupied and the data cleaned will be regenerated in a matter of hours.\
Similar steps can be taken for all apps that hold sensitive information (other browsers, password managers, crypto wallets).
We will then make sure important files are safe from ransomware.
Under resources, we'll add folders containing sensitive information.
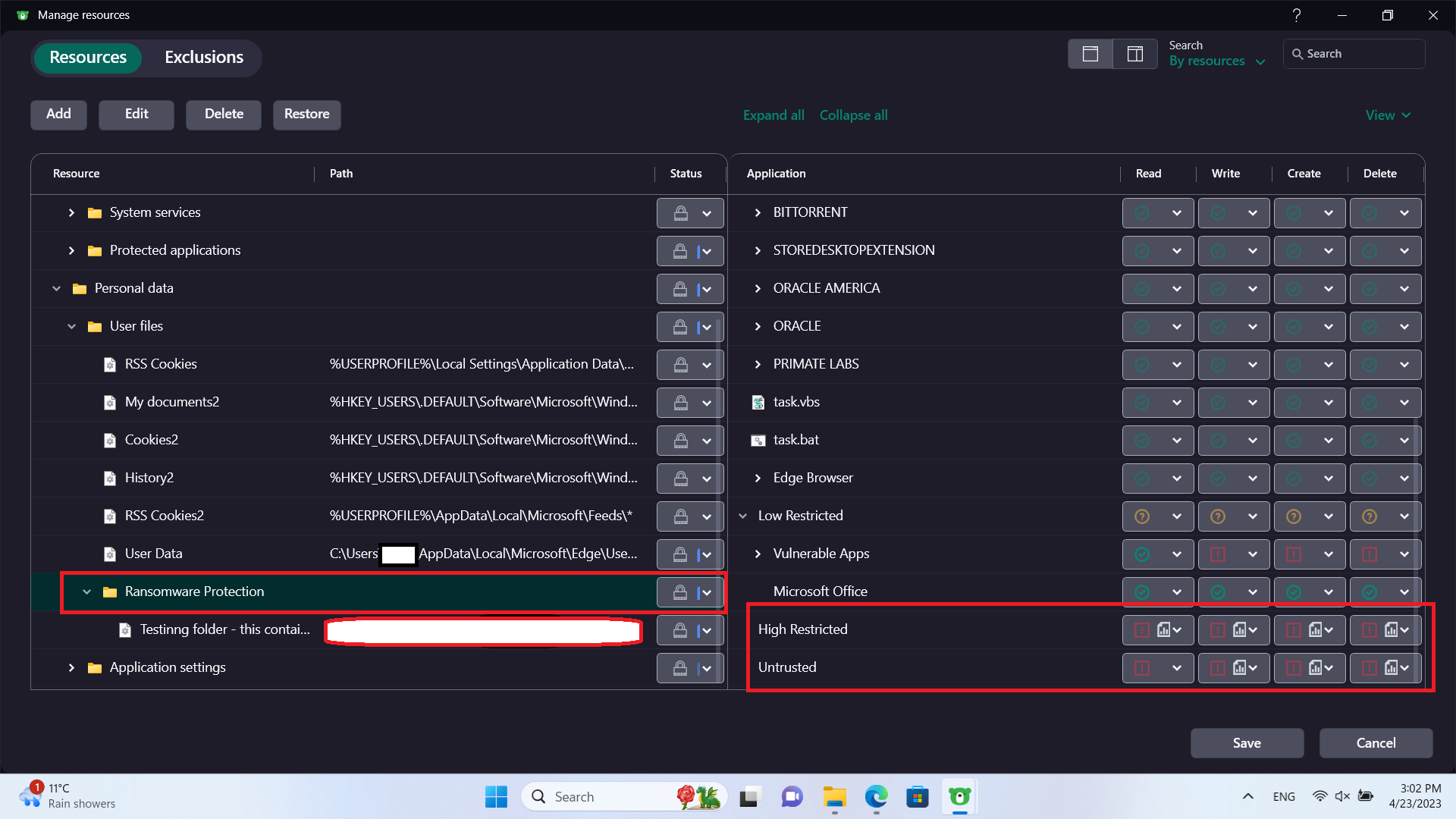
We'll make sure High Restricted apps and scripts don't have access to read or modify.
If they can't modify, they can't encrypt them either.
But what is an app/script performs code injection in a trusted process? We can block that too. Under Manage Applications, we can modify the rules:
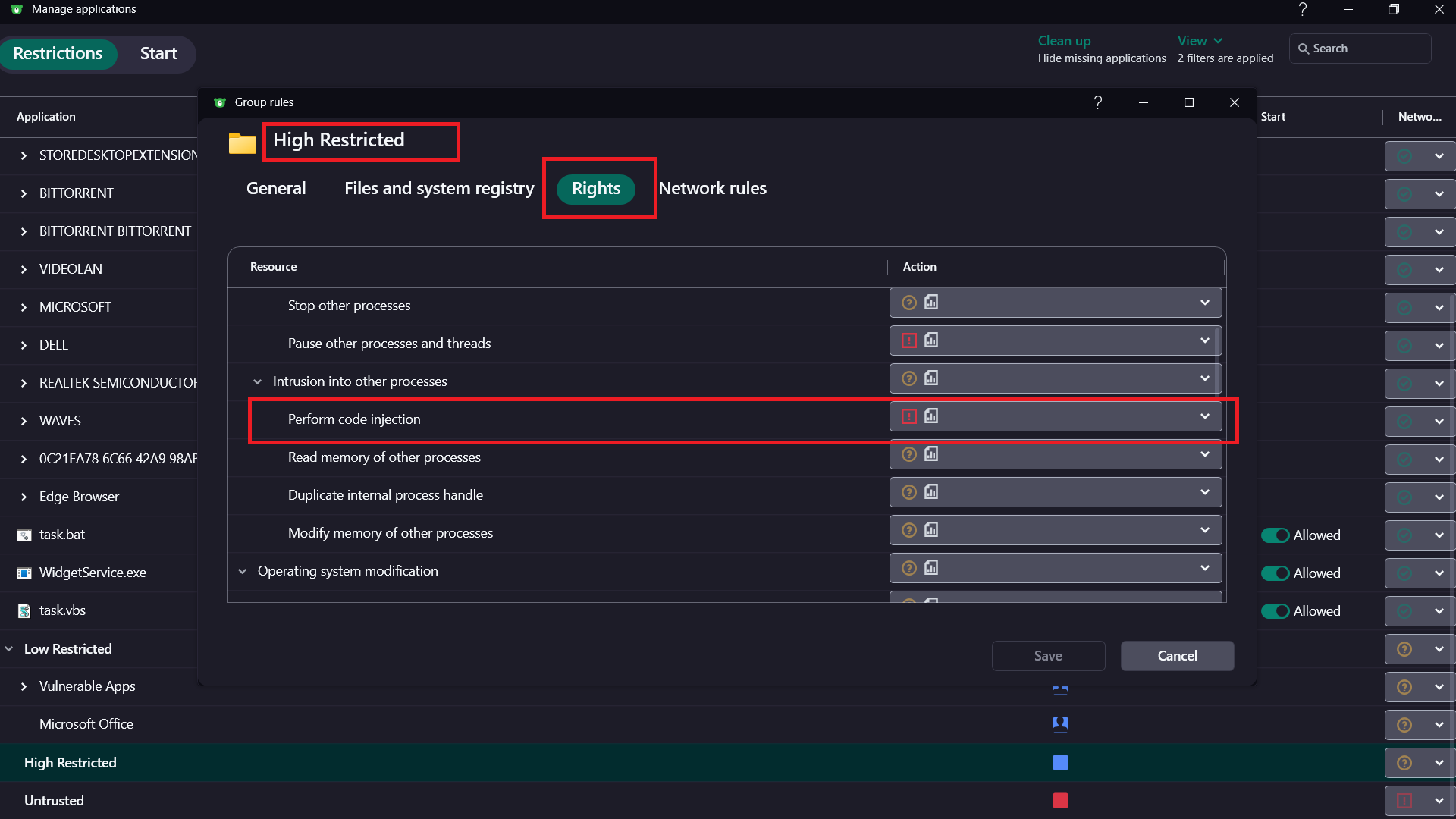
I highly recommend that in the same window, starting processes is disabled as well.
Next, we'll block execution of PowerShell 1.0 and Java. Java Runtime Environment must be installed prior to that.
For users who may wish to use some Java apps, various restrictions, such as disabling connection to the internet can be implemented.
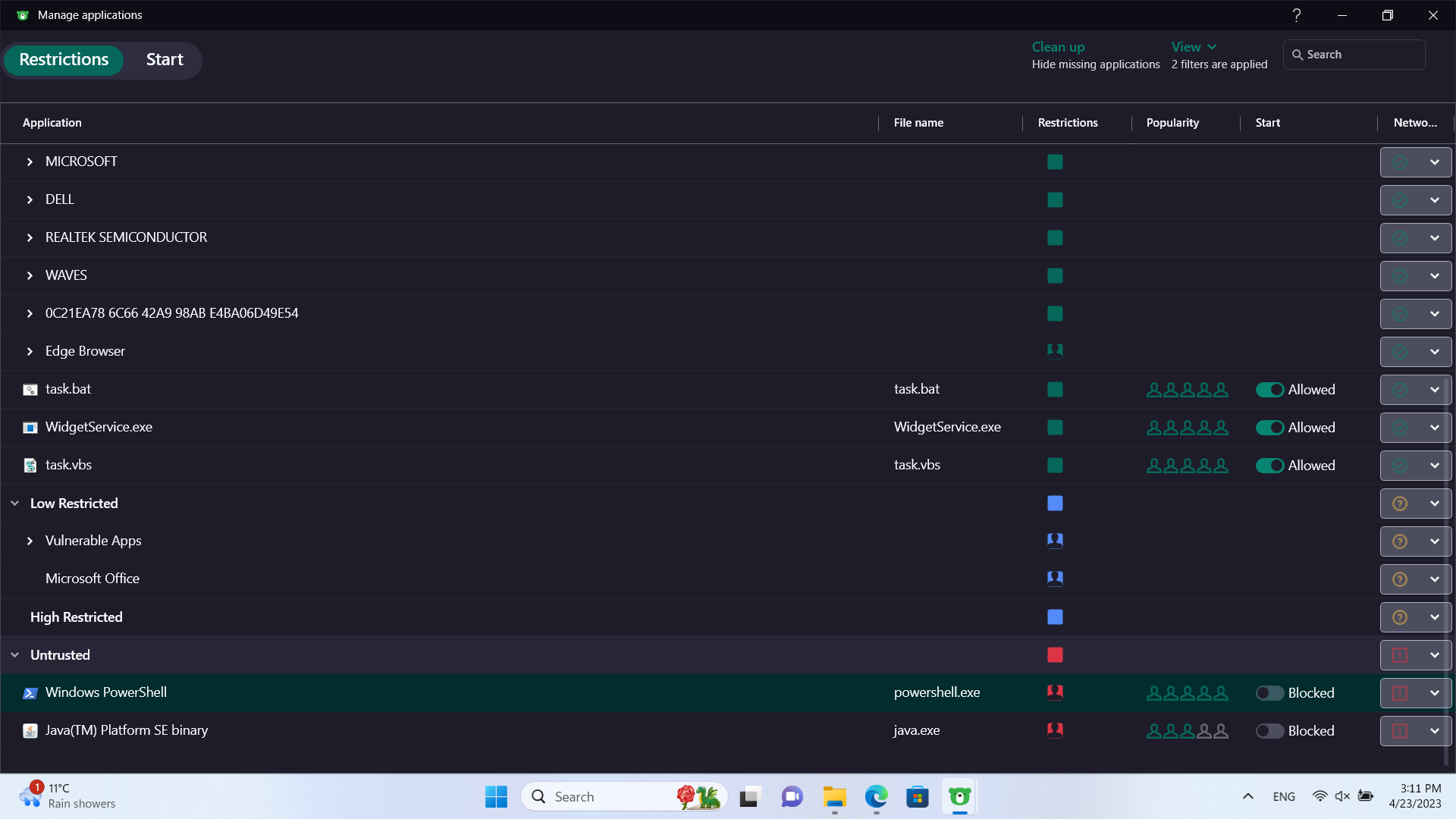
Under Untrusted, we'll add
Intrusion Prevention assigns trust to every object (script, program) individually and does not suffer issues where trust is assigned to the script interpretor, and all scripts can do whatever they decide.
For example, 5 *.bat files and 5 *.vbs scripts will have individual trust levels, based on the reputation Kaspersky has assigned to them. I tried many different Intrusion Prevention settings but a lot of them generated a sheer number of alerts & events. The most quiet and acceptable setups are 2 and displayed below:
Complete default-deny:
In this setup, it is impossible to execute code that has not undergone prior checks.
High-Restricted:
In this setup, code that has not undergone prior checks will be severely restricted.
Notice in both setups, I have unchecked "Trust digitally signed applications".
This will prevent code signing abuse
For more information on signed malware, I recommend looking here:

Understanding Code Signing Abuse in Malware Campaigns
Using a machine learning system, we analyzed 3 million software downloads, and provide insights in this three-part blog series. In this part of this series, we discuss the problems regarding code signing abuse.
Moving on, we will protect browser passwords and more crucially, session cookies from being accessed by anything else, apart from the browser itself.
For example, only Edge will have access to the Edge data folder.
To do this, we'll create a subgroup of trusted (under manage applications)
Under this group, we'll add the following:
Next, we under resources to add the Edge repository located at:
C:\Users\<AccountName>\AppData\Local\Microsoft\Edge\User Data
As shown above, we allow access to this directory for the Edge executables and block access by anything else, even if it is trusted.
This may prevent cleaners from accessing/deleting history and cookies. I advise against the usage of such software, browsers have cleaning abilities built-in.
Frequently, the space cleaned by such apps is less than the space they occupied and the data cleaned will be regenerated in a matter of hours.\
Similar steps can be taken for all apps that hold sensitive information (other browsers, password managers, crypto wallets).
We will then make sure important files are safe from ransomware.
Under resources, we'll add folders containing sensitive information.
We'll make sure High Restricted apps and scripts don't have access to read or modify.
If they can't modify, they can't encrypt them either.
But what is an app/script performs code injection in a trusted process? We can block that too. Under Manage Applications, we can modify the rules:
I highly recommend that in the same window, starting processes is disabled as well.
Next, we'll block execution of PowerShell 1.0 and Java. Java Runtime Environment must be installed prior to that.
For users who may wish to use some Java apps, various restrictions, such as disabling connection to the internet can be implemented.
Under Untrusted, we'll add
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
This setup will need to be monitored for errors. As mentioned above, less error-prone setting will be to just block the connection (which won't prevent droppers). To prevent droppers as well, I suggest starting of processes, code injection and modification of startup settings are all blocked for these apps."C:\Program Files (x86)\Java\jre-1.8\bin\javaw.exe"
Watch the videos to see the performance impact and see a test of few cases handled by Intrustion Prevention.
I did a GeekBench 6 with Kaspersky enabled and disabled.
These are the results:
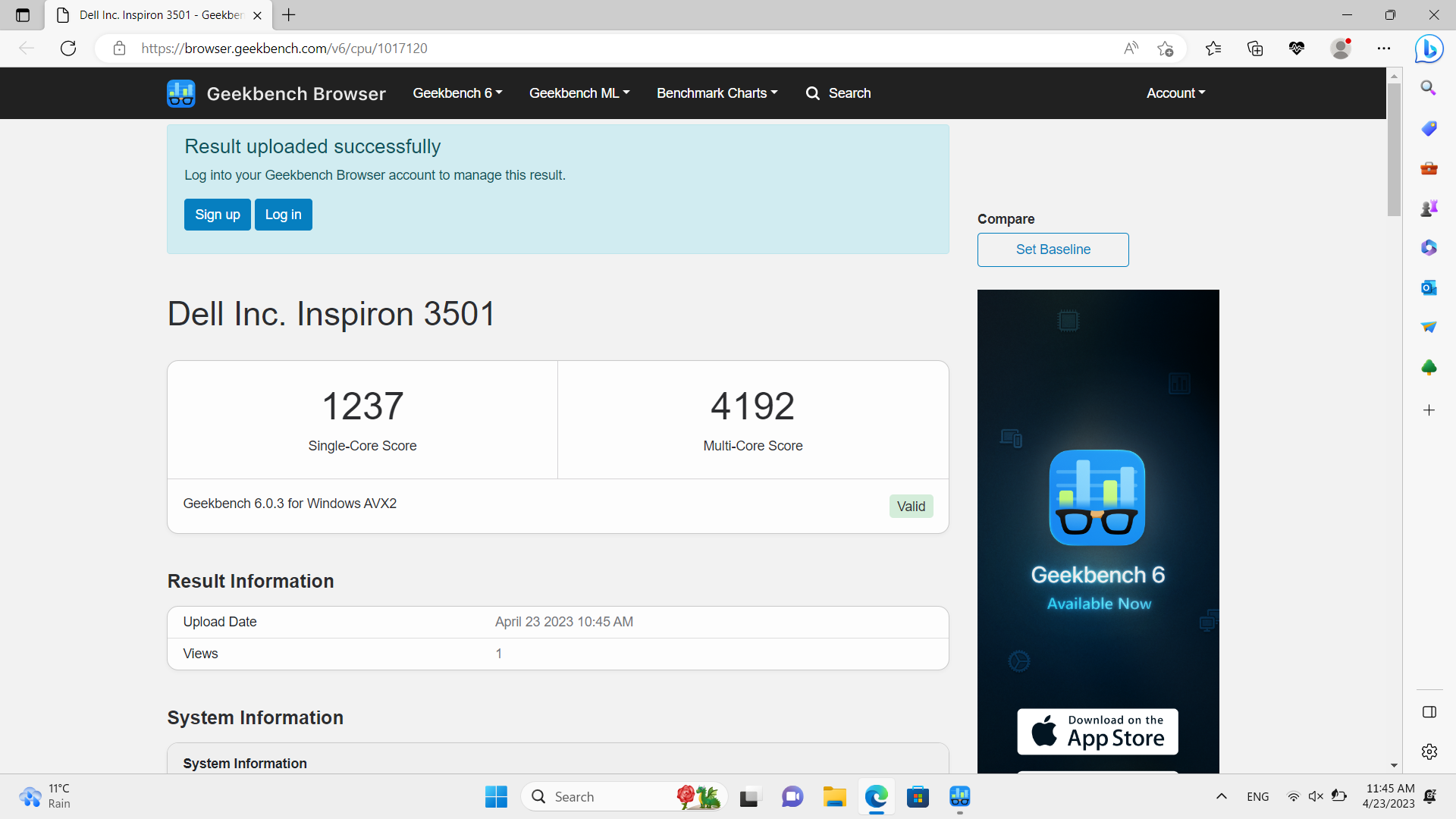
Enabled
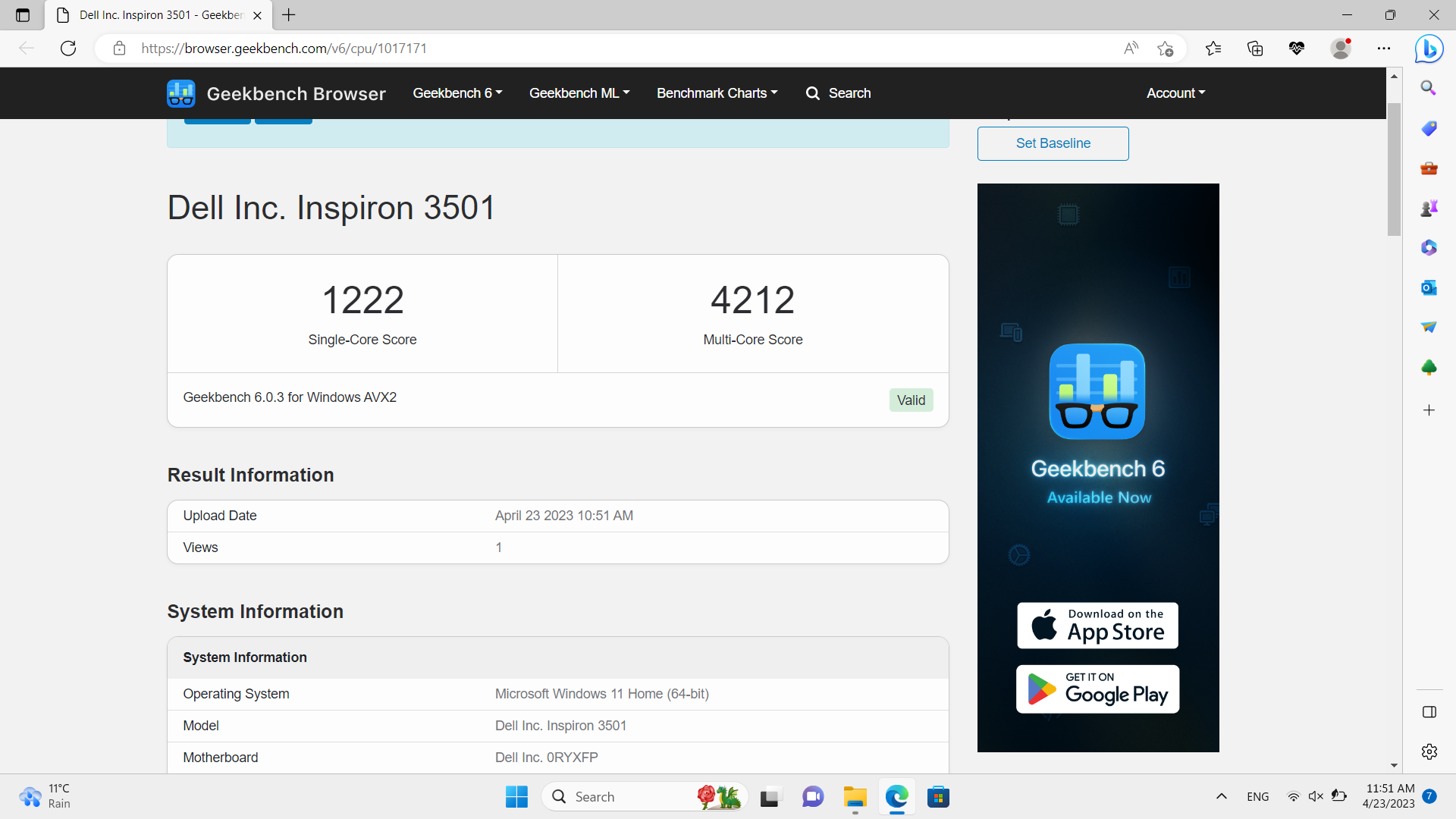
Disabled
I did a GeekBench 6 with Kaspersky enabled and disabled.
These are the results:
Enabled
Disabled
Last edited: