D
Deleted member 178
Thread author
ok, everybody here knows about malwares, Avs , etc... but there is an area we don't talk enough , datas protection.
One well known attack is called MITM aka Man In The Middle Attack:
Man-in-the-middle attack - Wikipedia
so what to do to counter it ?
basically you have to secure the transmission via encryption , for this we use the DNScrypt protocol:
DNSCrypt - Official Project Home Page
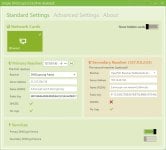
There is a simple apps called Simple DnsCrypt that will automatize and really simplify the implementation of this protocol
Simple DNSCrypt - Official Project Home Page
We will then choose from the list a DNS provider using DNSSEC.
DNSSEC – What Is It and Why Is It Important? - ICANN
Simple as that
Thanks for reading.
One well known attack is called MITM aka Man In The Middle Attack:
In cryptography and computer security, a man-in-the-middle attack (often abbreviated MitM, MiM attack, MitMA or the same using all capital letters) is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. A man-in-the-middle attack can be used against many cryptographic protocols.[1] One example of man-in-the-middle attacks is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within reception range of an unencrypted Wi-Fi wireless access point can insert himself as a man-in-the-middle.[2]
As an attack that aims at circumventing mutual authentication, or lack thereof, a man-in-the-middle attack can succeed only when the attacker can impersonate each endpoint to their satisfaction as expected from the legitimate other end. Most cryptographic protocols include some form of endpoint authentication specifically to prevent MITM attacks. For example, TLS can authenticate one or both parties using a mutually trusted certificate authority.[3]
Man-in-the-middle attack - Wikipedia
so what to do to counter it ?
basically you have to secure the transmission via encryption , for this we use the DNScrypt protocol:
DNSCrypt is a protocol that authenticates communications between a DNS client and a DNS resolver. It prevents DNS spoofing. It uses cryptographic signatures to verify that responses originate from the chosen DNS resolver and haven't been tampered with.
DNSCrypt - Official Project Home Page
There is a simple apps called Simple DnsCrypt that will automatize and really simplify the implementation of this protocol
Simple DNSCrypt - Official Project Home Page
We will then choose from the list a DNS provider using DNSSEC.
DNSSEC is a technology that was developed to, among other things, protect against such attacks by digitally 'signing' data so you can be assured it is valid. However, in order to eliminate the vulnerability from the Internet, it must be deployed at each step in the lookup from root zone to final domain name (e.g., www.icann.org). Signing the root (deploying DNSSEC on the root zone) is a necessary step in this overall processii. Importantly it does not encrypt data. It just attests to the validity of the address of the site you visit.
DNSSEC – What Is It and Why Is It Important? - ICANN
Simple as that
Thanks for reading.