No, I really have not had such an issue For any that are new to Comodo Firewall and will use it with Qihoo I would suggest the following:
1). Firewall- this would be the only big setting choice:
a. For those that want to be alerted when ANY application tries to connect out for the first time (and thus approved on a case by case basis)- set the Firewall to Custom Mode
b. For those that want to be alerted only to unknown applications connecting out, leave it in Safe Mode.
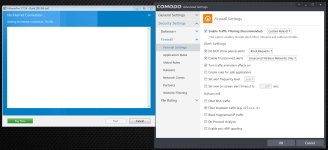
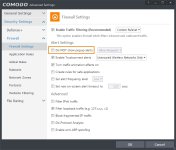
If you use Safe Mode, go into Firewall settings and check the "Do NOT show popup alerts" and change it to Block Requests. Do NOT do this if you use Custom Mode as you will already be deciding on Network access on a program by program basis.
2). Shut off HIPS (Qihoo is less noisy).
3). For those totally new to CF leave the Sandbox on Partially Limited. For those experienced, change sandbox setting to Untrusted (the current build 8.4.0.5165 now works with Windows 10).
That's it.
As anyone now reading this message is a security Geek (you can admit it- it's OK) It is going to be REALLY hard for you not to play with the other settings and do stuff like sandbox browsers (Geeks have NEVER seen a optional setting that they (we) don't want to check; but don't do it!!! It only will lead to frustration, and you have better things to obsess about (like what size emerald to get me for Christmas).
ps- There will be another Qihoo video released on Wednesday that will concentrate on Qihoo's mechanistic blocking routine.