Environment:
VMWare
Windows 10 LTSC 21H2
Windows Defender fully disabled (except for Windows Defender tests ofc)
4 GB RAM
No Internet
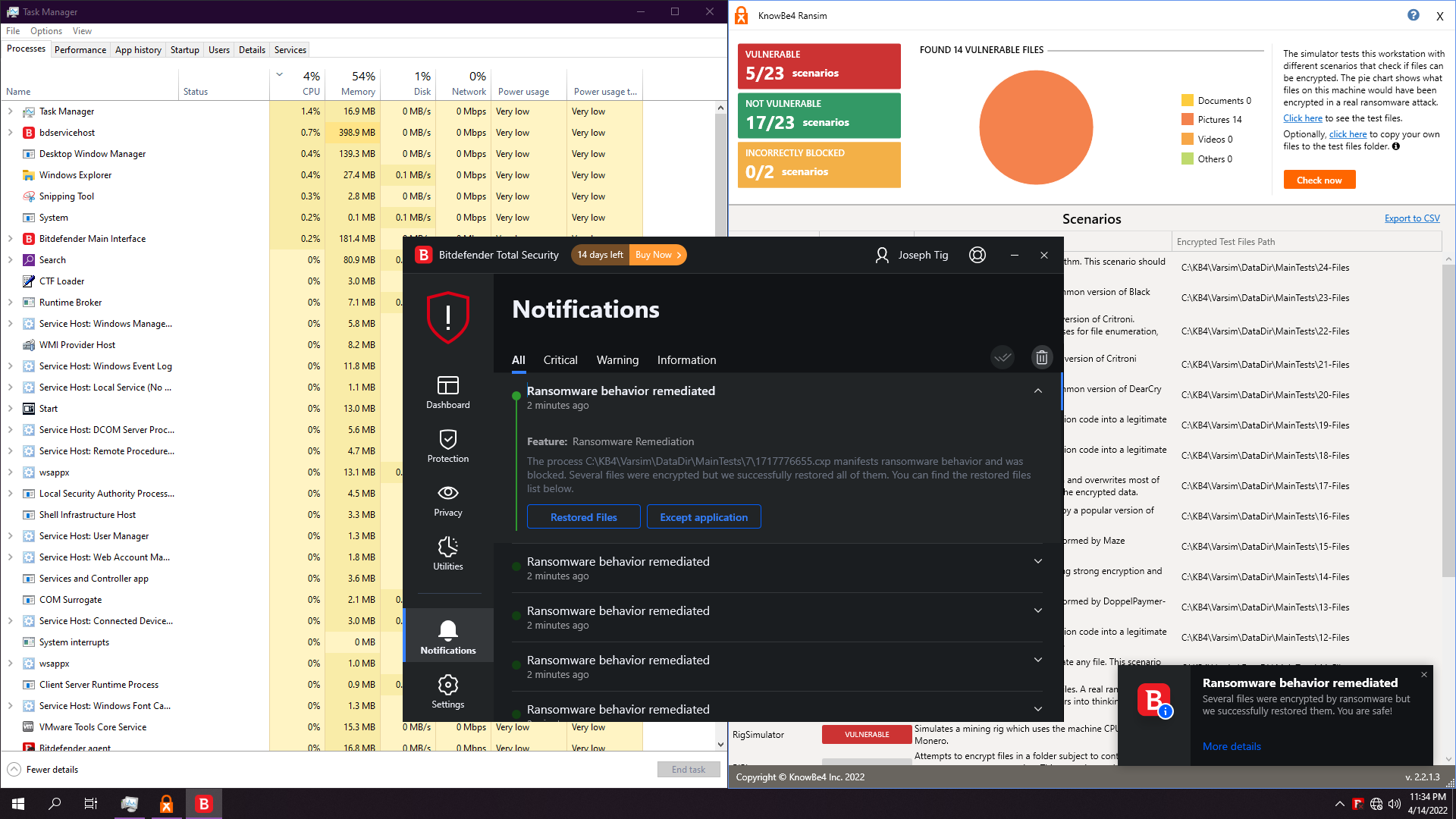
1. BitDefender Total Security 2022
Just Ransomware shield. ATP identifies the simulator, not the ransomwares itself, so we will just base the test on real behavioural shield, the ransomware remediation:
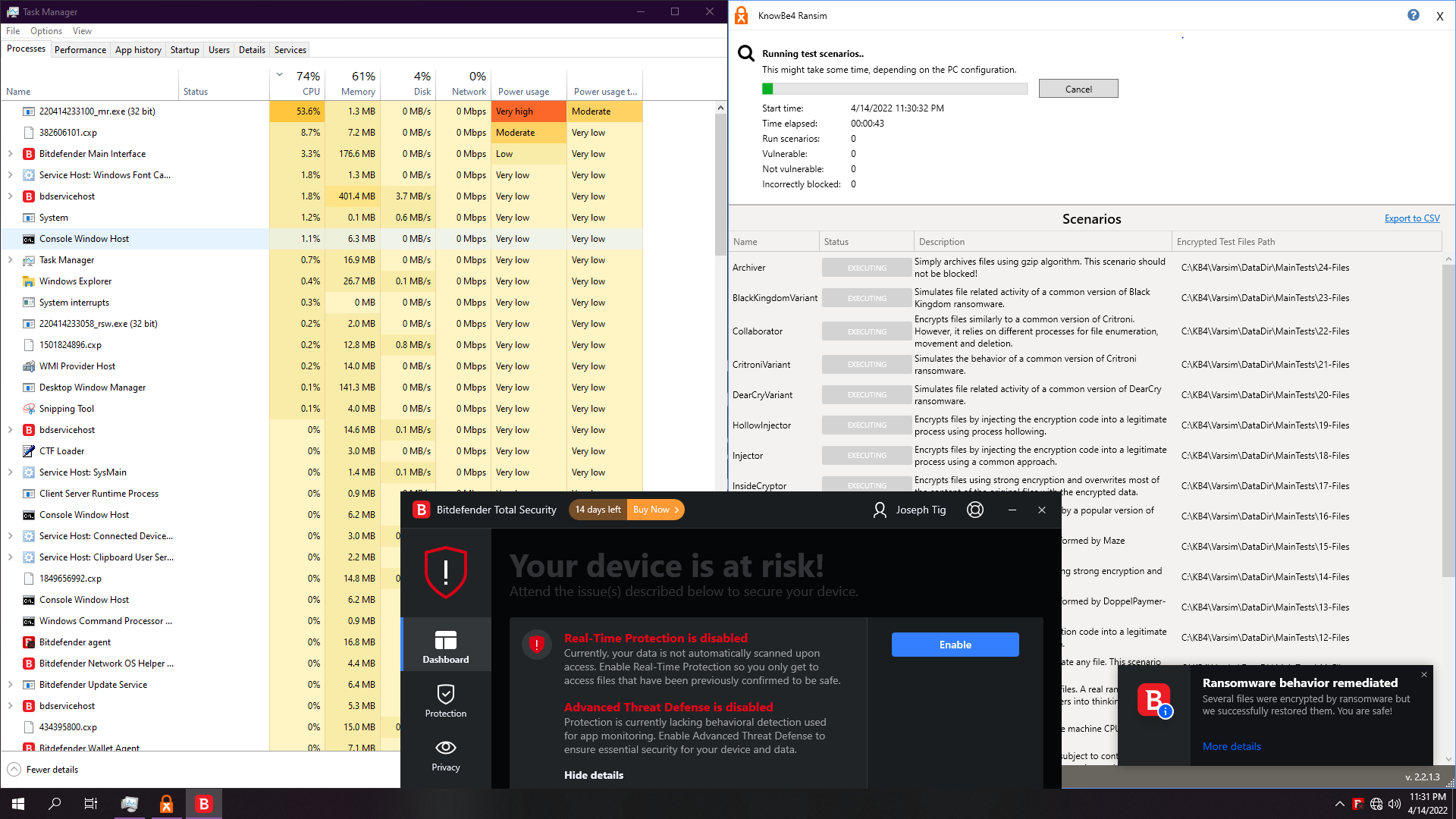
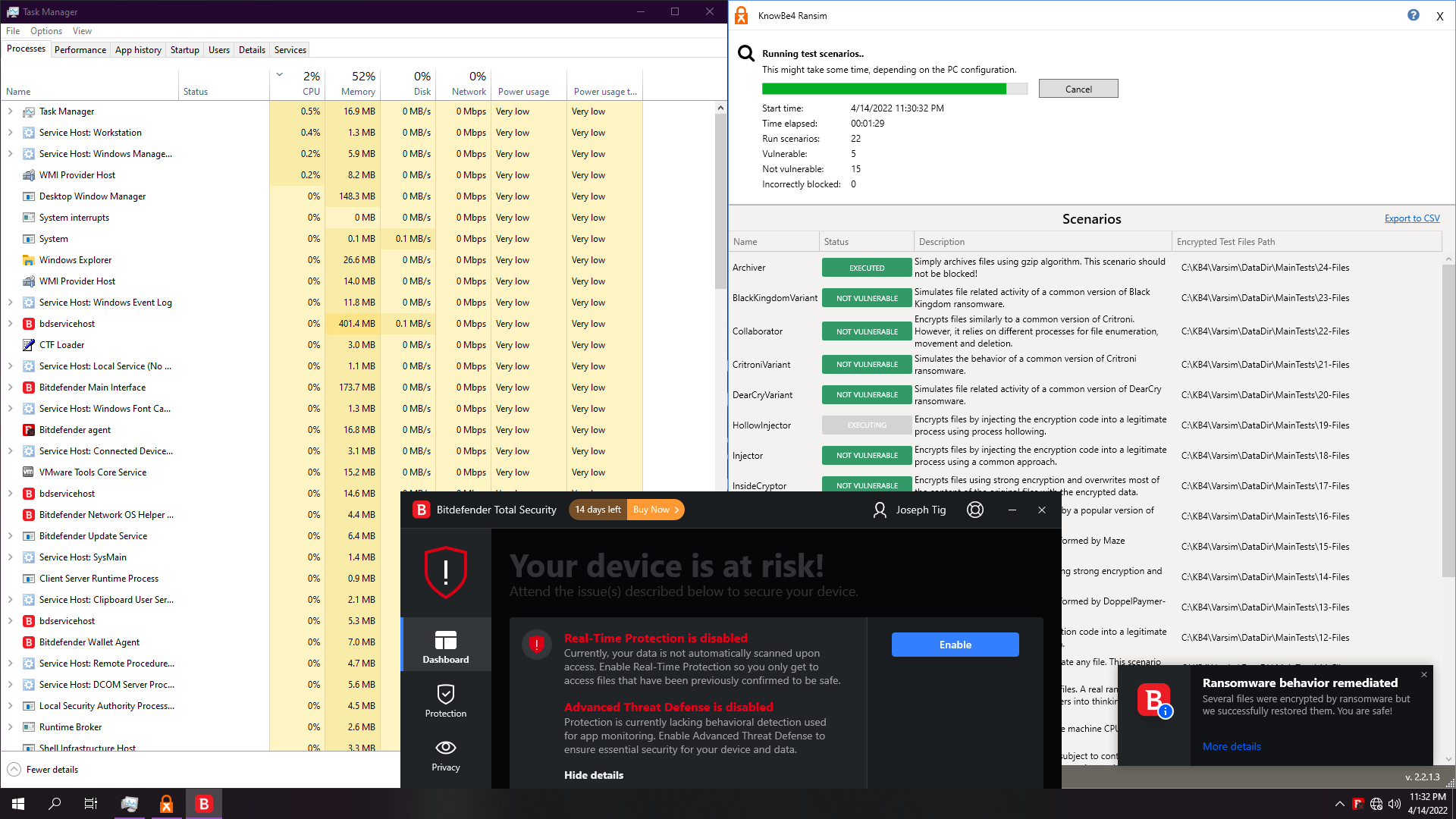
Test is pretty fast. About 1:30 min, and result is pretty good: 17/23 non vulnerable.
Resource usage however can be tremendous, having few moments when BD takes up over the ransomwares themselves.
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
2. Eset Internet Security
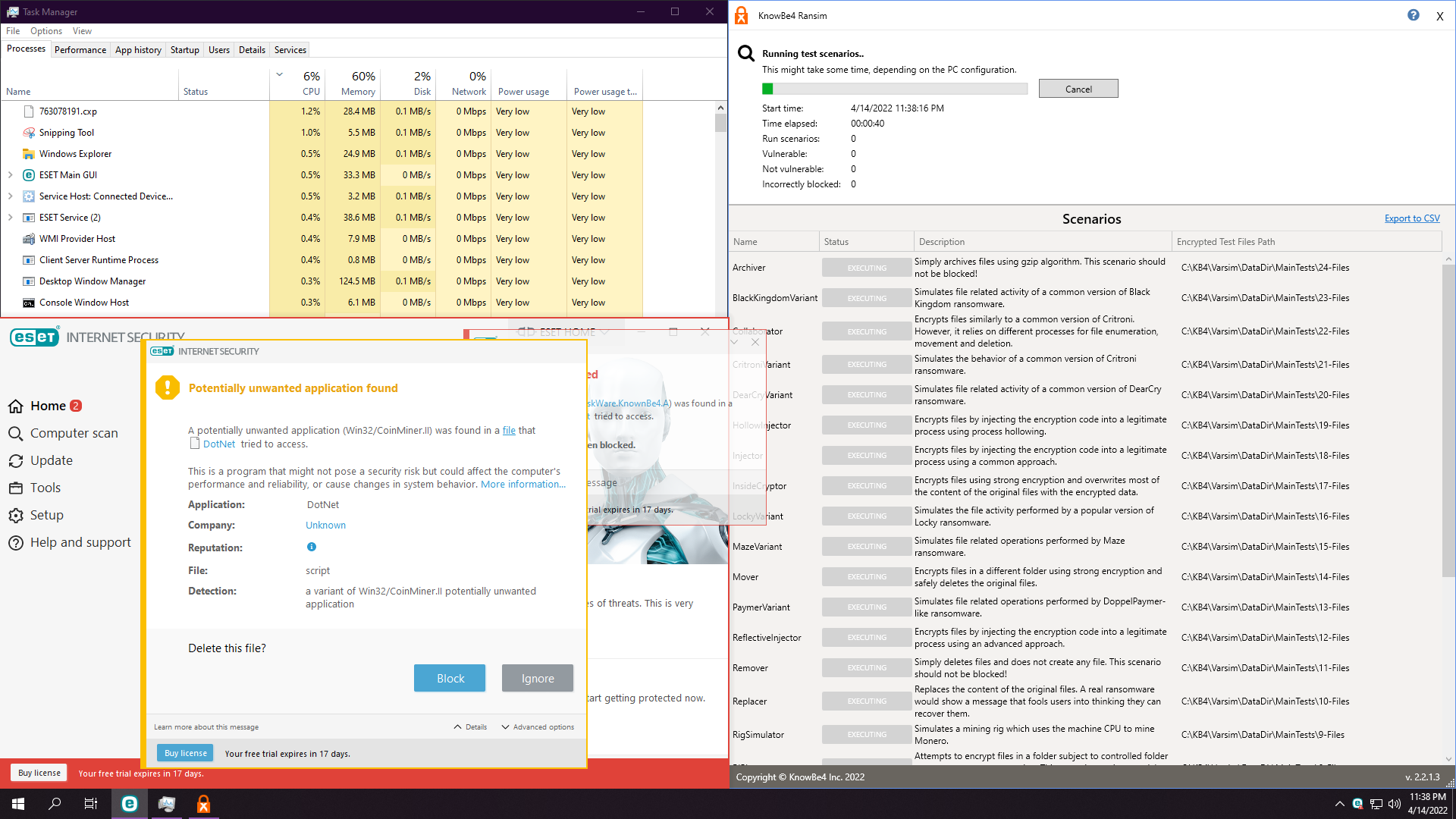
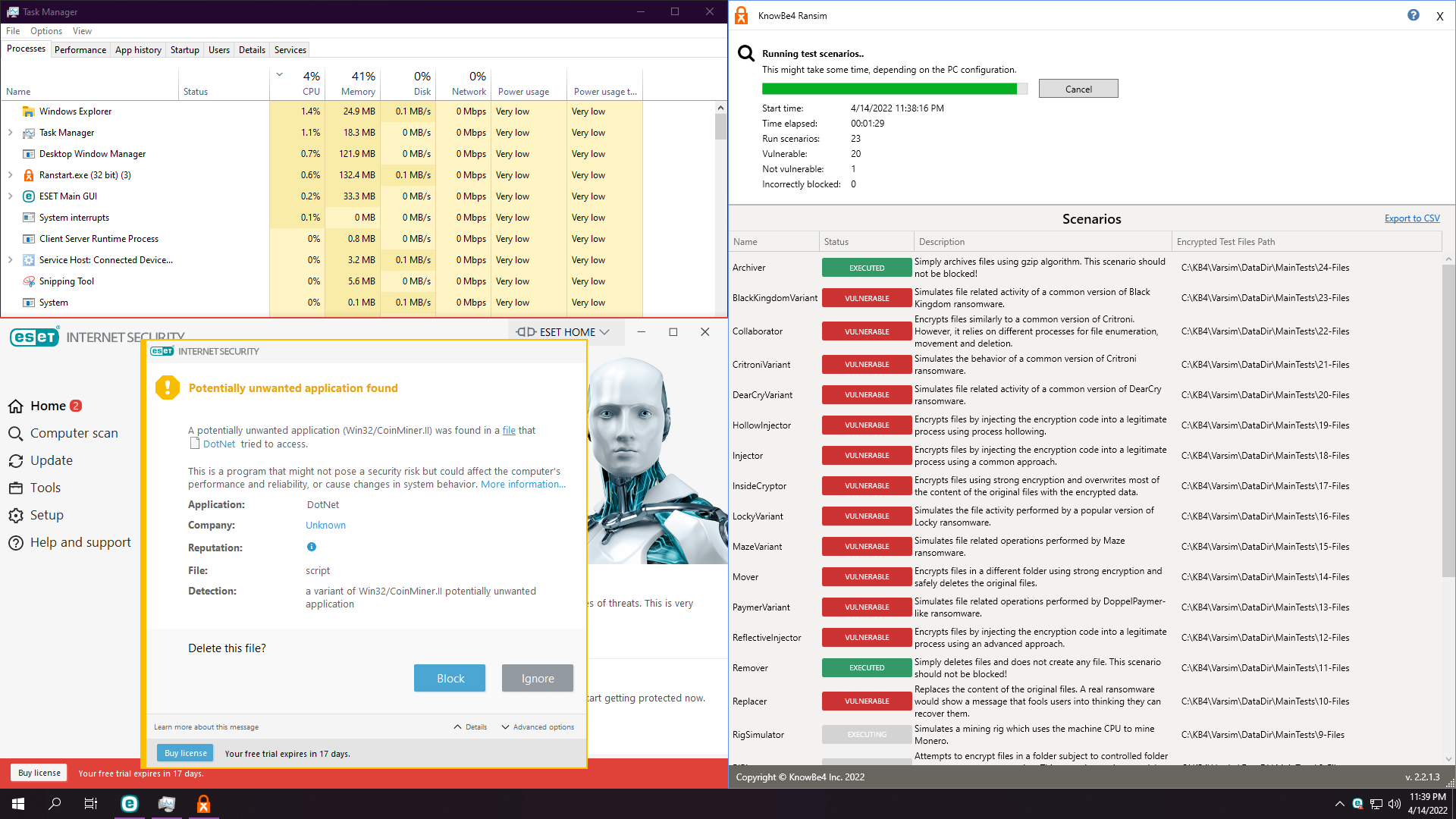
8 and 9 keep stuck. If we have a look at their folders, we didn't get ransomed. However, I have made this test a couple of times and results differ... Usually they do get ransomed, but hey, we got lucky this time.
We got popups, but we didn't interact with them.
Note: with custom settings from RoboMan (Q&A - Configure ESET Antivirus for Maximum Security (by RoboMan)), you would be overwhelmed by pop-ups. Will depend if you allow or block... But nothing automatic. And yeah, I forgot to disable Internet, but results are same for Eset.
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
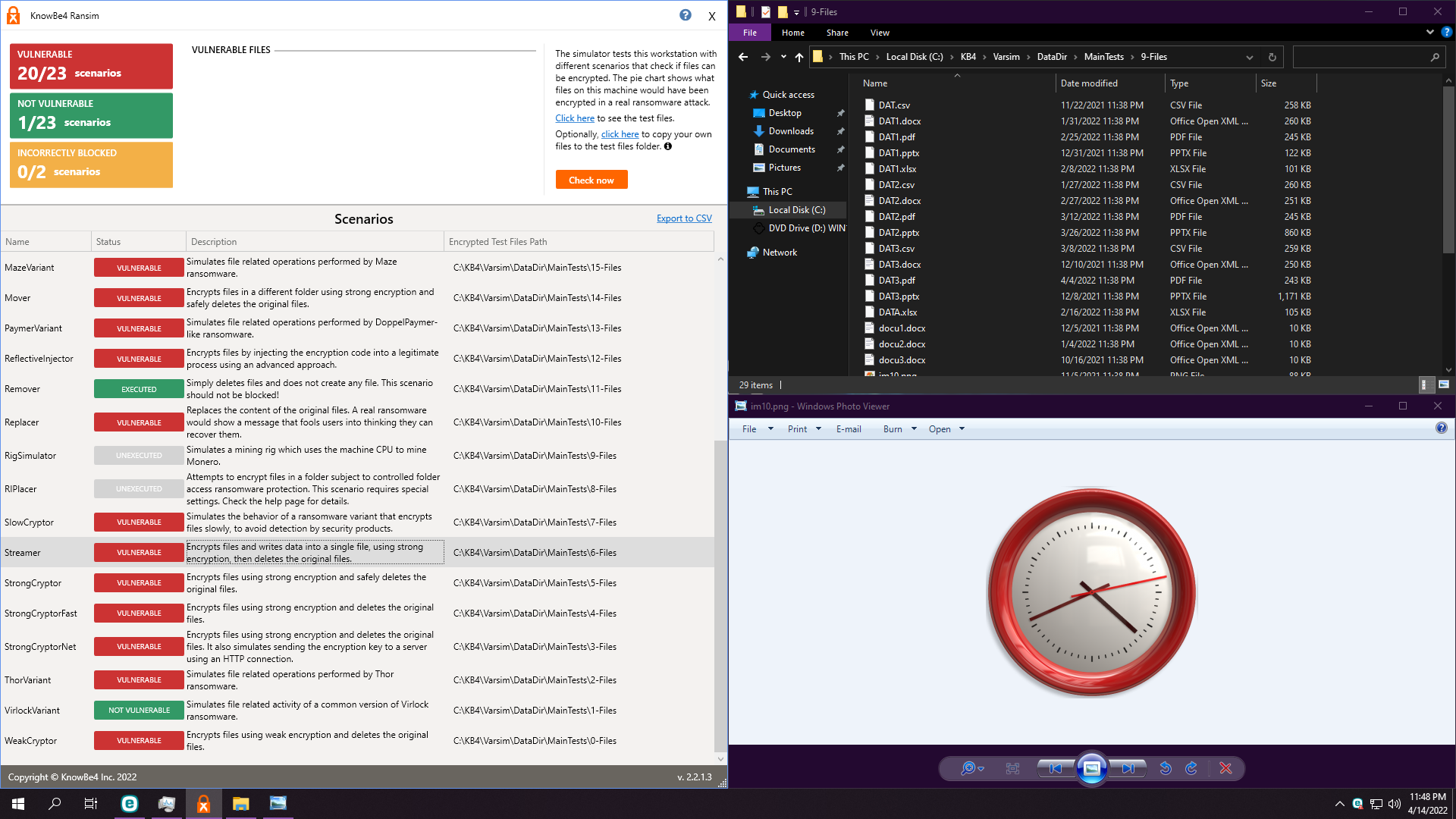
3. WiseVector StopX v306
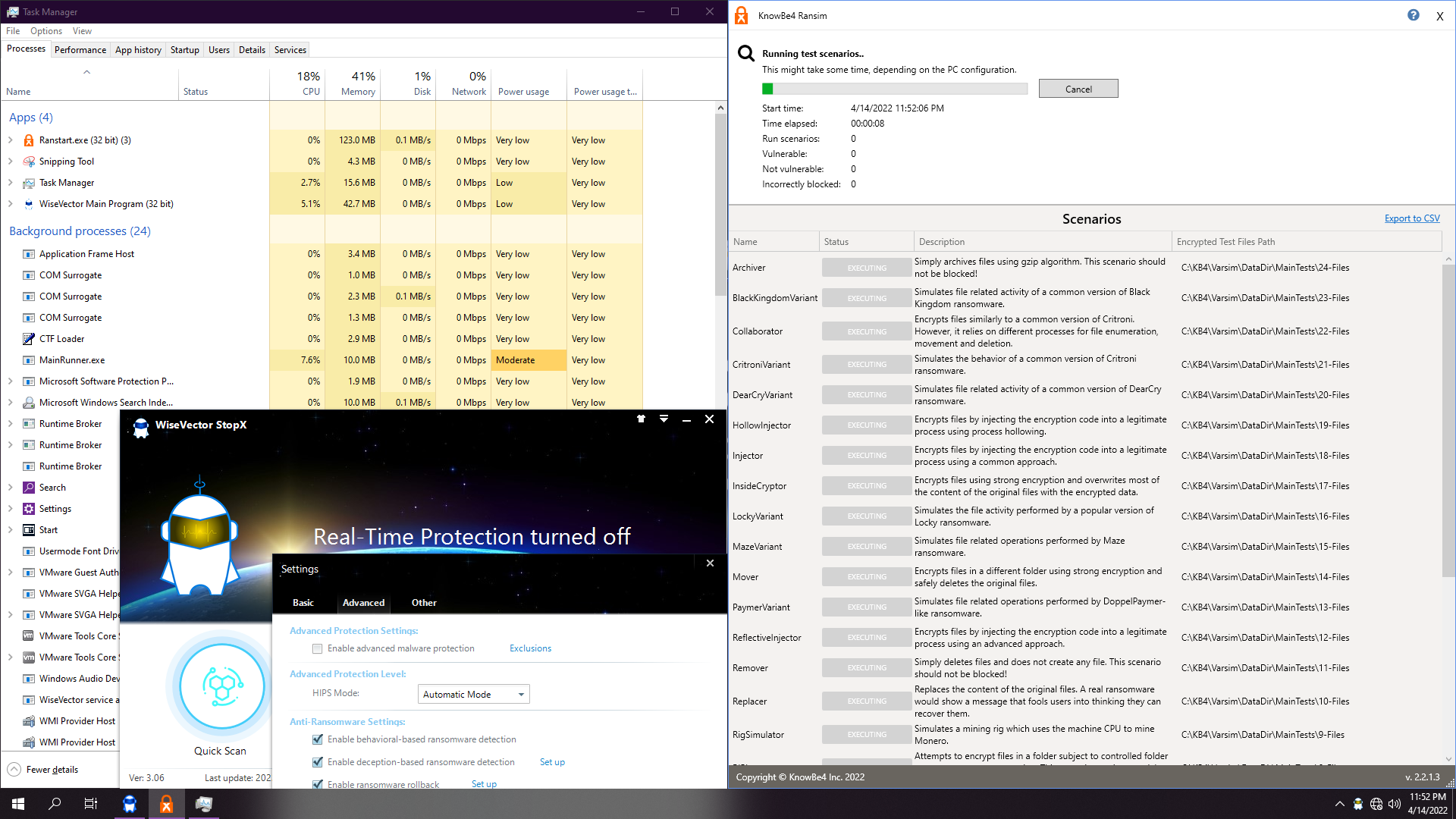
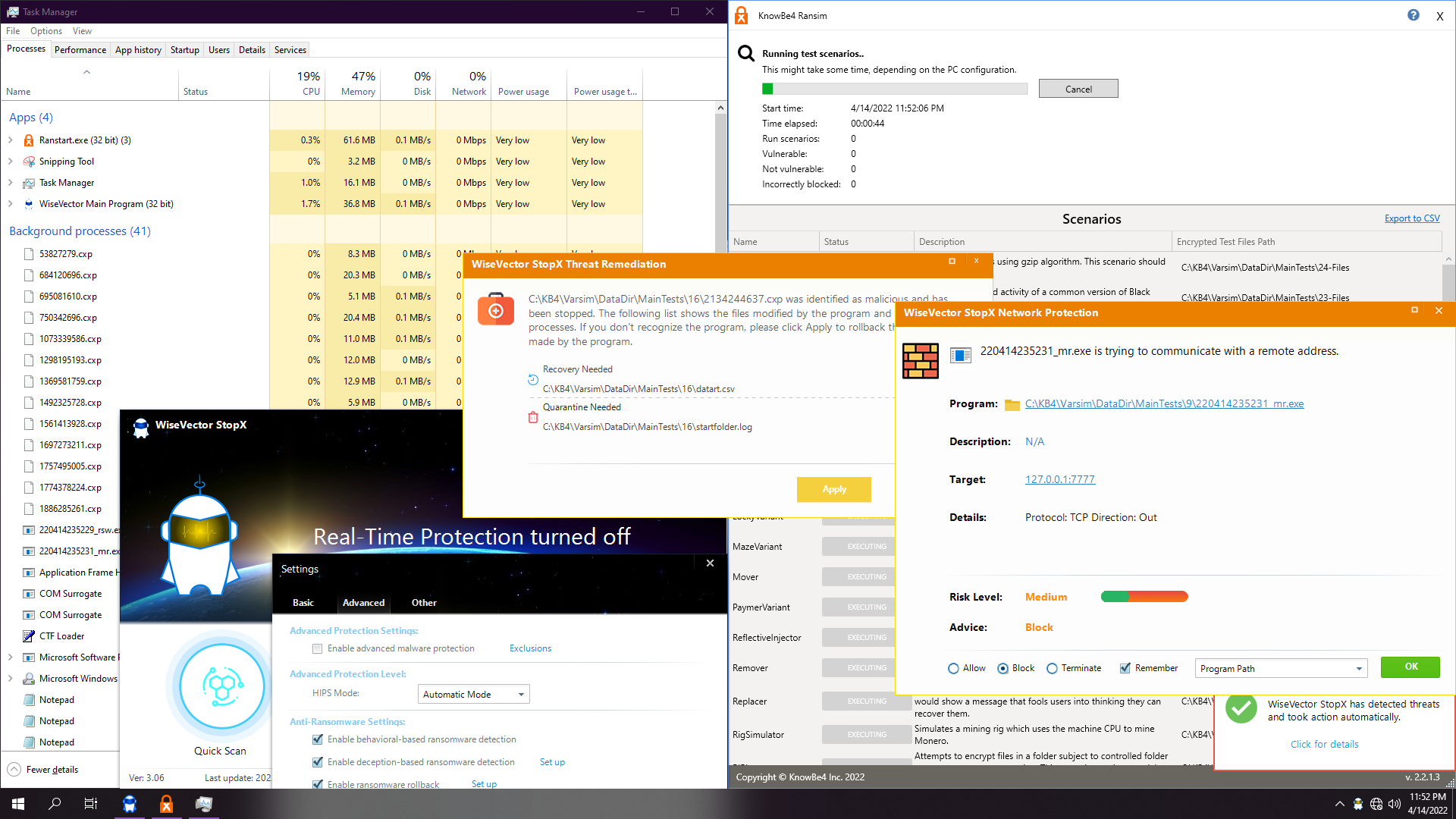
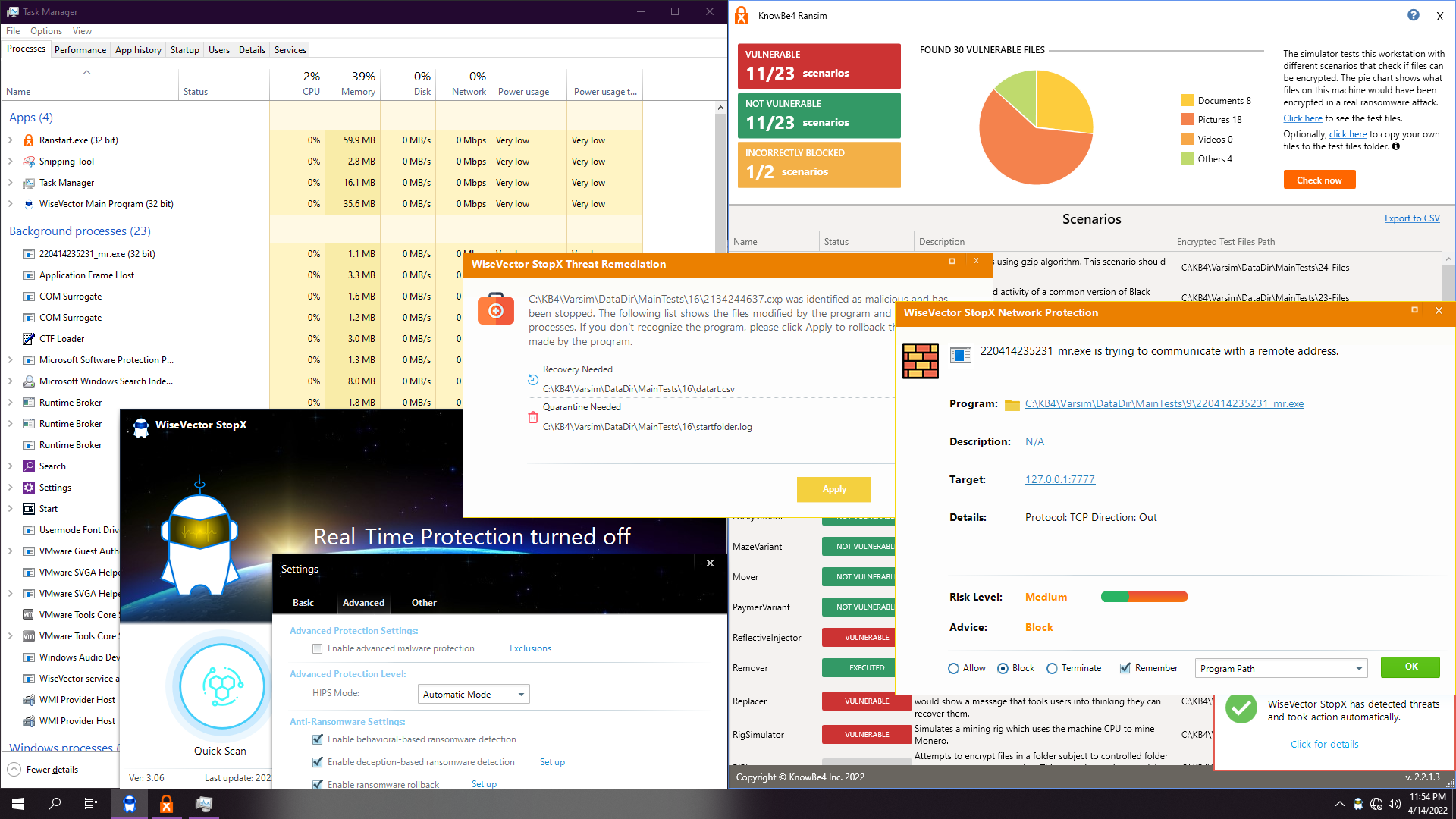
Depending on the ransom, it will autoremediate (16 as shown up here) or ask for recover (20 as shown down here):
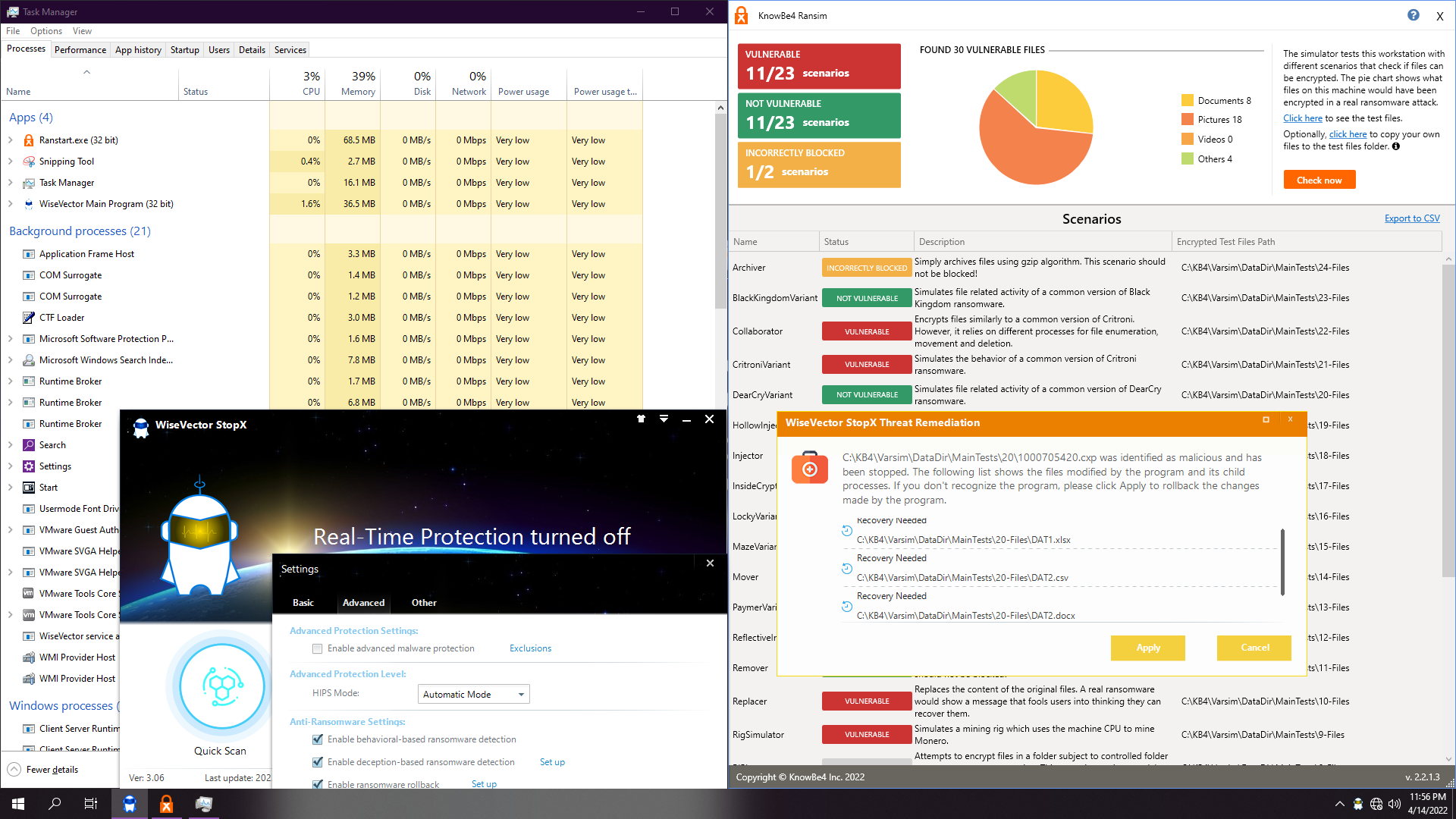
Test ends up soon, also about 1:30. Real-time protection and advanced malware protection are disabled. We just leave ransomware shields enabled and with default settings.
Result: 11 non vulnerable.
Note: very light on resources, similar to ESET.
Note 2: great improvement from V305 (WiseVector StopX vs 0-day ransomware (KnowBe4)). On equivalent conditions we were just protected of 4 ransom and just few days after, we got 11!!
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
4. Kaspersky Free 21.5
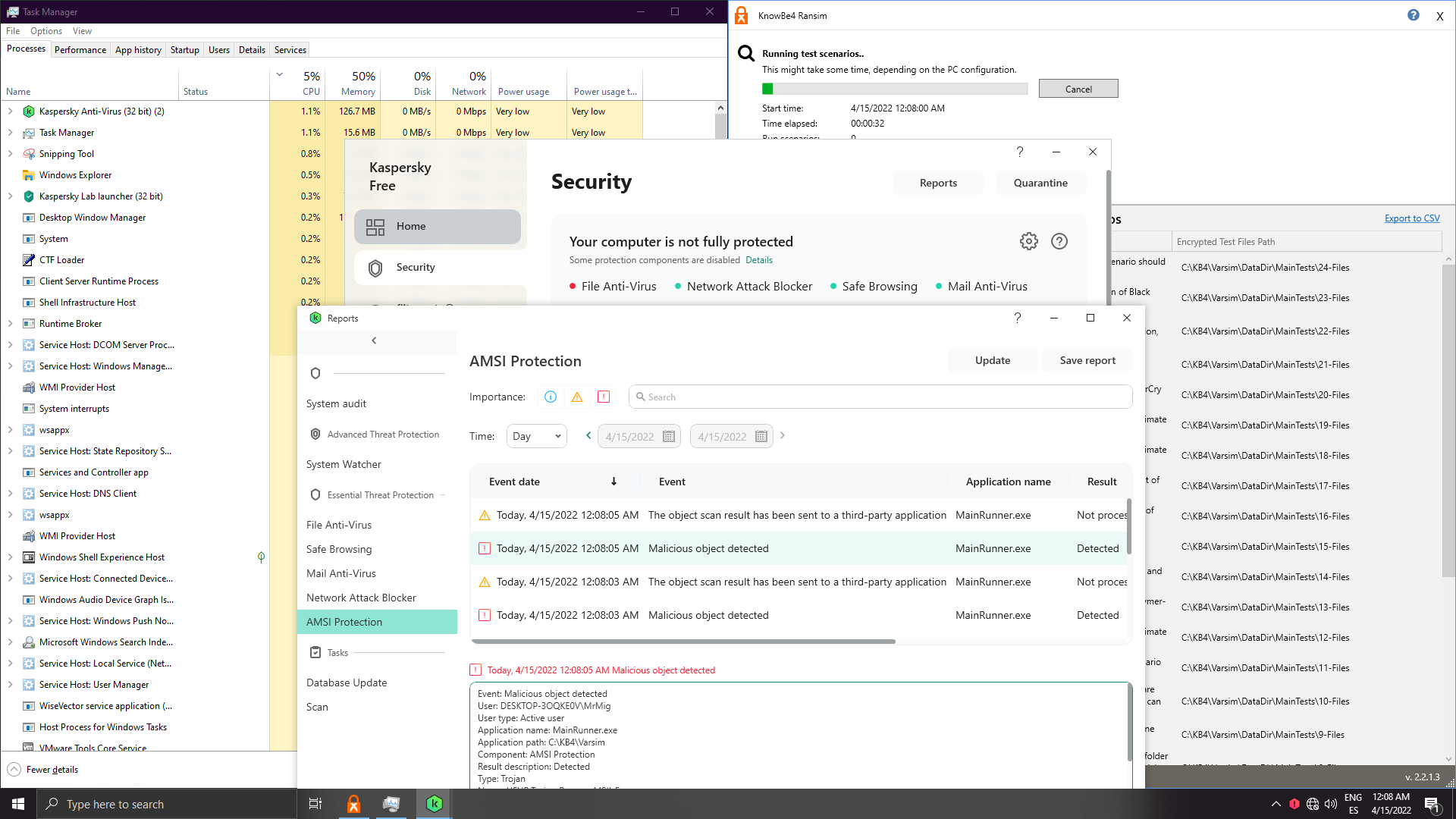
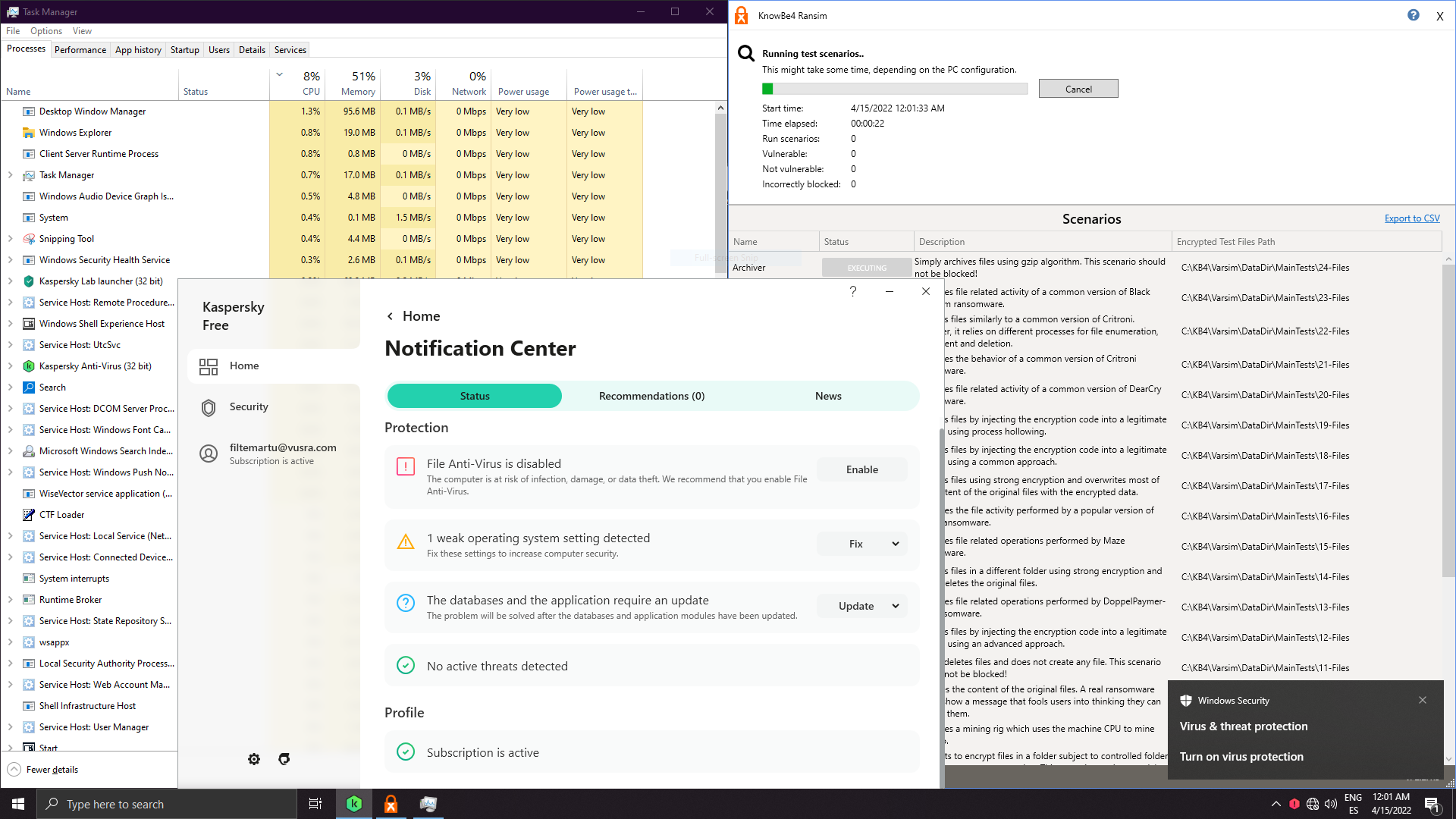
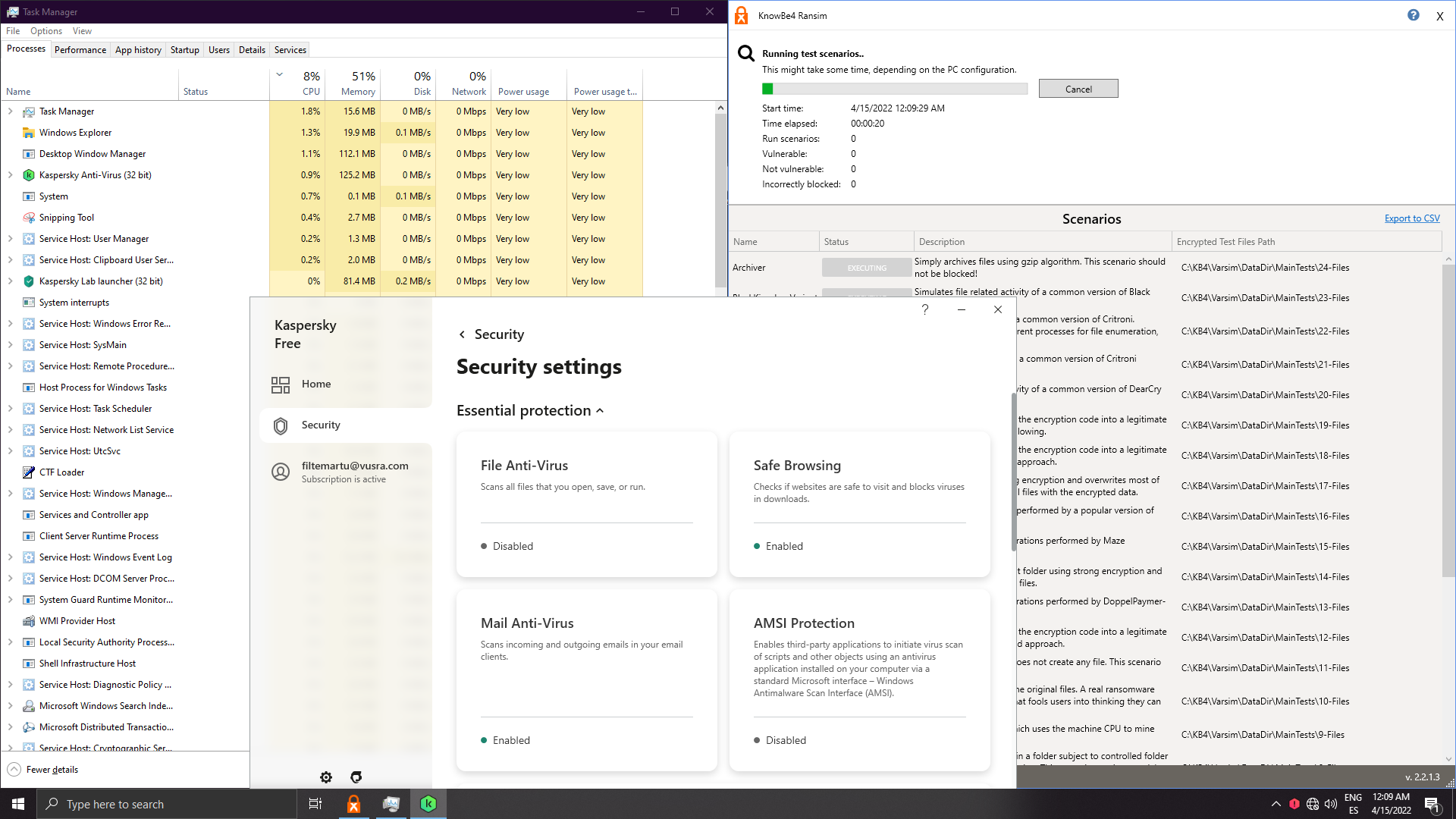
Let's disable AMSI and rely on system watcher:
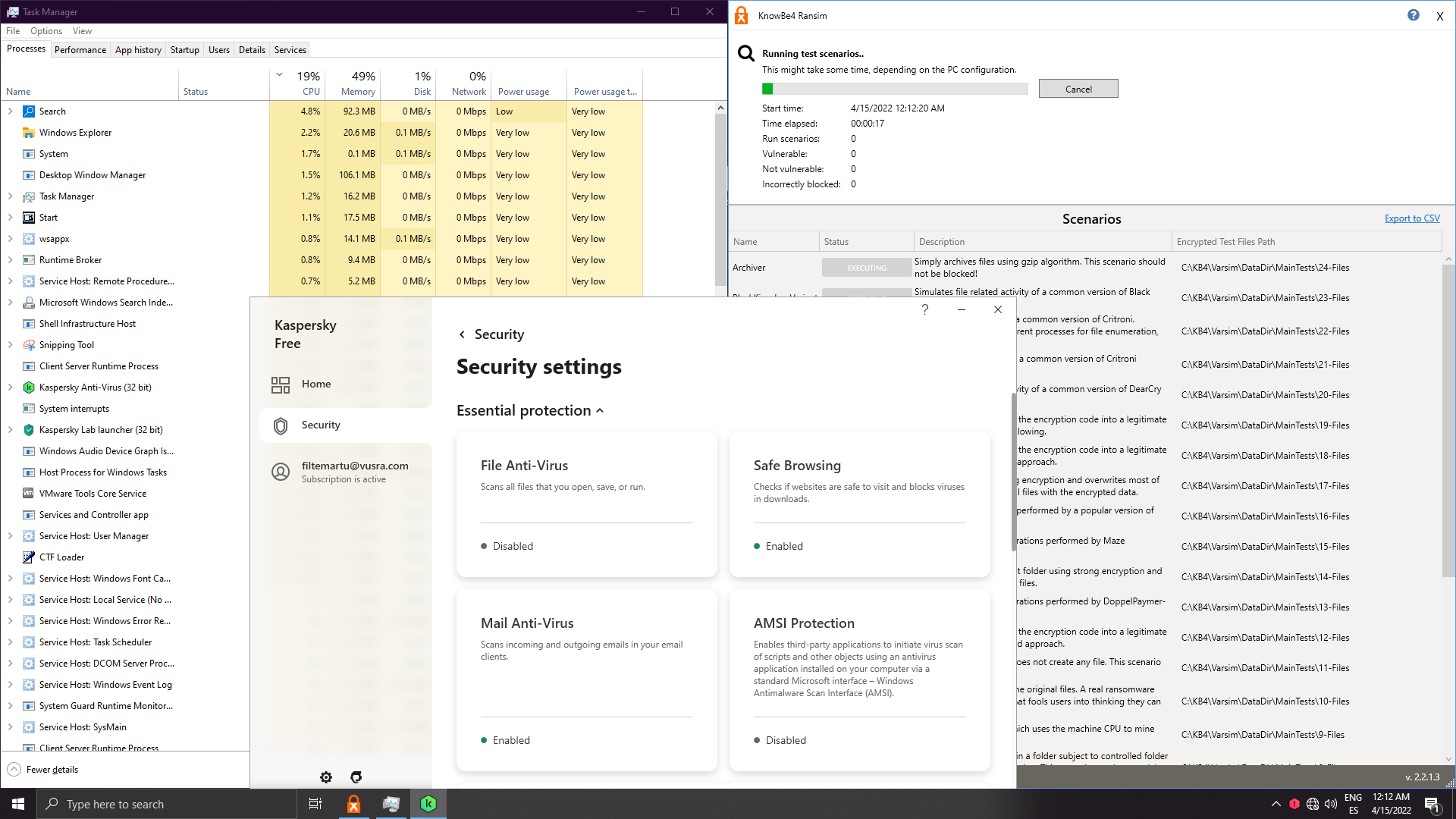
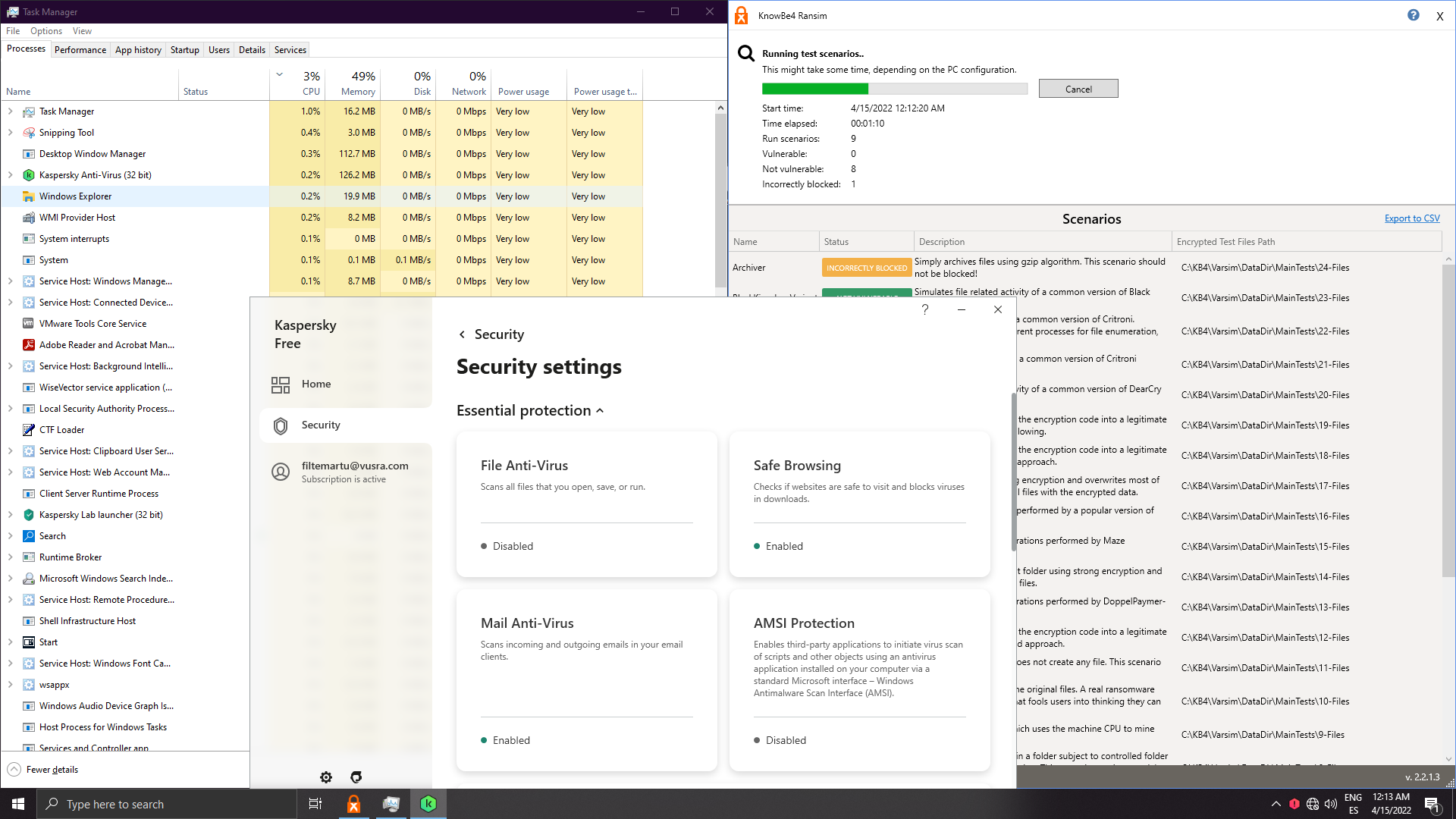
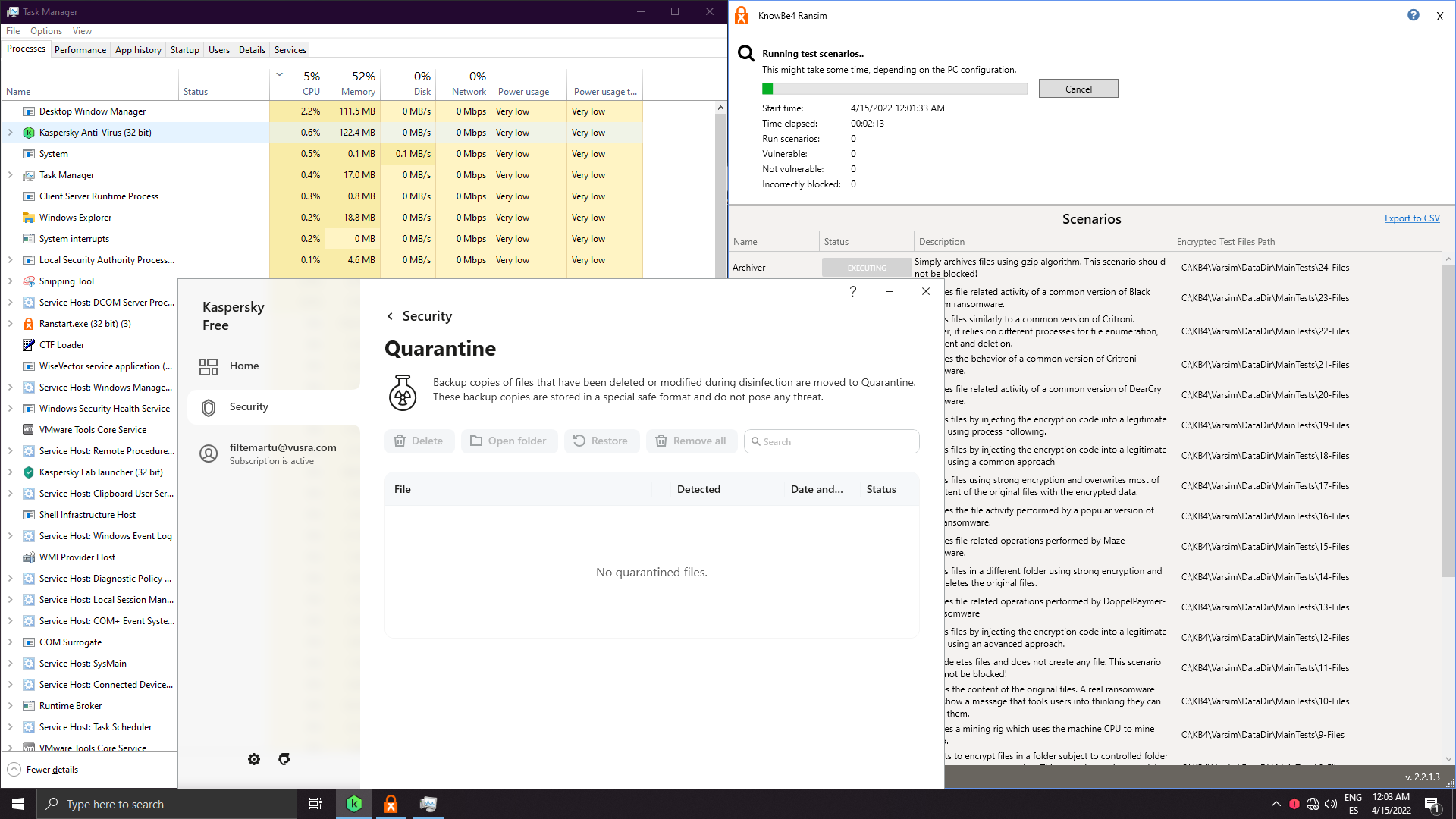
Surpringsily I can't find which component remediated the behaviour:
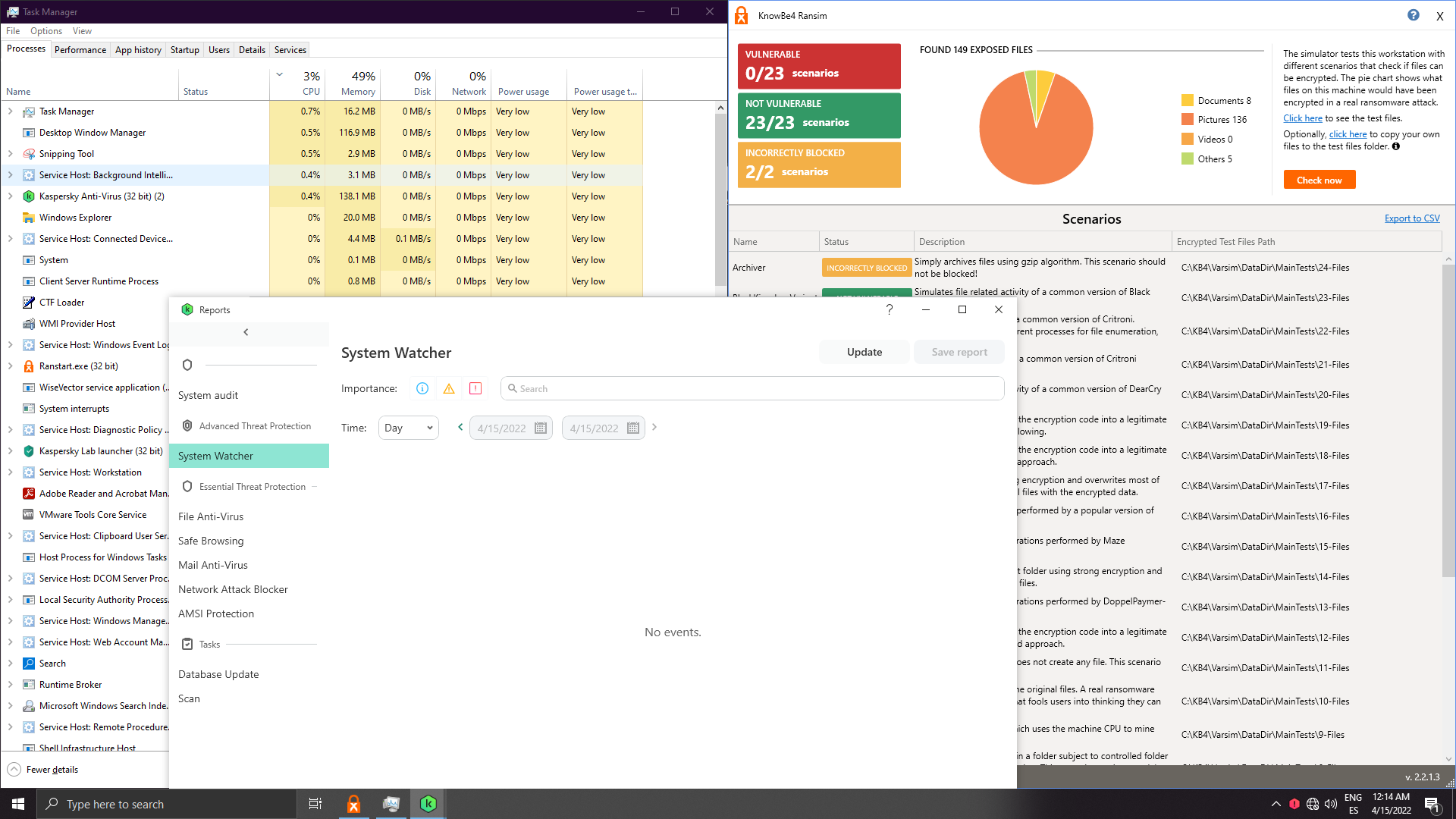
Threats aren't loaded in memory, system is clean, but is it really remediated or is it preblocked? On the past I remember I got system watcher popups and I could see cxp loading, but not anymore...
Result: FULLY CLEAN
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
5. F-Secure Safe 18.5
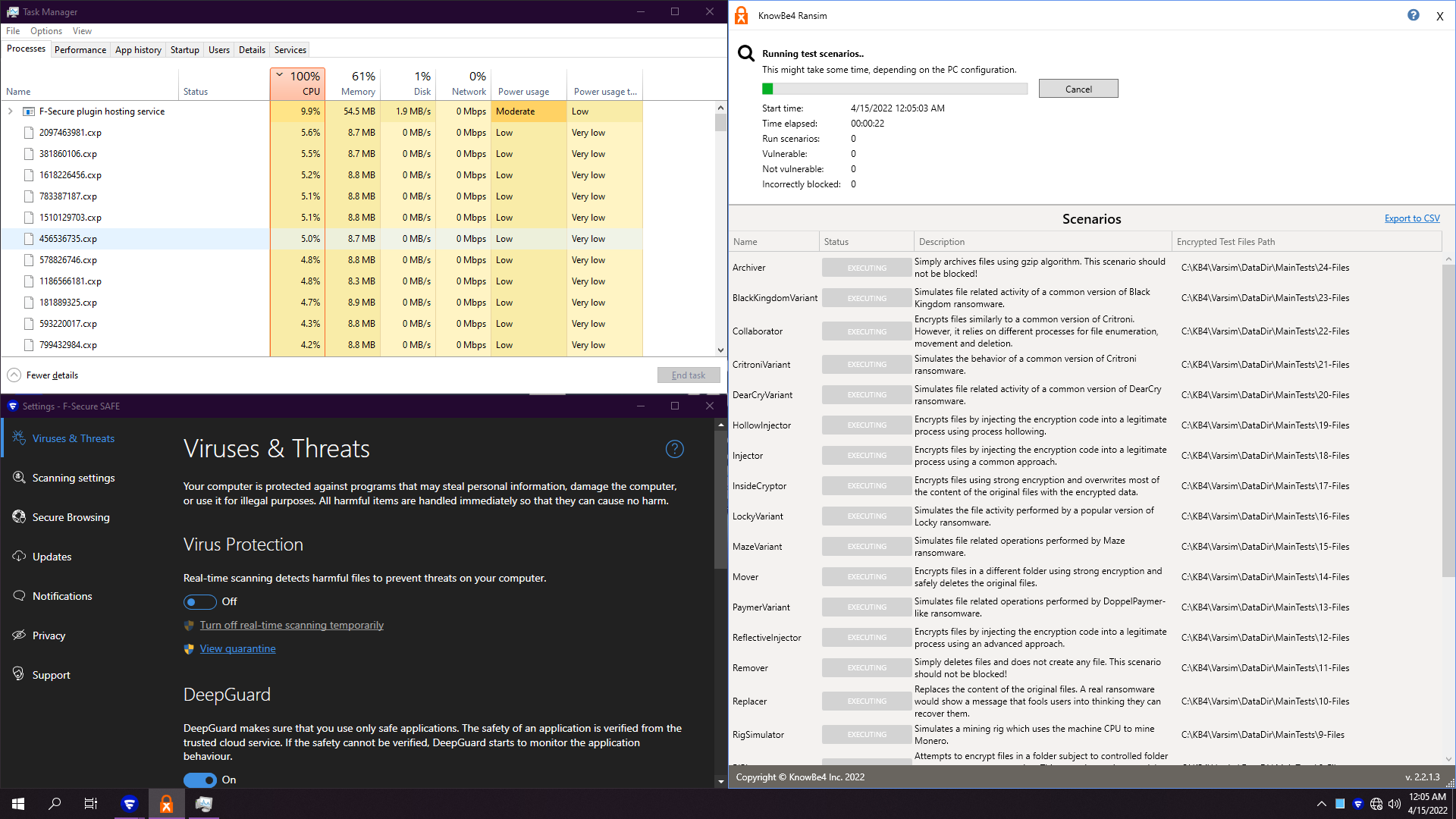
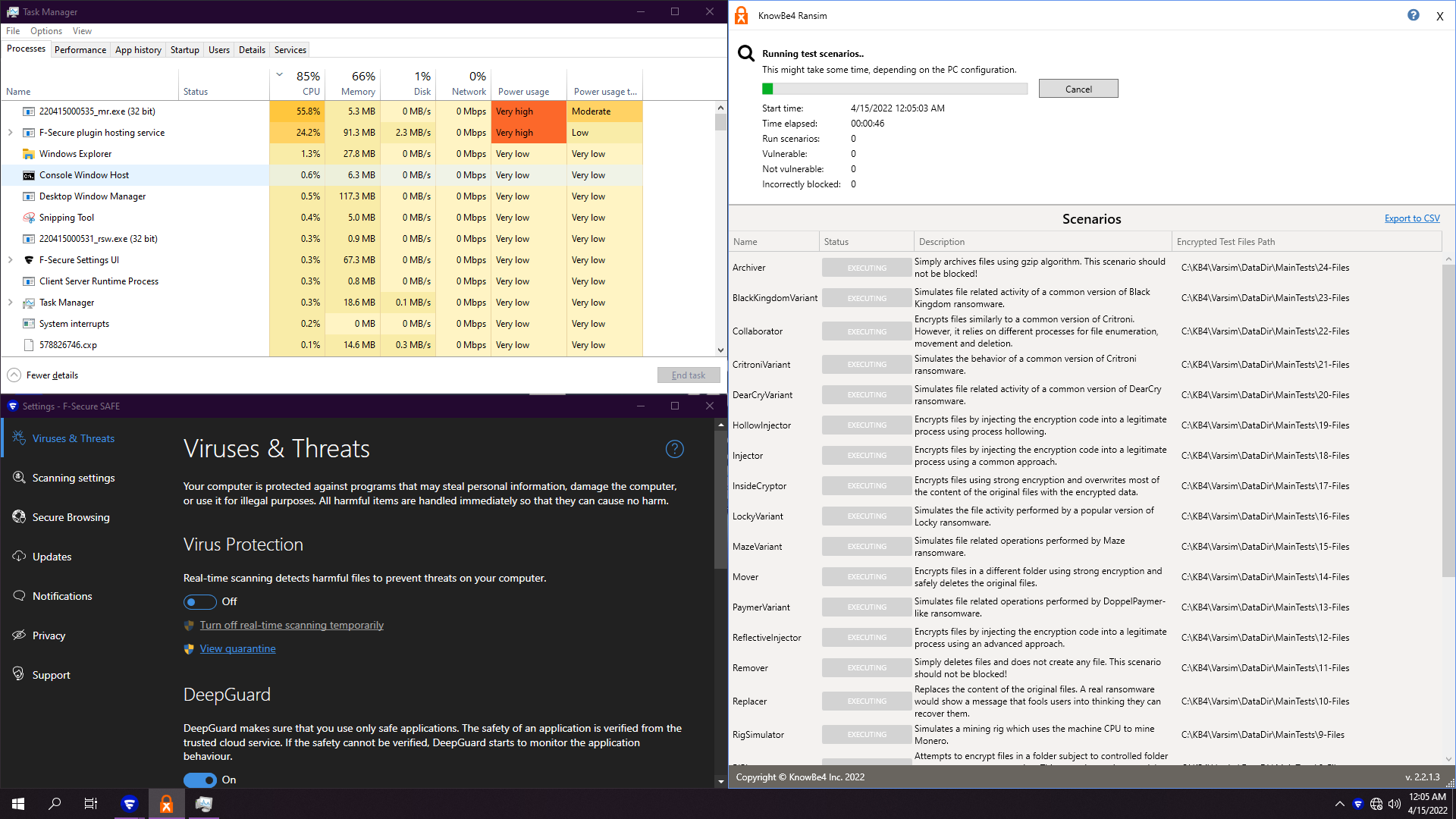
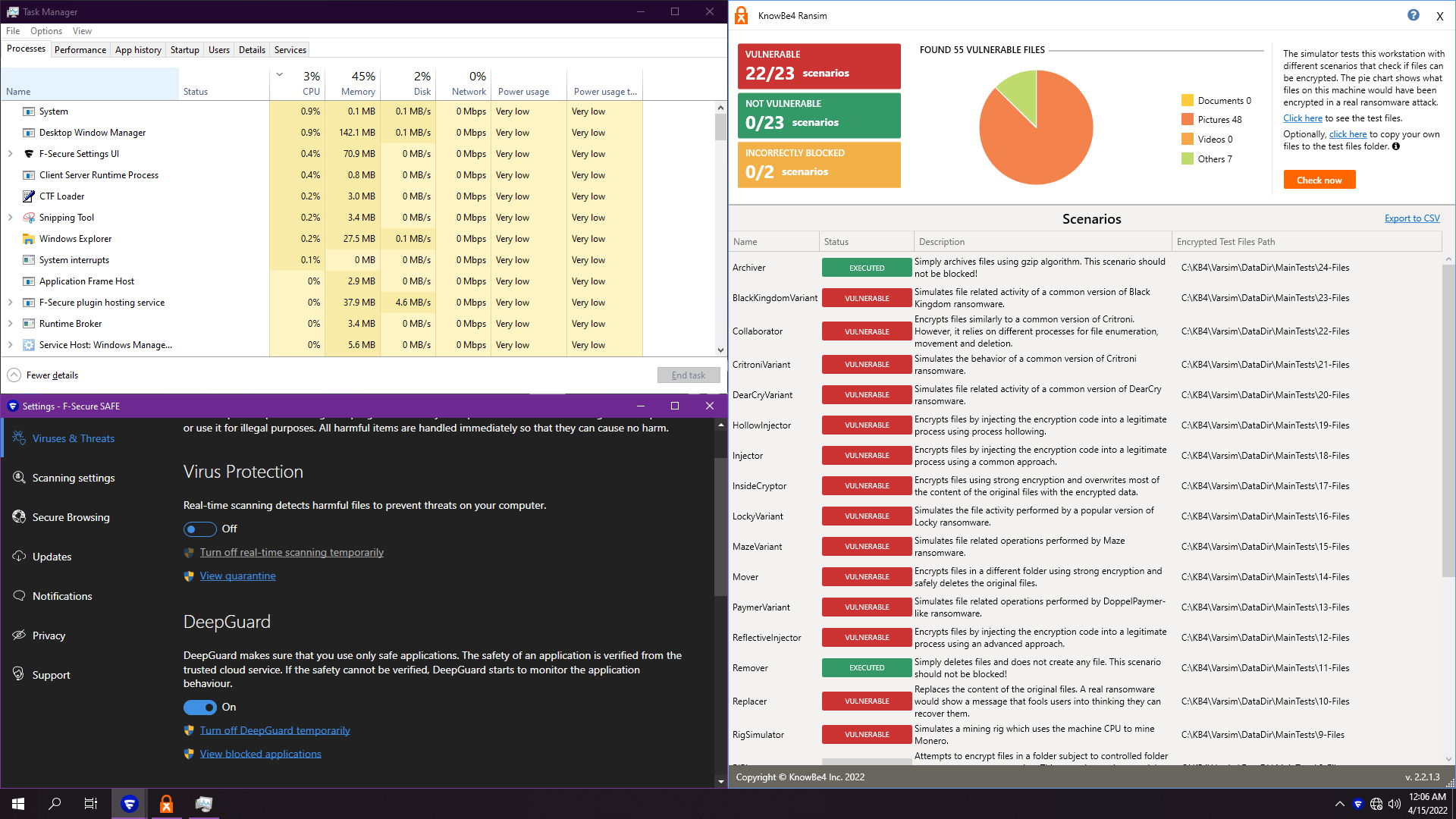
Results speak for themselves... 0 non vulnerable
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
6. Avira Prime
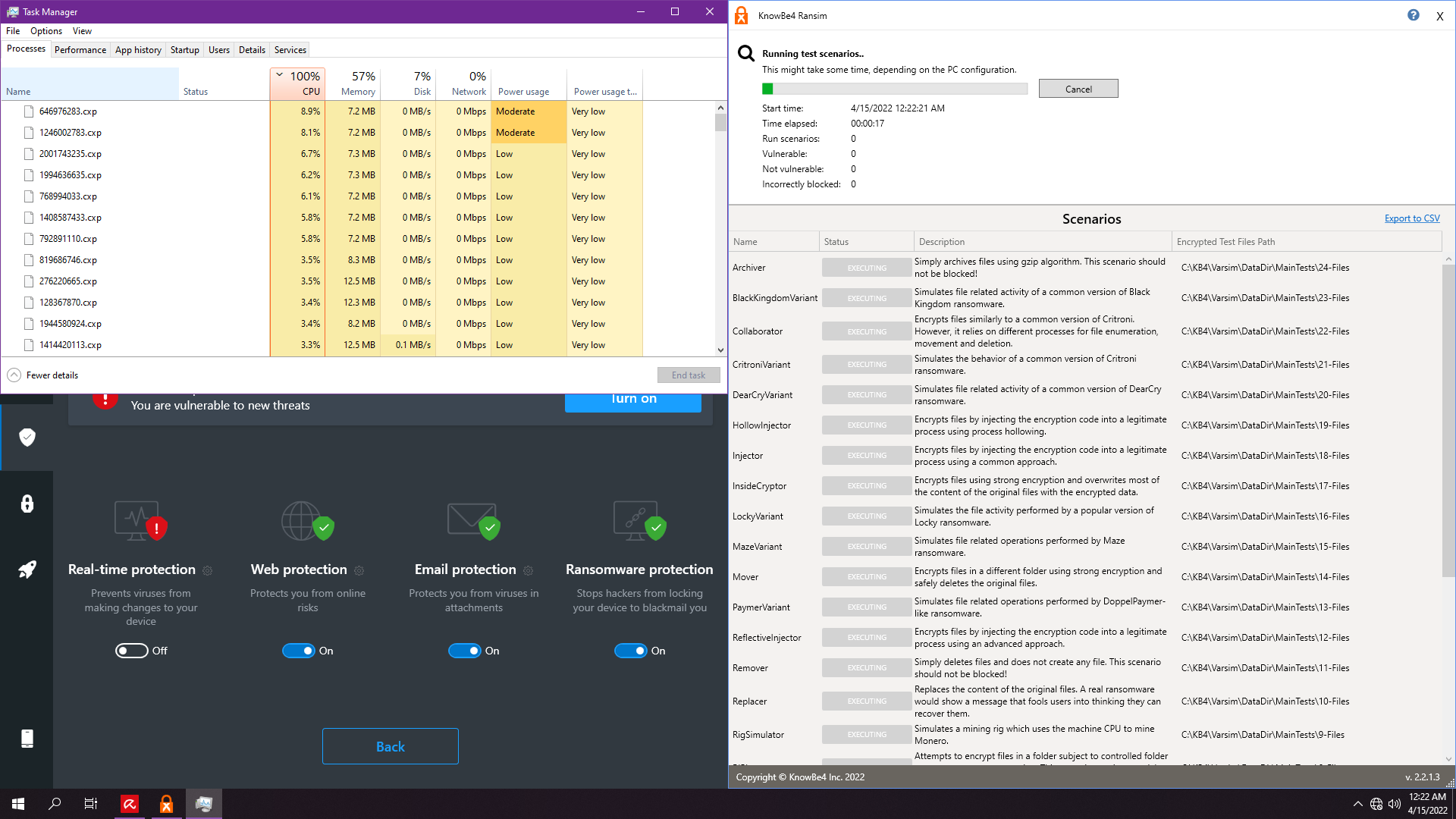
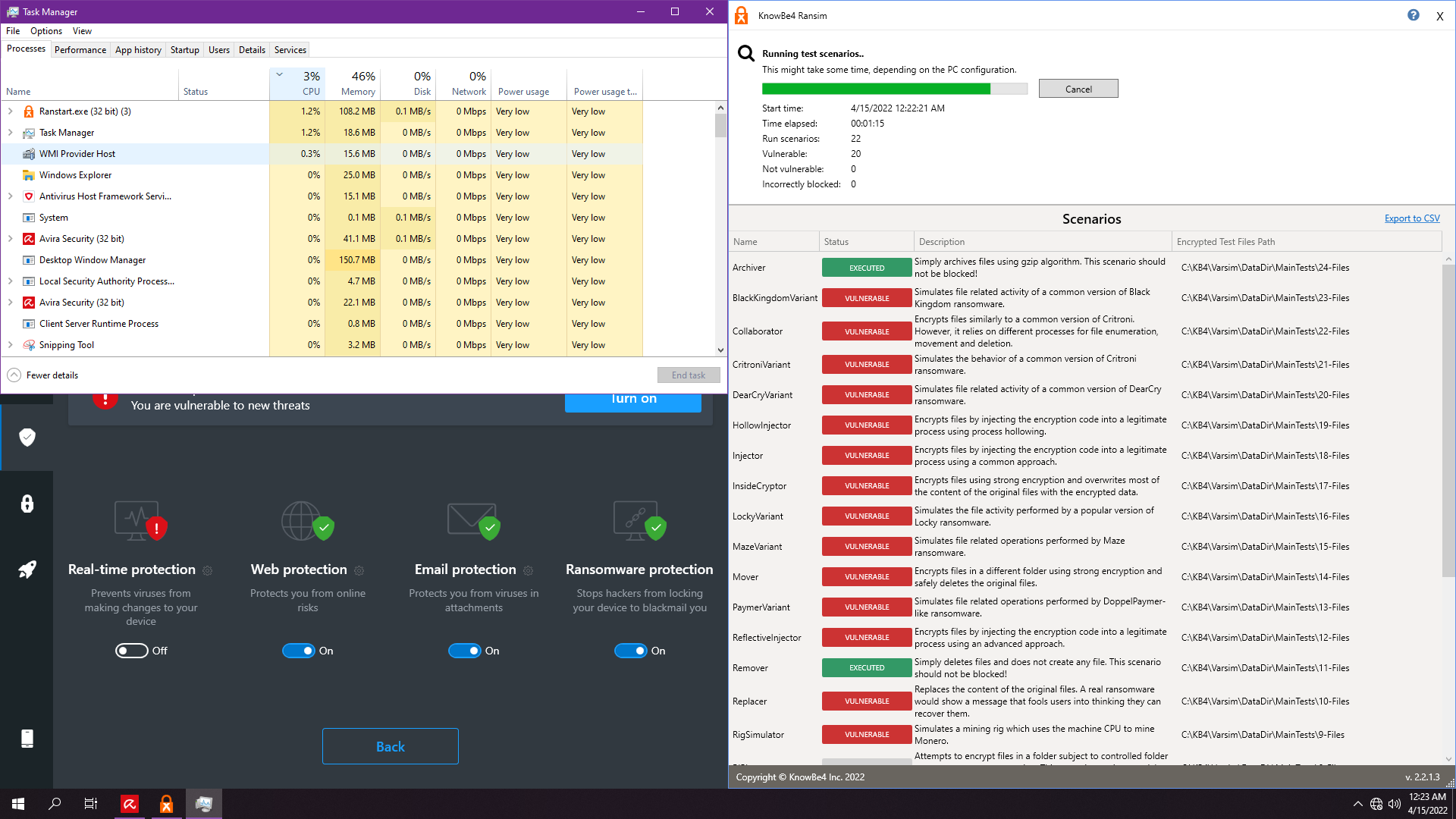
Note: Fastest test, although very bad results as well...
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
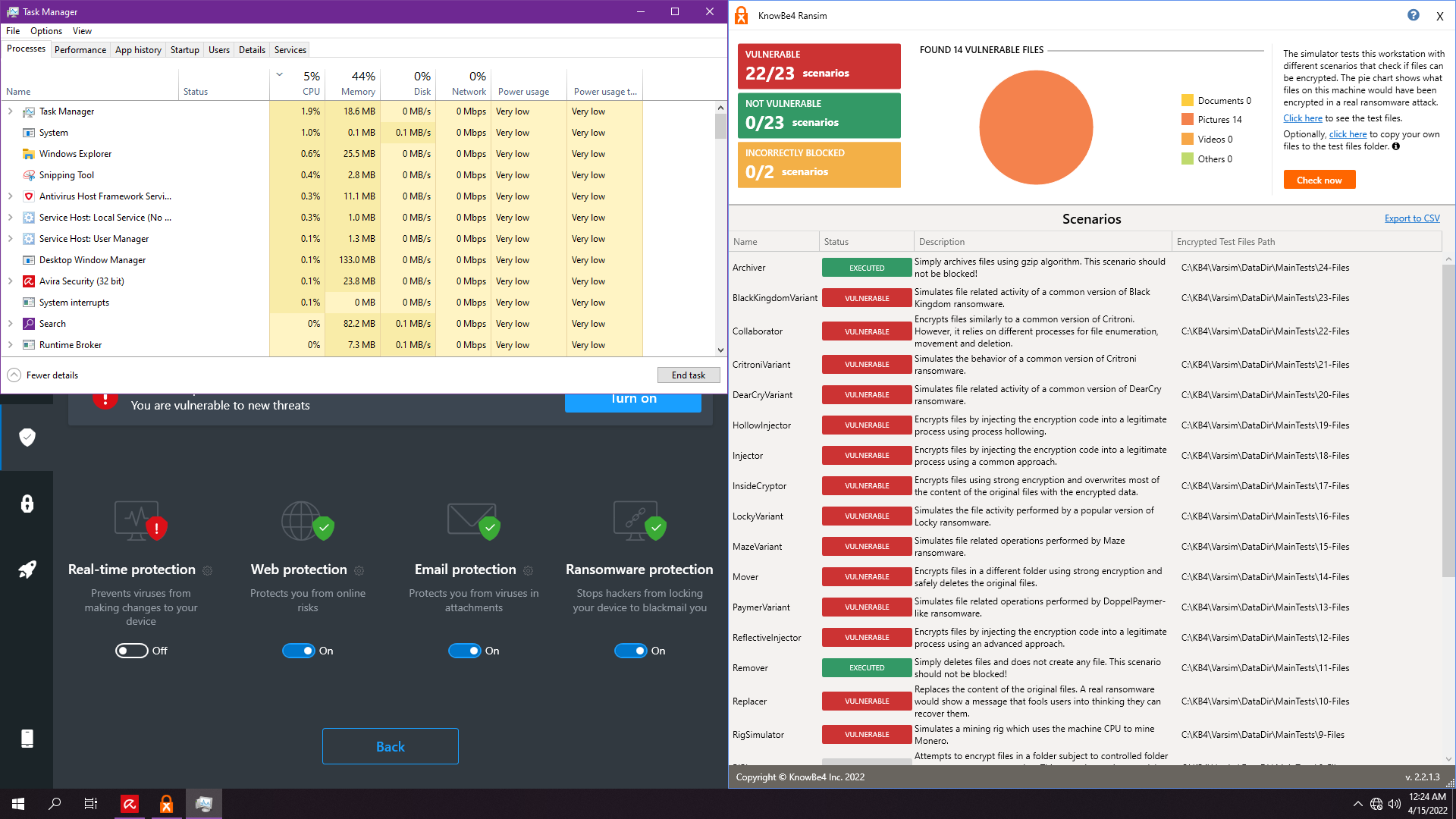
7. Microsfot Defender Default:
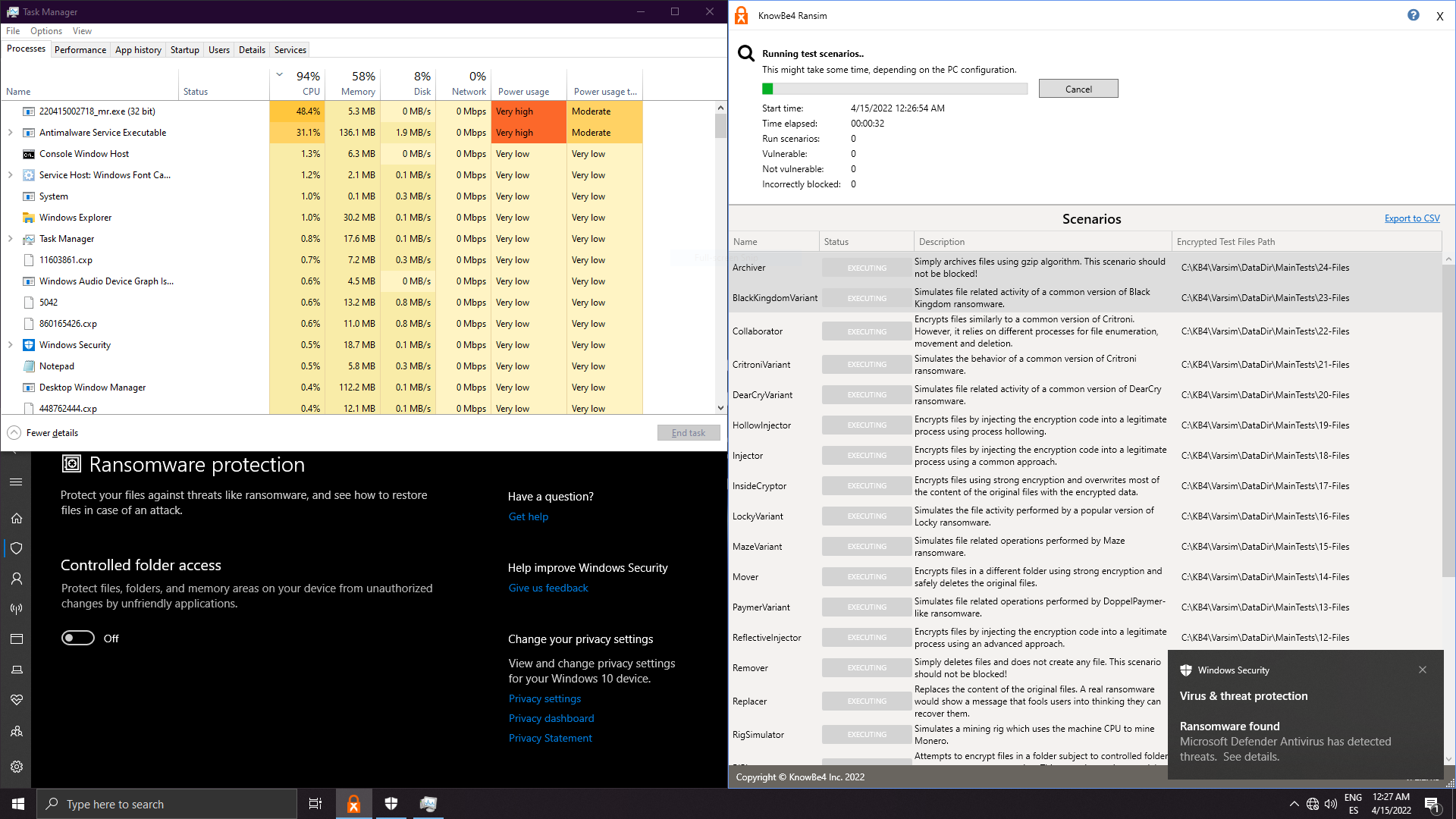
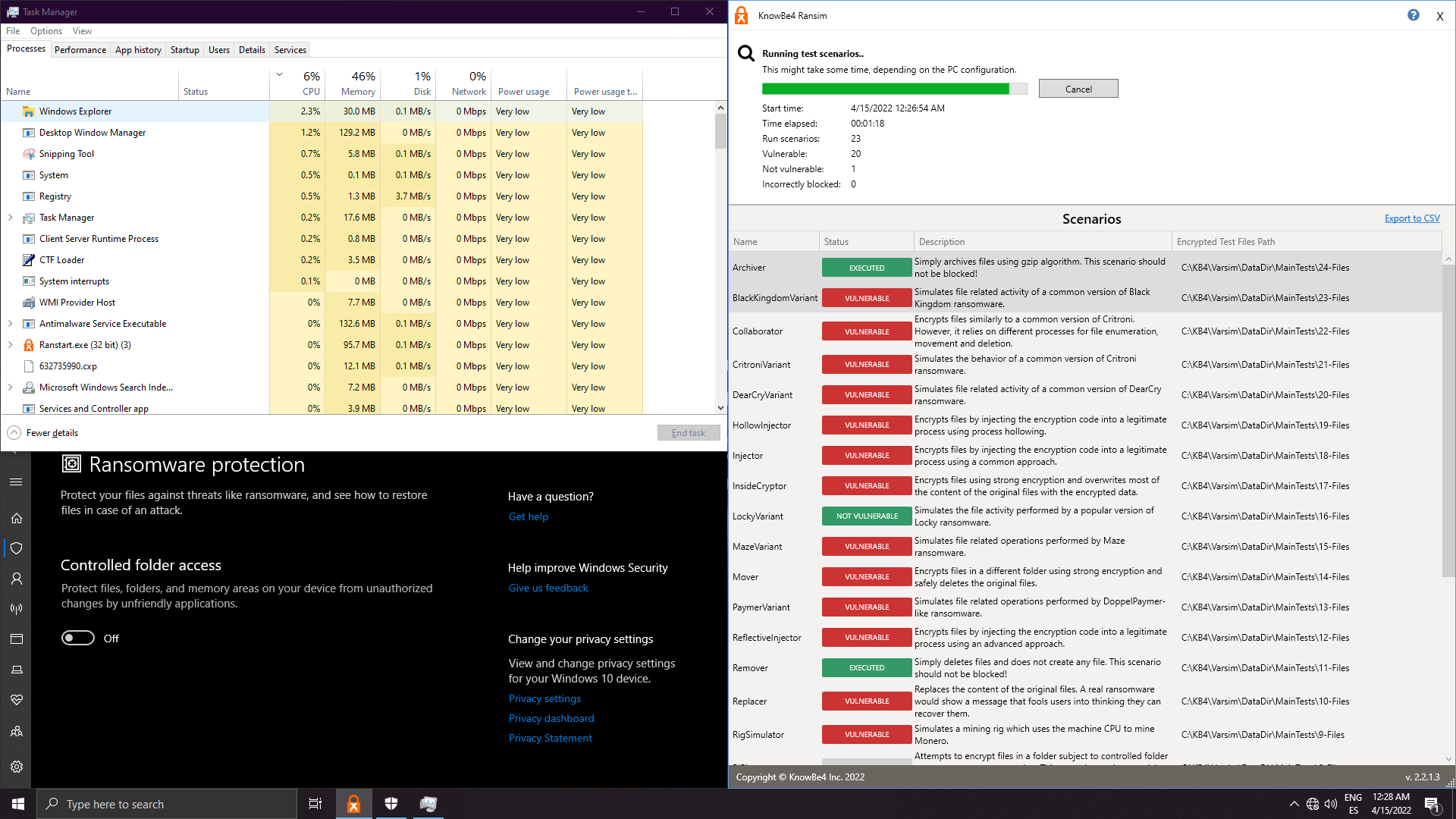
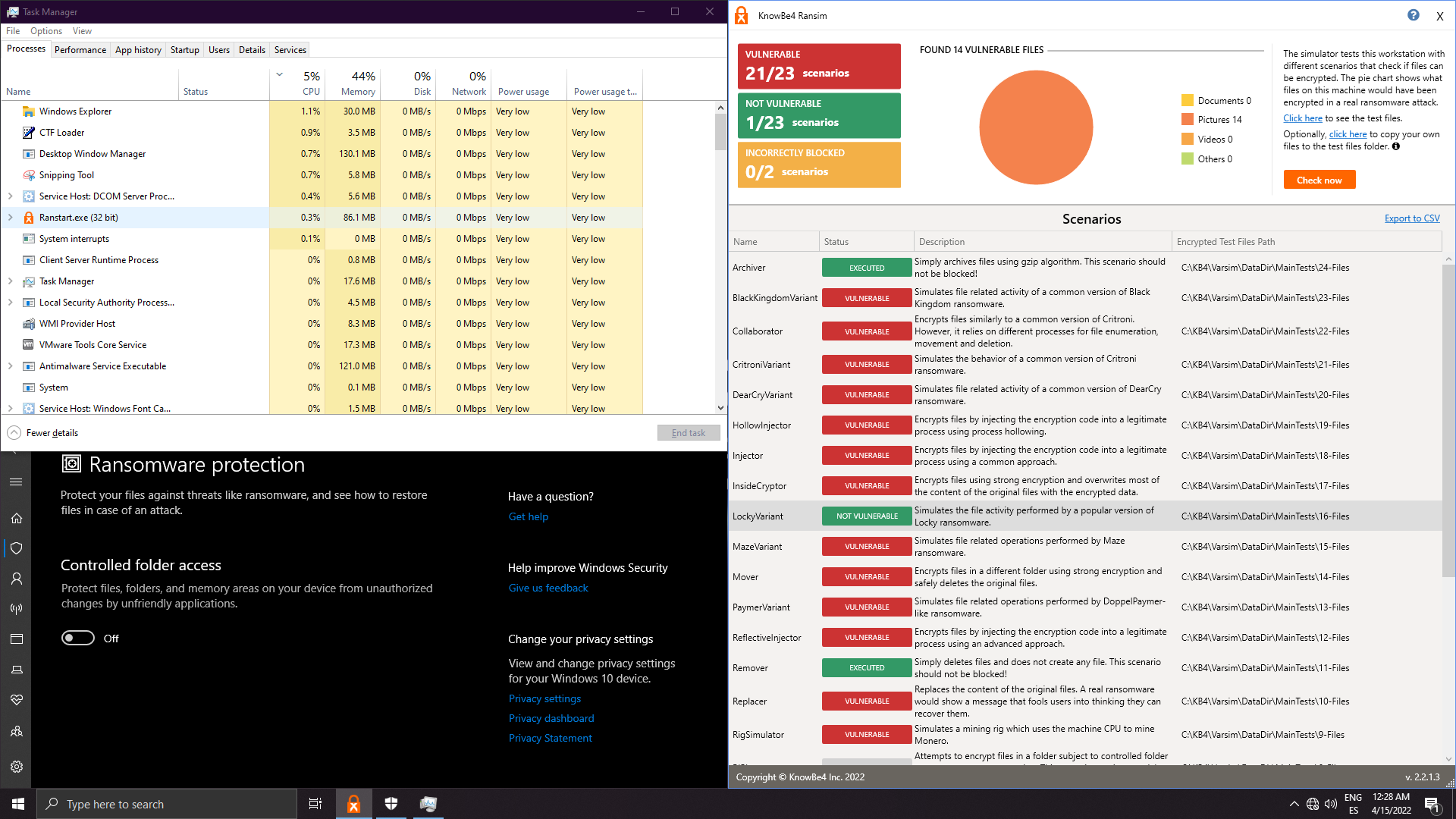
Well done Defender!! 1 popup 1 protected!! No extra hassle!!
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
8. Hardened Microsoft Defender
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
9. G-Data Internet Security 2022
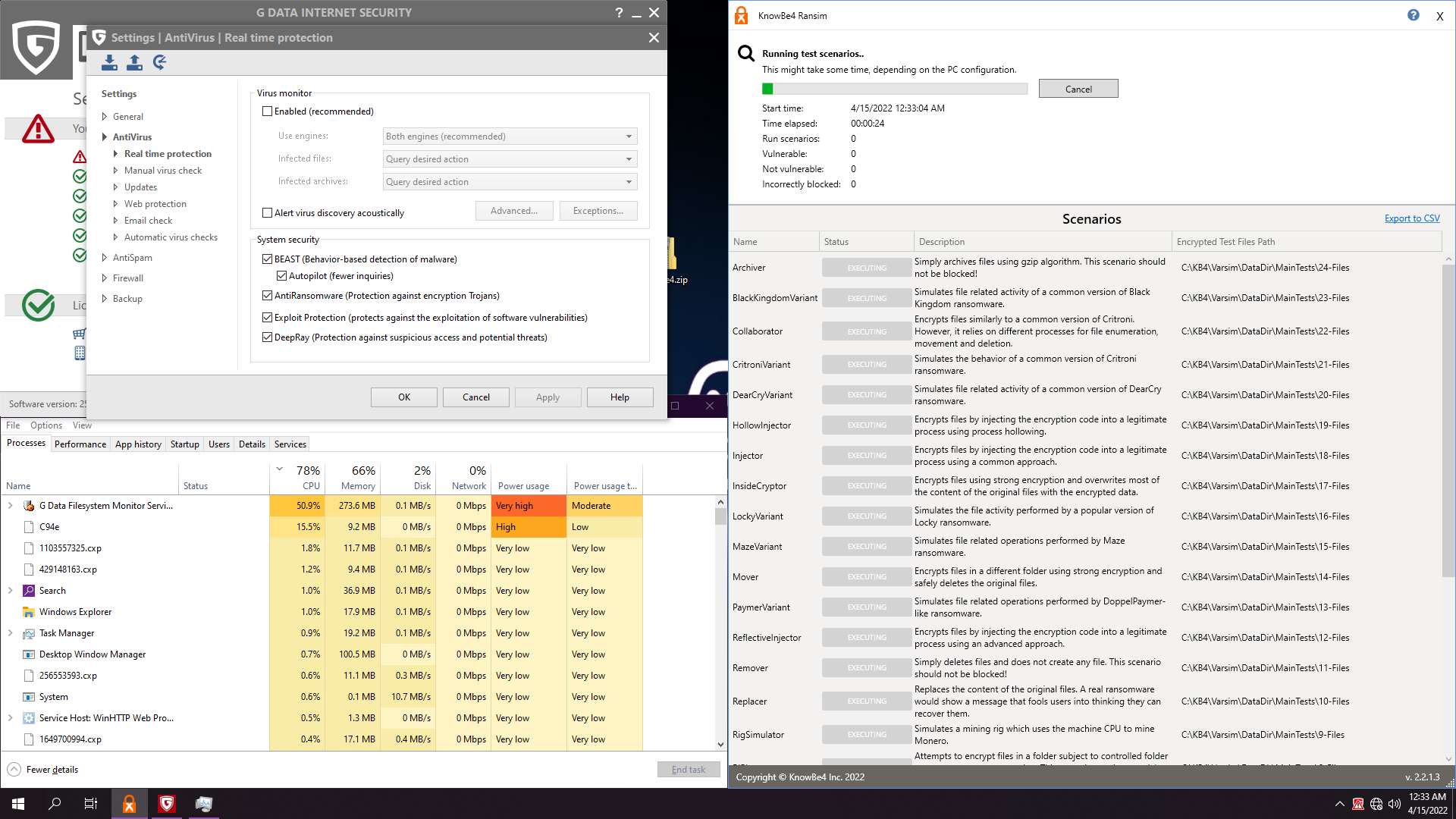
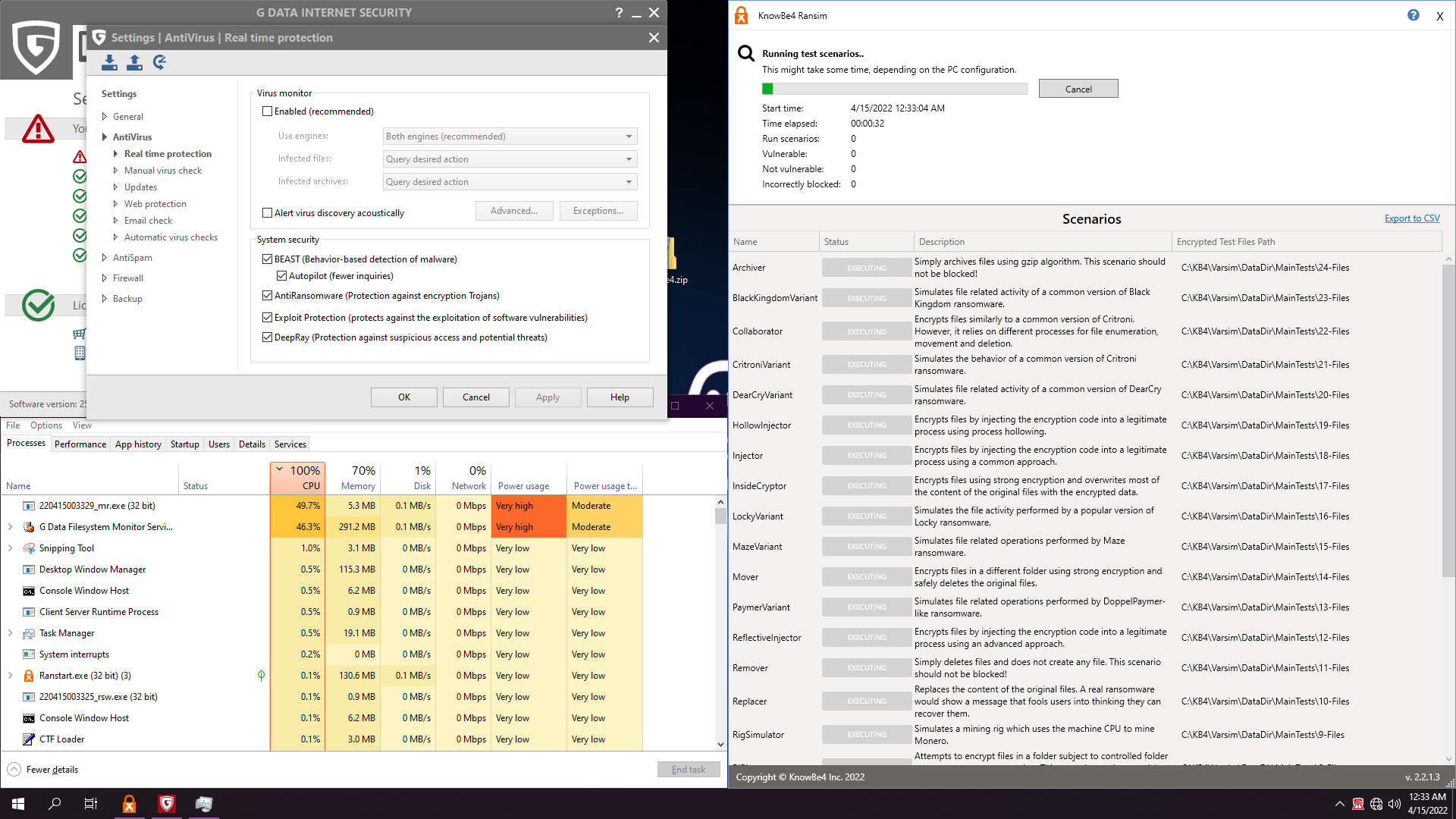
Very heavy on resources... Killed our test:
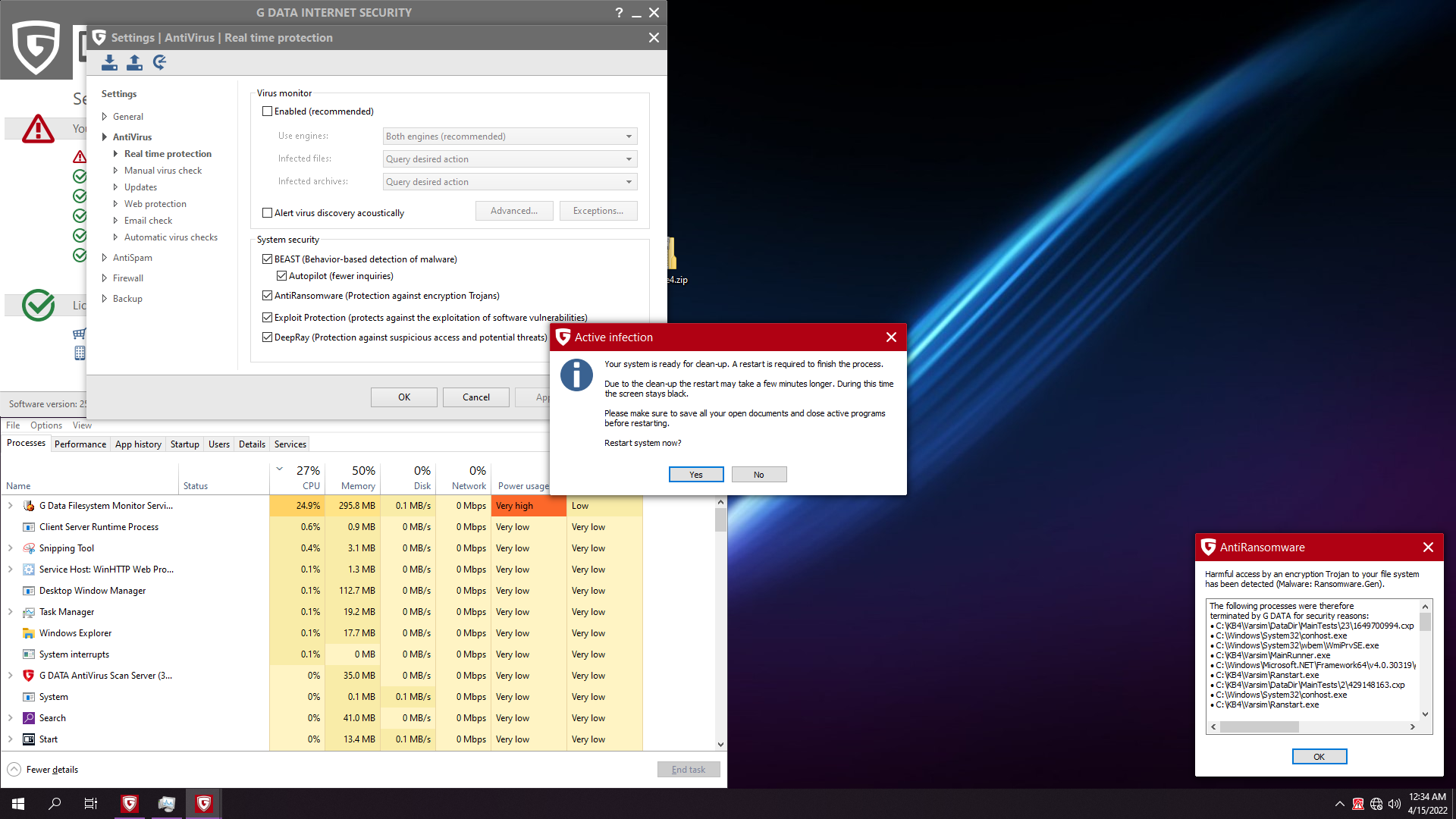
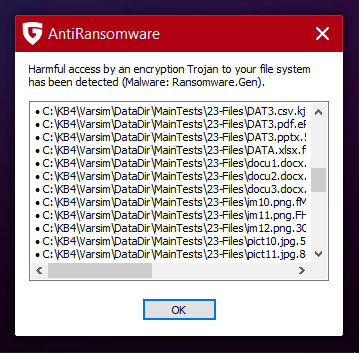
But only 1 ransom catched:
Let's reboot... Should we hope?
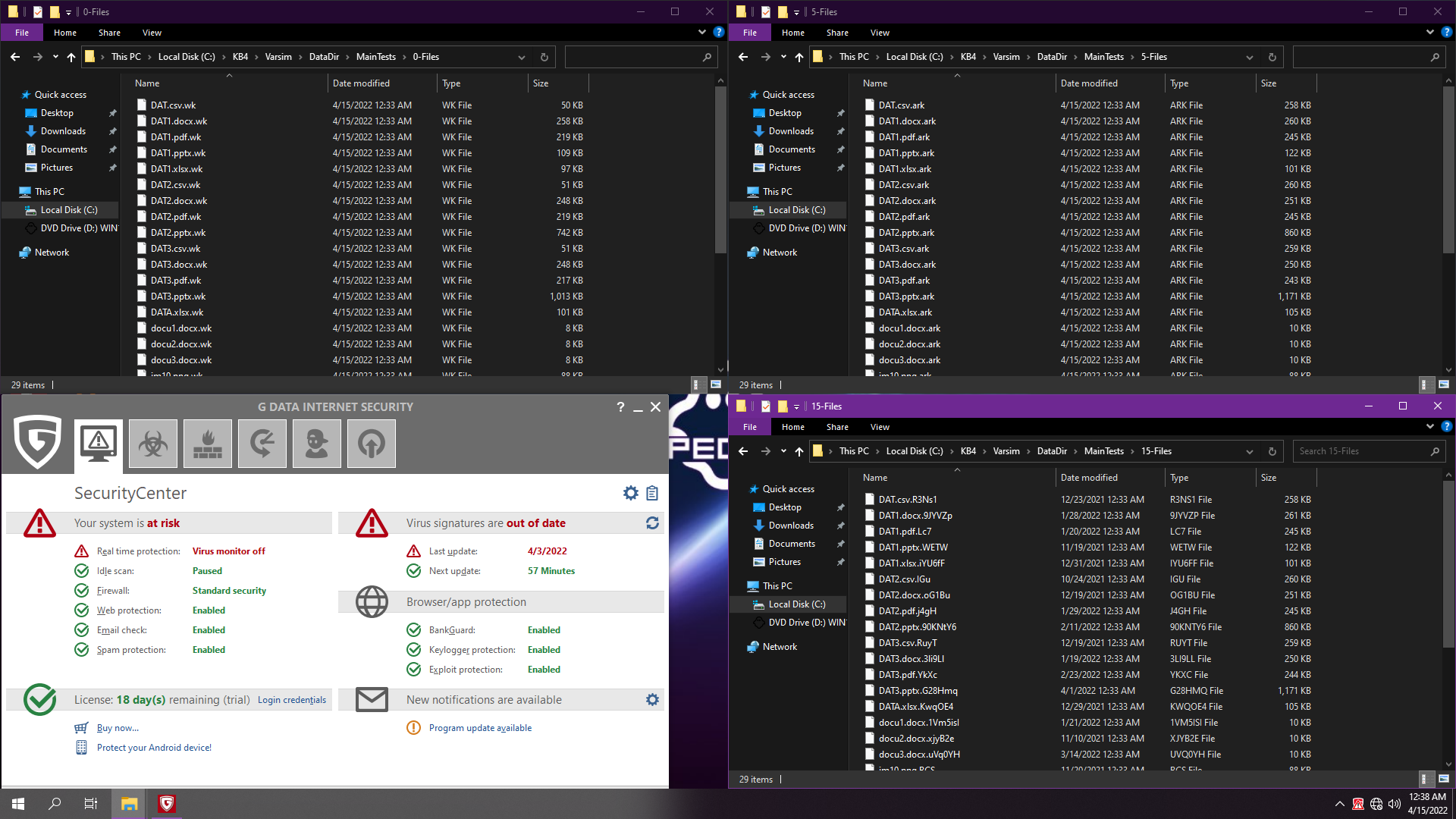
Nah, we shouldn't!!
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
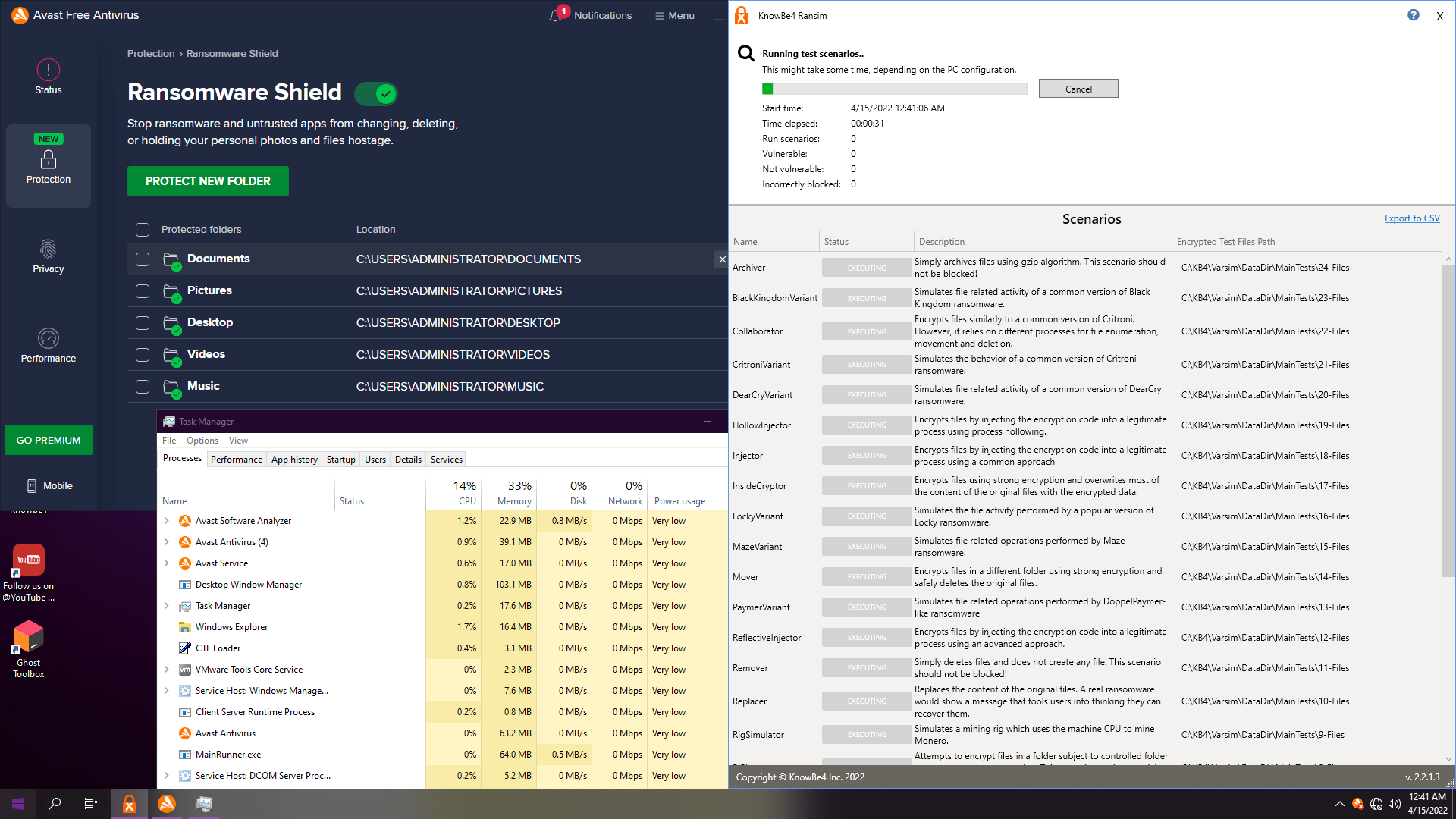
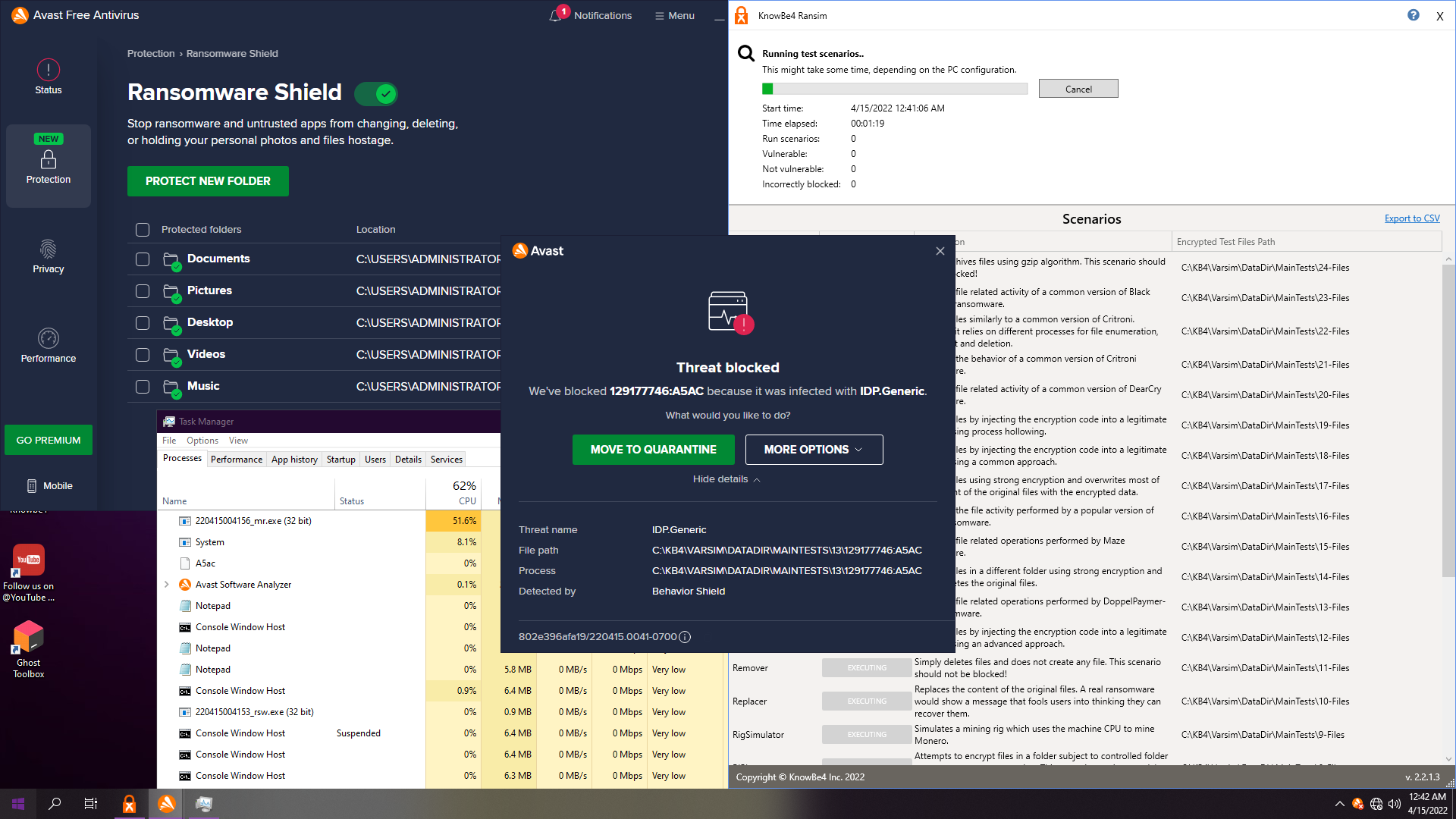
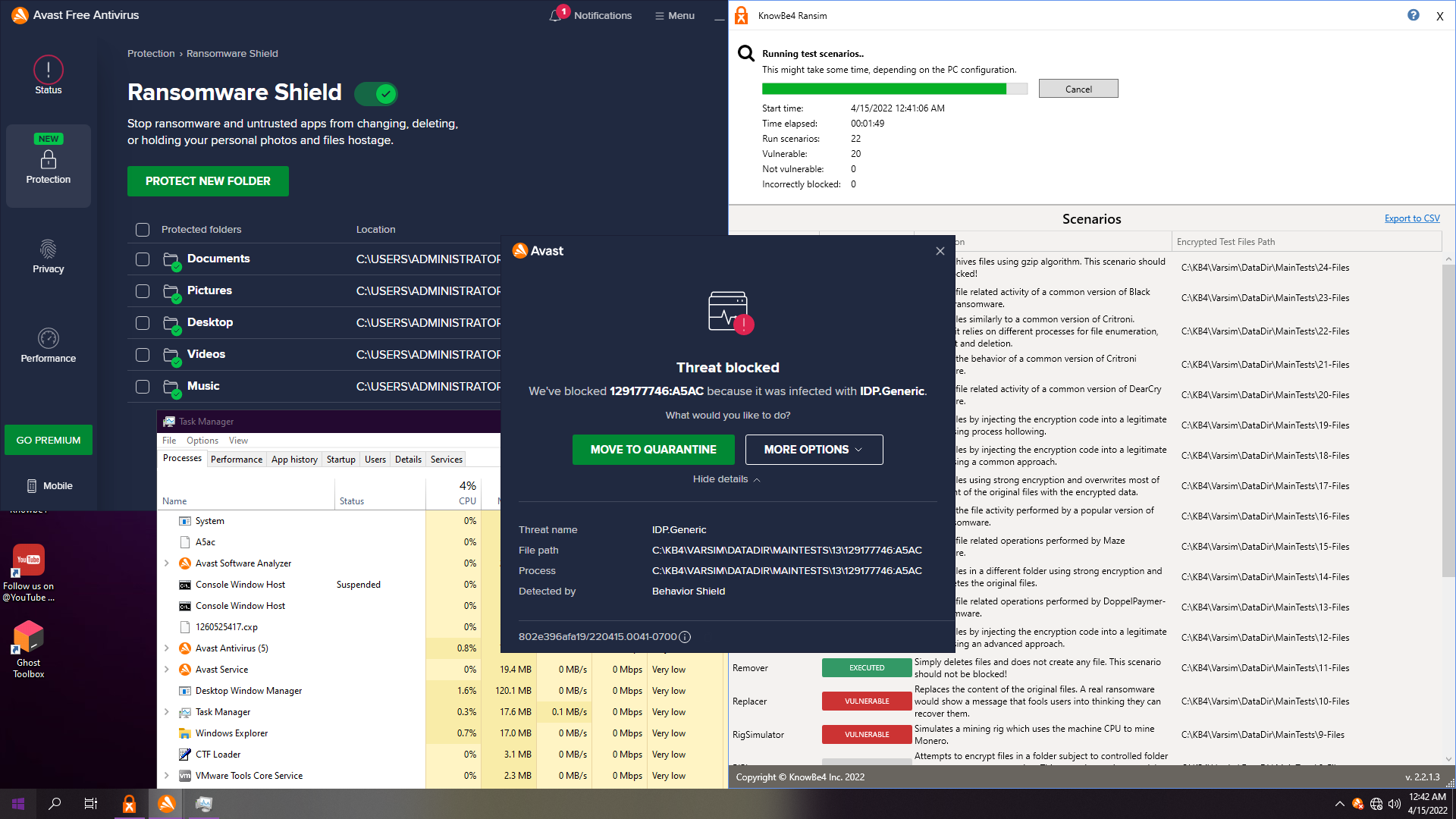
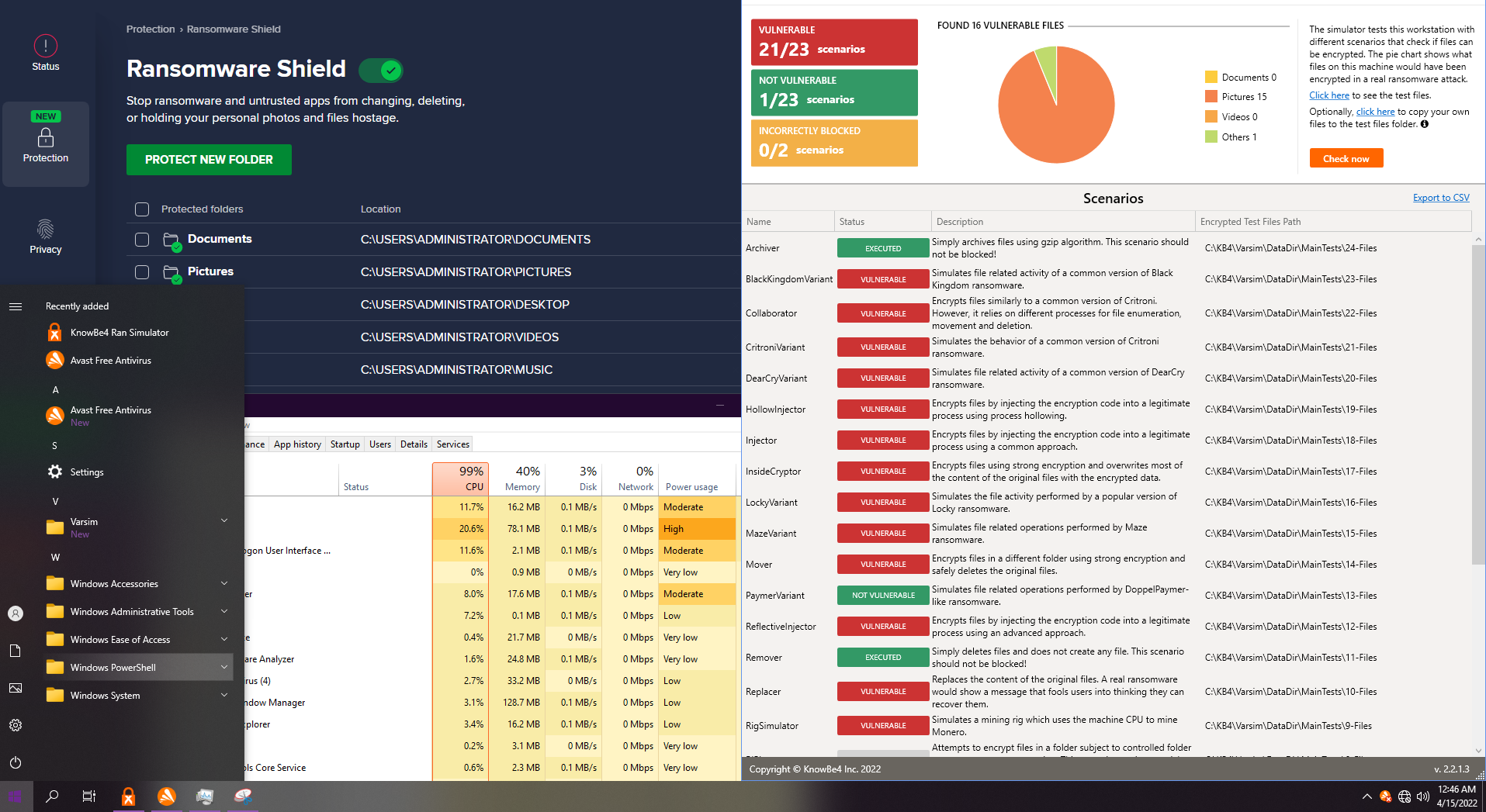
10. Avast Free
VMWare
Windows 10 LTSC 21H2
Windows Defender fully disabled (except for Windows Defender tests ofc)
4 GB RAM
No Internet
Ransomware simulator KnowBe4
1. BitDefender Total Security 2022
Just Ransomware shield. ATP identifies the simulator, not the ransomwares itself, so we will just base the test on real behavioural shield, the ransomware remediation:
Test is pretty fast. About 1:30 min, and result is pretty good: 17/23 non vulnerable.
Resource usage however can be tremendous, having few moments when BD takes up over the ransomwares themselves.
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
2. Eset Internet Security
8 and 9 keep stuck. If we have a look at their folders, we didn't get ransomed. However, I have made this test a couple of times and results differ... Usually they do get ransomed, but hey, we got lucky this time.
We got popups, but we didn't interact with them.
Note: with custom settings from RoboMan (Q&A - Configure ESET Antivirus for Maximum Security (by RoboMan)), you would be overwhelmed by pop-ups. Will depend if you allow or block... But nothing automatic. And yeah, I forgot to disable Internet, but results are same for Eset.
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
3. WiseVector StopX v306
Depending on the ransom, it will autoremediate (16 as shown up here) or ask for recover (20 as shown down here):
Test ends up soon, also about 1:30. Real-time protection and advanced malware protection are disabled. We just leave ransomware shields enabled and with default settings.
Result: 11 non vulnerable.
Note: very light on resources, similar to ESET.
Note 2: great improvement from V305 (WiseVector StopX vs 0-day ransomware (KnowBe4)). On equivalent conditions we were just protected of 4 ransom and just few days after, we got 11!!
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
4. Kaspersky Free 21.5
Let's disable AMSI and rely on system watcher:
Surpringsily I can't find which component remediated the behaviour:
Threats aren't loaded in memory, system is clean, but is it really remediated or is it preblocked? On the past I remember I got system watcher popups and I could see cxp loading, but not anymore...
Result: FULLY CLEAN
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
5. F-Secure Safe 18.5
Results speak for themselves... 0 non vulnerable
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
6. Avira Prime
Note: Fastest test, although very bad results as well...
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
7. Microsfot Defender Default:
Well done Defender!! 1 popup 1 protected!! No extra hassle!!
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
8. Hardened Microsoft Defender
Hardened Defender (security level: high/interactive/max - no difference)
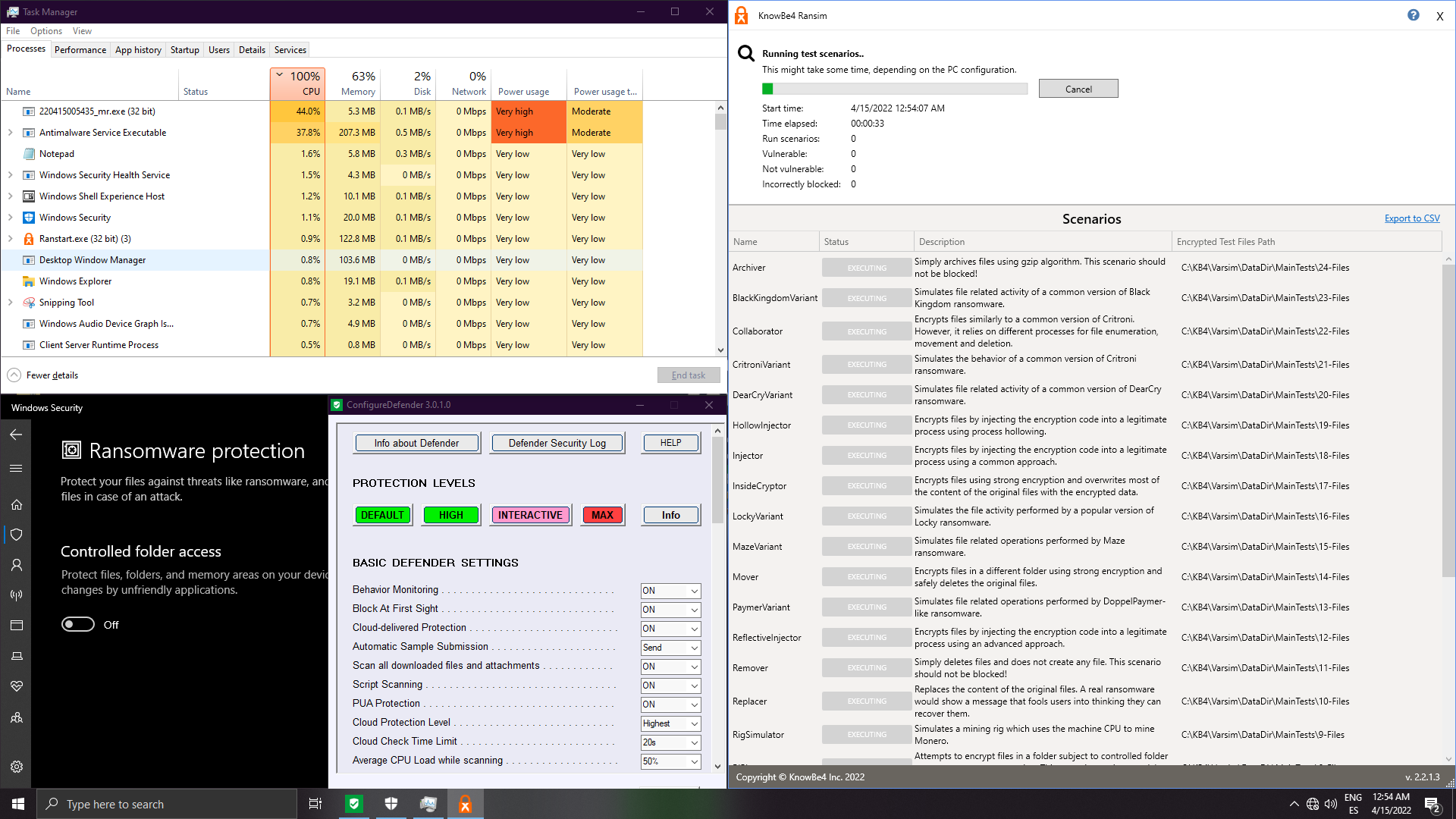
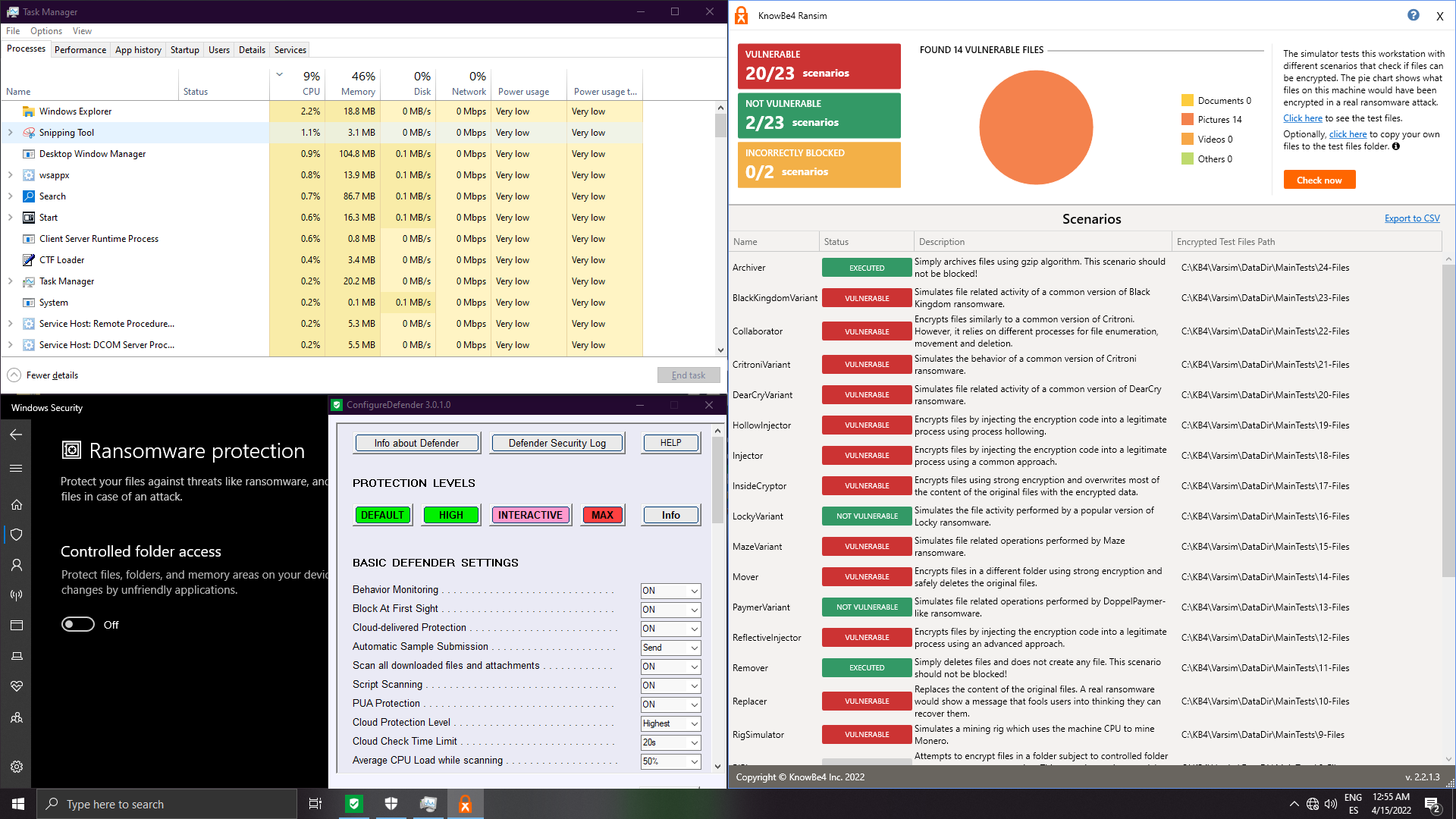
With Interactive/Max, the script is blocked (similar behaviour as if we keep enabled signatures on BD/ESET or the 2 other engines in WVX). This is not ransomware remediation but raw blocking --> Not valid for the test:
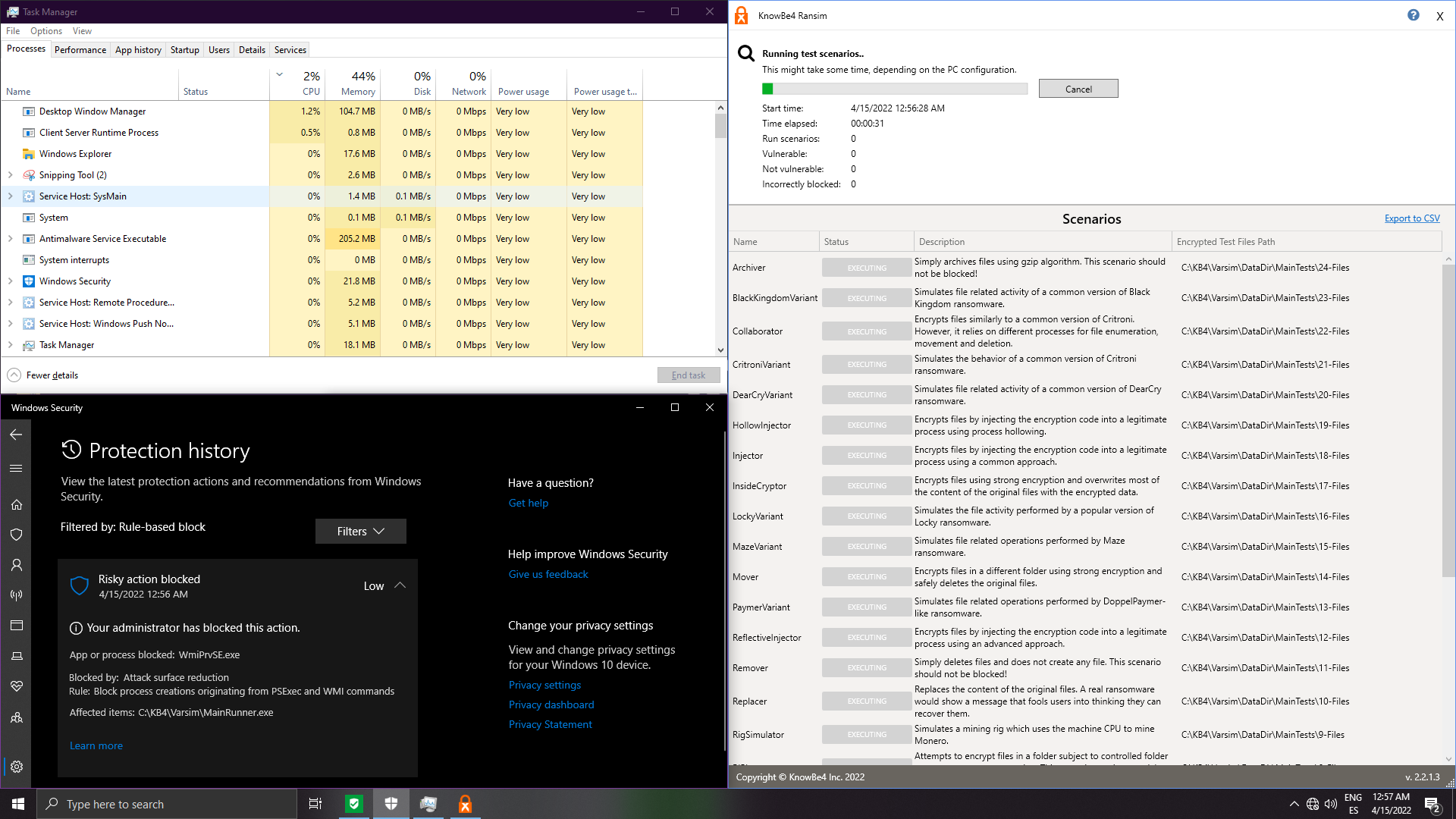
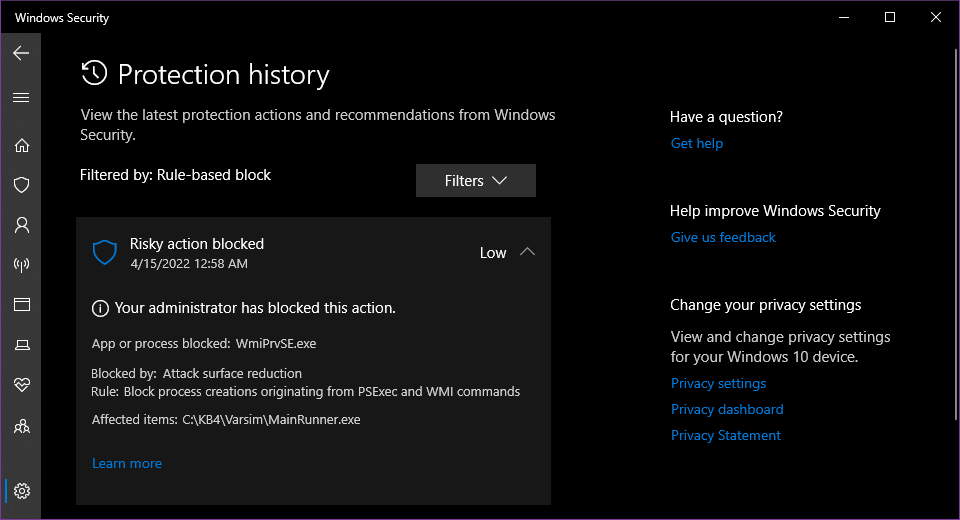
With Interactive/Max, the script is blocked (similar behaviour as if we keep enabled signatures on BD/ESET or the 2 other engines in WVX). This is not ransomware remediation but raw blocking --> Not valid for the test:
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
9. G-Data Internet Security 2022
Very heavy on resources... Killed our test:
But only 1 ransom catched:
Let's reboot... Should we hope?
Nah, we shouldn't!!
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
10. Avast Free