Hello,
I got some kind of redirect virus a short while ago. After scanning with many AV programs I found this guide and gave it a try
http://malwaretips.com/blogs/remove-browser-redirect-virus/
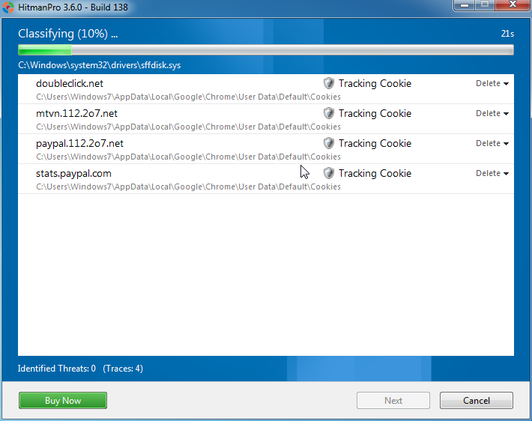
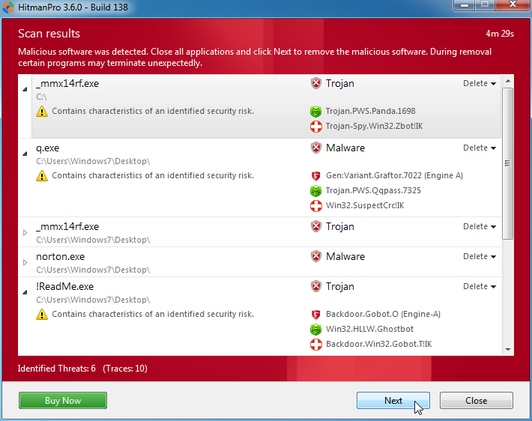
I followed ALL the steps and the virus appeared to be removed. I am running Firefox and Adblock. I've been having some problems clicking links and images lately so I tried disabling AdBlock to see if that fixed it. It didn't, and the virus has returned but not as bad as originally.
The virus does a few things
1. Sometimes I will click a link and new ad tab will open


2. Random text words will become links to popup ads

3. Popups like this appear

AdBlock stops the virus totally, but I have some problems, not sure if they are because or the virus or not.
For example, I can't click any pictures on ebay or zoom or enlarge

This problem occurs in Firefox and Chrome, but not in IE.
Thanks for any help and tell me if I need to provide any additional info. I am running Windows 7, 64 bit.
I got some kind of redirect virus a short while ago. After scanning with many AV programs I found this guide and gave it a try
http://malwaretips.com/blogs/remove-browser-redirect-virus/
I followed ALL the steps and the virus appeared to be removed. I am running Firefox and Adblock. I've been having some problems clicking links and images lately so I tried disabling AdBlock to see if that fixed it. It didn't, and the virus has returned but not as bad as originally.
The virus does a few things
1. Sometimes I will click a link and new ad tab will open


2. Random text words will become links to popup ads

3. Popups like this appear

AdBlock stops the virus totally, but I have some problems, not sure if they are because or the virus or not.
For example, I can't click any pictures on ebay or zoom or enlarge

This problem occurs in Firefox and Chrome, but not in IE.
Thanks for any help and tell me if I need to provide any additional info. I am running Windows 7, 64 bit.