cruelsister
Level 43
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
A friend that has read my previous drivel about Comodo noted to me that I never really discussed the settings of the Firewall itself. This was indeed a rather big failing on my part that I apologize for, so here is a quick Primer:
(Note that CIS and CF have differing default settings- but as I see no value in CIS the below refers to Comodo Firewall. I further assume that the Sandbox will be Enabled with the "Any" change active)
Although the Firewall module of CF lends itself to much tinkering with regards to Portsets, Network Zones, Traffic Filtering, etc. only the most Networkly adept people need to be concerned with this stuff, and quite frankly I question the real-world value of playing with these settings (it also gives me a headache). This being said, let's discuss the important things:
1). CF default settings- If you already have CF installed, all that I will discuss can be found on the main Firewall setting page (Tasks>Firewall Tasks>Open Advanced Settings).
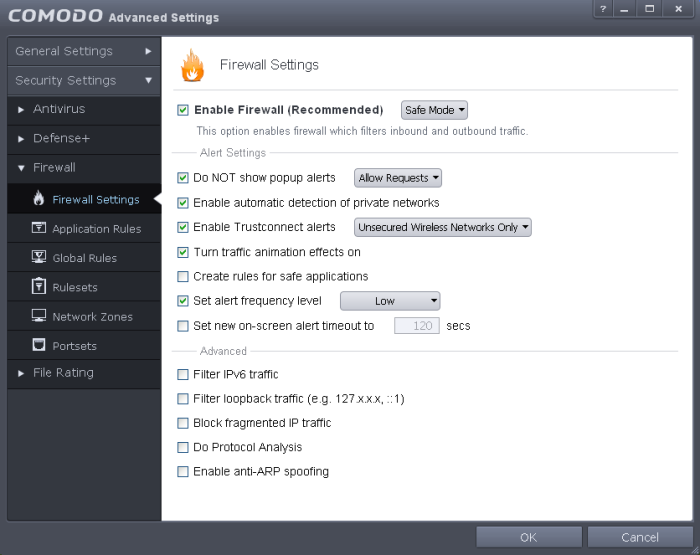
CF is configured to start in Safe Mode- this basically allows all applications that are whitelisted by Comodo to connect to the Network without any specific rules being made. Note also on that main page there is an unchecked box to "Create Rules for Safe Applications"- if you check this box and run a safe application like an email app or web browser, CF will start to pay attention to have the specific application operates and will automatically make rules specific for it. I personally leave it unchecked.
Note that no firewall popups will present for this default setting.
2). Custom Ruleset- This change can be made at the top, under Enable Traffic Filtering. Custom Ruleset simply will alert you to anything that tries to connect outbound, both safe apps and unknowns. A popup alert will occur asking whether the the connection request should be Allowed or Blocked, with an added checkbox to remember the action taken. This setting is very nice for the more advanced user that aside wanting all outbound requests by unknowns to result in an alert, but also wants to decide what legitimate applications should be allowed out.
3). The "Do Not Show Popup Alerts" setting- This is actually the point of this post. Custom Mode will give popups to everything (at least once, anyway); Safe Mode will not give popups for anything. By checking this box when the firewall is in Safe Mode what happens?
a). All whitelisted applications will still be allowed to connect to the Internet.
b). Any unknowns, which will be active in the Sandbox, that request network access will cause either a popup if the box is unchecked and you choose "Allow Requests", or will be denied any Network access silently by default.
In production systems I strongly recommend the uncheck that box and choose Block Requests. This will tell both Malware and Adware to go screw themselves when requesting Outbound connections without any input by the user. This would be really handy in preventing things like worms to connect to the C&C, and downloaders from downloading (note also that the malware from trojan downloaders will also be sandboxed, so no real issue here). Another benefit would be the silent blocking of script keyloggers. Remember that a keylogger in order to be successful must both log keystrokes AND send this information out to the Blackhats. Stopping even one of these actions would be successful protection.
As an example, seek out this test keylogger, evil.exe which is a Python script (and understand that a true malicious keylogger- not a script- would be prevented from logging anything if sandboxed in Full V):
(hxxps://samsclass.info/124/proj14/evil.htm)
Note that Comodo, although sandboxing the logger, won't actually stop the keylogging as user input is needed for it to work. This is what happens when evil.exe is run:
1). when the interface opens, you hit Enter
2). Open Notepad and type a few letters
3). Hit enter again
You will notice that a text file is created in the same directory as the logger, which will then be transmitted to Pastebin- a browser will then open an you will see the results. So what will happen when any of the above Firewall settings are used?
1). Firewall default settings- the keylogger logs keystrokes and successfully transmits out
2). Custom Mode- you will get a Outbound connection request popup. Blocking the transmission stops the logging effort
3). Safe Mode with "Do Not Show Popups" box unchecked, and action of "Block Requests"- Transmission by keylogger silently blocked, keylogger fails in malicious activity.
So the moral of this extended post- Blocking Outbound requests by sandboxed applications is good, especially if you put CF on Mom or Dad's computer.
(Note that CIS and CF have differing default settings- but as I see no value in CIS the below refers to Comodo Firewall. I further assume that the Sandbox will be Enabled with the "Any" change active)
Although the Firewall module of CF lends itself to much tinkering with regards to Portsets, Network Zones, Traffic Filtering, etc. only the most Networkly adept people need to be concerned with this stuff, and quite frankly I question the real-world value of playing with these settings (it also gives me a headache). This being said, let's discuss the important things:
1). CF default settings- If you already have CF installed, all that I will discuss can be found on the main Firewall setting page (Tasks>Firewall Tasks>Open Advanced Settings).

CF is configured to start in Safe Mode- this basically allows all applications that are whitelisted by Comodo to connect to the Network without any specific rules being made. Note also on that main page there is an unchecked box to "Create Rules for Safe Applications"- if you check this box and run a safe application like an email app or web browser, CF will start to pay attention to have the specific application operates and will automatically make rules specific for it. I personally leave it unchecked.
Note that no firewall popups will present for this default setting.
2). Custom Ruleset- This change can be made at the top, under Enable Traffic Filtering. Custom Ruleset simply will alert you to anything that tries to connect outbound, both safe apps and unknowns. A popup alert will occur asking whether the the connection request should be Allowed or Blocked, with an added checkbox to remember the action taken. This setting is very nice for the more advanced user that aside wanting all outbound requests by unknowns to result in an alert, but also wants to decide what legitimate applications should be allowed out.
3). The "Do Not Show Popup Alerts" setting- This is actually the point of this post. Custom Mode will give popups to everything (at least once, anyway); Safe Mode will not give popups for anything. By checking this box when the firewall is in Safe Mode what happens?
a). All whitelisted applications will still be allowed to connect to the Internet.
b). Any unknowns, which will be active in the Sandbox, that request network access will cause either a popup if the box is unchecked and you choose "Allow Requests", or will be denied any Network access silently by default.
In production systems I strongly recommend the uncheck that box and choose Block Requests. This will tell both Malware and Adware to go screw themselves when requesting Outbound connections without any input by the user. This would be really handy in preventing things like worms to connect to the C&C, and downloaders from downloading (note also that the malware from trojan downloaders will also be sandboxed, so no real issue here). Another benefit would be the silent blocking of script keyloggers. Remember that a keylogger in order to be successful must both log keystrokes AND send this information out to the Blackhats. Stopping even one of these actions would be successful protection.
As an example, seek out this test keylogger, evil.exe which is a Python script (and understand that a true malicious keylogger- not a script- would be prevented from logging anything if sandboxed in Full V):
(hxxps://samsclass.info/124/proj14/evil.htm)
Note that Comodo, although sandboxing the logger, won't actually stop the keylogging as user input is needed for it to work. This is what happens when evil.exe is run:
1). when the interface opens, you hit Enter
2). Open Notepad and type a few letters
3). Hit enter again
You will notice that a text file is created in the same directory as the logger, which will then be transmitted to Pastebin- a browser will then open an you will see the results. So what will happen when any of the above Firewall settings are used?
1). Firewall default settings- the keylogger logs keystrokes and successfully transmits out
2). Custom Mode- you will get a Outbound connection request popup. Blocking the transmission stops the logging effort
3). Safe Mode with "Do Not Show Popups" box unchecked, and action of "Block Requests"- Transmission by keylogger silently blocked, keylogger fails in malicious activity.
So the moral of this extended post- Blocking Outbound requests by sandboxed applications is good, especially if you put CF on Mom or Dad's computer.