Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
It is not an excuse, but rather an opportunity. Microsoft guys are not altruists. They have no motivation to optimize their code (like most programmers), except when they are forced to do it. I suspect that most of the Windows code is rather poorly optimized. The only motivation for Microsoft is probably the competition in the market and as we know, they do not complain.That's the excuse lazy developers use to not optimize their code, is why despite having faster computers, software is still slow.
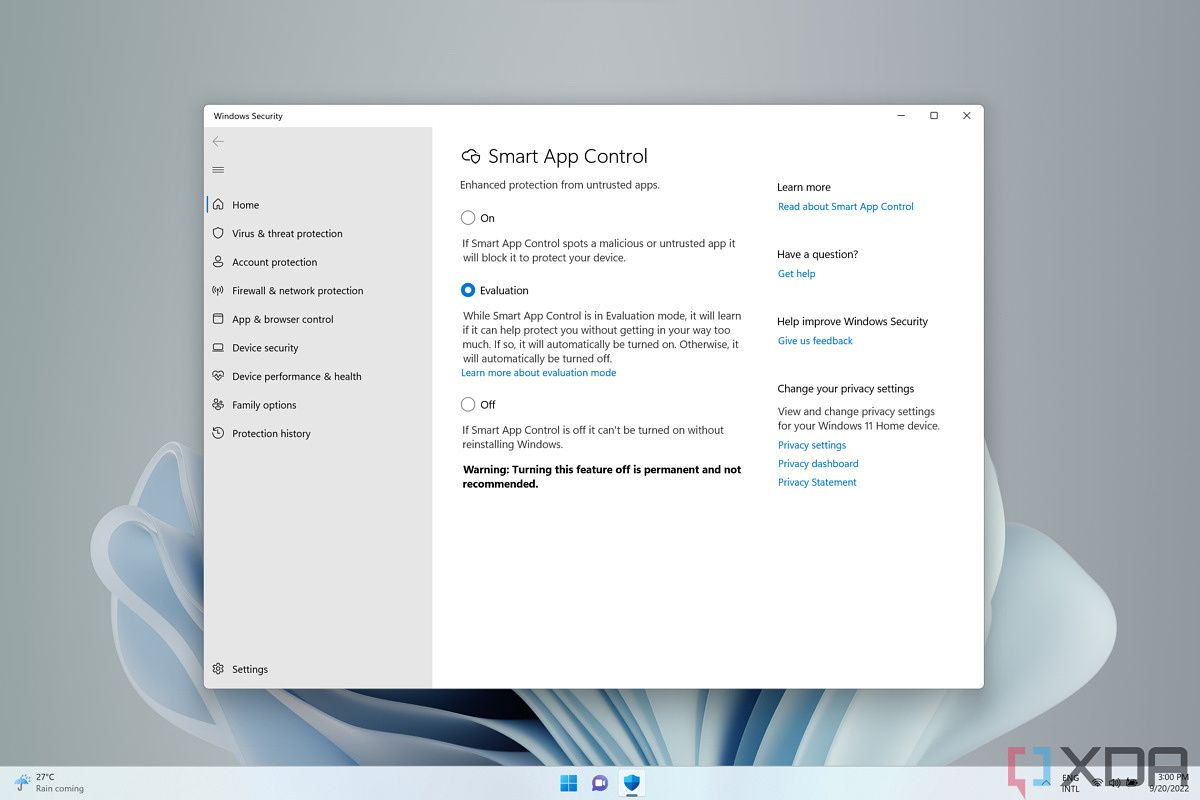
Anyway, SAC has got more important issues than impacting the performance of modern computers (Windows 11 is not intended for older machines).
Last edited: