Kaspersky and MS flag the files nowIn that case, the analysis is wrong and Kaspersky and Bitdefender nagged the malware.
Question Steamunlocked malware?
- Thread starter likeastar20
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
Was flagged by Behavior Blocking before signatures too.Kaspersky and MS flag the files now
If it was clean on open tips then no. It's a UDS blockWas flagged by Behavior Blocking before signatures too.
On opentip it’s not clean. Flagged as UDS and BSS, which is strictly behavior.If it was clean on open tips then no. It's a UDS block
UDS is a behavior based detection.
Someone said it was. UDS is a cloud signature. Not behavioural.Norton said the installer is clean.
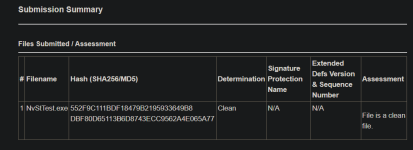
It's clean on opentip as well.

Kaspersky Threat Intelligence Portal
Kaspersky Threat Intelligence Portal allows you to scan files, domains, IP addresses, and URLs for threats, malware, virusesopentip.kaspersky.com
UDS is when a object is detected by behavioral detection, and then is converted into a UDS detect to prevent the attacks.Someone said it was. UDS is a cloud signature. Not behavioural.
Wrong file aswell, the Nulloy.zip is a UDS detection.Someone said it was. UDS is a cloud signature. Not behavioural.

Kaspersky Threat Intelligence Portal
Kaspersky Threat Intelligence Portal allows you to scan files, domains, IP addresses, and URLs for threats, malware, viruses
Last edited:
I'm taking a look at this sample in more detail tonight on workstation/lab. Maybe your right about the UDS.Wrong file aswell, the Nulloy.zip is a UDS detection.

Kaspersky Threat Intelligence Portal
Kaspersky Threat Intelligence Portal allows you to scan files, domains, IP addresses, and URLs for threats, malware, virusesopentip.kaspersky.com
It's not actually. It's mainly used for cloud-based early blacklisting which can be both automated and manual. It can automatically be derived from behavior blocking & ML models metadata, big data analysis but can be totally unrelated also. There were cases when even Kaspersky analyst manually created UDS signatures for samples I sent to them.UDS is a behavior based detection.
eg:
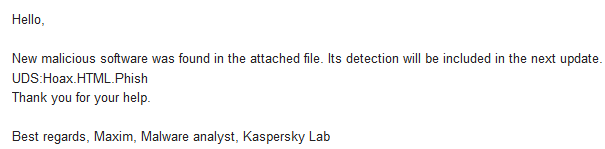
PDF’s always have weird detections, I see them have heuristic detections when it’s a signature. Anyways, the object was detected via automatic methods as opentip says it’s a Behavioral Stream Signature detection.It's not actually. It's mainly used for cloud-based early blacklisting which can be both automated and manual. It can automatically be derived from behavior blocking & ML models metadata, big data analysis but can be totally unrelated also. There were cases when even Kaspersky analyst manually created UDS signatures for samples I sent to them.
eg:
View attachment 278331
I believe according to their website and other people I’ve asked, UDS is a cloud based detection when malware is detected via other methods. For files like these, Ive never seen a UDS Signature, only automated detections.
Last edited:
Yes, completely possible for that to happen. I’ve never seen a signature have a UDS detection besides documents, and the one that they sent. Majority of the times it’s a automatic system in which PDM systems pickup an object, sending it to processing in KSN then creating a preventative cloud detection for the file.I've seen a PDF trigger PDM.Exploit. but that's their ML catching an adobe exploit.
Because no human actually took a look?Well, in that case, it definitely is evasive, bypassing Opentip, Intellix, and a lot of human researchers.
I myself don’t know how to code, nor really know how malware works, but how could it bypass human researchers?
Also, which file was it? I checked the opentip link someone sent and it’s currently listed as clean on Opentip with 1,000 users.
Maybe that company runs a triaged system?
I. E.
If only single file is received then direct to internal sandbox that's more sensitive than the public one. If the sandbox says Clean then inform the user that it's clean. Meanwhile flag the file for review with importance LOW
If more than 1 user but less than x reports it then perform the same as above but set importance to Normal
If major IT corporation or more than x users report it then inform the users to standby while the file is analyzed then flag the file with High Importance Requires Human in the loop
Ahh, didnt know thats how it works.Because no human actually took a look?
Maybe that company runs a triaged system?
I. E.
If only single file is received then direct to internal sandbox that's more sensitive than the public one. If the sandbox says Clean then inform the user that it's clean. Meanwhile flag the file for review with importance LOW
If more than 1 user but less than x reports it then perform the same as above but set importance to Normal
If major IT corporation or more than x users report it then inform the users to standby while the file is analyzed then flag the file with High Importance Requires Human in the loop
For us we think we are the most important people and our submissions should take priority. But for the person receiving your file they don't know you from a panicking old lady that saw a naked dude suddenly jump on her screen and being a good US bible belt evangelist she could not stand for such lude behavior from her computer! So she sent her whole download folder to the antivirus company for them to analyze.Ahh, didnt know thats how it works.
AV corporations receive thousands of emails daily with suspicious attachments. Only fraction of them are actually suspicious. But yet it's their duty to look at them all. So what to they do? They let the machines do the dirty work. Prime example: Stutnex was in the wild and part of the detection cloud for months. Before a curious analyst received an infected laptop and lo and behold Stutnex was one of the infections. Only then they decided to escalate and analyze and bam multi million dollar sabotage software was busted.
Last edited:
It's a dirty file. I'm sure they will agree. Let's see what the God and Goddess say. @Trident @cruelsister@cruelsister @Trident any thoughts?
Bitdefender added a signature for NvStTest.exe
Meanwhile, Norton said NvStTest.exe is clean.
Meanwhile, Norton said NvStTest.exe is clean.
Attachments
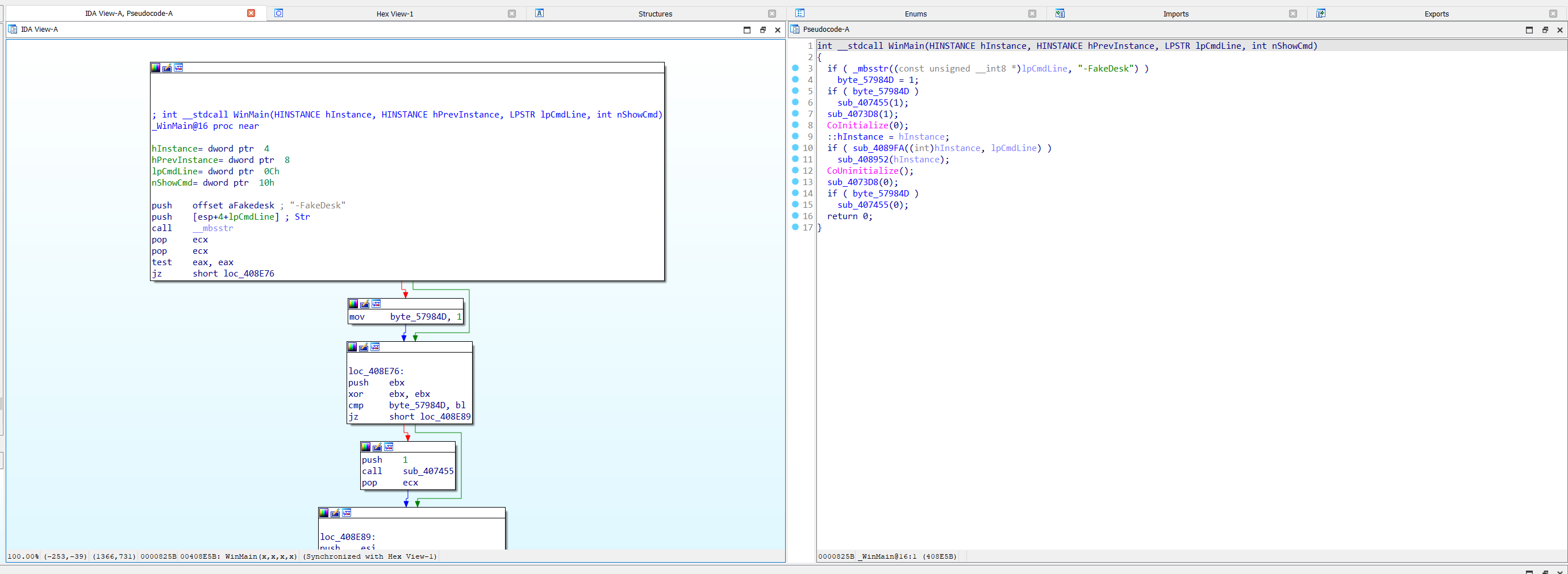
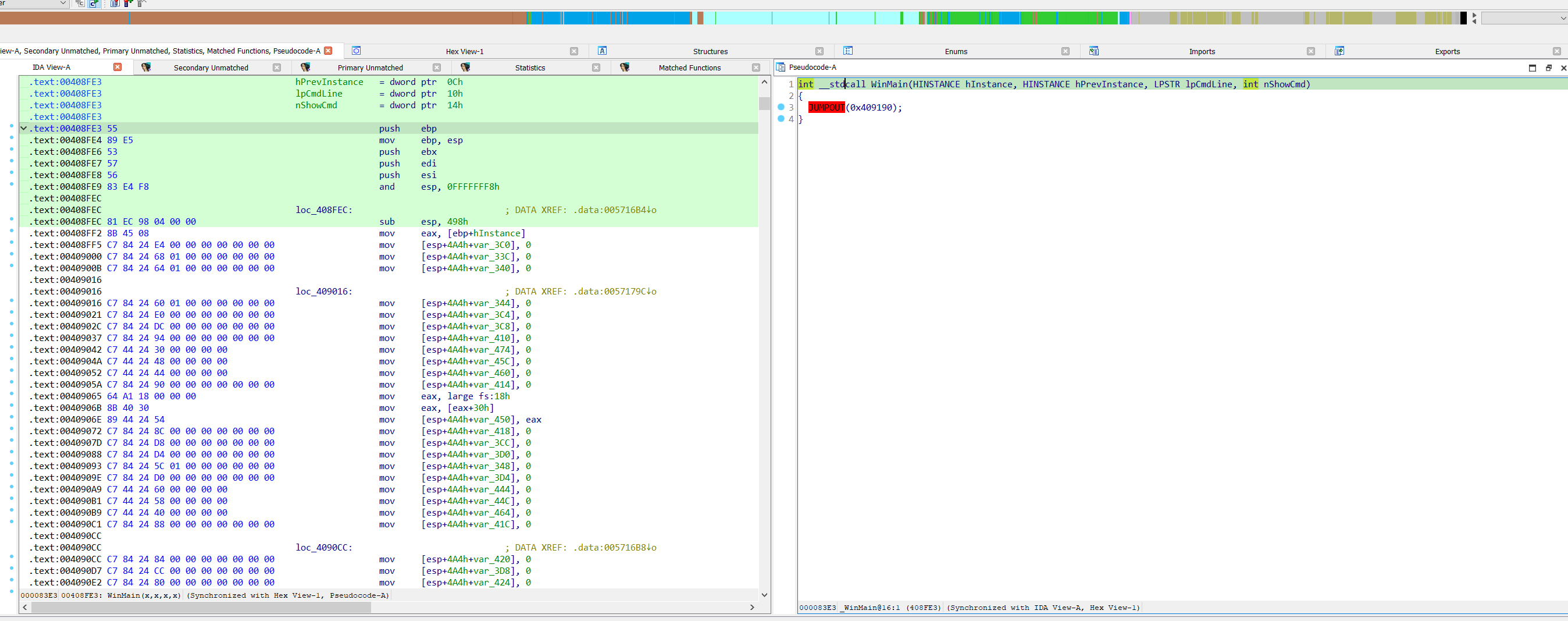
Hello there. I have not much time this weekend. But just from checking this file vs the original version's entry point, it is clearly patched. The patched code is unreadable because it manipulates the stack pointer. The original NvStTest in contrast is clearly readable. This patch alone is reason enough to declare it as malware because it is a modification that has nothing to do there and the file hasn't been signed by the publisher. @SkeletalDemise is very spot on with observations and analysis.
This blacksoul rule detects msvcp140.dll. I would not take it seriously.
Entry point of clean NvStTest:
Entry point of manipulated NvStTest (cannot be decompiled):
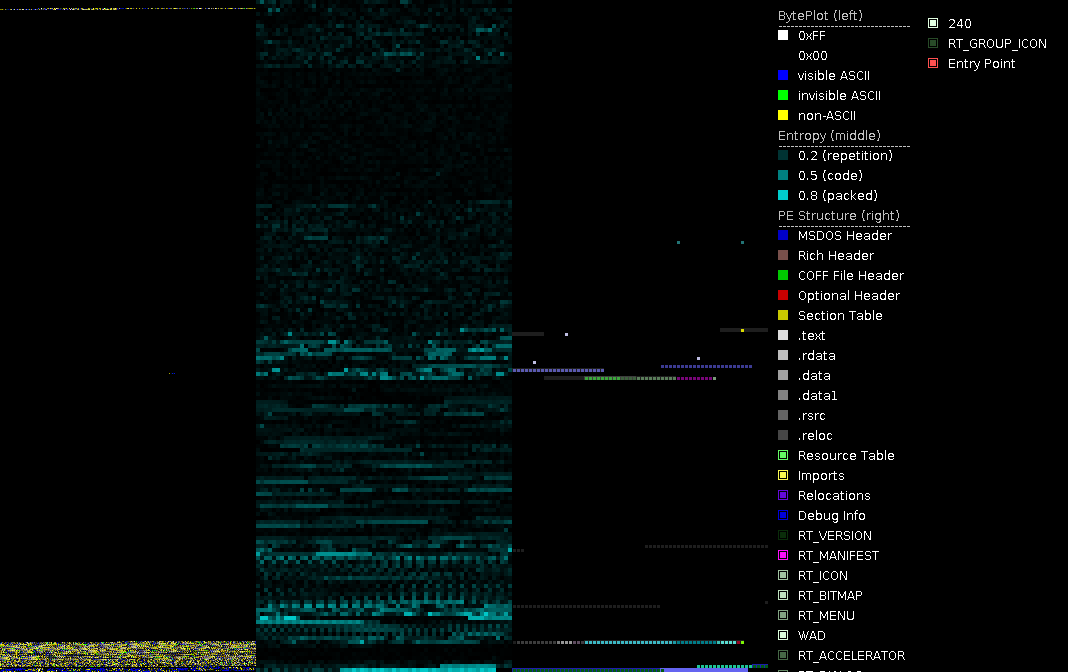
BinDiff of both files
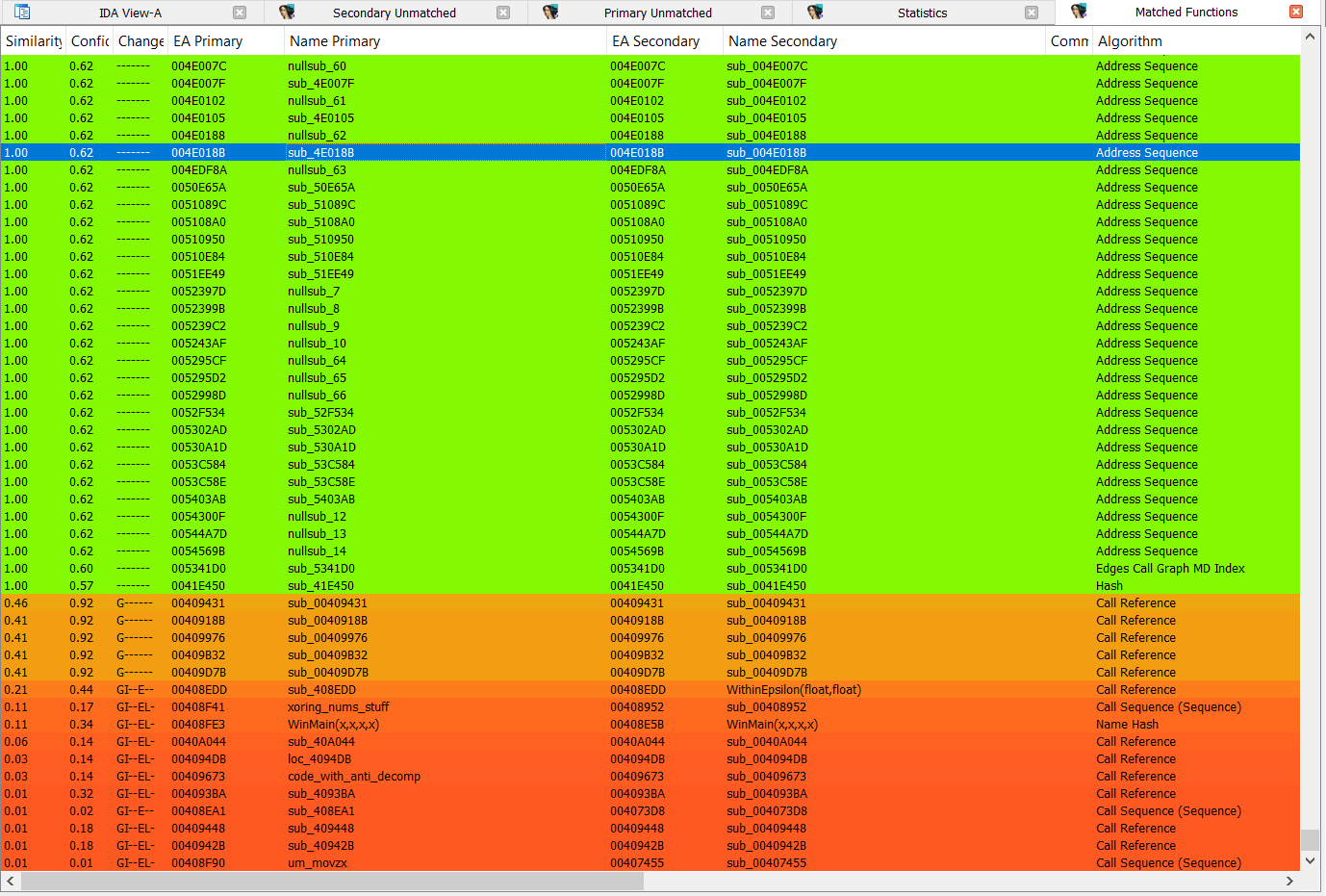
Diff for both files of PortEx, black byteplot on the left means same code/data. It is mostly the code near the entry point and some resources and the (missing) certificate that have been changed.
If this was a legitimate software update, you would expect something different:
Entry point of manipulated NvStTest (cannot be decompiled):
BinDiff of both files
Diff for both files of PortEx, black byteplot on the left means same code/data. It is mostly the code near the entry point and some resources and the (missing) certificate that have been changed.
If this was a legitimate software update, you would expect something different:
- not only entry point code changes
- certificate would be there
- code would be readable
- many functions with small differences due to recompilation (this file was not recompiled, some of the sections even have the same hash)
This blacksoul rule detects msvcp140.dll. I would not take it seriously.
Last edited:
You may also like...
-
Malware News Malware bypassed macOS Gatekeeper by abusing Apple's notarization proccess
- Started by enaph
- Replies: 1
-
Malware Analysis Tricky adware or malicious ?
- Started by likeastar20
- Replies: 10
-
Serious Discussion Orion Malware Cleaner (OMC) - By Trident
- Started by Trident
- Replies: 23
-
Serious Discussion The Necessity of Simulating the Full Malware Infection Chain for Security Suite Testing
- Started by harlan4096
- Replies: 3
-
Question My Asp.Net Website infected with some wired malware
- Started by thefrnd
- Replies: 3