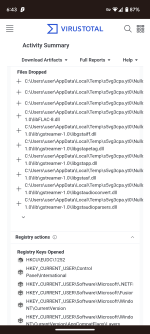
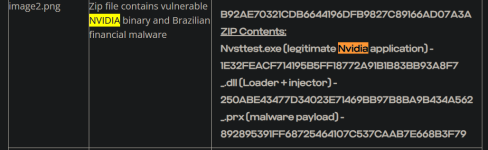
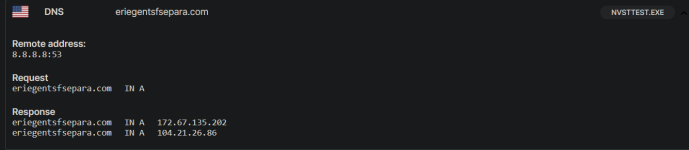
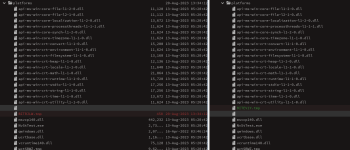
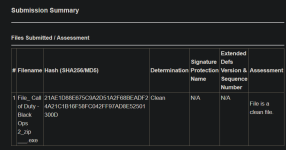
This Nulloy folder is dropped by another .exe as far as i know. Recently, I've seen some people get infected by this Nulloy malware. The original file seems to come from a steamunlocked redirect(not the actual downloded cracked game). BITRJLW.tmp & NvStTest.exe seem interesting. Asking @struppigel to take a look. On the VT community tab for NvStTest.exe, a community member says "Malware, usually associated with some kind of attempt to download a font that is an .exe"
 tria.ge
tria.ge
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
EDIT1: The file that dropped the Nulloy folder may have been this: VirusTotal
I only have the hash.
e5f4bab8de0352d77e4648c98ca00e17e0a97763d3a6b91dc0134e526836375d | Triage
Check this report malware sample e5f4bab8de0352d77e4648c98ca00e17e0a97763d3a6b91dc0134e526836375d, with a score of 7 out of 10.
EDIT1: The file that dropped the Nulloy folder may have been this: VirusTotal
I only have the hash.
Last edited: