Steven Liew Security Config
- Thread starter Steven Liew
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
M
Manzai
Hello 
1. Enable UAC, I recommend to enable
2. Install a pop-up blocker. For IE, I your recommend Simple Ad-block
3. Install Ccleaner . This software will remove the cookie and Browsing History.
1. Enable UAC, I recommend to enable
2. Install a pop-up blocker. For IE, I your recommend Simple Ad-block
3. Install Ccleaner . This software will remove the cookie and Browsing History.
I
illumination
I would enable UAC and upgrade your Eset to version 8, and disable realtime on Malwarebytes and just use MBAM as a on-demand... Other then, looks good..
Hello and welcome to MalwareTips!
1. Real-Time Protection:
First off all, update to ESET Smart Security 8 - http://www.eset.com/us/download/home/detail/family/5/ , then you can tweak it with the following settings:
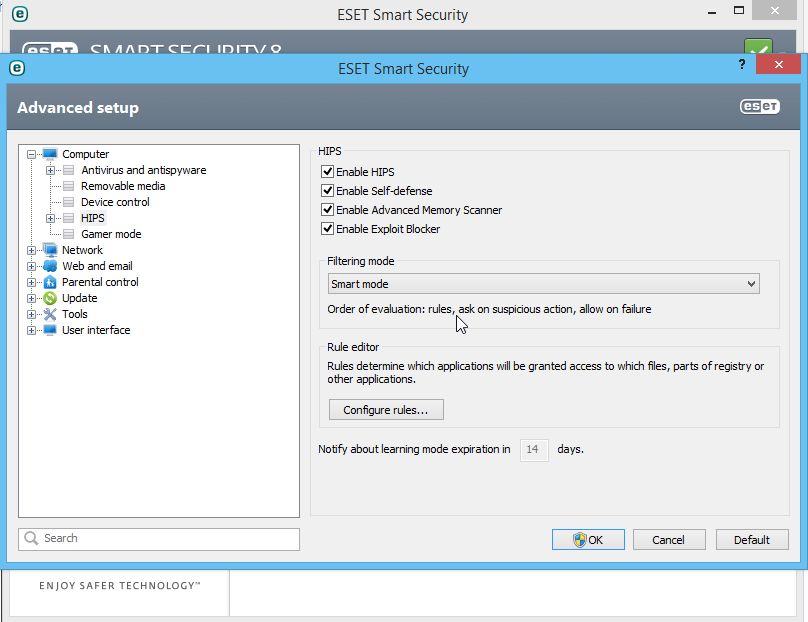
1. Enable "Smart mode" HIPS in ESET Smart Security.
2. Enable PUP detection in ESET Smart Security:
PUPs (potentially unwanted programs) are programs often offered when installing other programs (repacked freewares). They take the form of toolbars or adware.
uBlock - https://chrome.google.com/webstore/detail/µblock/cjpalhdlnbpafiamejdnhcphjbkeiagm?hl=en
You need an adblocker becauser apart from the simple fact that most ads are annoying, some of them might even lead you to adware or potentially unwanted programs. This add-on will block all the ads from a web page, making it look very clean and neat!
WOT (Web of Trust): https://addons.mozilla.org/en-US/firefox/addon/wot-safe-browsing-tool/
To help you avoid malicious sites you can use Web of Trust (WOT) a website rating browser plugin. After you add it to your browser make sure you only visit websites rated "Green" by WOT. Here is how it works:
3. Virtualization:
A virtualization software will allow you to browse the web or run another application in a completely safe environment. This is especially useful when visiting high-risk web sites, whether accidentally or deliberately, as the Web browser will be completely contained within the virtual environment, preventing any damage to your computer.
A sandbox can also be used to run any other applications which you think may be suspect - you can run the program inside the sandbox to determine whether or not it is safe while remaining completely protected against any malicious actions that it may try to carry out.
I strongly advise you to install Sandboxie and use it for when you're browsing the Internet or running shady or unknown programs. Sandboxie (Free/Paid) - link
Sandboxie runs your programs in an isolated space which prevents them from making permanent changes to other programs and data in your computer.
Always run suspicious of freshly downloaded files in a Sandboxie to verify that he download isn't compromised! Sandboxie will replicate perfectly your operating system so all the files should run without any problems in it.
If you learn how to properly use Sandboxie, then you really decrease your chances of gettings an infection, I'm always running my web browser sandbox just to be on the safe side.....
4. On-demand scanners
An on-demand scanners is a type of antivirus program that actively scans your computer for malware only when prompted to do so by the computer user, or by scheduling it as a time-specific task. Unlike a traditional antivirus, an on-demand scanner will NOT protect your computer in Real-Time.
Malwarebytes Anti-Malware and HitmanPro are two of the most known and used on-demand scanners. It's a good idea to have them installed on your machine, and perform regular scans with these anti-malware software.
Hitman Pro - Link
An on-demand scanner using multiple anti-malware engines and cloud technology. It offers unlimited free scanning but once you use it to remove detected malware it switches to a 30-day trial version. I recommend using it after you've scanned your hard-drive with the other products you have installed
5. Tips from MalwareTips to keep your computer clean
The single biggest factor in preventing a malware infection on your PC is YOU.
You don’t need expert knowledge or special training.You just need vigilance to avoid downloading and installing anything you do not understand or trust, no matter how tempting might be!
Below you can read , some tips on how to easily avoid a computer infection.Follow them and we can guarantee, that you’ll never have to deal with an infected PC.
Welcome... That's it for now.. I'm waiting for you reply for more..
1. Real-Time Protection:
First off all, update to ESET Smart Security 8 - http://www.eset.com/us/download/home/detail/family/5/ , then you can tweak it with the following settings:
1. Enable "Smart mode" HIPS in ESET Smart Security.
- Open ESET Smart Security or, click on Setup, or click the Protection status icon
Advanced setup.

- Expand Computer, and then click HIPS as seen below:
- Enable "Smart mode" HIPS
What Smart mode HIPS does: Only suspicious system events trigger a notification beyond the set of pre-defined rules in Automatic mode (operations such as system registry, active processes and programs).
2. Enable PUP detection in ESET Smart Security:
PUPs (potentially unwanted programs) are programs often offered when installing other programs (repacked freewares). They take the form of toolbars or adware.
- Double click on the Eset tray icon.
- Press F5 to access the advanced settings window.
- Go to "Computer" > "Antivirus and antispyware".
- In the "scanner options" section, check:
- "Enable detection of potentially unwanted applications".
- "Enable detection of potentially unsafe applications".
uBlock - https://chrome.google.com/webstore/detail/µblock/cjpalhdlnbpafiamejdnhcphjbkeiagm?hl=en
You need an adblocker becauser apart from the simple fact that most ads are annoying, some of them might even lead you to adware or potentially unwanted programs. This add-on will block all the ads from a web page, making it look very clean and neat!
WOT (Web of Trust): https://addons.mozilla.org/en-US/firefox/addon/wot-safe-browsing-tool/
To help you avoid malicious sites you can use Web of Trust (WOT) a website rating browser plugin. After you add it to your browser make sure you only visit websites rated "Green" by WOT. Here is how it works:
3. Virtualization:
A virtualization software will allow you to browse the web or run another application in a completely safe environment. This is especially useful when visiting high-risk web sites, whether accidentally or deliberately, as the Web browser will be completely contained within the virtual environment, preventing any damage to your computer.
A sandbox can also be used to run any other applications which you think may be suspect - you can run the program inside the sandbox to determine whether or not it is safe while remaining completely protected against any malicious actions that it may try to carry out.
I strongly advise you to install Sandboxie and use it for when you're browsing the Internet or running shady or unknown programs. Sandboxie (Free/Paid) - link
Sandboxie runs your programs in an isolated space which prevents them from making permanent changes to other programs and data in your computer.
Always run suspicious of freshly downloaded files in a Sandboxie to verify that he download isn't compromised! Sandboxie will replicate perfectly your operating system so all the files should run without any problems in it.
If you learn how to properly use Sandboxie, then you really decrease your chances of gettings an infection, I'm always running my web browser sandbox just to be on the safe side.....
4. On-demand scanners
An on-demand scanners is a type of antivirus program that actively scans your computer for malware only when prompted to do so by the computer user, or by scheduling it as a time-specific task. Unlike a traditional antivirus, an on-demand scanner will NOT protect your computer in Real-Time.
Malwarebytes Anti-Malware and HitmanPro are two of the most known and used on-demand scanners. It's a good idea to have them installed on your machine, and perform regular scans with these anti-malware software.
Hitman Pro - Link
An on-demand scanner using multiple anti-malware engines and cloud technology. It offers unlimited free scanning but once you use it to remove detected malware it switches to a 30-day trial version. I recommend using it after you've scanned your hard-drive with the other products you have installed
5. Tips from MalwareTips to keep your computer clean
The single biggest factor in preventing a malware infection on your PC is YOU.
You don’t need expert knowledge or special training.You just need vigilance to avoid downloading and installing anything you do not understand or trust, no matter how tempting might be!
Below you can read , some tips on how to easily avoid a computer infection.Follow them and we can guarantee, that you’ll never have to deal with an infected PC.
1. Avoid running programs that where downloaded from a untrustworthy source or don’t have a digital signature.
Before clicking the ‘Run‘ button make sure you know what the program is and always keep in mind from where you got it.
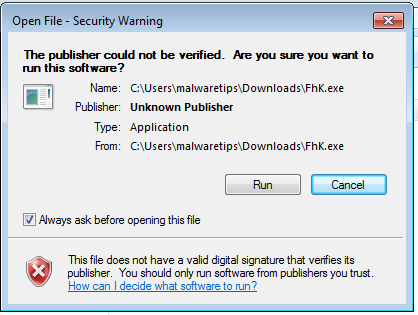
Everyone has seen this type of alert however most of the user for a reason or another, decide to ignore it and allow the file to run without any kind of restriction.
Files that don’t have a digital signature or were downloaded from a unknown source should always be treated as dangerous.
I strongly recommend that you check each file before allowing it to run :
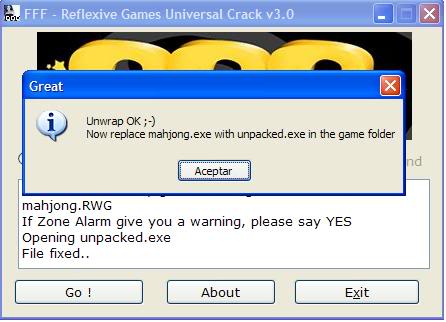
2.Avoid keygens,cracks and other warez
Keygen , cracks and patches are the most common ways of getting your PC infected.
I strongly advise you to avoid them, as there is little quality control in the world of illegal software, and it is easy for an attacker to name a piece of malware after a popular movie, album, or program to tempt you into downloading it.
3. Download files only from trusted sources.
You can drastically reduce the risk of an infection by knowing what and from where you are downloading a file.
We recommend that you install a site advisor like Web of Trust or Norton Safe Web, which will help you decide if the site is trustworthy or not.
As a general rule it’s recommended that you download files from known and reputable sites that have confirmed that the download is malware free.
If you are unsure about the quality of a download, leave the site and research the software you are being asked to install. If it is OK, you can always come back to site and install it. If it is not OK, you will avoid a malware headache.
4. Use common sense while online
Finding something on the internet does not guarantee that it is true. Anyone can publish information online, so before accepting a statement as fact or taking action, verify that the source is reliable.
If it’s sounds to good to be truth then most likely is!
You’ll not win the lottery and you’ll not get an amazing prize on the Internet so don’t fall for this type of scams.
Ignore emails or websites who promise you a great prize as there is always a catch behind this type of promises.
Completing a survey will not grant you a iPhone or 1000$ instead it will give the cyber criminals your personal details.
5. Keep your computer up-to-date and secure
Always update your OS or software when an update is available as this can greatly reduce the chances of an exploit.
Also keep in mind that a simple antivirus engine doesn’t do the job anymore, you need to have a layered system protection as malware threats are constantly changing and improving thus making the antivirus engine obsolete.
An antivirus engine, firewall , host intrusion prevention system, a site advisor and sandbox are security layers which every computer needs to be safe in today’s world.
You can build up your malware defenses with our help by starting a thread in our Security Configuration Wizard forum.
Another common mistake made by Windows users is to disable the User Account Control.
The way Microsoft found to keep security, comfort and function in balance by integrating User Account Control (UAC) that seamlessly, is one of the benefits Windows 7 offers.When using a Limited/Standard User Account , your user profile might still getting compromised, but not Windows 7 basic operating system in the background. Even your profile got hit, all your pictures, MP3 files or documents can be restored easily by logging in to another account that is not yet compromised.
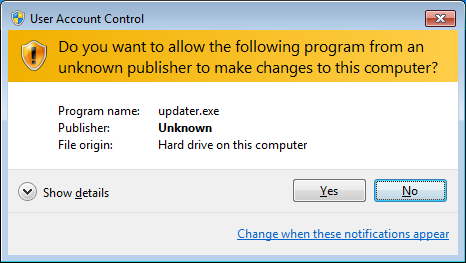
I strongly advise you to let this Windows feature enabled and pay a very close attention to this pop-ups , as this could save your PC from an infection.
Other Quick Security Tips :
Before clicking the ‘Run‘ button make sure you know what the program is and always keep in mind from where you got it.

Everyone has seen this type of alert however most of the user for a reason or another, decide to ignore it and allow the file to run without any kind of restriction.
Files that don’t have a digital signature or were downloaded from a unknown source should always be treated as dangerous.
I strongly recommend that you check each file before allowing it to run :
- Scan it with your antivirus.
- Scan it with an on-demad scanner (programs that you can install on your computer and use them only for scans) like HitmanPro and Malwarebytes Anti-Malware.
- Submit the file to virustotal.com, a site which will scan your program with the 43 known antivirus engines.
2.Avoid keygens,cracks and other warez
Keygen , cracks and patches are the most common ways of getting your PC infected.
I strongly advise you to avoid them, as there is little quality control in the world of illegal software, and it is easy for an attacker to name a piece of malware after a popular movie, album, or program to tempt you into downloading it.

3. Download files only from trusted sources.
You can drastically reduce the risk of an infection by knowing what and from where you are downloading a file.
We recommend that you install a site advisor like Web of Trust or Norton Safe Web, which will help you decide if the site is trustworthy or not.
As a general rule it’s recommended that you download files from known and reputable sites that have confirmed that the download is malware free.
If you are unsure about the quality of a download, leave the site and research the software you are being asked to install. If it is OK, you can always come back to site and install it. If it is not OK, you will avoid a malware headache.
4. Use common sense while online
Finding something on the internet does not guarantee that it is true. Anyone can publish information online, so before accepting a statement as fact or taking action, verify that the source is reliable.
If it’s sounds to good to be truth then most likely is!
You’ll not win the lottery and you’ll not get an amazing prize on the Internet so don’t fall for this type of scams.
Ignore emails or websites who promise you a great prize as there is always a catch behind this type of promises.
Completing a survey will not grant you a iPhone or 1000$ instead it will give the cyber criminals your personal details.
5. Keep your computer up-to-date and secure
Always update your OS or software when an update is available as this can greatly reduce the chances of an exploit.
Also keep in mind that a simple antivirus engine doesn’t do the job anymore, you need to have a layered system protection as malware threats are constantly changing and improving thus making the antivirus engine obsolete.
An antivirus engine, firewall , host intrusion prevention system, a site advisor and sandbox are security layers which every computer needs to be safe in today’s world.
You can build up your malware defenses with our help by starting a thread in our Security Configuration Wizard forum.
Another common mistake made by Windows users is to disable the User Account Control.
The way Microsoft found to keep security, comfort and function in balance by integrating User Account Control (UAC) that seamlessly, is one of the benefits Windows 7 offers.When using a Limited/Standard User Account , your user profile might still getting compromised, but not Windows 7 basic operating system in the background. Even your profile got hit, all your pictures, MP3 files or documents can be restored easily by logging in to another account that is not yet compromised.

I strongly advise you to let this Windows feature enabled and pay a very close attention to this pop-ups , as this could save your PC from an infection.
Other Quick Security Tips :
- Uninstall Java if you don’t really need it as this is one of the most exploited programs.
- Use complex passwords for you online accounts – Passwords should be a minimum of eight characters and contain a combination of letters (uppercase/lowercase), numbers, and special symbols (!,@, #, &, %,*)
- Do not open email attachments from unknown sources or files sent through an instant messenger
- Don’t give out your details to people who don’t have a legitimate need to know them.
- While on social networks it’s best to be reserved when allowing people to see your profile or updates.
Welcome... That's it for now.. I'm waiting for you reply for more..
You may also like...
-
Advanced Plus Security Devjit’s Gaming PC 2026
- Started by devjitdutta2025
- Replies: 44
-
Advanced Plus Security Divine_Barakah's Second Laptop Security Config
- Started by Divine_Barakah
- Replies: 93
-
Advanced Plus Security eonline 2025 security config
- Started by eonline
- Replies: 0
-
Question Does Thunderbird download spam emails on the computer?
- Started by IceLion36
- Replies: 15
-