Are u sure about max block any unrecognized file by microsoft? Is first time i hear that. Maybe @Andy Ful can confirm this.Why windows defender on max won't allow any unrecognized file by Microsoft to run it is based upon the telemetry windows collect.
By doing this 99.999% of malware will be blocked.
Only downside is false positives around unpopular software.
About other security software you mentioned voodoo shield would be a good alternative.
Symantec Endpoint Unmanaged without time limit
- Thread starter Vitali Ortzi
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Are u sure about max block any unrecognized file by microsoft? Is first time i hear that. Maybe @Andy Ful can confirm this.
Using the Maximum Protection Level
The Max Protection Level blocks anything suspicious via Attack Surface Reduction, Controlled Folder Access, SmartScreen (set to block) and cloud level (set to block) - Defender Security Center is hidden.
K but for what understand are 2 different things, block 100% any file unrecognized means be 100% protected (only way is if windows whitelist malware, like comodo did xD), other thing is block different things with ASR, etc, etc (not sure if give 100% protection).Using the Maximum Protection Level
The Max Protection Level blocks anything suspicious via Attack Surface Reduction, Controlled Folder Access, SmartScreen (set to block) and cloud level (set to block) - Defender Security Center is hidden.
If is how u tell there is no match vs others av vendors LOL
Are u sure about max block any unrecognized file by microsoft? Is first time i hear that. Maybe @Andy Ful can confirm this.
Never said it gives 100% protection .K but for what understand are 2 different things, block 100% any file unrecognized means be 100% protected (only way is if windows whitelist malware, like comodo did xD), other thing is block different things with ASR, etc, etc (not sure if give 100% protection).
But so far no malware in the wild to my knowledge was able to bypass the max settings.
About unrecognized files I was a little misleading it's actually every unknown executable by max cloud level blocking.
Yes that was my deduction.Never said it gives 100% protection .
But so far no malware in the wild to my knowledge was able to bypass the max settings.
About unrecognized files I was a little misleading it's actually every unknown executable.
I didnt thought the score was so high, maybe some1 more can confirm if only few/no malware was able to bypass windows defender max settings.
Work only with unknown executables? Or more type of file too?
Chri.Mi and Vitali Ortzi,
There were malware samples that could bypass ConfigureDefender MAX Protection Level via scripts, especially .jar (Java) and Python (.py). They were usually mitigated after executing the EXE payloads. Anyway, scripts can rarely bypass the MAX settings.
There were malware samples that could bypass ConfigureDefender MAX Protection Level via scripts, especially .jar (Java) and Python (.py). They were usually mitigated after executing the EXE payloads. Anyway, scripts can rarely bypass the MAX settings.
What about a malicious dll /dll hijack?Chri.Mi and Vitali Ortzi,
There were malware samples that could bypass ConfigureDefender MAX Protection Level via scripts, especially .jar (Java) and Python (.py). They were usually mitigated after executing the EXE payloads. Anyway, scripts can rarely bypass the MAX settings.
WD like most AVs, checks DLLs (for example when you open the folder) similarly to EXE files.What about a malicious dll /dll hijack?
Anyway, there are differences between running EXEs and DLLs that can be probably used in another way to bypass advanced AV features.
Edit.
It is probable that DLL Search Order Hijacking can be used to bypass the WD Sandbox in the cloud (part of BAFS in Windows E5) and similar sandboxes of other AVs.
Last edited:
I uninstalled this on my second computer too. Proactive detection settings are resetting back to normal by itself. I had no problems like this even with buggy comodo. I'm now using Win Defender at tweaked settings but thinking to install Avast Free.
Unfortunately, you didn't run the self-diagnosis tool.I uninstalled this on my second computer too. Proactive detection settings are resetting back to normal by itself. I had no problems like this even with buggy comodo. I'm now using Win Defender at tweaked settings but thinking to install Avast Free.
But yes windows defender is pretty strong.
About Avast it's not as good as Symantec but since you had issues it's totally understandable to get rid of it I would have done the same .
anyone else who encounters an issue please run the Symantec diagnosis tool before giving up on SEP and of course send results.
Yeah I was gonna use that diagnosis tool but give up after. I want to try different programs after all.Unfortunately, you didn't run the self-diagnosis tool.
But yes windows defender is pretty strong.
About Avast it's not as good as Symantec but since you had issues it's totally understandable to get rid of it I would have done the same .
But please anyone else please run the Symantec diagnosis tool before giving up on SEP.
Have fun!Yeah I was gonna use that diagnosis tool but give up after. I want to try different programs after all.
I don't see any "SEP tools" on Comss. ru to download and use Deception. dat.You forgot to import deception policies .
Download SEP tools from Cmoss .ru
And import Deception .dat files to SPEM .
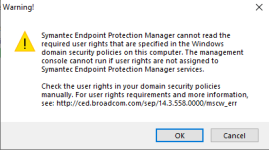
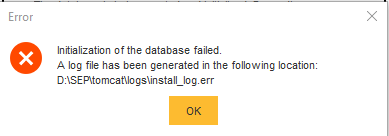
I was interested in the endpoint manager as I am using SEP currently, I went to install it but because im using the home version if windows I cant access gpedit, meaning I cant fix this error saying it cant read required user rights , I can get past it and install it, but after that I get another error saying that it failed to intialize the databases, I was wondering if there was an way to fix this without gpedit?
Attachments
First, since Symantec endpoint protection manager is a management server of SEP.I was interested in the endpoint manager as I am using SEP currently, I went to install it but because im using the home version if windows I cant access gpedit, meaning I cant fix this error saying it cant read required user rights , I can get past it and install it, but after that I get another error saying that it failed to intialize the databases, I was wondering if there was an way to fix this without gpedit?
You are supposed to use a dedicated PC to run as a server for SPEM to work properly.
About using Windows Home as a management server of SEP(SPEM).
I'm not entirely sure it will even work on your Microsoft Windows Home device , since it was built primary for windows server in mind.
Even though I have encountered no issues running SPEM on a Windows LTSC machine as well .
And please run this tool if you experience any issues.
http://ced.broadcom.com/symhelp/2/dl
Oh, since you don't have the required SLF file I will send you the SLF file in a PM wait a moment.
And in case you want to uninstall please download cleanwipe from cmoss.ru to remove SPEM/SEP from your current machine.
Last edited:
If you are installing sep manager in VM, try VMware with 3 cores and 3 gb ram to virtual pc. ( 2 cores and 2 gb ram seems to be too slow for my liking)..with 3 cores and 3 gb ram it's super smooth.
I'm using Symantec Endpoint Protection Firewall and IDS modules only and now my Webroot SecureAnywhere flags one of Symantec .dll files (GEDatastore.dll) as a Trojan.Gen.2. Sigh. Submitted it as a FP.
UPDATE: It's now whitelisted
Hi,
I've added in/out block rule for mshta.exe. Is there any other "lolbins" network rules that is recommended to block?
Regards,
-sepik
UPDATE: It's now whitelisted
Hi,
I've added in/out block rule for mshta.exe. Is there any other "lolbins" network rules that is recommended to block?
Regards,
-sepik
Last edited:
Where you able to modify the rules via unmanged client?Hi,
I've added in/out block rule for mshta.exe. Is there any other "lolbins" network rules that is recommended to block?
Regards,
-sepik
Anyway use all the firewall related rules that are presented in H_C firewall hardening .
Thanks I will recommend this Configuration on over 4 threaded computers.If you are installing sep manager in VM, try VMware with 3 cores and 3 gb ram to virtual pc. ( 2 cores and 2 gb ram seems to be too slow for my liking)..with 3 cores and 3 gb ram it's super smooth.
And Wich windows version and license type you have been running on the SPEM VM ?
Last edited:
windows 10 pro, unlicensed.Thanks I will recommend this Configuration on over 4 threaded computers.
And Wich windows version and license type you have been running on the SPEM VM ?
You may also like...
-
App Review Cisco AMP Endpoint Antivirus 2025
- Started by Shadowra
- Replies: 7
-
-
BReleasing Windows 11, version 25H2 to the Release Preview Channel
- Started by Brandon LeBlanc
- Replies: 4
-
Serious Discussion Simple Steps to Secure Your Windows 11 PC
- Started by Divergent
- Replies: 0