On normal PC, I never had any serious problems, maybe a flashing explorer or a bad task manager, but usually fixed within a week. I have not had BSOD since Vista, except caused by me.Is Canary build very buggy? Do you use this on your test pc only?
Advanced Security TairikuOkami's Configuration 202x
- Thread starter TairikuOkami
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Last updated
- Jan 31, 2026
- How it's used?
- For home and private use
- Operating system
- Windows 11
- On-device encryption
- N/A
- Log-in security
- Biometrics (Windows Hello PIN, TouchID, Face, Iris, Fingerprint)
- Security updates
- Allow security updates and latest features
- Update channels
- Allow beta system updates
- User Access Control
- Always notify
- Smart App Control
- Off
- Network firewall
- Enabled
- About WiFi router
- ISP Controlled Router
- Real-time security
- Firewall security
- Microsoft Defender Firewall with Advanced Security
- About custom security
- Disabled IPv6, PS, WSH. Blocked TCP ports 1-65535 except a select few
Detailed info: Windows Setup 1 + Windows Setup 2 + Windows Tweaks

- Periodic malware scanners
- Windows Repair Toolbox (Malware removal): Autoruns + SophosClean + NPE
- Malware sample testing
- I do not participate in malware testing
- Environment for malware testing
- N/A
- Browser(s) and extensions
- Brave for Google/YouTube
Chromium for Streaming
LibreWolf for Facebook
Microsoft Edge
Code:taskkill /im msedge.exe /f taskkill /im msedgewebview2.exe /f rem Run Wise Disk Cleaner start "" /wait "%ProgramFiles(x86)%\Wise\Wise Disk Cleaner\WiseDiskCleaner.exe" -a -all rem Run Wise Registry Cleaner start "" /wait "%ProgramFiles(x86)%\Wise\Wise Registry Cleaner\WiseRegCleaner.exe" -a -all rem Trim Some Edges - edge://settings/privacy/cookies/AllCookies rd "%ProgramFiles(x86)%\Microsoft\EdgeUpdate\Download" /s /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\*history*." /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\AccountBookmarks" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\arbitration_service_config.json" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\BookmarkMergedSurfaceOrdering" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\BrowsingTopicsSiteData" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\BrowsingTopicsSiteData-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\BrowsingTopicsState" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Custom Dictionary.txt" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\DashTrackerDatabase" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\DashTrackerDatabase-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\default_cloud_config.json" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\DIPS" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\DIPS-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Extension Cookies" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\ExtensionActivityComp" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\ExtensionActivityComp-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\ExtensionActivityEdge" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\ExtensionActivityEdge-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\HubApps" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\HubApps Icons" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\HubApps Icons-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\InterestGroups" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\LOG" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\LOG.old" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Login Data" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Login Data-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\MediaDeviceSalts" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\MediaDeviceSalts-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Network Action Predictor" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Network Action Predictor-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Network Persistent State" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\PreferredApps" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\PrivateAggregation" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\PrivateAggregation-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Reporting and NEL" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Reporting and NEL-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\QuotaManager" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\QuotaManager-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\SharedStorage" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Shortcuts" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Shortcuts-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Top Sites" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Top Sites-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\uu_host_config" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Visited Links" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Vpn Tokens" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Vpn Tokens-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\WebAssistDatabase" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\WebAssistDatabase-journal" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Web Data" /s /f /q del "%LocalAppData%\Microsoft\Edge\User Data\Default\Web Data-journal" /s /f /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Asset Store" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\AssistanceHome" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\AutofillAiModelCache" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\AutofillStrikeDatabase" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\blob_storage" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\BudgetDatabase" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Cache" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\ClientCertificates" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Code Cache" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Collections" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\commerce_subscription_db" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Continuous Migration" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\databases" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\DawnGraphiteCache" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\DawnWebGPUCache" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\DNR Extension Rules" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\discount_infos_db" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\discounts_db" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Download Service" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\DualEngine" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgeCoupons" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgeEDrop" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgeHubAppUsage" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgeJourneys" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgePassageEmbeddings" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgePushStorageWithWinRt" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgeTravel" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgeUserUsage" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EdgeWallet" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\EntityExtraction" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Extensions" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Extension Rules" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Extension Scripts" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Extension State" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Feature Engagement Tracker" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\GPUCache" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Feedback Reports" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\File System" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\IndexedDB" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\JumpListIconsRecentClosed" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\JumpListIconsRecentWorkspacesV2" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\JumpListIconsTopSites" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Local Extension Settings" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Local Storage" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Managed Extension Settings" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\MediaFoundationCdmStore" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Nurturing" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\optimization_guide_hint_cache_store" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\optimization_guide_model_metadata_store" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\OptimizationGuideAssetStore.db" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\parcel_tracking_db" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Password_Diagnostics" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Pdf" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\PDF Restore Data" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\PersistentOriginTrials" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Platform Notifications" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\PriceComparison" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Safe Browsing Network" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Segmentation Platform" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\SemanticEncoder.db" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Service Worker" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Session Storage" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Sessions" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Settings Search" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Shared Dictionary" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\shared_proto_db" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Site Characteristics Database" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Storage" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Sync App Settings" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Sync Data" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Sync Extension Settings" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\VideoDecodeStats" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\WebrtcVideoStats" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Web Applications" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\WebStorage" /s /q rd "%LocalAppData%\Microsoft\Edge\User Data\Default\Workspaces" /s /qrem Disabled
rem edge://flags/#allow-all-sites-to-initiate-mirroring
rem edge://flags/#edge-compose
rem edge://flags/#edge-copilot-mode
rem edge://flags/#edge-copilot-mode-profile-toggle
rem edge://flags/#edge-copilot-vision
rem edge://flags/#edge-llm-on-device-model-performance-param
rem edge://flags/#edge-ntp-composer-allow-copilot-search
rem edge://flags/#edge-ntp-composer-feed-integration
rem edge://flags/#edge-omnibox-commercial-copilot-chat
rem edge://flags/#edge-omnibox-ui-hide-steady-state-url-scheme
rem edge://flags/#edge-omnibox-ui-hide-steady-state-url-trivial-subdomains
rem edge://flags/#edge-optin-experimentation
rem edge://flags/#edge-rounded-containers
rem edge://flags/#edge-visual-rejuv-mica
rem edge://flags/#enable-force-dark
rem edge://flags/#enable-quic
rem edge://flags/#enable-windows-gaming-input-data-fetcher
rem edge://flags/#media-router-cast-allow-all-ips
rem edge://flags/#prefetch-new-tab-page-trigger
rem edge://flags/#ui-disable-partial-swap
rem Enabled
rem edge://flags/#disallow-doc-written-script-loads
rem edge://flags/#enable-standard-device-bound-session-credentials
rem edge://flags/#enable-tls13-early-data
rem edge://flags/#local-network-access-check
rem edge://flags/#origin-keyed-processes-by-default
rem edge://flags/#strict-origin-isolationrem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem Microsoft Edge release notes for Beta Channel
rem Microsoft Edge release notes for Stable Channel
rem Microsoft Edge Browser Policy Documentation
rem edge://policy
rem reg delete "HKCU\Software\Policies\Microsoft\Edge" /f
rem reg delete "HKLM\Software\Policies\Microsoft\Edge" /f
rem ________________________________________________________________________________________
rem 1 - Allow the audio sandbox to run
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "AudioSandboxEnabled" /t REG_DWORD /d "1" /f
rem 1 - Blocks external extensions from being installed
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "BlockExternalExtensions" /t REG_DWORD /d "1" /f
rem 1 - Allow pages to use the built-in AI APIs
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "BuiltInAIAPIsEnabled" /t REG_DWORD /d "0" /f
rem 1 - Compose is enabled for writing on the web
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ComposeInlineEnabled" /t REG_DWORD /d "0" /f
rem 1 - AllowJavaScriptJit / 2 - BlockJavaScriptJit (Do not allow any site to run JavaScript JIT)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultJavaScriptJitSetting" /t REG_DWORD /d "0" /f
rem 1 - Allow users to open files using the DirectInvoke protocol
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DirectInvokeEnabled" /t REG_DWORD /d "0" /f
rem 1 - Disable taking screenshots
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DisableScreenshots" /t REG_DWORD /d "1" /f
rem 1 - DNS interception checks enabled
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DNSInterceptionChecksEnabled" /t REG_DWORD /d "0" /f
rem 1 - Captures the searches user does on third party search providers
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "Edge3PSerpTelemetryEnabled" /t REG_DWORD /d "0" /f
rem 1 - Machine learning powered autofill suggestions
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EdgeAutofillMlEnabled" /t REG_DWORD /d "0" /f
rem 1 - Drop lets users send messages or files to themselves
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EdgeEDropEnabled" /t REG_DWORD /d "0" /f
rem 1 - Control access to AI-enhanced search in History
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EdgeHistoryAISearchEnabled" /t REG_DWORD /d "0" /f
rem 1 - Microsoft Edge will attempt to connect to the Microsoft Edge management service to download and apply policy assigned to the Azure AD account of the user
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EdgeManagementEnabled" /t REG_DWORD /d "0" /f
rem 1 - If you enable this policy, users will be able to access the Microsoft Edge Workspaces feature
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EdgeWorkspacesEnabled" /t REG_DWORD /d "0" /f
rem 1 - Allow Google Cast to connect to Cast devices on all IP addresses (Multicast), Edge trying to connect to 239.255.255.250 via UDP port 1900
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EnableMediaRouter" /t REG_DWORD /d "0" /f
rem The Experimentation and Configuration Service is used to deploy Experimentation and Configuration payloads to the client / 0 - RestrictedMode / 1 - ConfigurationsOnlyMode / 2 - FullMode
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ExperimentationAndConfigurationServiceControl" /t REG_DWORD /d "0" /f
rem 1 - Allows Microsoft Edge to prompt the user to switch to the appropriate profile when Microsoft Edge detects that a link is a personal or work link
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "GuidedSwitchEnabled" /t REG_DWORD /d "0" /f
rem 1 - Hide restore pages dialog after browser crash
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "HideRestoreDialogEnabled" /t REG_DWORD /d "1" /f
rem 1 - Show Hubs Sidebar
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "HubsSidebarEnabled" /t REG_DWORD /d "0" /f
rem 0 -InPrivate mode available / 1 - disabled / 2 - forced
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "InPrivateModeAvailability" /t REG_DWORD /d "1" /f
rem 1 - Allow sites to be reloaded in Internet Explorer mode (IE mode)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "InternetExplorerIntegrationReloadInIEModeAllowed" /t REG_DWORD /d "0" /f
rem 1 - Enable IPv6 reachability check override
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "IPv6ReachabilityOverrideEnabled" /t REG_DWORD /d "0" /f
rem Control whether Microsoft 365 Copilot Chat shows in the Microsoft Edge for Business toolbar
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "Microsoft365CopilotChatIconEnabled" /t REG_DWORD /d "0" /f
rem 1 - Shows content promoting the Microsoft Edge Insider channels on the About Microsoft Edge settings page
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "MicrosoftEdgeInsiderPromotionEnabled" /t REG_DWORD /d "0" /f
rem 1 - Mouse Gesture Enabled
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "MouseGestureEnabled" /t REG_DWORD /d "0" /f
rem 1 - Microsoft Edge built-in PDF reader powered by Adobe Acrobat enabled
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NewPDFReaderEnabled" /t REG_DWORD /d "0" /f
rem 1 - The network service process will run sandboxed, but it will block all cookies, you will be logged out instantly, till you disable it
rem reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NetworkServiceSandboxEnabled" /t REG_DWORD /d "1" /f
rem 1 - Hide the default top sites from the new tab page
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NewTabPageHideDefaultTopSites" /t REG_DWORD /d "1" /f
rem 1 - Enable QR Code Generator
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "QRCodeGeneratorEnabled" /t REG_DWORD /d "0" /f
rem 1 - Allow QUIC protocol
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "QuicAllowed" /t REG_DWORD /d "0" /f
rem 1 - Enable Read Aloud feature in Microsoft Edge
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ReadAloudEnabled" /t REG_DWORD /d "0" /f
rem 1 - Allow remote debugging
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "RemoteDebuggingAllowed" /t REG_DWORD /d "0" /f
rem 1 - Launches Renderer processes into an App Container for additional security benefits
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "RendererAppContainerEnabled" /t REG_DWORD /d "1" /f
rem 0 - Enable search in sidebar / 1 - DisableSearchInSidebarForKidsMode / 2 - DisableSearchInSidebar
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SearchInSidebarEnabled" /t REG_DWORD /d "2" /f
rem 1 - Search for image enabled
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SearchForImageEnabled" /t REG_DWORD /d "0" /f
rem 1 - Allow screen capture
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ScreenCaptureAllowed" /t REG_DWORD /d "0" /f
rem 1 - Allow notifications to set Microsoft Edge as default PDF reader
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ShowPDFDefaultRecommendationsEnabled" /t REG_DWORD /d "0" /f
rem 1 - Enable tab preview on hover
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ShowTabPreviewEnabled" /t REG_DWORD /d "0" /f
rem 1 - The policy can be used to prevent users from opting out of the default behavior of isolating all sites
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SitePerProcess" /t REG_DWORD /d "1" /f
rem 1 - Allow Speech Recognition
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SpeechRecognitionEnabled" /t REG_DWORD /d "0" /f
rem 1 - Users can drag a link, or text on a webpage
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SuperDragDropEnabled" /t REG_DWORD /d "0" /f
rem 1 - URL reporting in Edge diagnostic data enabled
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "UrlDiagnosticDataEnabled" /t REG_DWORD /d "0" /f
rem 1 - Edge User Data Profile Location
rem reg add "HKLM\Software\Policies\Microsoft\Edge" /v "UserDataDir" /t REG_SZ /d "Z:\Edge\User Data" /f
rem 1 - Allow video capture
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "VideoCaptureAllowed" /t REG_DWORD /d "0" /f
rem 1 - Wallet Donation Enabled
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "WalletDonationEnabled" /t REG_DWORD /d "0" /f
rem 1 - DNS-based WPAD optimization (Web Proxy Auto-Discovery)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "WPADQuickCheckEnabled" /t REG_DWORD /d "0" /f
rem 0 - Prevent Desktop Shortcut creation upon install default
reg add "HKLM\Software\Policies\Microsoft\EdgeUpdate" /v "CreateDesktopShortcutDefault" /t REG_DWORD /d "0" /f
reg add "HKLM\Software\Policies\Microsoft\EdgeUpdate" /v "CreateDesktopShortcut{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}" /t REG_DWORD /d "0" /f
reg add "HKLM\Software\Policies\Microsoft\EdgeUpdate" /v "RemoveDesktopShortcutDefault" /t REG_DWORD /d "1" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem ..................................... Appearances ......................................
rem 0 - Show share button
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ConfigureShare" /t REG_DWORD /d "1" /f
rem 1 - Show Collections button
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EdgeCollectionsEnabled" /t REG_DWORD /d "0" /f
rem 1 - Extensions Performance Detector enabled
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ExtensionsPerformanceDetectorEnabled" /t REG_DWORD /d "0" /f
rem 1 - Show favorites bar
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "FavoritesBarEnabled" /t REG_DWORD /d "1" /f
rem 1 - The performance detector detects tab performance issues and recommends actions to fix the performance issues
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "PerformanceDetectorEnabled" /t REG_DWORD /d "0" /f
rem 1 - Pin browser essentials toolbar button
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "PinBrowserEssentialsToolbarButton" /t REG_DWORD /d "0" /f
rem 1 - Show mini menu when selecting text
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "QuickSearchShowMiniMenu" /t REG_DWORD /d "0" /f
rem 1 - Always show the Downloads button on the toolbar
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ShowDownloadsToolbarButton" /t REG_DWORD /d "0" /f
rem 1 - Show home button
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ShowHomeButton" /t REG_DWORD /d "0" /f
rem 1 - nable split screen feature
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SplitScreenEnabled" /t REG_DWORD /d "0" /f
rem 1 - Show feedback button
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "UserFeedbackAllowed" /t REG_DWORD /d "0" /f
rem 1 - Show tab actions menu (Show vertical tabs)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "VerticalTabsAllowed" /t REG_DWORD /d "0" /f
rem 1 - Show web capture button
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "WebCaptureEnabled" /t REG_DWORD /d "0" /f
rem ________________________________________________________________________________________
rem 1 - Enables background updates to the list of available templates for Collections and other features that use templates
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "BackgroundTemplateListUpdatesEnabled" /t REG_DWORD /d "0" /f
rem 1 - Enable the Search bar
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SearchbarAllowed" /t REG_DWORD /d "0" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem .............................. Cookies and site permissions ............................
rem PDF Documents
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "AlwaysOpenPdfExternally" /t REG_DWORD /d "1" /f
rem Ads setting for sites with intrusive ads / 1 - Allow ads on all sites / 2 - Block ads on sites with intrusive ads. (Default value)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "AdsSettingForIntrusiveAdsSites" /t REG_DWORD /d "1" /f
rem Clipboard / 2 - BlockClipboard / 3 - AskClipboard
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultClipboardSetting" /t REG_DWORD /d "2" /f
rem File Editing / 2 - BlockFileSystemRead / 3 - AskFileSystemRead
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultFileSystemReadGuardSetting" /t REG_DWORD /d "2" /f
rem File Editing / 2 - BlockFileSystemWrite / 3 - AskFileSystemWrite
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultFileSystemWriteGuardSetting" /t REG_DWORD /d "2" /f
rem Location / 1 - AllowGeolocation / 2 - BlockGeolocation / 3 - AskGeolocation
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultGeolocationSetting" /t REG_DWORD /d "2" /f
rem Insecure Content / 2 - BlockInsecureContent / 3 - AllowExceptionsInsecureContent
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultInsecureContentSetting" /t REG_DWORD /d "2" /f
rem Notifications / 1 - AllowNotifications / 2 - BlockNotifications / 3 - AskNotifications
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultNotificationsSetting" /t REG_DWORD /d "2" /f
rem Motion or light sensors / 1 - AllowSensors / 2 - BlockSensors
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultSensorsSetting" /t REG_DWORD /d "2" /f
rem Serial ports / 2 - BlockSerial / 3 - AskSerial
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultSerialGuardSetting" /t REG_DWORD /d "2" /f
rem USB Devices / 2 - BlockWebUsb / 3 - AskWebUsb
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultWebUsbGuardSetting" /t REG_DWORD /d "2" /f
rem ________________________________________________________________________________________
rem 1 - Allow audio capture
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "AudioCaptureAllowed" /t REG_DWORD /d "0" /f
rem Bluetooth / 2 - BlockWebBluetooth / 3 - AskWebBluetooth
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultWebBluetoothGuardSetting" /t REG_DWORD /d "2" /f
rem Access to HID devices via the WebHID API / 2 - BlockWebHid / 3 - AskWebHid
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultWebHidGuardSetting" /t REG_DWORD /d "2" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem ...................................... Downloads .......................................
rem Set download directory
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DownloadDirectory" /t REG_SZ /d "%USERPROFILE%\Desktop" /f
rem 1 - Ask me what to do with each download (Ignored when download directory is set)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "PromptForDownloadLocation" /t REG_DWORD /d "1" /f
rem 1 - Open Office files in the browser
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "QuickViewOfficeFilesEnabled" /t REG_DWORD /d "0" /f
rem 1 - Enable insecure download warnings
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ShowDownloadsInsecureWarningsEnabled" /t REG_DWORD /d "0" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem ..................................... Extensions .......................................
rem 1 - Allow extensions from other stores
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ControlDefaultStateOfAllowExtensionFromOtherStoresSettingEnabled" /t REG_DWORD /d "0" /f
rem 1 - DeveloperToolsAllowed / 2 - DeveloperToolsDisallowed (Don't allow using the developer tools)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DeveloperToolsAvailability" /t REG_DWORD /d "2" /f
rem ________________________________________________________________________________________
rem 1 - Blocks external extensions from being installed
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "BlockExternalExtensions" /t REG_DWORD /d "1" /f
rem 1 - EnabledForBrowser (Prevent the browser process from creating dynamic code) / 0 - Default
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ExtensionDeveloperModeSettings" /t REG_DWORD /d "1" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem ...................................... Languages .......................................
rem 1 - Enable spellcheck
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SpellcheckEnabled" /t REG_DWORD /d "1" /f
rem 1 - Use text prediction
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "TextPredictionEnabled" /t REG_DWORD /d "0" /f
rem 1 - Offer to translate pages that aren't in a language I read
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "TranslateEnabled" /t REG_DWORD /d "0" /f
rem ________________________________________________________________________________________
rem 1 - The Microsoft Editor service provides enhanced spell and grammar checking for editable text fields on web pages
rem Google, Microsoft can get your passwords via web browser's spellcheck
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "MicrosoftEditorProofingEnabled" /t REG_DWORD /d "0" /f
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "MicrosoftEditorSynonymsEnabled" /t REG_DWORD /d "0" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem ..................................... New tab page .....................................
rem Page Layout / 1 - DisableImageOfTheDay / 2 - DisableCustomImage / 3 - DisableAll
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NewTabPageAllowedBackgroundTypes" /t REG_DWORD /d "1" /f
rem 1 - Allow Microsoft News content on the new tab page
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NewTabPageContentEnabled" /t REG_DWORD /d "0" /f
rem 1 - Preload the new tab page for a faster experience
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NewTabPagePrerenderEnabled" /t REG_DWORD /d "0" /f
rem ________________________________________________________________________________________
rem 1 - Hide the default top sites from the new tab page
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NewTabPageHideDefaultTopSites" /t REG_DWORD /d "1" /f
rem 1 - Allow quick links on the new tab page
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NewTabPageQuickLinksEnabled" /t REG_DWORD /d "0" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem ....................................... Personal .......................................
rem 1 - Add profile
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "BrowserAddProfileEnabled" /t REG_DWORD /d "0" /f
rem 1 - Browse as guest
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "BrowserGuestModeEnabled" /t REG_DWORD /d "0" /f
rem 1 - Allow users to configure Family safety and Kids Mode
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "FamilySafetySettingsEnabled" /t REG_DWORD /d "0" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem ............................ Privacy, search, and services .............................
rem 1 - Suggest similar sites when a website can't be found
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "AlternateErrorPagesEnabled" /t REG_DWORD /d "0" /f
rem 1 - Clear browsing data when Microsoft Edge closes
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ClearBrowsingDataOnExit" /t REG_DWORD /d "1" /f
rem 1 - Clear cached images and files when Microsoft Edge closes
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ClearCachedImagesAndFilesOnExit" /t REG_DWORD /d "1" /f
rem 1 - AllowCookies / 2 - BlockCookies / 4 - SessionOnly except ones listed in SaveCookiesOnExit
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DefaultCookiesSetting" /t REG_DWORD /d "4" /f
rem edge://settings/privacy/cookies/AllCookies
rem reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "0" /t REG_SZ /d "[*.]ntp.msn.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "1" /t REG_SZ /d "[*.]account.samsung.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "2" /t REG_SZ /d "[*.]alza.sk" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "3" /t REG_SZ /d "[*.]netflix.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "4" /t REG_SZ /d "[*.]deviantart.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "5" /t REG_SZ /d "[*.]discord.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "6" /t REG_SZ /d "[*.]duckduckgo.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "7" /t REG_SZ /d "[*.]elevenforum.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "8" /t REG_SZ /d "[*.]tesco.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "9" /t REG_SZ /d "[*.]fio.sk" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "10" /t REG_SZ /d "[*.]forums.mydigitallife.net" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "11" /t REG_SZ /d "[*.]github.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "12" /t REG_SZ /d "[*.]heureka.sk" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "13" /t REG_SZ /d "[*.]hoyolab.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "14" /t REG_SZ /d "[*.]hoyoverse.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "15" /t REG_SZ /d "[*.]imdb.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "16" /t REG_SZ /d "[*.]isthereanydeal.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "17" /t REG_SZ /d "[*.]itesco.sk" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "18" /t REG_SZ /d "[*.]malwaretips.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "19" /t REG_SZ /d "[*.]www.elevenforum.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "20" /t REG_SZ /d "[*.]myanimelist.net" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "21" /t REG_SZ /d "[*.]nextdns.io" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "22" /t REG_SZ /d "[*.]mbank.sk" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "23" /t REG_SZ /d "[*.]modland.net" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "24" /t REG_SZ /d "[*.]nordaccount.com /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "25" /t REG_SZ /d "[*.]primevtc.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "26" /t REG_SZ /d "[*.]roextended.ro" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "27" /t REG_SZ /d "[*.]softpedia.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "28" /t REG_SZ /d "[*.]steamcommunity.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "29" /t REG_SZ /d "[*.]steampowered.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "30" /t REG_SZ /d "[*.]nordvpn.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "31" /t REG_SZ /d "[*.]truckersmp.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "32" /t REG_SZ /d "[*.]twitch.tv" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "33" /t REG_SZ /d "[*.]vk.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "34" /t REG_SZ /d "[*.]wilderssecurity.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "35" /t REG_SZ /d "[*.]goodreads.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "36" /t REG_SZ /d "[*.]ce-tescoassets.com" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "37" /t REG_SZ /d "[*.]allegro.sk" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SaveCookiesOnExit" /v "37" /t REG_SZ /d "[*.]wolt.com" /f
rem Diagnostic Data / 0 - Off / 1 - RequiredData / 2 - OptionalData
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DiagnosticData" /t REG_DWORD /d "0" /f
rem Enhance the security state in Microsoft Edge / 0 - Standard mode / 1 - Balanced mode / 2 - Strict mode
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EnhanceSecurityMode" /t REG_DWORD /d "2" /f
rem Automatically switch to more secure connections with Automatic HTTPS / allowed / disallowed / force_enabled / force_balanced_enabled
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "HttpsOnlyMode" /t REG_SZ /d "force_enabled" /f
rem Search on new tabs uses search box or address bar / redirect - address bar / bing - search box
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NewTabPageSearchBox" /t REG_SZ /d "redirect" /f
rem 1 - Use a web service to help resolve navigation errors
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ResolveNavigationErrorsUseWebService" /t REG_DWORD /d "0" /f
rem 1 - Scareware blocker
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ScarewareBlockerProtectionEnabled" /t REG_DWORD /d "0" /f
rem 1 - Show me search and site suggestions using my typed characters - broken since 142
rem reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SearchSuggestEnabled" /t REG_DWORD /d "0" /f
rem 1 - Suggest group names when creating a new tab group
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "TabServicesEnabled" /t REG_DWORD /d "0" /f
rem Tracking prevention / 0 - Off / 1 - Basic / 2 - Balanced / 3 - Strict
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "TrackingPrevention" /t REG_DWORD /d "0" /f
rem 1 - Typosquatting Checker (just sending what you type to MS)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "TyposquattingCheckerEnabled" /t REG_DWORD /d "0" /f
rem 1 - Visual search (sending what you are looking at to MS)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "VisualSearchEnabled" /t REG_DWORD /d "0" /f
rem ________________________________________________________________________________________
rem 1 - Allow users to bypass Enhanced Security Mode
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EnhanceSecurityModeAllowUserBypass" /t REG_DWORD /d "0" /f
rem Force the default Search engine and Prevent adding custom search engines
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ManagedSearchEngines" /t REG_SZ /d "[{\"allow_search_engine_discovery\":false},{\"is_default\":true,\"name\":\"DuckDuckGo\",\"keyword\":\"duckduckgo.com\",\"search_url\":\"DuckDuckGo - Protection. Privacy. Peace of mind.{searchTerms}\",\"suggest_url\":\"DuckDuckGo - Protection. Privacy. Peace of mind.{searchTerms}\",\"image_search_url\":\"https://www.duckduckgo.com/images/detail/search?iss=sbiupload\"}]" /f
rem reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ManagedSearchEngines" /t REG_SZ /d "[{\"allow_search_engine_discovery\":false},{\"is_default\":true,\"name\":\"Brave\",\"keyword\":\"search.brave.com\",\"search_url\":\"Brave Search{searchTerms}\",\"suggest_url\":\"https://api.search.brave.com/res/v1/suggest/{searchTerms}\",\"image_search_url\":\"https://api.search.brave.com/res/v1/images/search\"}]" /f
rem Allow personalization of ads, Microsoft Edge, search, news and other Microsoft services by sending browsing history, favorites and collections, usage and other browsing data to Microsoft
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "PersonalizationReportingEnabled" /t REG_DWORD /d "0" /f
rem Enable Microsoft Bing trending suggestions in the address bar
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "AddressBarTrendingSuggestEnabled" /t REG_DWORD /d "0" /f
rem Allow recommendations and promotional notifications from Microsoft Edge
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ShowRecommendationsEnabled" /t REG_DWORD /d "0" /f
rem Choose whether users can receive customized background images and text, suggestions, notifications, and tips for Microsoft services)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SpotlightExperiencesAndRecommendationsEnabled" /t REG_DWORD /d "0" /f
rem Use secure DNS (DoH)
rem reg add "HKLM\Software\Policies\Microsoft\Edge" /v "BuiltInDnsClientEnabled" /t REG_DWORD /d "1" /f
rem reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DnsOverHttpsMode" /t REG_SZ /d "secure" /f
rem reg add "HKLM\Software\Policies\Microsoft\Edge" /v "DnsOverHttpsTemplates" /t REG_SZ /d "https://freedns.controld.com/p2?" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem ...................................... Profiles ........................................
rem 1 - Save and fill personal info
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "AutofillAddressEnabled" /t REG_DWORD /d "0" /f
rem 1 - Save and fill payment info
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "AutofillCreditCardEnabled" /t REG_DWORD /d "0" /f
rem Browser sign-in settings / 0 - Disable / 1 - Enable / 2 - Force users to sign-in to use the browser (all profiles)
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "BrowserSignin" /t REG_DWORD /d "1" /f
rem 1 - Let users compare the prices of a product they are looking at, get coupons or rebates from the website they're on
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EdgeShoppingAssistantEnabled" /t REG_DWORD /d "0" /f
rem 1 - Forces data synchronization in Microsoft Edge. This policy also prevents the user from turning sync off.
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ForceSync" /t REG_DWORD /d "1" /f
rem If you enable this policy all the specified data types will be included for synchronization
reg add "HKLM\Software\Policies\Microsoft\Edge\ForceSyncTypes" /v "1" /t REG_SZ /d "extensions" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\ForceSyncTypes" /v "2" /t REG_SZ /d "favorites" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\ForceSyncTypes" /v "3" /t REG_SZ /d "settings" /f
rem If you enable this policy all the specified data types will be excluded from synchronization
reg add "HKLM\Software\Policies\Microsoft\Edge\SyncTypesListDisabled" /v "1" /t REG_SZ /d "addressesAndMore" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SyncTypesListDisabled" /v "2" /t REG_SZ /d "apps" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SyncTypesListDisabled" /v "3" /t REG_SZ /d "collections" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SyncTypesListDisabled" /v "4" /t REG_SZ /d "edgeWallet" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SyncTypesListDisabled" /v "5" /t REG_SZ /d "edgeFeatureUsage" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SyncTypesListDisabled" /v "6" /t REG_SZ /d "history" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SyncTypesListDisabled" /v "7" /t REG_SZ /d "openTabs" /f
reg add "HKLM\Software\Policies\Microsoft\Edge\SyncTypesListDisabled" /v "8" /t REG_SZ /d "passwords" /f
rem 1 - Disable Share Microsoft Edge Browsing Data with other Windows Features
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "LocalBrowserDataShareEnabled" /t REG_DWORD /d "0" /f
rem 1 - Suggest strong passwords
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "PasswordGeneratorEnabled" /t REG_DWORD /d "0" /f
rem 1 - Offer to save passwords
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "PasswordManagerEnabled" /t REG_DWORD /d "0" /f
rem 1 - Show alerts when passwords are found in an online leak
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "PasswordMonitorAllowed" /t REG_DWORD /d "0" /f
rem 1 - Show the "Reveal password" button in password fields
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "PasswordRevealEnabled" /t REG_DWORD /d "0" /f
rem Sign in: / 0 - Automatically / 1 - With device password
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "PrimaryPasswordSetting" /t REG_DWORD /d "0" /f
rem 1 - Show Microsoft Rewards experience and notifications
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "ShowMicrosoftRewards" /t REG_DWORD /d "0" /f
rem ________________________________________________________________________________________
rem 1 - Single sign-on for work or school sites using this profile enabled
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "AADWebSiteSSOUsingThisProfileEnabled" /t REG_DWORD /d "0" /f
rem 1 - Allow single sign-on for Microsoft personal sites using this profile
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "MSAWebSiteSSOUsingThisProfileAllowed" /t REG_DWORD /d "0" /f
rem Configure the list of domains where Microsoft Edge should disable the password manager
rem reg add "HKLM\Software\Policies\Microsoft\Edge\PasswordManagerBlocklist" /v "1" /t REG_SZ /d "Steam Community" /f
rem reg add "HKLM\Software\Policies\Microsoft\Edge\PasswordManagerBlocklist" /v "2" /t REG_SZ /d "Steam Store" /f
rem =================================== Windows Policies ===================================
rem ------------------------------------ Microsoft Edge ------------------------------------
rem ................................ System and performance ................................
rem 1 - Continue running background apps when Microsoft Edge is closed
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "BackgroundModeEnabled" /t REG_DWORD /d "0" /f
rem Efficiency Mode / 1 - Enables efficiency mode
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EfficiencyModeEnabled" /t REG_DWORD /d "0" /f
rem 1 - Use hardware acceleration when available
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "HardwareAccelerationModeEnabled" /t REG_DWORD /d "0" /f
rem 1 - Enable RAM (memory) resource controls
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "RAMResourceControlsEnabled" /t REG_DWORD /d "0" /f
rem 1 - Save resources with sleeping tabs
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "SleepingTabsEnabled" /t REG_DWORD /d "0" /f
rem 1 - Startup boost
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "StartupBoostEnabled" /t REG_DWORD /d "0" /f
rem ________________________________________________________________________________________
rem 1 - If ECH is enabled, Microsoft Edge might or might not use ECH depending on server support, the availability of the HTTPS DNS record
rem Enable: DOH + the paramater: --enable-features="EncryptedClientHello" - Cloudflare Browser Check
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "EncryptedClientHelloEnabled" /t REG_DWORD /d "1" /f
rem NetworkPrediction / 0 - Always / 1 - WifiOnly / 2 - Never
reg add "HKLM\Software\Policies\Microsoft\Edge" /v "NetworkPredictionOptions" /t REG_DWORD /d "2" /f"C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --enable-features="EnableCsrssLockdown,EncryptedClientHello,IsolatePrerenders,IsolateSandboxedIframes,RendererAppContainer,WinSboxDisableExtensionPoint" --disable-webgl --no-pings


- Secure DNS
- Desktop VPN
- Password manager
- Maintenance tools
- File and Photo backup
- Subscriptions
- Microsoft OneDrive 100GB
- System recovery
- Risk factors
- Browsing to popular websites
- Buying from online stores, entering banks card details
- Logging into my bank account
- Downloading software and files from reputable sites
- Gaming
- Gaming with third-party mods
- Streaming audio/video content from trusted sites or paid subscriptions
- Streaming audio/video content from shady sites
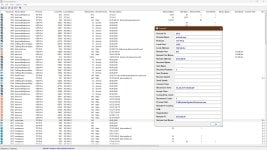
- Computer specs

Showcase - TairikuOkami's PC built in 2024
After 5/10 Years, finally a little upgrade. My previous GPU is no longer supported, so it had to be done anyway. It took ~6 months to buy. It is not perfect yet, there are several issues like EXPO profile for RAM can not be set, but that is the price for buying the latest hardware. For the... malwaretips.com
malwaretips.com
- Notable changes
- 30-01-26 Windows 11 26H2 Dev (CMD as admin fails...)
26-05-24 Windows 11 24H2 + Hasleo Backup Suite (PreOS)
28-10-23 Microsoft 365 Basic & DDG (the only usable search)
- What I'm looking for?
Looking for medium feedback.
- Notes by Staff Team
This setup configuration may put you and your device at risk!
We do not recommend that other members use this setup. We cannot be held responsible for problems that may occur to your device by using this security setup.
Is it necessary to apply such rules if using a 3rd party firewall aksing for permission before any connection?I have decided to remove WFC, it was giving me too much headache. Windows Firewall with outbound allowed still honors block rules, so I am just going to block bad ports by default like:
Code:netsh advfirewall firewall delete rule name=all netsh advfirewall firewall add rule name="TCP Block" dir=out action=block protocol=TCP remoteport=1-79,81-442,444-852,854-1024 netsh advfirewall firewall add rule name="UDP Block" dir=out action=block protocol=UDP remoteport=1-442,444-1024 netsh advfirewall firewall add rule name="Brave TCP" dir=out action=block protocol=TCP remoteport=1-442,444-65535 program="C:\Users\Tairi\AppData\Local\BraveSoftware\Brave-Browser\Application\brave.exe" netsh advfirewall firewall add rule name="Edge TCP" dir=out action=block protocol=TCP remoteport=1-442,444-65535 program="C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" netsh advfirewall firewall add rule name="Edge UDP" dir=out action=block protocol=UDP remoteport=443 program="C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" netsh advfirewall firewall add rule name="LibreWolf TCP" dir=out action=block protocol=TCP remoteport=1-442,444-65535 program="C:\Program Files\LibreWolf\librewolf.exe" netsh advfirewall firewall add rule name="LibreWolf UDP" dir=out action=block protocol=UDP remoteport=443 program="C:\Program Files\LibreWolf\librewolf.exe" netsh advfirewall firewall add rule name="OneDrive TCP" dir=out action=block protocol=TCP remoteport=1-442,444-65535 program="C:\Program Files\Microsoft OneDrive\OneDrive.exe" netsh advfirewall firewall add rule name="IceDrive TCP" dir=out action=block protocol=TCP remoteport=1-442,444-65535 program="C:\Users\Tairi\AppData\Local\Temp\IcedrivePortable\Icedrive.exe"
I have restricted some exes (lolbins) like mshta.exe via Disallow policy. Port 80 aka http is not allowed. To partially prevent malware using legitimate processes, I have allowed only trusted IP ranges for the most vulnerable apps like svchost or discord. Process Hacker checks running processes in VirusTotal.
Hi,
It is always interesting to discuss the No-AV setup.
Many attacks will be blocked, but some popular attack vectors are still possible. Therefore, the user must be cautious and have extensive knowledge and experience in using Process Hacker (System Informer).
In your case, the problem may be related to game mods or game updates. For example, when the gaming server is compromised, the malicious content will be installed. In such cases, the protection provided by NextDNS is often slowed.
Unfortunately, the installed malware often uses trusted IP ranges and HTTPS.
ProcessHacker with VT integration is a good protection layer, but may be insufficient nowadays. Many malware use DLLs (no integration with VT) for persistence.
It would be interesting to use SAC or a specially adjusted WDAC policy to periodically audit non-system DLLs and drivers. The audit starts when enabling SAC in Evaluate mode or copying the WDAC policy to the appropriate folder.
Last edited:
No need to worry, friend. What a coincidence, I also tested a WannaCry sample back in 2017. I had BDTS with folder protection similar to what MD has today. WannaCry also did not encrypt protected folders because I was using the SUA account and still had the C:\Users\Public folders protected. The process remained running but was unable to elevate system or administrator privileges on the SUA account to encrypt my files. Then I ran the test without folder protection, and it only encrypted the files of the standard account users. The admin account files remained untouched. Since I was using RBX at the time, I just reverted to a previous snapshot and I was back, just for peace of mind, but Wannacry did not spread to other machines. Coincidence or not, you think similarly to me, you like to configure and harden the operating system without relying too much on AVs. In your settings, theoretically, ransomware and malware would not be able to do much, I presume, precisely because of the configuration restrictions you imposed on your OS. For example, the malware would not be able to communicate with C2 due to your DNS and the blocking of ports commonly used and abused by malware. Here we will also consider LOLBins. If your system is applied, blocked by the firewall, the malware would also not be able to download the payload, so the malware would remain inactive. Very interesting configuration @TairikuOkami.Thanks, it would be actually interesting to see, how would this AV-less setup hold against real a malware/ransomware, but that would require someone more skilled than me. I once tested wannacry real life and it failed to do anything, since ransomware requires SYSTEM permissions and I pretty much denied that on important partitions and folders.
Of course not, these rules only apply to the Windows firewall. But you can still apply them if you uninstall the third-party firewall or disable it for testing purposes.Is it necessary to apply such rules if using a 3rd party firewall aksing for permission before any connection?
Same as @TairikuOkami's post number #33. I won't post here anymore, otherwise it will clutter up @TairikuOkami's thread, which is about his computer settings. Let's respect him.What ports should be allowed?
Yes, I have noticed the settings after asking you; apologies.Same as @TairikuOkami's post number #33. I won't post here anymore, otherwise it will clutter up @TairikuOkami's thread, which is about his computer settings. Let's respect him.
Easier to control and monitor, chromium browsers leak via default DNS, unless it is blocked.What was your reason for switching to DoT on Windows 11 over the default DoH?
People mention that it has less vulnerabilities compared to widespread HTTP. Good article:

DNS-over-TLS (DoT) vs DNS-over-HTTPS (DoH): What’s the Difference?
Learn which encrypted DNS protocol is best for security, compliance, and network control in 2025.
 controld.com
controld.com
Attachments
Last edited:
@TairikuOkami Thanks again for sharing your configuration.  When I used CF/CIS, I blocked all TCP ports 1-65535 on the firewall. I never did that on the Windows firewall. But it's interesting, it gives you peace of mind when you know that no ports are open or exposed to the web.
When I used CF/CIS, I blocked all TCP ports 1-65535 on the firewall. I never did that on the Windows firewall. But it's interesting, it gives you peace of mind when you know that no ports are open or exposed to the web. 
DOT can have a clear advantage only in Enterprises or for users who can efficiently monitor the network traffic. In the case of malicious traffic, it can be blocked without blocking other connections. Also, the users cannot easily bypass the restrictions put by the Enterprise Administrators.
However, for most home users, properly configured DOH is considered a better solution.
However, for most home users, properly configured DOH is considered a better solution.
I see. It makes it easy for you to monitor it. You're still using DoH in your browser so there's that.Easier to control and monitor, chromium browsers leak via default DNS, unless it is blocked.
People mention that it has less vulnerabilities compared to widespread HTTP. Good article:

DNS-over-TLS (DoT) vs DNS-over-HTTPS (DoH): What’s the Difference?
Learn which encrypted DNS protocol is best for security, compliance, and network control in 2025.controld.com
If you want to use DoT even in your browser then you could install YogaDNS or AdGuard Home. AdGuard Home can prevent leaking default DNS in Chromium by using something like, https://1.1.1.1/dns-query as the bootstrap address.
I like DoH/3 & DoQ (both slightly faster than DoH and DoQ) but browsers and operating systems don't natively support them so third-party software is needed.
I've been tweaking & tweaking DNS / DoH for a few days on various VMs with some "help" from chatGPT, I've learned a little. I'm no longer in the mode (or mood) to analyze w/wireshark...for most home users, properly configured DOH is considered a better solution.
Based on these images, I can picture the moment of betrayal... You forced your pet bear into the bathtub against his will; no amount of lavender oil can mask the look in your pet bear's eyes... "Great-smelling lavender oil" cannot erase the memory of the struggle—I see a pet bear who's plotting revenge!I have just cleaned my pet bear, totally unrelated to the security, then again, it makes me feel safe, considering my life problems. I have used the Lavender oil, it smells great, but looks dashy.
View attachment 290260 mView attachment 290262
I was "forced" to switch back to Stable. Canary failed to update due to insufficient space. My partition was 64GB, no surprise there 25H2 took 65GB after a clean install.
Unfortunately due to stupid MS, I had to remove all partitions, since 11 considered the faster disk as secondary and refused to install it, just like during HDD's jumper days.
Luckily my BIOS allows me to clear SSDs, I had to remove everything to be able to clean install 11, it worked, sadly on a slower SSD, but 25H2 runs pretty light, after tweaking.
Unfortunately due to stupid MS, I had to remove all partitions, since 11 considered the faster disk as secondary and refused to install it, just like during HDD's jumper days.
Luckily my BIOS allows me to clear SSDs, I had to remove everything to be able to clean install 11, it worked, sadly on a slower SSD, but 25H2 runs pretty light, after tweaking.

I think you mean "after seriously hacking".25H2 runs pretty light, after tweaking.
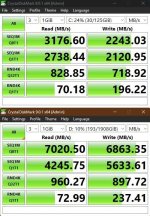
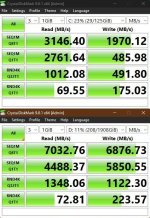
I have reverted back to 26H1, I got bored and I wanted NVMe 70% performance gain, but it did not turn out the way I expected.
Slow disk has got noticeably slower and fast disk has got slightly faster. I have to use slow disk for Windows, not happy about it.
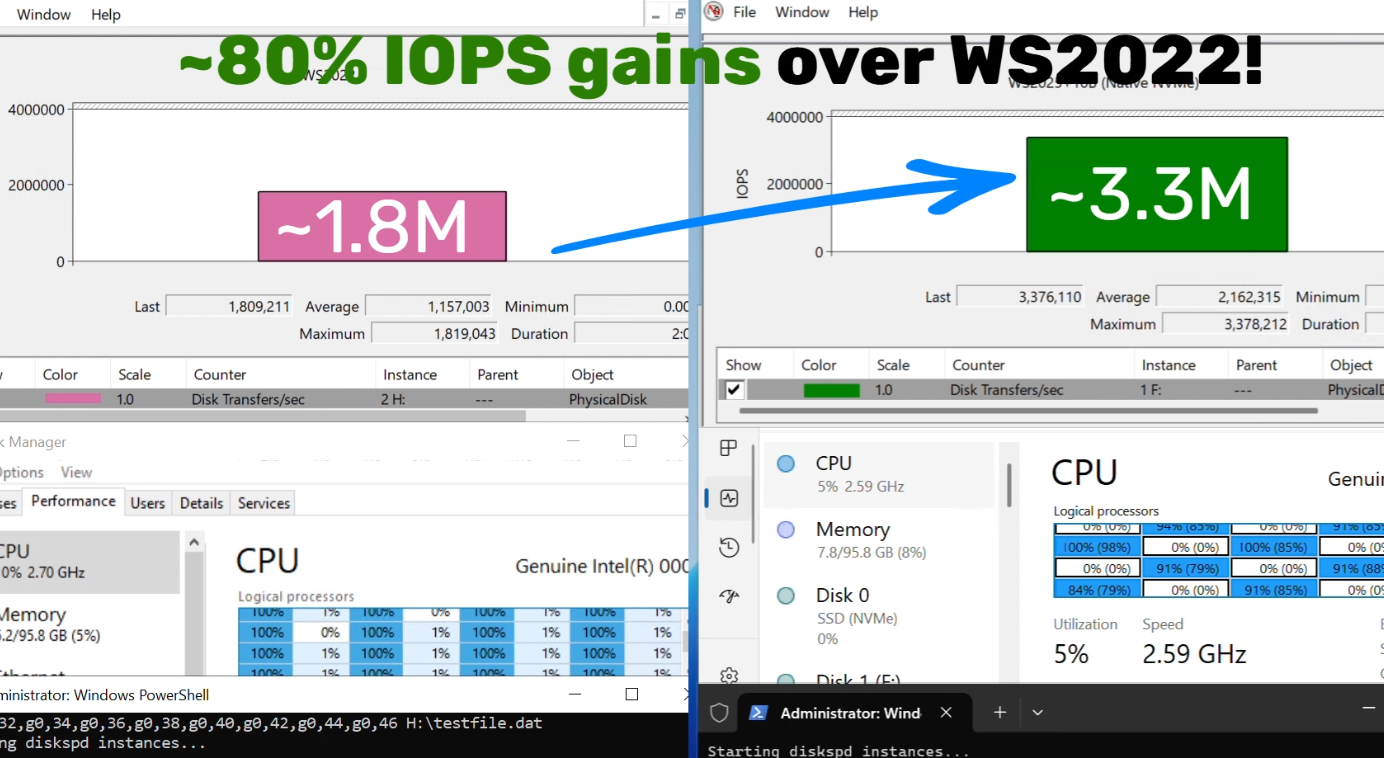
 techcommunity.microsoft.com
techcommunity.microsoft.com
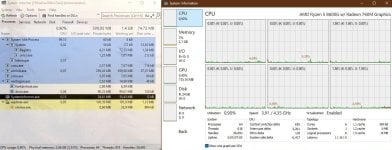
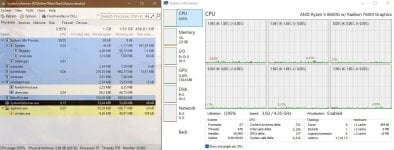
Windows 11 Home (28020.1362) - it settles down after 7min - 62 processes (+SystemInformer/+XnView) / 618 threads / 26962 handles / 2.1GB RAM
Slow disk has got noticeably slower and fast disk has got slightly faster. I have to use slow disk for Windows, not happy about it.
Code:
reg add "HKLM\System\CurrentControlSet\Policies\Microsoft\FeatureManagement\Overrides" /v "156965516" /t REG_DWORD /d "1" /f
reg add "HKLM\System\CurrentControlSet\Policies\Microsoft\FeatureManagement\Overrides" /v "735209102" /t REG_DWORD /d "1" /f
reg add "HKLM\System\CurrentControlSet\Policies\Microsoft\FeatureManagement\Overrides" /v "1853569164" /t REG_DWORD /d "1" /f



Announcing Native NVMe in Windows Server 2025: Ushering in a New Era of Storage Performance | Microsoft Community Hub
We’re thrilled to announce the arrival of Native NVMe support in Windows Server 2025—a leap forward in storage innovation that will redefine what’s possible...

Windows 11 Home (28020.1362) - it settles down after 7min - 62 processes (+SystemInformer/+XnView) / 618 threads / 26962 handles / 2.1GB RAM
Last edited:
I got Revolut Premium, so I could buy commodities like silver with smaller fees and as a bonus I got NordVPN Standard and unlike other VPNs, it just works with my config, no background processes either when OFF. I can watch US/UK Netflix content, like Mr Bean, but the best part is, that it works with NextDNS flawlessly. Best from both worlds. 



You may also like...
-
-
-
Expired SwifDoo Christmas 2025: PDF 18 Software Programs for free
- Started by Brownie2019
- Replies: 1
-
App Review Testing Orion Malware Cleaner Designed by Me
- Started by Trident
- Replies: 8
-