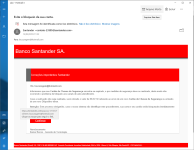
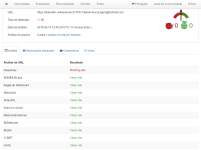
- Dec 23, 2014
- 8,908
Update February 13 2019 20:00 EST:...
One important thing to consider is that this is neither an injection nor a privilege escalation.
Installed Avast binaries have self-protection mechanisms in place to avoid injections. In this instance, they are using an Avast file to run a binary in a similar way that a DLL using Windows’ rundll32.exe can run. ...
[/QUOTE]
The above Avast explanation is not exactly true. It is true for the first DLL payload (lrdsnhrxxxfery64), but the next payload (lrdsnhrxxxfery98) is injected to aswrundll.exe . The truth is that aswrundll.exe is a simple tool to run DLLs, it is not installed and protected by Avast. It has not got any self-protection mechanism, too.
The truth is also, that Avast introduced the new vector of attack, similar to rundll32.exe.
Edit.
To be honest, that does not matter at all, for the average Avast customer. Such a vector of attack is only harder to uncover by more advanced user.
One important thing to consider is that this is neither an injection nor a privilege escalation.
Installed Avast binaries have self-protection mechanisms in place to avoid injections. In this instance, they are using an Avast file to run a binary in a similar way that a DLL using Windows’ rundll32.exe can run. ...
[/QUOTE]
The above Avast explanation is not exactly true. It is true for the first DLL payload (lrdsnhrxxxfery64), but the next payload (lrdsnhrxxxfery98) is injected to aswrundll.exe . The truth is that aswrundll.exe is a simple tool to run DLLs, it is not installed and protected by Avast. It has not got any self-protection mechanism, too.
The truth is also, that Avast introduced the new vector of attack, similar to rundll32.exe.
Edit.
To be honest, that does not matter at all, for the average Avast customer. Such a vector of attack is only harder to uncover by more advanced user.
Last edited: