Hi all,
today I made a simple malware reverse analysis of this sample of Trojan.
Sample type: Trojan.Win32.Generic.pak!cobra
MD5: 50567a1ed4779ffc2596c341fe38fd4e
SHA1: 4292df38e122dd6beb02230210575e80a6ed71ed
SHA256: 0cd8d196f66e2bec6636976fbceae5298cc2acf8e7c8c700f717034eadb854f2
Library used by the sample:
mscoree.dll:
0x402000 _CorExeMain
While reversing the malware I found these strings particuarly interesting, because some of them are obfuscated:
One interesting thing is that this application, that appereantly would change the icon of .exe files, it runs malicious code to infect the machine only by using a library, but most of the code is "[DebuggerHidden]" (see for example the fourth screenshot); and this is an important thing to remember.
The sample must be run under Win32.
These are the screenshots of my malware reverse analysis (The most important source code).
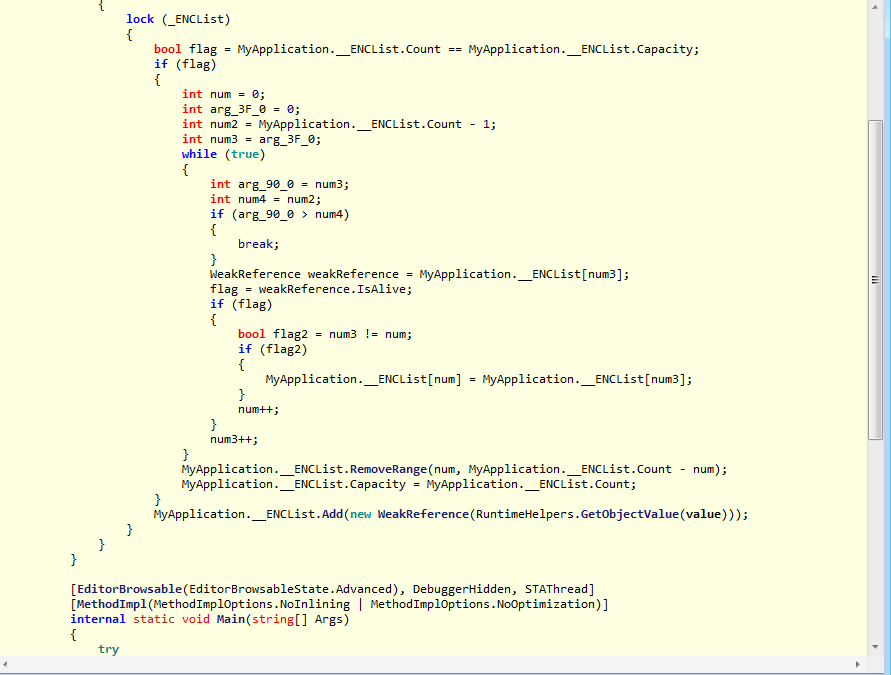
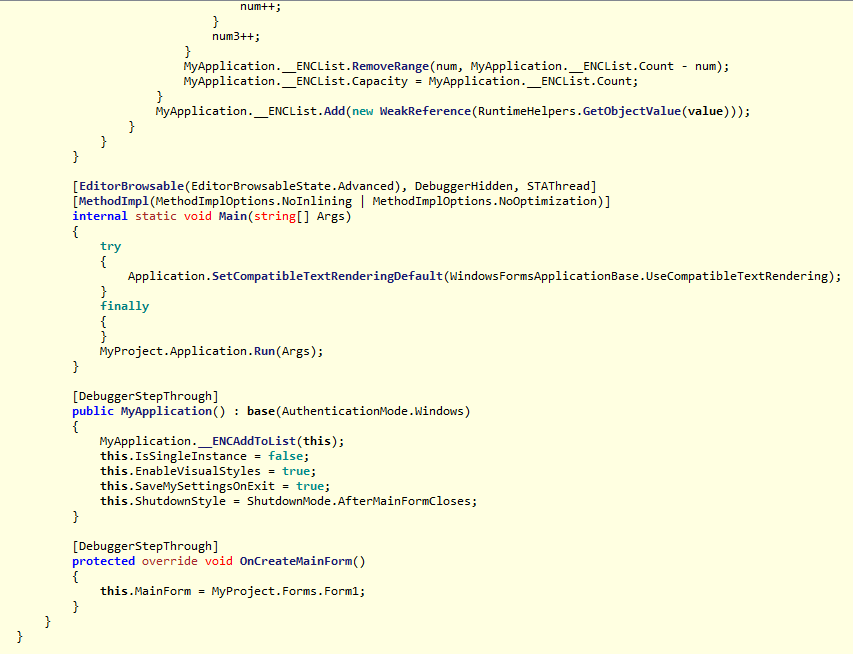
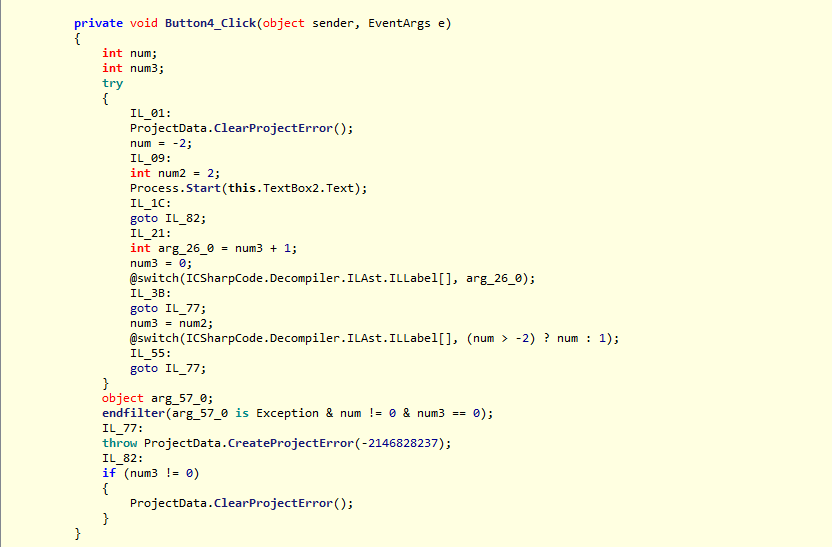
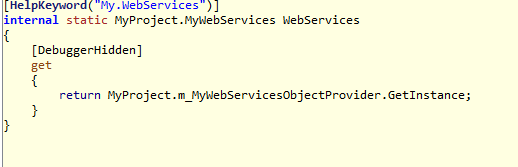
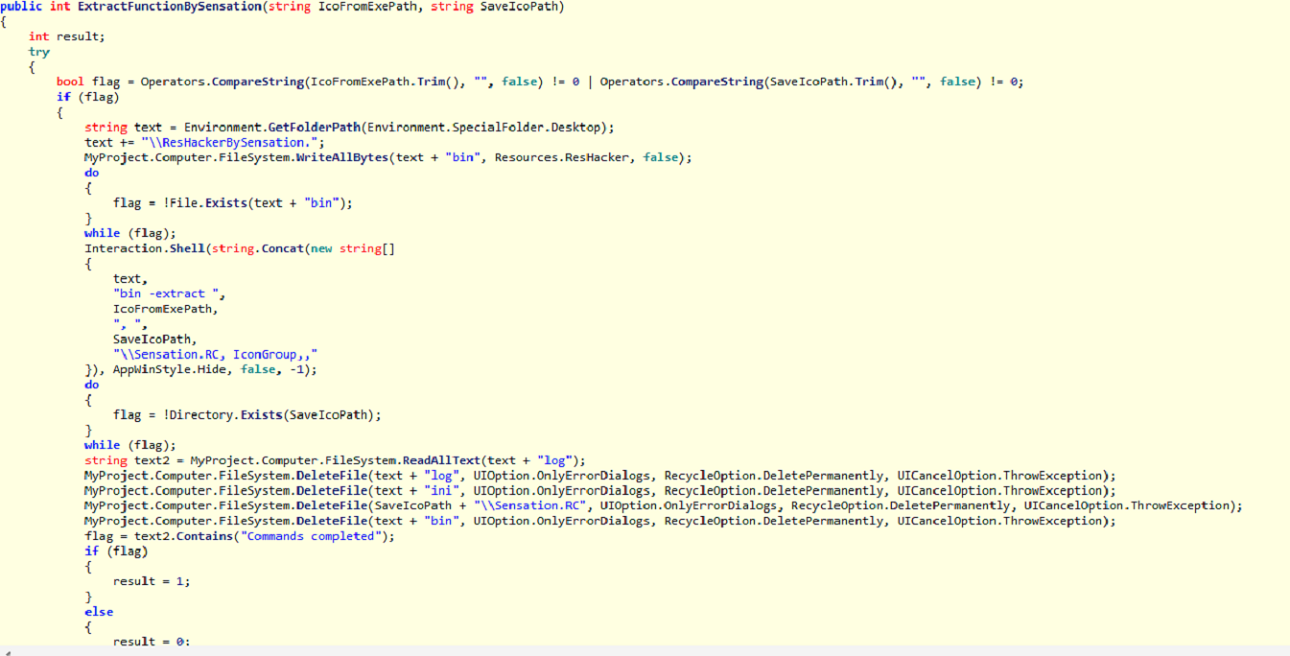
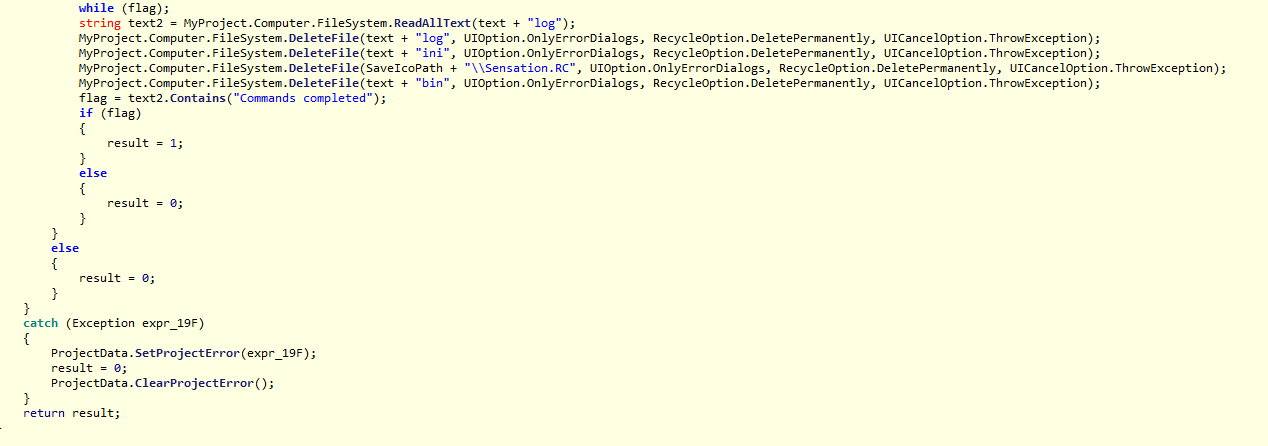
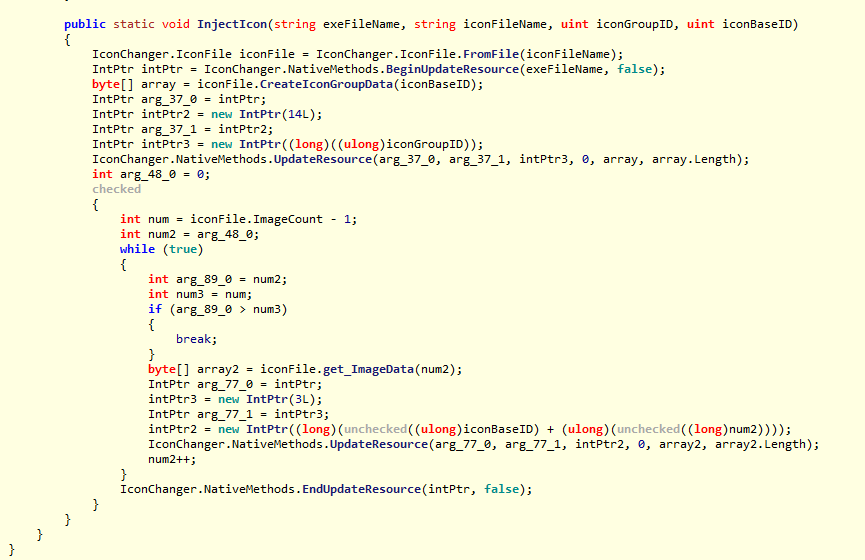
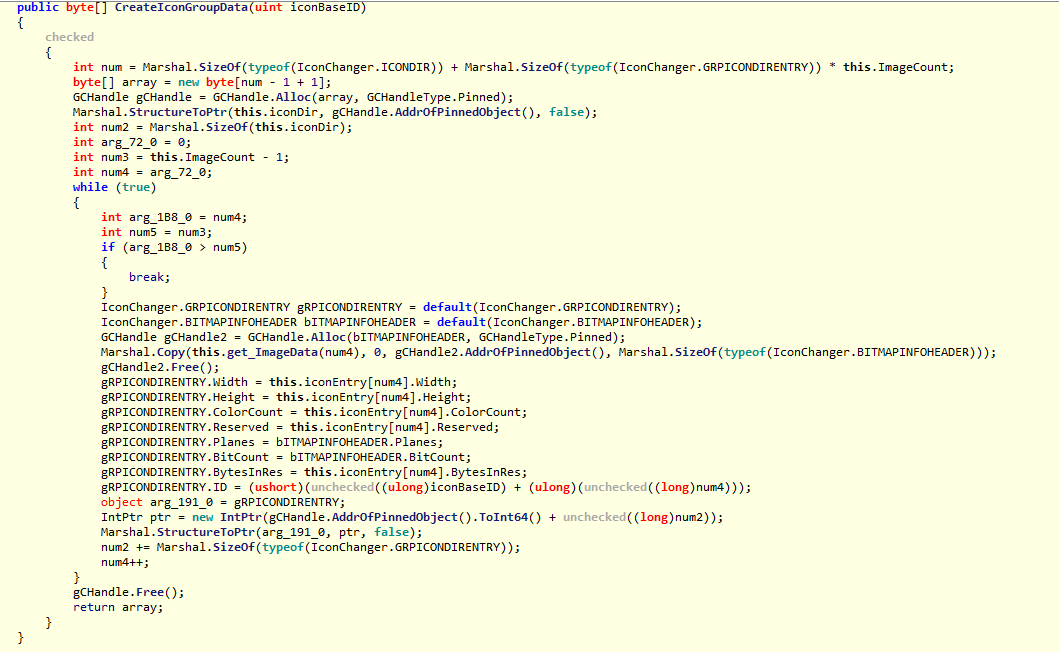
File Sections:
For this malware analysis I used a Windows 7 VM inside VirtualBox (latest version).
This is the VirusTotal Report:
Detection Ratio: 4/53
Software used: ILSpy
Thank you all for reading
today I made a simple malware reverse analysis of this sample of Trojan.
Sample type: Trojan.Win32.Generic.pak!cobra
MD5: 50567a1ed4779ffc2596c341fe38fd4e
SHA1: 4292df38e122dd6beb02230210575e80a6ed71ed
SHA256: 0cd8d196f66e2bec6636976fbceae5298cc2acf8e7c8c700f717034eadb854f2
Library used by the sample:
mscoree.dll:
0x402000 _CorExeMain
While reversing the malware I found these strings particuarly interesting, because some of them are obfuscated:
Code:
IconData
height
Vnao^T
0/U'KE
$sIb+
?!RIGM
*++su]G
glll,:
={vA]]]a~~
,XPRUU
mhh83m
t:FGGC
|eFaaaB
ow644t
UPP #Q
@tvZEEENd
=?Tiohh(
$.Hkhh8
|r+`!^
]w]iaaa
{lauuu
<yrNUU
iZIIINIII
vk%%%nPKF
w+,,ty
a52iH\l, mscorlib, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089#System.Resources.RuntimeResourceSet
hSystem.Drawing.Bitmap, System.Drawing, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3aPADPADwOne interesting thing is that this application, that appereantly would change the icon of .exe files, it runs malicious code to infect the machine only by using a library, but most of the code is "[DebuggerHidden]" (see for example the fourth screenshot); and this is an important thing to remember.
The sample must be run under Win32.
These are the screenshots of my malware reverse analysis (The most important source code).
File Sections:
Code:
Name - Virtual address - Virtual size - Raw size - Entropy - MD5
.text 8192 1247300 1247744 6.16 c301800889b42018ac6305f6232a23f4
.sdata 1261568 142 512 2.06 bcfb9ab6f13950c8e0cdcdc18ceac0cd
.rsrc 1269760 172944 173056 1.98 3a06f005d96dbf93b7645294976a1ee0
.reloc 1449984 12 512 0.10 3271c072aa0b1850cfc845bef54e4a26For this malware analysis I used a Windows 7 VM inside VirtualBox (latest version).
This is the VirusTotal Report:
Detection Ratio: 4/53
Software used: ILSpy
Thank you all for reading
Last edited: