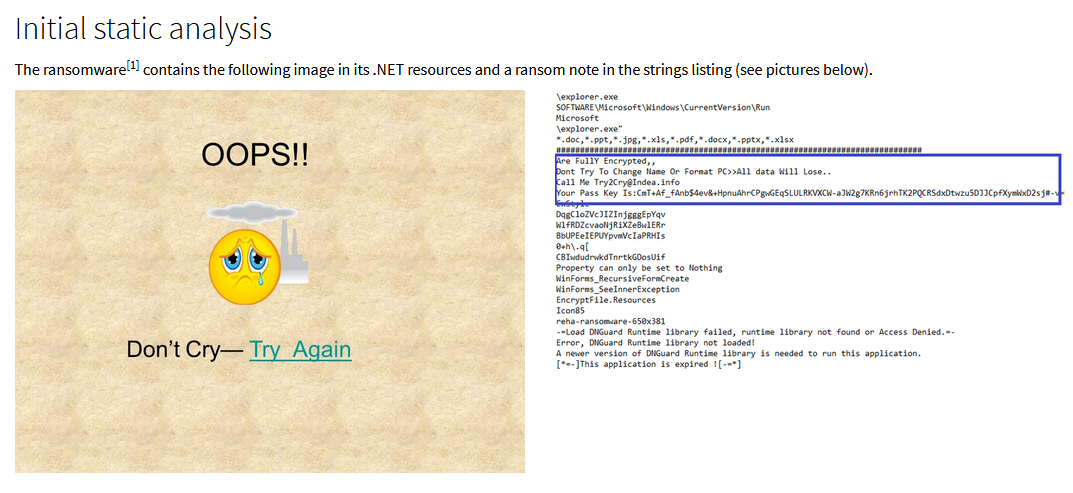
This is a small summary of a ransomware analysis I made. It's decryptable.
Try2Cry ransomware adopts USB flash drive spreading using LNK files. The last ransomware that did the same was the infamous Spora. The code of Try2Cry looks oddly familiar, though.
A big portion of my work as malware analyst at G Data is writing detection signatures for our product. One of those signatures checks for a USB worm component that I have seen in certain variants of .NET based RATs like njRAT and BlackNet RAT. When this worm signature hit on an unidentified sample[1], I got curios. It was a .NET ransomware that seemed oddly familiar to me. I couldn’t put a finger on it yet.
...