What does this tutorial explain?
Privacy extensions not always apply the right restrictions. Content blockers like Noscript, uBlockOrigin in advanced mode apply restrictions which you don't always need (or become a hassle to configure for daily use). This tutorial shows how you can increase your privacy and security ON-DEMAND in an easy way with most settings pre-defined.
Step 1 configure Extensioner to add increased security and privacy on-demand.
The advantage with on-demand usage is that you can increase protection levels, because these higher protection levels are only switched on when you think you need it (e.g. for use with VPN or for risky browsing).
Step 2 Configuring Policy Control
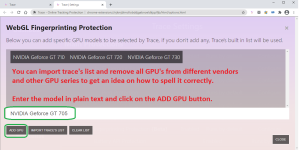
Step 3 Configuring Trace
Now you need to fine tune your anti-fingerprinting settings to make the fake values as realistic as possible
Attachments
Last edited by a moderator: