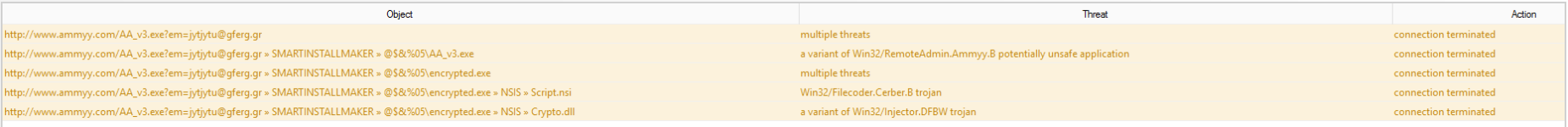
I would like to report that I was hit by a cerber3 ransomware variant embedded in the currently available ammyy setup. Ammyy is a remote control software, such as VNC or Teamviewer, and their site was visibly hacked recently because their setup was repacked as a virus deployer and it is not detected by most antiviruses. The malicious setup is not detected, but worse still, the deployed viral exe is not either.
Some antiviruses detect the setup as being a RemoteAdmin, but as Ammy is a remote admin tool, you will of course allow the execution, and the setup will deploy and run the virus. Very astute way to ensure the antivirus is bypassed.
Once you launch the setup, the file encrypted.exe is deployed into <local settings>\temp along the legit Ammyy setup and both are executed. Then the ransomware starts encrypting your data.
Now a HIPS soft may help with this, but if the hackers are not too stupid they would name the exe video_helper_driver64.exe or whatever may seem a legit Ammyy companion and then you would allow it to run.
Note that the legit setup is signed by the company and the repacked setup is not.
I submitted the malicious setup to some AV sites, explaining the false detection problem, but they use automated analysis and just report a RemoteAdmin threat, so I'm not sure they'll investigate further to discover how cerber3 can be embedded in there.
The malicious setup, sometimes detected as RemoteAdmin:
Antivirus scan for 5b13f477c35822e4ba55dfb3d0d99677e1d50dabc78035970104540255df8ec3 at 2016-09-13 12:54:09 UTC - VirusTotal
The deployed ransomware:
https://www.virustotal.com/en/file/...3efa7ec5e6f32ee9e500a7394e3daf7a916/analysis/
As a side note I tried Comodo AV and IS in a VM and only AV warned me about Ammyy being a possible RemoteAdmin threat. I find strange that they don't have the same behaviour, but perhaps it's because I tested on Windows XP and some OS features are not available. Also Avira did not find a thing although the virustotal reports show otherwise.