- Oct 25, 2014
- 2,636
- 7,291
- 3,588
- 40
Hi @jv16
I have scan your homepage with virustotal and get this from virustotal
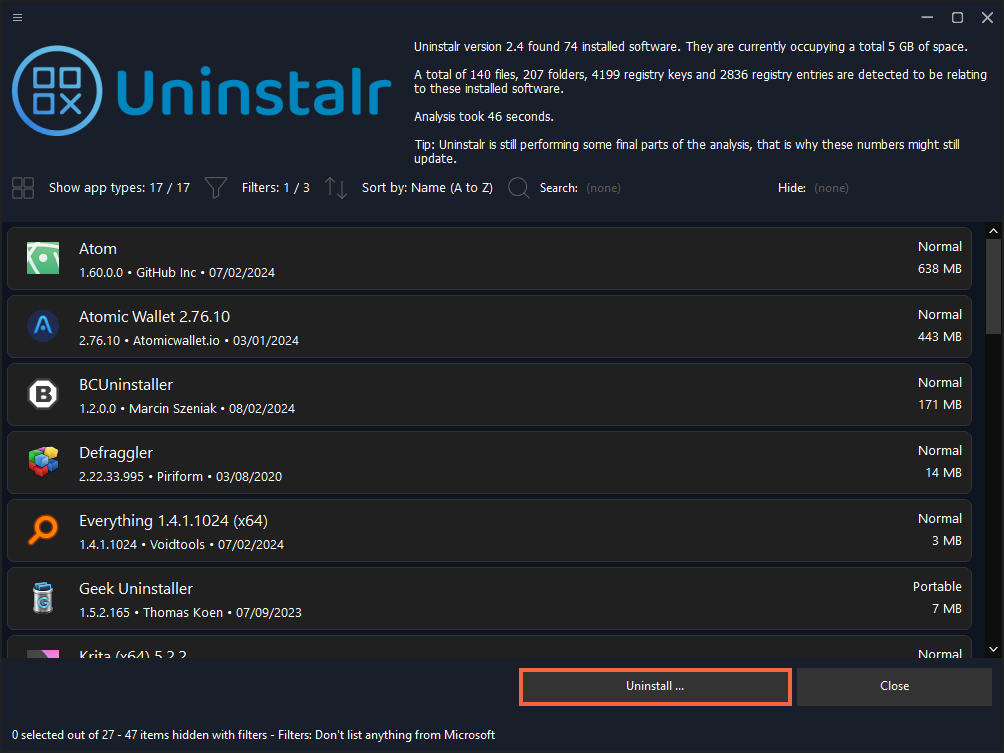 uninstalr.com
uninstalr.com
Uninstalr_Setup
Mops21
I have scan your homepage with virustotal and get this from virustotal

Uninstalr_Setup
Mops21
