I used to use cracked software in the past. If cracked file detected by Kaspersky, then I just find a different one.hahahah open the door to play as hell the malware as want. do not worry we all were that natives. we were follow the instructions mentioned in the cracking websites
run as admin and put it in exclusion as it is false positives hahahaa
Advice Request USB Malware
- Thread starter Nagisa
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
i used to download from trusted forms / teams such MDL forms/Daz teams but that was in the pastI used to use cracked software in the past. If cracked file detected by Kaspersky, then I just find a different one.
Well, nearly all my colleagues at university has صور حبيبتي.exe (the translation is My girlfriend's photos lol) malware on their flash drives. I do not know what it does, but Trend Micro detected it and failed to remove it.
you are single hahahaha in Egypt كحييييييييييييييانWell, nearly all my colleagues at university has صور حبيبتي.exe (the translation is My girlfriend's photos lol) malware on their flash drives. I do not know what it does, but Trend Micro detected it and failed to remove it.
always uncheck "Donot show extension for known files " to avoid packed with double extension "exe is hidden" it is type of file steganography to hide malwares old but still bit tricky
i was hit by some trojans or something and neither gdata nor norton could remove it because i was offline for a couple of weeks ...... avast did clean it
Is USB malware still relevant today?
Hello. The short answer is: Yes, USB malware is relevant.
The long answer:
As noted by some other members it doesn't get that much news coverage which is because there isn't anything new to say about it. They aren't rare, though, they are a daily occurrence at my work place. It is mostly still the same old families that are spreading via USB drives, e.g., Gamarue and Dinihou. Some RAT's, ransomware, and stealers adopted this strategy too but it is one feature of many, so it doesn't get too much attention.
Yes, the infamous autorun.inf method doesn't work anymore since Windows 7. Most USB spreaders today (including Dinihou, Gamarue) use a different method which requires the user to open one of the files on the USB flash drives.
USB worms today spread by placing windows shortcut files alongside your personal files on the drive. Then they hide the personal files. The shortcut files will look exactly like your personal files. So to you it will seem like those are the documents that you put there yourself. If you open them, the shortcuts will run the malware but also open your hidden personal files. You won't notice anything.
Shortcut icons usually have an arrow on the bottom left corner but even that is fixed by some of the worms using certain registry tweaks.
Examples of USB worm infections
Down below is an example of how a Spora infection looked like if you enable to view hidden files (taken from this article). This was probably due to a bug but the first Spora versions not only did the shortcut infection on removable drives but also on the C: drive. Here the legitimate folders (Programs Files etc) here were hidden by the malware. The five files at the bottom that look like folders are malware shortcuts and execute the hidden malware executable that is marked in red here as well as open the actual folder with explorer to not raise suspicion.
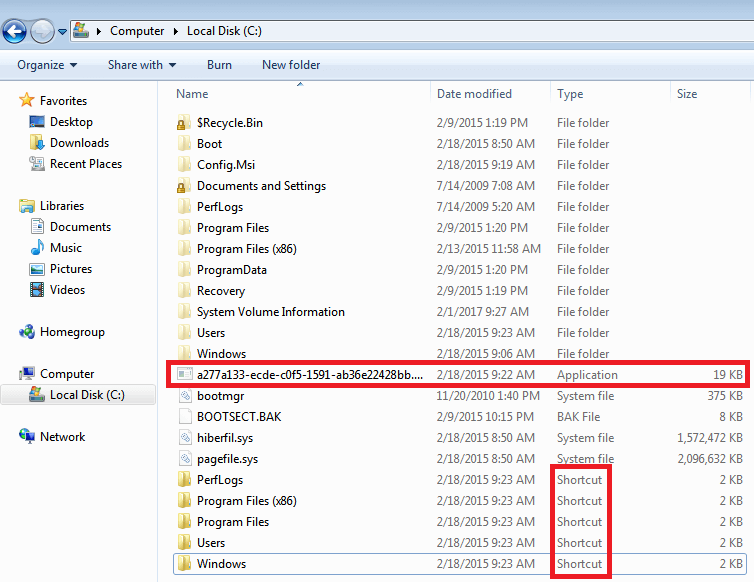
From the perspective of a user, you are executing the malware merely by browsing the folders on your system. If anyone asked you if you executed something odd, you will probably deny that, since you only opened folders. You can also see that the arrow that normally indicates a shortcut icon is missing here.
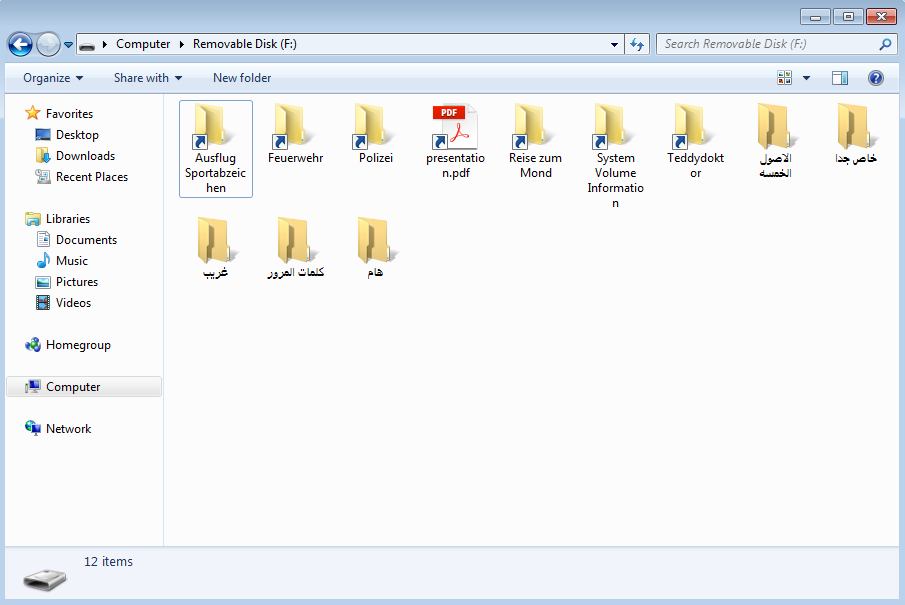
For comparison this is a Try2Cry infection on a USB flash drive which does not remove the arrow from the shortcut icons. So it might occur to you that something is wrong.
Other threats via USB
USB worms are not the only threat, but others are less relevant in terms of how likely you might be affected by them.
Viruses (file infectors) may spread via USB flash drives. But this only happens if you have no working Antivirus program because almost all viruses are very old and well-detected by them.
Of course you may also put malware executables on your USB drive yourself (e.g. you backup a trojanized version of a legit program). But that's not a USB drive specific issue.
Attacks via Rubberducky only work if you plug in someone else's USB flash drive or allow others to do that.
Protection from USB malware
Don't plug your USB flash drive in public computers.
Don't plug unknown USB flash drives into your computer.
Use an Antivirus program.
The shortcut files of USB worms usually run a hidden worm executable in the same location as well as open the original file. If you point a shortcut to cmd.exe or powershell.exe, you can run any command in it.@struppigel what is the shortcut usually pointing to, is it pointing to an executable, dropping script or downloading script?
I can see a 19 KB app on the picture above...
Is it the same for other threats?
Also, does the executable have the code to actually open the folder it mimics, or upon running it, nothing visible will happen?
I’ve seen some infostealers (don’t remember the family) that drops in the user folders XP-style shortcuts (Documents and Settings for example) and they point to a hidden executable in a similar manner.
E.g. Spora shortcut files will point to cmd.exe using the following arguments:
Code:
/c explorer.exe "<originalfile>" & type "<worm>" > "%%tmp%%\<worm>" & start "<originalfile>" "%%tmp%%\<worm>"This command runs explorer on the original file of the user. That means there is no need to have any code for mimicing the folder, the original folder or file is actually opened as usual.
Furthermore this command will copy the worm executable from the removable drive to TEMP and run it, thus, infect the system the USB drive is currently attached to.
Similarly, if it is not a folder but some document that the shortcut mimics, the original file will be opened as usual.
Edit: Having dropper or downloader LNKs wouldn't be good from the point of view of the attacker. Droppers are too big in size and you will need as many of them as there are files on the drive. Downloaders require Internet connection whereas USB worms can spread to devices without Internet. So from an attacker's perspective they would limit their targets if they used a downloader.
Last edited:
You may also like...
-
-
-
-
-
Suspicion regarding compromised Android smartphone.
- Started by Shikhar11
- Replies: 137

