Advice Request USB Malware
- Thread starter Nagisa
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
it exist but rarely and could be easily block by disabling Autorun/Autoplay features. also most malware is come from web so if your device is infected , Attached device will be infected 
@DDE_Server is correct. They do exist, but are rare even in the news flow.

 malwaretips.com
malwaretips.com
Member @struppigel though made an analysis on one of them.

 malwaretips.com
malwaretips.com

Rare BadUSB attack detected in the wild against US hospitality provider
Hackers use snail-mail to send target company an envelope with a malware-laced USB thumb drive. A US hospitality provider has recently been the target of an incredibly rare BadUSB attack, ZDNet has learned from cyber-security firm Trustwave. The attack happened after the company received an...
 malwaretips.com
malwaretips.com
Member @struppigel though made an analysis on one of them.

Try2Cry ransomware tries to worm
This is a small summary of a ransomware analysis I made. It's decryptable. Try2Cry ransomware adopts USB flash drive spreading using LNK files. The last ransomware that did the same was the infamous Spora. The code of Try2Cry looks oddly familiar, though. A big portion of my work as malware...
 malwaretips.com
malwaretips.com
More than you think, many people when buy a new PC, like to transfer files and programs from the old to the new, some of these programs are download from the internet, like KMS activators for the office or some IPTV player.
Many of these programs can contain malware, I infected my new PC with a Trojan with a KMS in a USB and suspect I am not the only one doing this.
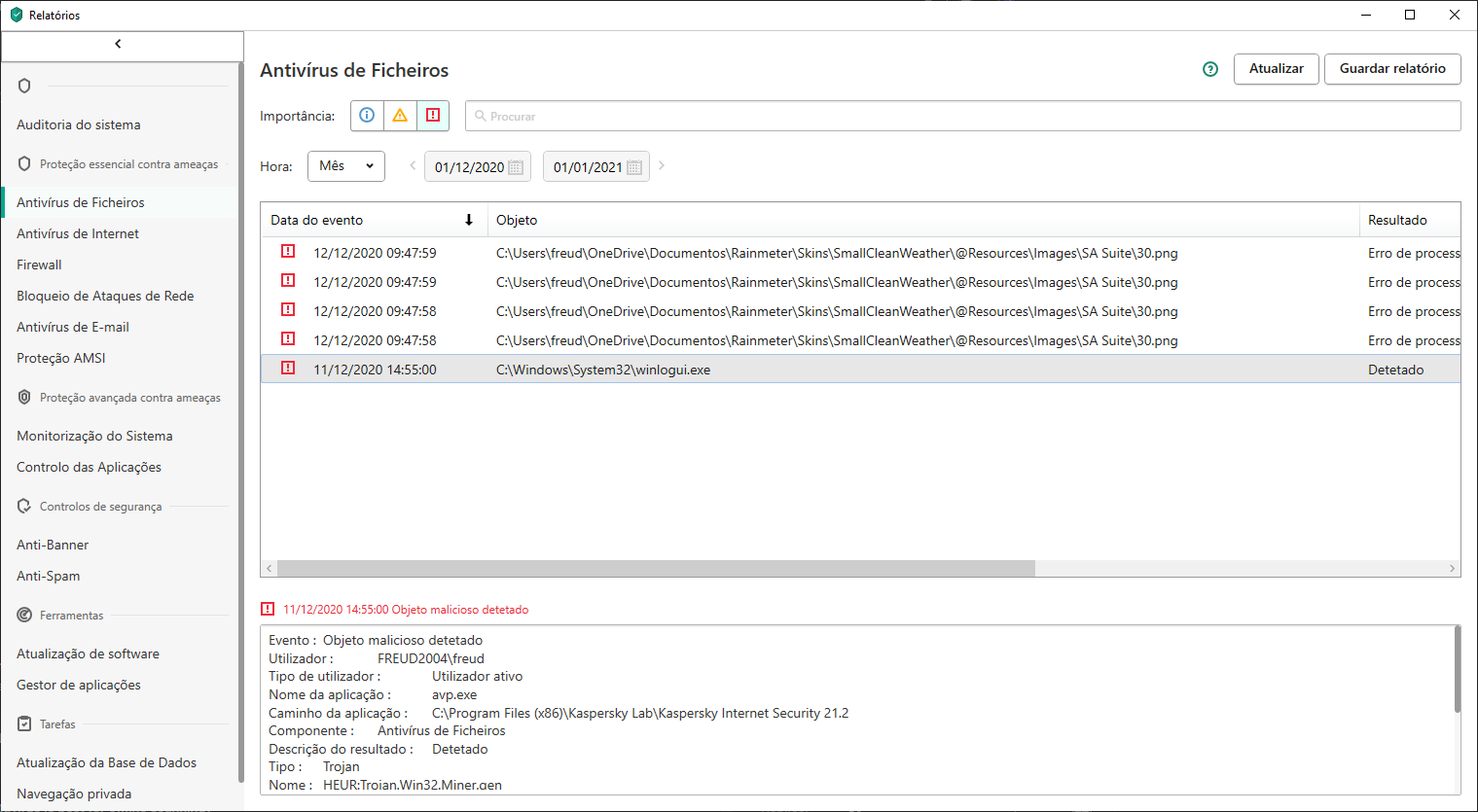
Many of these programs can contain malware, I infected my new PC with a Trojan with a KMS in a USB and suspect I am not the only one doing this.
F
ForgottenSeer 85179
just use SRP and problem solved.Hi, one of the things I do to a new PC is to disable Autorun, but if you use a tune-up utility that usually does it for you.
Also normal USB Malware isn't the real problem with USB devices. Bad-USB is.
the source is infected file downloaded from the internet. If you download the exe from official websites without using cracks then no problems also KMS is windows activator which is not self run so if you run it and gave it admin rights then you are the one to be blamedMore than you think, many people when buy a new PC, like to transfer files and programs from the old to the new, some of these programs are download from the internet, like KMS activators for the office or some IPTV player.
Many of these programs can contain malware, I infected my new PC with a Trojan with a KMS in a USB and suspect I am not the only one doing this.
View attachment 251946
he also could disable USB access via Group policyjust use SRP and problem solved.
Also normal USB Malware isn't the real problem with USB devices. Bad-USB is.
F
ForgottenSeer 85179
I don't think any enduser do thishe also could disable USB access via Group policy

if he/she are paranoid enoughI don't think any enduser do this
- Aug 17, 2014
- 12,729
- 123,837
- 8,399
Just to inform people who never heard about "BadUSB" looks like a useful report:
 www.manageengine.com
www.manageengine.com
What is BadUSB | How to Protect Against BadUSB Attacks - ManageEngine Device Control Plus
BadUSB is an attack to gain control over the targeted computers using keystroke injections. Learn more about types of BadUSBs and how to prevent BadUSB attacks.
it exist but rarely and could be easily block by disabling Autorun/Autoplay features. also most malware is come from web so if your device is infected , Attached device will be infected
Autorun is disabled by default since Windows 7. Autoplay is not dangerous. The modern USB malware does not use them at all.Hi, one of the things I do to a new PC is to disable Autorun, but if you use a tune-up utility that usually does it for you.
BadUSB simply emulates a keyboard. This can be done when using the USB device with a micro controller that allows for overwriting. There are commercial & legal devices that use this method for Admin or pentester tasks.
One can prevent BadUSB by restricting the installation of USB devices (not necessary in the home environment).
How to Fix the Critical BadUSB Security Flaw in Less than 10 Minutes (heimdalsecurity.com)
Another method (patched by Microsoft) depended on the exploit via the vulnerability in displaying the icon of the shortcut. This was a very dangerous infection technique.
In the home environment, the USB malware is usually related to a shortcut (LNK file) that pretends to be a document or another innocent file (by using a spoofed icon). The shortcut can run a payload that is hidden somewhere in the USB device.
yes some hardware keylogger are being sold in online marketing used to gain access to systems and run monitoring software for spyingAutorun is disabled by default since Windows 7. Autoplay is not dangerous. The modern USB malware does not use them at all.
BadUSB simply emulates a keyboard. This can be done when using the USB device with a micro controller that allows for overwriting. There are commercial & legal devices that use this method for Admin or pentester tasks.
One can prevent BadUSB by restricting the installation of USB devices (not necessary in the home environment).
How to Fix the Critical BadUSB Security Flaw in Less than 10 Minutes (heimdalsecurity.com)
Another method (patched by Microsoft) depended on the exploit via the vulnerability in displaying the icon of the shortcut. This was a very dangerous infection technique.
In the home environment, the USB malware is usually related to a shortcut (LNK file) that pretends to be a document or another innocent file (by using a spoofed icon). The shortcut can run a payload that is hidden somewhere in the USB device.
This can help in many cases. But will often fail when the shortcut uses scripting engines. The only effective method is blocking shortcuts on USB devices, but I know only a few solutions that can do that. One of them is Windows built-in SRP (a special and rare setting used in SWH and H_C).also if you have some sort of default deny solutions which is found in most security softs the malware will fail to run even it is not in your AV signature
Edit.
Other solutions like AppLocker and Application Control cannot do that. Shortcuts can be also blocked by AppGuard.
in production environment , The removable devices has certain type of protection in the protection solution which is called data lose prevention. The main function of it is monitoring the data at rest and when being transmitted. the device is classified and you enforce proper policies to control removable media access and it is level of access read/write/execute/no permission which depend on the classification of your data sensitivity 

if you uses Vodoosheild it will block script execution when shortcut will try to run it as i thinkThis can help in many cases. But will often fail when the shortcut uses scripting engines. The only effective method is blocking shortcuts on USB devices, but I know only a few solutions that can do that. One of them is Windows built-in SRP (a special and rare setting used in SWH and H_C).
Edit.
Other solutions like AppLocker and Application Control cannot do that. Shortcuts can be also blocked by AppGuard.
the source is infected file downloaded from the internet. If you download the exe from official websites without using cracks then no problems also KMS is windows activator which is not self run so if you run it and gave it admin rights then you are the one to be blamed

Yes I was stupid enough tum run an exe, with admin rights. Happens to the best
I am given the example what not to do.
that is the way we learn.by the hard wayYes I was stupid enough tum run an exe, with admin rights. Happens to the best.
I am given the example what not to do.
They explained how they crack worked and it was depend mainly on vulnerability in microsoft license system they were brilliant rallyKMS was and still famous Microsoft office/windows activator. to run it has to be as an admin as it create auto start service which automatically start each time with windows and office to activate it . it is real time crack

Just to finish.... I am so intelligent that I put the program in KIS exclusions, brilliant...
Because I want my new computer ready fast, so I could game, the bonus was a trojan.
So, don't do this, it's my advice.
Because I want my new computer ready fast, so I could game, the bonus was a trojan.
So, don't do this, it's my advice.
hahahah open the door to play as hell the malware as want. do not worry we all were that natives. we were follow the instructions mentioned in the cracking websitesJust to finish.... I am so intelligent that I put the program in KIS exclusions, brilliant...
Because I want my new computer ready fast, so I could game, the bonus was a trojan.
So, don't do this, it's my advice.
run as admin and put it in exclusion as it is false positives hahahaa
You may also like...
-
-
-
-
-
Suspicion regarding compromised Android smartphone.
- Started by Shikhar11
- Replies: 137
