Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
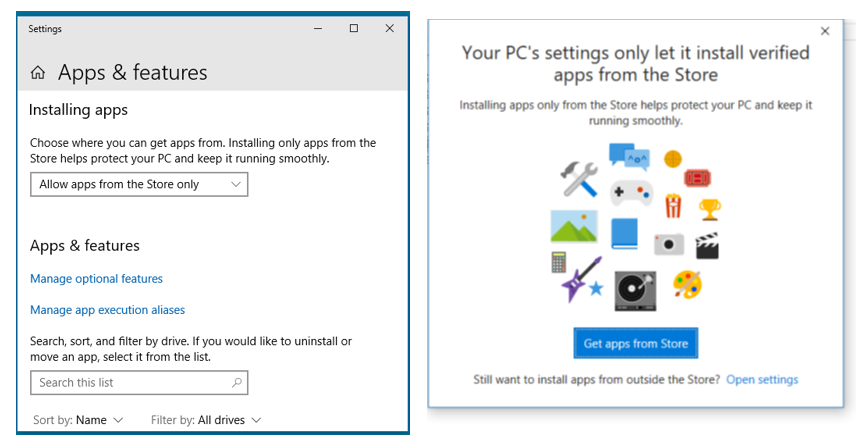
Pictures explain it all, when you try to execute a downloaded program it will be blocked (rtight), when clicking on change settings you will be shown options (left) to temporarily allow software not from Microsoft Store (and or non-Microsoft signed code). Windows update works okay while allowing aps from the Store only.