What?Really? there is some idiots that put their phone in their backpockets and sit on it...?
Use Windows 10 build-in (anti)execution options
- Thread starter Windows_Security
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Jul 3, 2015
- 8,153
Looks like Umbra didn't drink his coffee yet. He must have been replying to a different thread or PM or somethingWhat?
D
Deleted member 178
lol yes ^^He must have been replying to a different thread or PM or something
- Jul 3, 2015
- 8,153
@Windows_Security, would you be able to share your Exploit guard settings for MS Word, Excel and Powerpoint?Windows 10 has so many great build in features. Bu some are hidden or not easy to find. Also with WD exploit protection, every update overwrites the programs alread set by Windows back to its default. When you want to add stuf (e.g. PowerPoint below), you need to ad a full path name rule to make your additions stick/permanent.
View attachment 193519
And if anyone else has a set of rules that works for these apps, please share. Or link me to relevant content.
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Mar 13, 2016
- 1,298
@shmu26
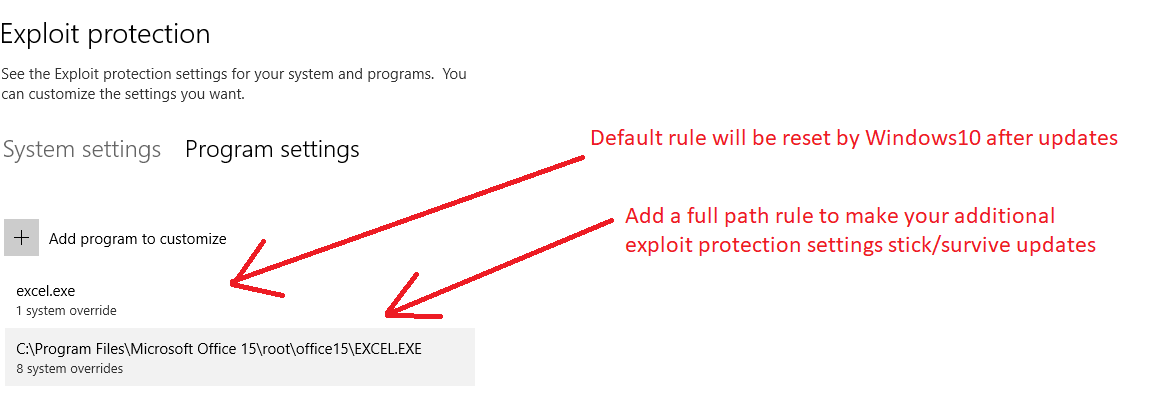
Example for Excell (they are all the same for Word, Powerpoint) for my Office 2013 which came with my Asus Transformer
- Block low integrity images
- Block remote images
- Block untrusted fonts
- Code integrity guard
- Disable extension points
- Do not allow child processes
- Force randomization for images (Mandatory ASLR) ==> this is the default rule
- Validate image dependency integrity
I have to check my wife's Yoga520, she also has Outlook on her Office 2016, I think Outlook is allowed to launch child processes. Checked: Outlook is allowed to start other child programs.
My system defaults are:
- Control Flow Guard
- DEP
- SEHOP
- Validate HEAP
Above is on 32 bits with Office 2013. I read somewhere that code integrity guard is enabled by default for Microsoft products compiled with Visual Code studio 2015 or above, so this would mean that at least a few of above settings are probably already enabled when using Office 2016.
Example for Excell (they are all the same for Word, Powerpoint) for my Office 2013 which came with my Asus Transformer
- Block low integrity images
- Block remote images
- Block untrusted fonts
- Code integrity guard
- Disable extension points
- Do not allow child processes
- Force randomization for images (Mandatory ASLR) ==> this is the default rule
- Validate image dependency integrity
I have to check my wife's Yoga520, she also has Outlook on her Office 2016, I think Outlook is allowed to launch child processes. Checked: Outlook is allowed to start other child programs.
My system defaults are:
- Control Flow Guard
- DEP
- SEHOP
- Validate HEAP
Above is on 32 bits with Office 2013. I read somewhere that code integrity guard is enabled by default for Microsoft products compiled with Visual Code studio 2015 or above, so this would mean that at least a few of above settings are probably already enabled when using Office 2016.
Last edited:
- Dec 23, 2014
- 8,908
Access, Excel, Outlook, PowerPoint, Word
Windows default system-wide mitigations: Control Flow Guard (CFG), DEP (for 64-bit apps), Randomize memory allocations (Bottom-Up ASLR), High entropy ASLR, Validate exception chains (SEHOP), Validate heap integrity.
.
Microsoft Security BaseLine Windows ver. 1803 (the below per-application mitigations should be activated alongside system-wide): DEP (for 32-bit apps), Export address filtering (EAF), Force randomization for images (Mandatory ASLR), Import address filtering (IAF), Simulate Execution (SimExec), Validate API Invocation (CallerCheck), Validate Stack Integrity (StackPivot).
'
Do not allow child processes is not required (for MS Office) if one uses ASR, although this mitigation is stronger, because the user cannot start printing session (printing is still possible with some trick) and cannot open any other applications from the protected one (Word cannot open an embedded spreadsheet in Excel etc.).
.
Block untrusted fonts mitigation is not required for most users, because in Windows 10, the GDI font parsing is no longer performed in kernel mode but via fontdrvhost.exe, which is running in AppContainer (user mode). Blocking untrusted fonts is the system-wide mitigation, so the fonts are blocked everywhere (PDF viewers, 3rd party web browsers, etc.) - sometimes this can be not convenient (not readable text).
.
Other mitigations are also possible, but should be tested on the concrete machine, because some apps integrated with MS Office applications may work improperly.
Windows default system-wide mitigations: Control Flow Guard (CFG), DEP (for 64-bit apps), Randomize memory allocations (Bottom-Up ASLR), High entropy ASLR, Validate exception chains (SEHOP), Validate heap integrity.
.
Microsoft Security BaseLine Windows ver. 1803 (the below per-application mitigations should be activated alongside system-wide): DEP (for 32-bit apps), Export address filtering (EAF), Force randomization for images (Mandatory ASLR), Import address filtering (IAF), Simulate Execution (SimExec), Validate API Invocation (CallerCheck), Validate Stack Integrity (StackPivot).
'
Do not allow child processes is not required (for MS Office) if one uses ASR, although this mitigation is stronger, because the user cannot start printing session (printing is still possible with some trick) and cannot open any other applications from the protected one (Word cannot open an embedded spreadsheet in Excel etc.).
.
Block untrusted fonts mitigation is not required for most users, because in Windows 10, the GDI font parsing is no longer performed in kernel mode but via fontdrvhost.exe, which is running in AppContainer (user mode). Blocking untrusted fonts is the system-wide mitigation, so the fonts are blocked everywhere (PDF viewers, 3rd party web browsers, etc.) - sometimes this can be not convenient (not readable text).
.
Other mitigations are also possible, but should be tested on the concrete machine, because some apps integrated with MS Office applications may work improperly.
Last edited:
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Mar 13, 2016
- 1,298
@Andy Ful,: The trick you mention is that save as PDF and then print the PDF to paper?
- Dec 23, 2014
- 8,908
That should work well for printing one or two documents, because printing has to be done with external PDF application. There is another trick for printing many documents directly from the protected MS Office.@Andy Ful,: The trick you mention is that save as PDF and then print the PDF to paper?
One has to print once from another application that leaves the printing session opened. Not every application works that way. I noticed that Adobe Touch (Universal Application for viewing/printing PDF files), leaves the printing session opened. So, I prepared a blank PDF document (in Word) and saved it on the Desktop with the name 'Start Printing Session'. Then after printing the blank PDF from Adobe Touch, I could print freely all the day from protected MS Office applications.
If I correctly remember, that trick also worked with Word Mobile (free) which is an excellent Universal Application for viewing MS Word documents (also Excel Mobile and PowerPoint Mobile for other documents).
Last edited:
- Jul 3, 2015
- 8,153
- Jul 3, 2015
- 8,153
@Andy Ful: so bottom line, what do you say are the recommended WDEG rules for a typical user to enable for Word/Excel/Powerpoint, on Windows 10 1803?Access, Excel, Outlook, PowerPoint, Word
Windows default system-wide mitigations: Control Flow Guard (CFG), DEP (for 64-bit apps), Randomize memory allocations (Bottom-Up ASLR), High entropy ASLR, Validate exception chains (SEHOP), Validate heap integrity.
.
Microsoft Security BaseLine Windows ver. 1803 (the below per-application mitigations are activated alongside system-wide): DEP (for 32-bit apps), Export address filtering (EAF), Force randomization for images (Mandatory ASLR), Import address filtering (IAF), Simulate Execution (SimExec), Validate API Invocation (CallerCheck), Validate Stack Integrity (StackPivot).
'
Do not allow child processes is not required (for MS Office) if one uses ASR, although this mitigation is stronger, because the user cannot start printing session (printing is still possible with some trick) and cannot open any other applications from the protected one (Word cannot open an embedded spreadsheet in Excel etc.).
.
Block untrusted fonts mitigation is not required for most users, because in Windows 10, the GDI font parsing is no longer performed in kernel mode but via fontdrvhost.exe, which is running in AppContainer (user mode). Blocking untrusted fonts is the system-wide mitigation, so the fonts are blocked everywhere (PDF viewers, 3rd party web browsers, etc.) - sometimes this can be not convenient (not readable text).
.
Other mitigations are also possible, but should be tested on the concrete machine, because some apps integrated with MS Office applications may work improperly.
And if 3rd party AV?
Last edited:
- Dec 23, 2014
- 8,908
That is simple. Do not touch anything & use default settings.:emoji_disappointed:@Andy Ful: so bottom line, what do you say are the recommended WDEG rules for a typical user to enable for Word/Excel/Powerpoint, on Windows 10 1803?
Microsoft always "knew better" what is good for the customers. Home users were usually the 'guinea pigs' for them. Many security features were (and still are) poorly documented. Microsoft introduced many different command interpreters, programming interfaces, and software components (CMD Shell, Windows Script Host, PowerShell, VBA, .NET Framework, COM Objects, WMI, ActiveX, OLE, Application Shim, etc.). The same can be said for managing the networks. Almost any file can be dangerous and can support exploits. Executable code can be run/injected/hooked in many different ways. MS Office can be abused easily and the new versions can introduce the new attack vectors. Windows 10 is a nightmare for security software developers. I could complain and complain about how bad Microsoft is from the security point of view.
My personal opinion is that Microsoft equally contributed to the development of society computerization and to the development of computer malware.
Should we blame Microsoft for this? Maybe, so. Unfortunately, evolution did the same for all living organisms.
Last edited:
- Jul 3, 2015
- 8,153
Well, I am not a big fan of the theory of evolution, but if I was to craft a WDEG policy for Office apps, I would enable the following. I created this tentative list based on @Windows_Security's policy, subtracting the mitigations about which you said that they are already activated by default on Windows 10 1803. Please comment, especially if I misunderstood something. (I can't claim that I really know what all these mitigations are actually doing...)That is simple. Do not touch anything & use default settings.:emoji_disappointed:
Microsoft always "knew better" what is good for the customers. Home users were usually the 'guinea pigs' for them. Many security features were (and still are) poorly documented. Microsoft introduced many different command interpreters, programming interfaces, and software components (CMD Shell, Windows Script Host, PowerShell, VBA, .NET Framework, COM Objects, WMI, ActiveX, OLE, Application Shim, etc.). The same can be said for managing the networks. Almost any file can be dangerous and can support exploits. Executable code can be run/injected/hooked in many different ways. MS Office can be abused easily and the new versions can introduce the new attack vectors. Windows 10 is a nightmare for security software developers. I could complain and complain about how bad Microsoft is from the security point of view.
My personal opinion is that Microsoft equally contributed to the development of society computerization and to the development of computer malware.
Should we blame Microsoft for this? Maybe, so. Unfortunately, evolution did the same for all living organisms.
enable:
Block remote images
Code integrity guard
Disable extension points
Force randomization for images
Validate image dependency integrity
I would not enable "Do not allow child processes" because of printing issues and other usability issues. This mitigation is covered sufficiently well by ASR.
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Mar 13, 2016
- 1,298
My Windows 10 Security using internal mechanisms only
 thanks to this forum (to use ideas), Andy and Andreas
thanks to this forum (to use ideas), Andy and Andreas 
P.S. maybe Andy could add 7 and 8 to Hard Configrator (with seperate option to set ACL deny execute file/traverse on download folders, becauise that is the only one with functional impact.) Setting this ACL on public folders or User/Appdata/Temp temporaray Internet folders, etc. has zero functional impact). So many hurdles and tripwires for malware makes me smile and security a non-issue.
- Andy's Configure (Windows) Defender (to easily enable Attack Surface Reduction, Smartscreen and other stuff)
- Andy's Hard Configurator to block execution of removable disks and run as basic user (allow run as admin)
- Andreas' NVT (Windows) SysHardener (to disable all the home user obsolete stuff and set UAC to deny elevation of unsigned)
- Eenabled Windows Defender protected folders feature for Ransonware protection
- Allow user to only install apps from store
- Added a few extra WD Anti Exploit Protection settings (e.g. Edge, Office2013 and Powershell)
- Added a Deny Execute Access Control List for internet facing folders and User startup folders (last one also with deny create/write)
- Removed basic user rights from HKCU startup entries with regedit
- Added MalwareBytes extension for Chrome with some about:flags hardening and Adguard to Edge (with optimized filters and browser security enabled), using Norton Safebrowsing as DNS (set in hardware properties of wireless card)
- Added user programs (in AppData) and startup folders to protected folders list to effectively set them in whitelist mode (thx @Andy Ful for the TIP) and close Basic User holes
P.S. maybe Andy could add 7 and 8 to Hard Configrator (with seperate option to set ACL deny execute file/traverse on download folders, becauise that is the only one with functional impact.) Setting this ACL on public folders or User/Appdata/Temp temporaray Internet folders, etc. has zero functional impact). So many hurdles and tripwires for malware makes me smile and security a non-issue.
Last edited:
- Dec 23, 2014
- 8,908
Yes. I think that my post could be misunderstood, so I edited the phrase "are activated" to 'should be activated".Well, I am not a big fan of the theory of evolution, but if I was to craft a WDEG policy for Office apps, I would enable the following. I created this tentative list based on @Windows_Security's policy, subtracting the mitigations about which you said that they are already activated by default on Windows 10 1803. Please comment, especially if I misunderstood something. (I can't claim that I really know what all these mitigations are actually doing...)
enable:
Block remote images
Code integrity guard
Disable extension points
Force randomization for images
Validate image dependency integrity
I would not enable "Do not allow child processes" because of printing issues and other usability issues. This mitigation is covered sufficiently well by ASR.
I meant that all blue mitigations in my post:
Windows 10 - Use Windows 10 build-in (anti)execution options
are activated in Microsoft Security BaseLine Windows ver. 1803. It means that they should be activated by the user via Exploit Guard panel.
Windows_Security mitigations are (mostly) beyond Microsoft Security BaseLine for Windows ver. 1803 . If they work on his computer, then probably can work on many other computers.
I would recommend to start with Security BaseLine first, and after some time (if all works well) apply the rest proposed mitigations.
- Jul 3, 2015
- 8,153
Okay, that takes the mystery out of it. It makes a lot more sense now.Yes. I think that my post could be misunderstood, so I edited the phrase "are activated" to 'should be activated".
I meant that all blue mitigations in my post:
Windows 10 - Use Windows 10 build-in (anti)execution options
are activated in Microsoft Security BaseLine Windows ver. 1803. It means that they should be activated by the user via Exploit Guard panel.
Windows_Security mitigations are (mostly) beyond Microsoft Security BaseLine for Windows ver. 1803 . If they work on his computer, then probably can work on many other computers.
I would recommend to start with Security BaseLine first, and after some time (if all works well) apply the rest proposed mitigations.
- Dec 23, 2014
- 8,908
Wow, I am impressed to see such restricted & secure setup.My Windows 10 Security using internal mechanisms only
So IMO opinion on Windows 10 Home edition security is a non-issue
- Andy's Configure (Windows) Defender (to easily enable Attack Surface Reduction, Smartscreen and other stuff)
- Andy's Hard Configurator to block execution of removable disks and run as basic user (allow run as admin)
- Andreas' NVT (Windows) SysHardener (to disable all the home user obsolete stuff and set UAC to deny elevation of unsigned)
- Eenabled Windows Defender protected folders feature for Ransonware protection
- Allow user to only install apps from store
- Added a few extra WD Anti Exploit Protection settings (e.g. Edge, Office2013 and Powershell)
- Added a Deny Execute Access Control List for internet facing folders and User startup folders (last one also with deny create/write)
- Removed basic user rights from HKCU startup entries with regedit
- Added MalwareBytes extension for Chrome with some about:flags hardening and Adguard to Edge (with optimized filters and browser security enabled), using Norton Safebrowsing as DNS (set in hardware properties of wireless card)
- Using Kaspersky free Secure Connection VPN on ad-hoc basis (only when abroad for online banking & booking)
thanks to this forum (to use ideas), Andy and Andreas
P.S. maybe Andy could add 7 and 8 to Hard Configrator (with seperate option to set ACL deny execute file/traverse on download folders, becauise that is the only one with functional impact.) Setting this ACL on public folders or User/Appdata/Temp temporaray Internet folders, etc. has zero functional impact). So many hurdles and tripwires for malware makes me smile and security a non-issue.
The point 7 is covered in default-deny setup. The create/write restrictions can be applied via Ransomware protection. Please post your ideas, if you can see additional advantages of doing this also via ACL.
I was considering the point 8, but Windows Updates and updates of some applications, often use those keys. I think that it will prevent OneDrive updates.
Last edited:
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Mar 13, 2016
- 1,298
Andy,
only install. also' regular' programs which use the HKLM run keys (elevated). Because ransomware likes to misuses the HKCU keys to survive re-boot, I don't set a deny, but remove the rights of standard user, so in order to change them you need to be admin or higher. Same trick with windows startfolders for users, don't set a deny, but remove the create/write rights for current user. this still allow updates invoked by Windows itself (as admin, system or trusted installer).
I use basic user as default level with run MSI as admin reg tweak, So right click run as admin allows to install everything. I know this is not as secure as Default deny (not anymore when adding these folder holes to protected folders feature of WD), I like to have the option to right click run as admin to install stuff.I accept the down side that basic user has holes compared to default deny
It is my experience that you don't need a watertight block, just adding several hurdles and tripwires from different angles, makes it very dificult for exploits to succeed (e.g. add a WD exploit rule for powershell to disable launching child processes, I don't need NVT OS armor for that).
I
Regards
Kees
only install. also' regular' programs which use the HKLM run keys (elevated). Because ransomware likes to misuses the HKCU keys to survive re-boot, I don't set a deny, but remove the rights of standard user, so in order to change them you need to be admin or higher. Same trick with windows startfolders for users, don't set a deny, but remove the create/write rights for current user. this still allow updates invoked by Windows itself (as admin, system or trusted installer).
I use basic user as default level with run MSI as admin reg tweak, So right click run as admin allows to install everything. I know this is not as secure as Default deny (not anymore when adding these folder holes to protected folders feature of WD), I like to have the option to right click run as admin to install stuff.
It is my experience that you don't need a watertight block, just adding several hurdles and tripwires from different angles, makes it very dificult for exploits to succeed (e.g. add a WD exploit rule for powershell to disable launching child processes, I don't need NVT OS armor for that).
I
Regards
Kees
Last edited:
- Dec 23, 2014
- 8,908
Understand. My point is that some updates use this key also as standard user (no admin rights) - the Windows OneDrive is an example. That is also common for most updates for applications that are installed in the Userspace, because they do not need admin rights to update.Andy,
only install. also' regular' programs which use the HKLM run keys (elevated). Because ransomware likes to misuses the HKCU keys to survive re-boot, I don't set a deny, but remove the rights of standard user, so in order to change them you need to be admin or higher.
I am still considering such protection, because the malware can often use the Run key in HKCU hive to get persistence. But maybe the better solution will be installing one of the simple realtime tools that can notify about modifying the Run key?
Yes, that could be an advantage over blocking those folders by the WD Ransomware protection. The installations in the Userspace will not be a problem (mostly), except OneDrive and other installers that cannot be run as administrator.Same trick with windows startfolders for users, don't set a deny, but remove the create/write rights for current user. this still allow updates invoked by Windows itself (as admin, system or trusted installer).
I have to think it over, because the Start Folders are already well protected in Hard_Configurator via SRP. In the Recommended SRP settings those restrictions are higher than ACL deny execute. I did not see the malware in the wild that could bypass that protection and execute the payload as standard user, even when the payload was copied there.
You have the special setup that does not allow elevation of unsigned executables, so you cannot use directly the "Run As SmartScreen" option (RunAsSmartscreen executable is not digitally signed and requires elevation). That is OK, for the users which know the limitations of Windows SmartScreen. Your setup is still default-deny for files running as standard user (SRP 'Default Security Level' = Disallowed or Basic User) and additionally restricted on the elevation of unsigned programs.I use basic user as default level with run MSI as admin reg tweak, So right click run as admin allows to install everything. I know this is not as secure as Default deny., I like to have the option to right click run as admin to install stuff.I accept the down side that basic user has holes compared to default deny. but I trust ASR and Smartscreen to block execution (by myself) of untrusted/poor reputation programs.
The second will trigger only when something could bypass the first.
The mitigation 'Disabling child processes in PowerShell' + Constrained Language mode (applied by SRP) is a pretty good protection. Anyway, I think that you can disable PowerShell executables via Hard_Configurator (<Block Sponsors>). Windows Updates use directly System.Management.Automation.dll to retrieve PowerShell functions. System scheduled tasks and other processes will bypass this protection when running with admin or higher rights.It is my experience that you don't need a watertight block, just adding several hurdles and tripwires from different angles, makes it very dificult for exploits to succeed (e.g. add a WD exploit rule for powershell to disable launching child processes, I don't need NVT OS armor for that).
.
Regards
Last edited:
- Jul 3, 2015
- 8,153
So if you block powershell.exe with an anti-exe software, Windows Updates will bypass it?Windows Updates use directly System.Management.Automation.dll to retrieve PowerShell functions.
- Dec 23, 2014
- 8,908
Yes, except maybe a few updates for 3rd party vendors (AMD, Intel, NVIDIA, etc.). I am not sure about updates from Microsoft Store, but this should not be the issue.So if you block powershell.exe with an anti-exe software, Windows Updates will bypass it?
.
Edit.
Some scheduled tasks and some software can use Powershell executables, but this can be solved by the semi-advanced user via adding whitelisted commandlines to the anti-exe program.
Last edited:
Similar threads
B
- Replies
- 0
- Views
- 306
B
-
- Sticky
- Poll
Serious Discussion
Pre-execution vs post-execution protections explained
- Replies
- 6
- Views
- 1,750
