- Dec 23, 2014
- 8,816
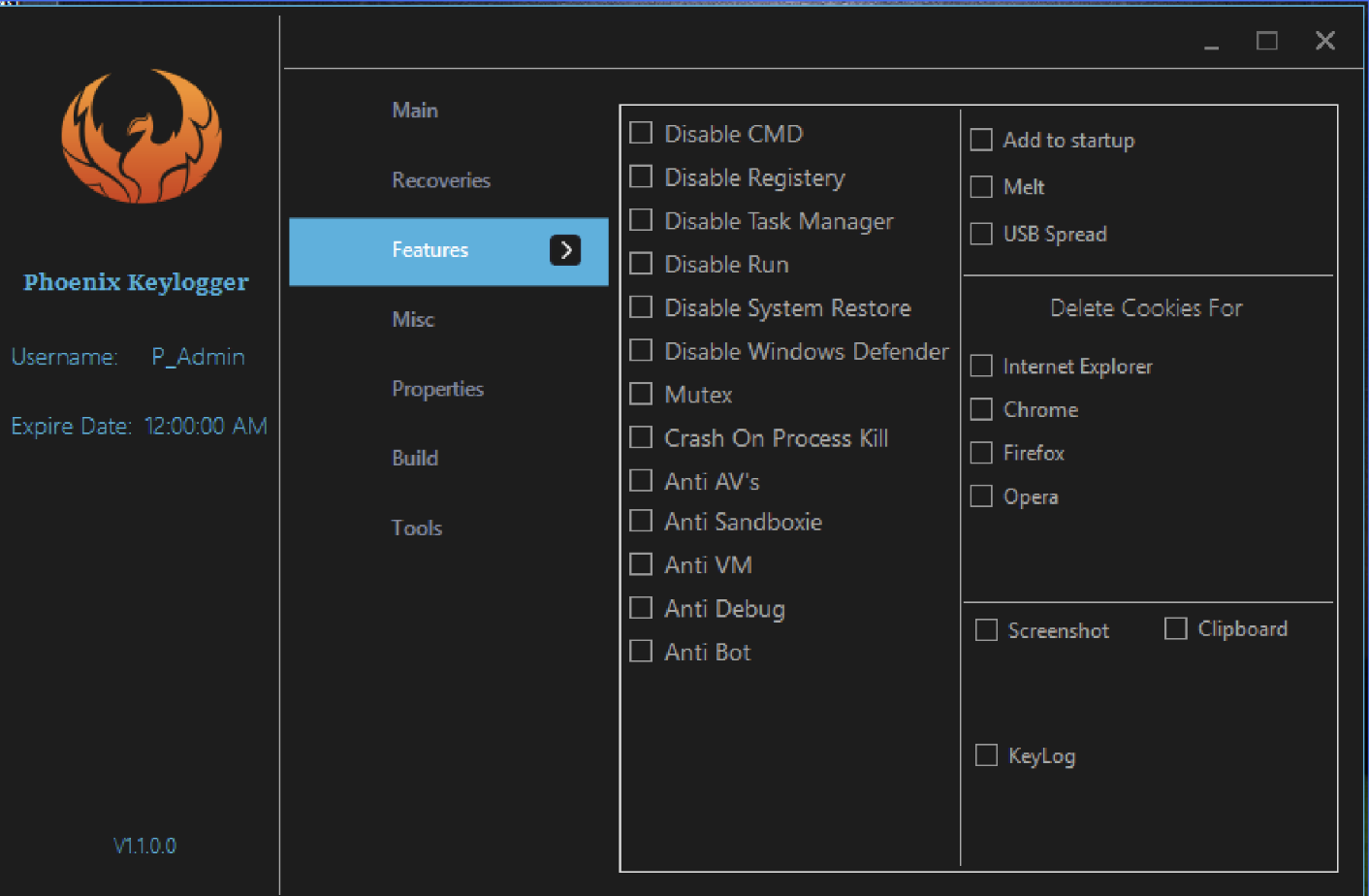
That is right. Using both H_C and VS can hardly be recommended, for many reasons....
What VS will add? nothing much, so basically wasting resources and offering surface attacks.
Anyway, many users will choose VS (over SRP/H_C) because it seems more user-friendly. Windows built-in SRP blocks some processes silently, so the user who is not trained/accustomed to security Logs can have a problem to see if something was blocked and what concretely was blocked.
It is much easier with H_C because it uses NirSoft FullEventLogView (with custom config) to see the blocked entries, but it is still easier with VS because the info about the blocked process can be seen in the VS alert.
On the other side, some users will prefer SRP, if they do not like too much prompting about things they already know.