Thank you oldschool. I use Lockdown with Kaspersky IS. I'm experimenting what posture works best while i'm gaming and browsing the web without too many popups.Almost as effective but still substantial protection with less alerts. Autopilot is what Dan recommends for tests because it is most like an AV (for testing purposes).
New Update VoodooShield CyberLock 7.0
- Thread starter danb
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
AutoPilot is really meant to only be used if you have another robust security product, and you want an extra layer of protection, like VoodooAi and WhitelistCloud. A lot of people also run CyberLock on AutoPilot for a day or two after after it was just installed, to reduce any potential unwanted blocks. So AutoPilot is quite effective, but really, if you are browsing the web or checking email, your computer should be lockedHey Dan
Keeping Cyberlock in "Auto Pilot" be just as affective as "Smart/Always on" mode?
Thank you Dan. It's an amazing program.AutoPilot is really meant to only be used if you have another robust security product, and you want an extra layer of protection, like VoodooAi and WhitelistCloud. A lot of people also run CyberLock on AutoPilot for a day or two after after it was just installed, to reduce any potential unwanted blocks. So AutoPilot is quite effective, but really, if you are browsing the web or checking email, your computer should be locked.
Sorry for the delay, but I keep thinking of new features and tweaks to add, and some of the new features and tweaks will also help explain how the new Attack Chains feature works. It is actually quite complex, but I think we can present it in a way that is super easy to understand.Eagerly awaiting for that version.
It's funny, for around a decade there was a constant flow of new ideas and tweaks to add to VS, but the last 3-4 months we finally ran out of new ideas. But it looks like this new feature is going to create tons of new ideas that we can add and build upon. I already have some super cool stuff in mind, but I am going to take a coding break for a few days after killing myself on this new feature
Hey Guys!
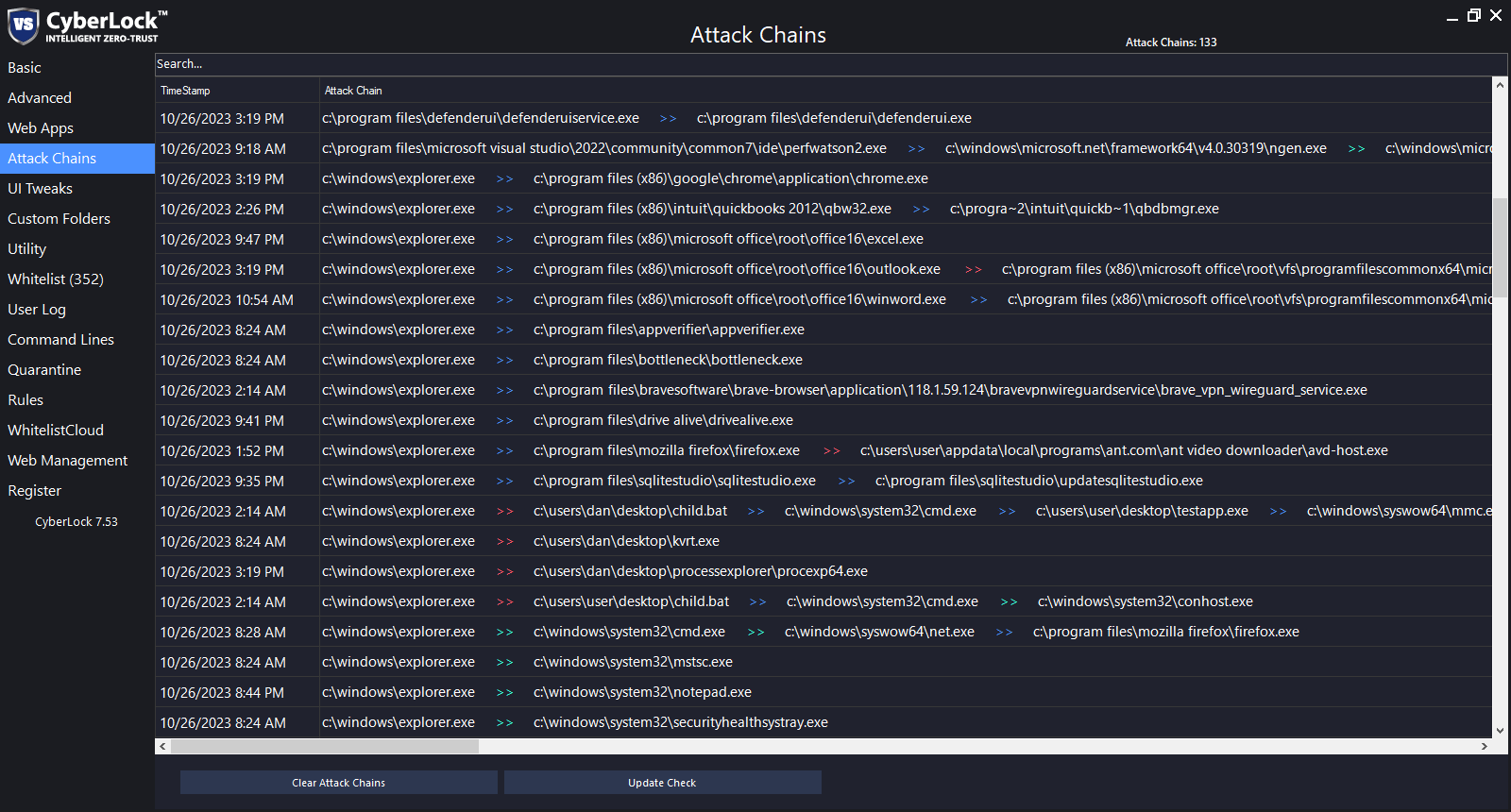
Here is the latest version of CyberLock that has implemented the new Attack Chains feature. Please keep in mind the Attack Chains feature is very new and there are tons of really cool features we will add soon. You will see colored arrows in the Attack Chain list. These are based on rules that we need to finish defining, so the colored arrows do not necessarily represent what actions CyberLock is going to take at each link of the chain. We have written most of the basic rules, but we need to tweak the rules a little and add a few more.
Ultimately, hopefully within a month or so, the colored arrows and rules will match CyberLock’s actions, and then we will be able to fully implement this new feature. It is actually going to be quite easy and fun to do, and we are a lot further along than I thought we would be. And if things go right, we might even be able to do away with the command lines feature altogether, and instead of having a Whitelist, we will have an App list, Web App list, Vulnerable App list, etc. It is difficult to explain, but it is going to be very cool. We will also be able to eliminate most of the remaining unwanted blocks.
Some of the rules for the new attack chain feature are already implemented and auto allowing items that would otherwise be blocked. You can search the developer log for “RuleID: 77” to see these items.
So we have a little more work to do, but I wanted you guys to see what the new attack chains feature is all about, because trust me, there are going to be tons of really cool things we can do with it.
It takes an hour or so to start really building up the attack chain list in CyberLock Settings. In fact, if you restart your computer after installing the new version, it will add a lot of them pretty quick.
This version is completely stable, but it is labeled a beta because there is a super small chance that one of the rules that are already implemented is not correct, so I just want you guys to be aware of this so you can be extra careful until we have the rules where we want them.
You guys will understand pretty quickly how this new feature works, but basically, if you see a red arrow, that means CyberLock should block the attack chain at that point. Like I was saying, the rules are not 100% right yet, so if you see any attack chains that do not seem correct, please let me know and we can fix it. Once they are all fixed, we will fully implement the rules so that CyberLock will block the attack chains at the red arrows. BTW, if you see any white arrows, please let me know, that means that none of the rules were applied to the arrow.
Green arrows: System Processes
Blue arrows: Allow / Benign / Safe
Red arrows: Block / Malicious / Not Safe
CyberLock 7.53 beta
SHA-256: 6edee845df7afdfa09db64e7491bb5ac3378c31bc99ee0f7d96342cb8b6e20d0
Have a great weekend!
Dan
Here is the latest version of CyberLock that has implemented the new Attack Chains feature. Please keep in mind the Attack Chains feature is very new and there are tons of really cool features we will add soon. You will see colored arrows in the Attack Chain list. These are based on rules that we need to finish defining, so the colored arrows do not necessarily represent what actions CyberLock is going to take at each link of the chain. We have written most of the basic rules, but we need to tweak the rules a little and add a few more.
Ultimately, hopefully within a month or so, the colored arrows and rules will match CyberLock’s actions, and then we will be able to fully implement this new feature. It is actually going to be quite easy and fun to do, and we are a lot further along than I thought we would be. And if things go right, we might even be able to do away with the command lines feature altogether, and instead of having a Whitelist, we will have an App list, Web App list, Vulnerable App list, etc. It is difficult to explain, but it is going to be very cool. We will also be able to eliminate most of the remaining unwanted blocks.
Some of the rules for the new attack chain feature are already implemented and auto allowing items that would otherwise be blocked. You can search the developer log for “RuleID: 77” to see these items.
So we have a little more work to do, but I wanted you guys to see what the new attack chains feature is all about, because trust me, there are going to be tons of really cool things we can do with it.
It takes an hour or so to start really building up the attack chain list in CyberLock Settings. In fact, if you restart your computer after installing the new version, it will add a lot of them pretty quick.
This version is completely stable, but it is labeled a beta because there is a super small chance that one of the rules that are already implemented is not correct, so I just want you guys to be aware of this so you can be extra careful until we have the rules where we want them.
You guys will understand pretty quickly how this new feature works, but basically, if you see a red arrow, that means CyberLock should block the attack chain at that point. Like I was saying, the rules are not 100% right yet, so if you see any attack chains that do not seem correct, please let me know and we can fix it. Once they are all fixed, we will fully implement the rules so that CyberLock will block the attack chains at the red arrows. BTW, if you see any white arrows, please let me know, that means that none of the rules were applied to the arrow.
Green arrows: System Processes
Blue arrows: Allow / Benign / Safe
Red arrows: Block / Malicious / Not Safe
CyberLock 7.53 beta
SHA-256: 6edee845df7afdfa09db64e7491bb5ac3378c31bc99ee0f7d96342cb8b6e20d0
Have a great weekend!
Dan
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Hey @danb ,
How can I report attack chains that do not seem correct to you?
I can't copy them from that screen.
I saw a red arrow involving mpcmdrun,exe, olk.exe and when updating Edge to the latest version.
How can I report attack chains that do not seem correct to you?
I can't copy them from that screen.
I saw a red arrow involving mpcmdrun,exe, olk.exe and when updating Edge to the latest version.
Gandalf_The_Grey: Do you have any idea on the license subscription period for Voodooshield still valid
for this new CyberLock?
for this new CyberLock?
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Yes, it is the same, just another name...Gandalf_The_Grey: Do you have any idea on the license subscription period for Voodooshield still valid
for this new CyberLock?
Oops, I forgot to mention that, thank you. Please take a screenshot with a snipping tool that allows you to just screenshot the one attack chain. A screenshot will be perfect, that was I can see the color of all of the arrows, and I can keep all of them and double check them as we refine the attack chain rules. BTW, so far there are only a total of 5 rules, and they got us to about 95% of where we need to be, so I am guessing we will probably only need a few more rules for everything to be correct and so we can fully implement this new feature into CyberLock. Yeah, I have the mpcmdrun,exe red arrow as wellHey @danb ,
How can I report attack chains that do not seem correct to you?
I can't copy them from that screen.
I saw a red arrow involving mpcmdrun,exe, olk.exe and when updating Edge to the latest version.
ok, installed 7.53 beta in VMware win10 Guest VM, then rebooted, I have 20 "listings" under attach chains. I think 1 had a red >> the rest were blue or green, assuming those 2 colors, it is really hard for me to distinguish between those colors unless they are either all blue or all green and my eyes are playing tricks (would not be the first time). I feel more clueless than informed about attack chains... anything more to know, or just relax and let VS/CL run and do its thing, and usually silent here...
update for 7.53 -- walked away from pc for about 20 minutes, now I have a popup
CyberLock.exe - System Error
a new guard page for the stack cannot be create [ok]
all I can do is hit ok, and see that VS/CL is no longer running. fyi av = MS Defender.
CyberLock.exe - System Error
a new guard page for the stack cannot be create [ok]
all I can do is hit ok, and see that VS/CL is no longer running. fyi av = MS Defender.
F
ForgottenSeer 94738
I am fundamentally against these red-green signals because I am color blind and can only distinguish the colors if the colored area is large and the colors are very strong. This is not even that rare among the male population.ok, installed 7.53 beta in VMware win10 Guest VM, then rebooted, I have 20 "listings" under attach chains. I think 1 had a red >> the rest were blue or green, assuming those 2 colors, it is really hard for me to distinguish between those colors unless they are either all blue or all green and my eyes are playing tricks (would not be the first time). I feel more clueless than informed about attack chains... anything more to know, or just relax and let VS/CL run and do its thing, and usually silent here...
You will get the hang of it, it is super easy... there is really not much to do. The important thing is that the attack chains feature will reduce unwanted blocks even further.ok, installed 7.53 beta in VMware win10 Guest VM, then rebooted, I have 20 "listings" under attach chains. I think 1 had a red >> the rest were blue or green, assuming those 2 colors, it is really hard for me to distinguish between those colors unless they are either all blue or all green and my eyes are playing tricks (would not be the first time). I feel more clueless than informed about attack chains... anything more to know, or just relax and let VS/CL run and do its thing, and usually silent here...
Hmmm, that is very odd, it has been perfectly stable on my 2 machines, and one of them is 10 years oldupdate for 7.53 -- walked away from pc for about 20 minutes, now I have a popup
CyberLock.exe - System Error
a new guard page for the stack cannot be create [ok]
all I can do is hit ok, and see that VS/CL is no longer running. fyi av = MS Defender.
I totally understand. There is already a feature where if you right click on any of the chains, it will display the attack chain in order, but does not have the arrows. Please let me know what ideas you might have that will work well for people who are color blind, and if anyone else has any suggestions, please let me know, thank you!I am fundamentally against these red-green signals because I am color blind and can only distinguish the colors if the colored area is large and the colors are very strong. This is not even that rare among the male population.
Maybe something like this?I totally understand. There is already a feature where if you right click on any of the chains, it will display the attack chain in order, but does not have the arrows. Please let me know what ideas you might have that will work well for people who are color blind, and if anyone else has any suggestions, please let me know, thank you!
Green arrows: System Processes -->
Blue arrows: Allow / Benign / Safe --✓-->
Red arrows: Block / Malicious / Not Safe --x-->
This looks great!Hey Guys!
Here is the latest version of CyberLock that has implemented the new Attack Chains feature. Please keep in mind the Attack Chains feature is very new and there are tons of really cool features we will add soon. You will see colored arrows in the Attack Chain list. These are based on rules that we need to finish defining, so the colored arrows do not necessarily represent what actions CyberLock is going to take at each link of the chain. We have written most of the basic rules, but we need to tweak the rules a little and add a few more.
Ultimately, hopefully within a month or so, the colored arrows and rules will match CyberLock’s actions, and then we will be able to fully implement this new feature. It is actually going to be quite easy and fun to do, and we are a lot further along than I thought we would be. And if things go right, we might even be able to do away with the command lines feature altogether, and instead of having a Whitelist, we will have an App list, Web App list, Vulnerable App list, etc. It is difficult to explain, but it is going to be very cool. We will also be able to eliminate most of the remaining unwanted blocks.
Some of the rules for the new attack chain feature are already implemented and auto allowing items that would otherwise be blocked. You can search the developer log for “RuleID: 77” to see these items.
So we have a little more work to do, but I wanted you guys to see what the new attack chains feature is all about, because trust me, there are going to be tons of really cool things we can do with it.
It takes an hour or so to start really building up the attack chain list in CyberLock Settings. In fact, if you restart your computer after installing the new version, it will add a lot of them pretty quick.
This version is completely stable, but it is labeled a beta because there is a super small chance that one of the rules that are already implemented is not correct, so I just want you guys to be aware of this so you can be extra careful until we have the rules where we want them.
You guys will understand pretty quickly how this new feature works, but basically, if you see a red arrow, that means CyberLock should block the attack chain at that point. Like I was saying, the rules are not 100% right yet, so if you see any attack chains that do not seem correct, please let me know and we can fix it. Once they are all fixed, we will fully implement the rules so that CyberLock will block the attack chains at the red arrows. BTW, if you see any white arrows, please let me know, that means that none of the rules were applied to the arrow.
Green arrows: System Processes
Blue arrows: Allow / Benign / Safe
Red arrows: Block / Malicious / Not Safe
CyberLock 7.53 beta
SHA-256: 6edee845df7afdfa09db64e7491bb5ac3378c31bc99ee0f7d96342cb8b6e20d0
View attachment 279407
Have a great weekend!
Dan
I don't have this version installed, but I do have a question just from the screenshot. Can you explain to me how come a chain is already blocked (red arrow) but still spawns the the processes afterwards? Or is it the visualized path of what would happen if the chain is not blocked?
Also, the name "attack chain" seems to me as though they are all malicious, even though many are system processes or benign. Maybe rename to "process chains"?
Yeah, or maybe put a S, A, B, like this...Maybe something like this?
Green arrows: System Processes -->
Blue arrows: Allow / Benign / Safe --✓-->
Red arrows: Block / Malicious / Not Safe --x-->
> S >
> A >
> B >
BTW, I made the arrows bold and it looks quite a bit better, it will be part of the next release. We also need to figure out what to do with the colors for Light Mode... they look pretty good on Dark Mode, but not so great on Light.
Thank you, I appreciate that! Yes, exactly, it is it the visualized path of what would happen if the user allows the blocked part of chain.This looks great!
I don't have this version installed, but I do have a question just from the screenshot. Can you explain to me how come a chain is already blocked (red arrow) but still spawns the the processes afterwards? Or is it the visualized path of what would happen if the chain is not blocked?
Also, the name "attack chain" seems to me as though they are all malicious, even though many are system processes or benign. Maybe rename to "process chains"?
Yeah, I know what you mean, I struggled with the term Attack as well. If we think of something that works better we can certainly change it. Thanks again!
Thanks for the clarification.Thank you, I appreciate that! Yes, exactly, it is it the visualized path of what would happen if the user allows the blocked part of chain.
Yeah, I know what you mean, I struggled with the term Attack as well. If we think of something that works better we can certainly change it. Thanks again!
You may also like...
-
-
App Review Old Norton vs New Norton - Engine Comparatif
- Started by Shadowra
- Replies: 51
-
-
SOpera One R3 arrives with new AI, Google integrations, and more
- Started by Santiago Benavides García
- Replies: 0
