- Jan 24, 2011
- 9,379
Dear VoodooShield fans,
We are thrilled to announce that we are partnering with the VoodooShield team to give away 20 VoodooShield CyberLock Pro license keys, thanks to @danb. Don't miss out on this exciting opportunity to secure your digital devices with the VoodooShield CyberLock Pro! We've added below some of the main features of VoodooShield CyberLock Pro, however, we recommend checking the VoodoShield official website to have a more in-depth view of this great anti-malware product.
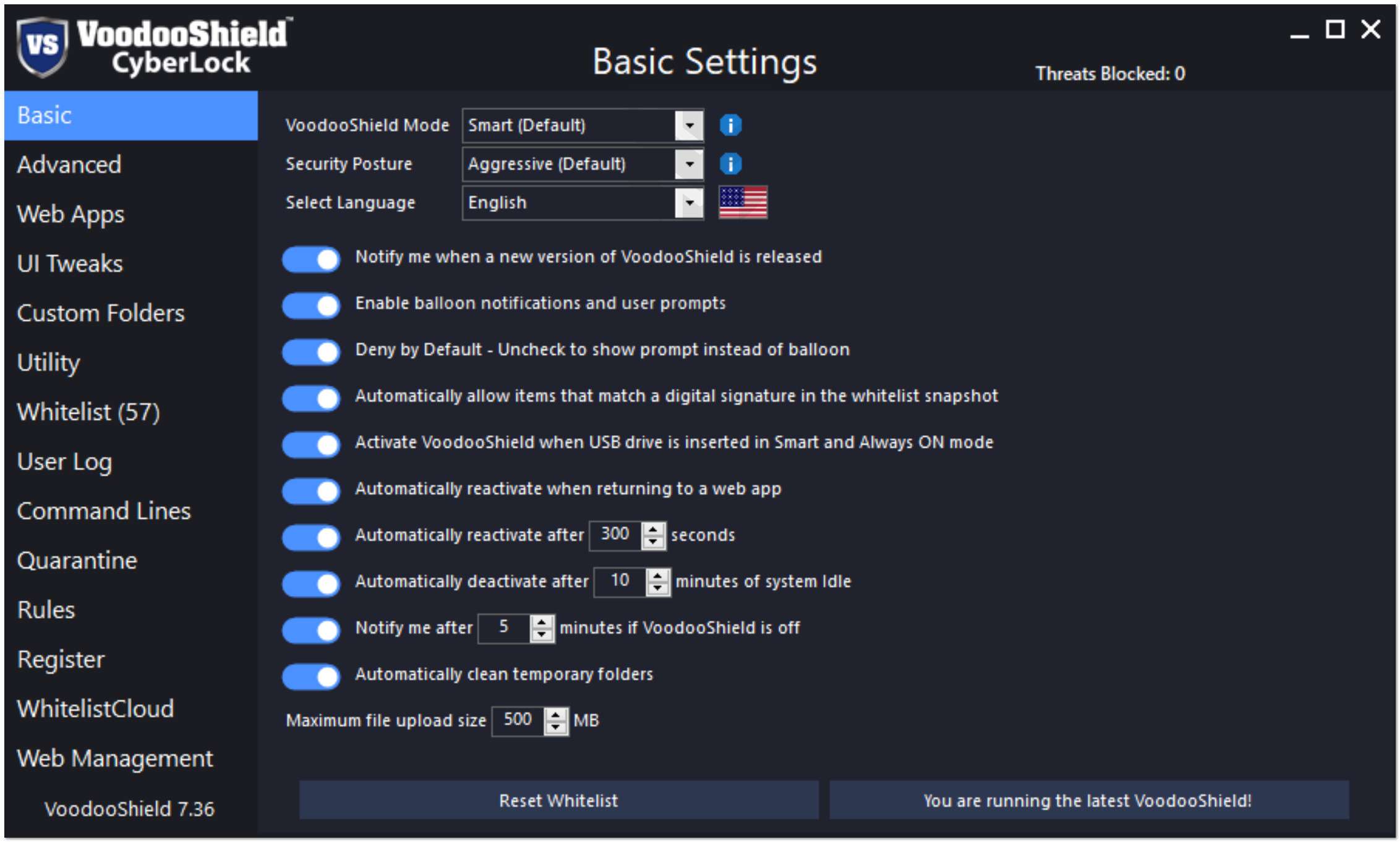
VoodooShield CyberLock Pro is a revolutionary computer protection tool that goes beyond traditional antivirus solutions. Its dynamic security posture adjusts on the fly based on the user's current activity and behavior, offering a tighter and more robust lock than any other product.
In addition, the Antimalware Contextual Engine examines the context of every feature of every possible attack chain event, allowing benign events and blocking potentially malicious ones. This enables VoodooShield to provide top-notch protection against ransomware, script, LOLBins, and fileless malware.
WhitelistCloud, a patent-pending advanced file reputation service, continuously monitors all running processes to ensure only safe items are running at any given time. Instead of scanning for malicious files like traditional antivirus solutions, WhitelistCloud scans for safe files to keep administrators and users aware of the safety of their networks.

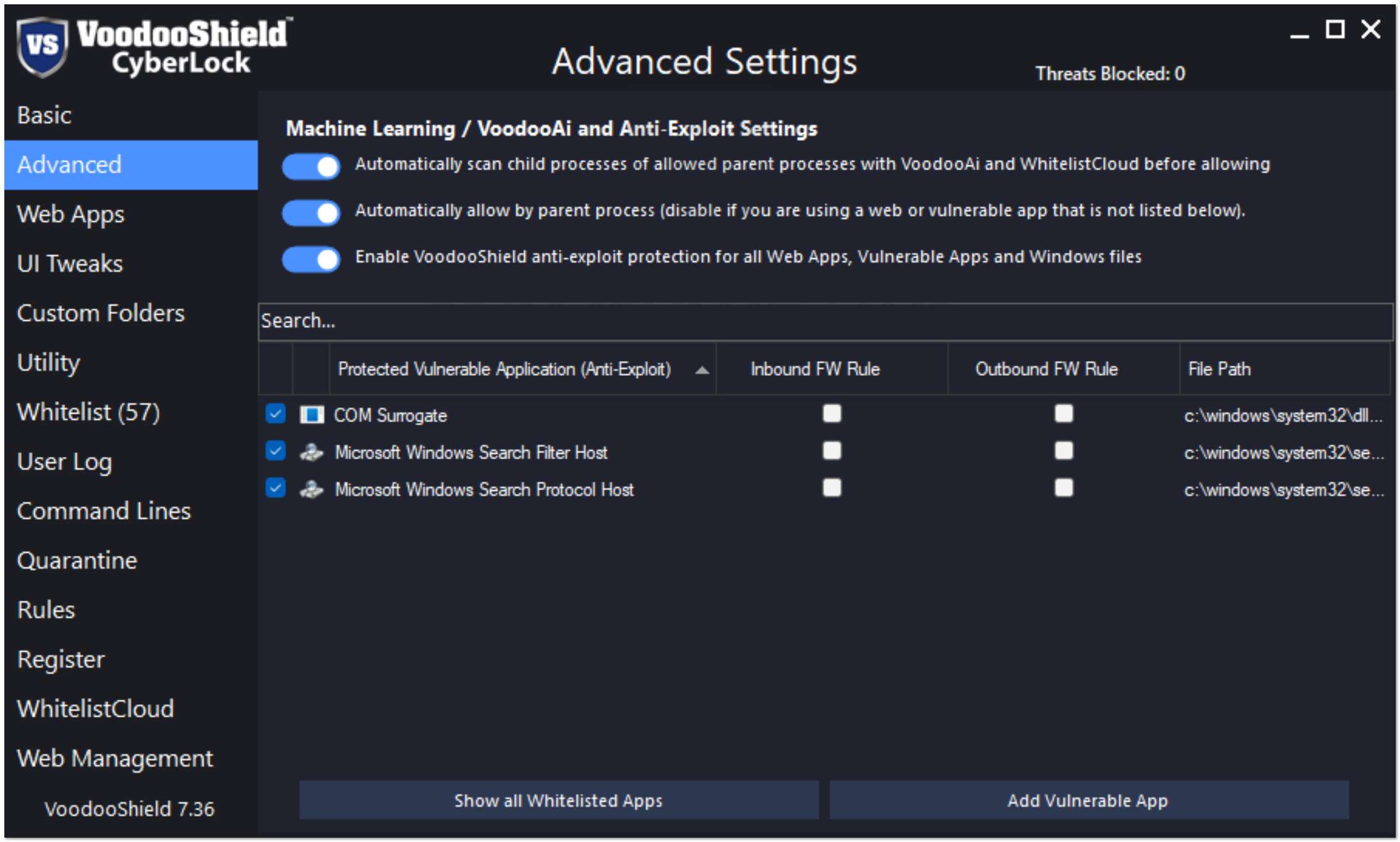
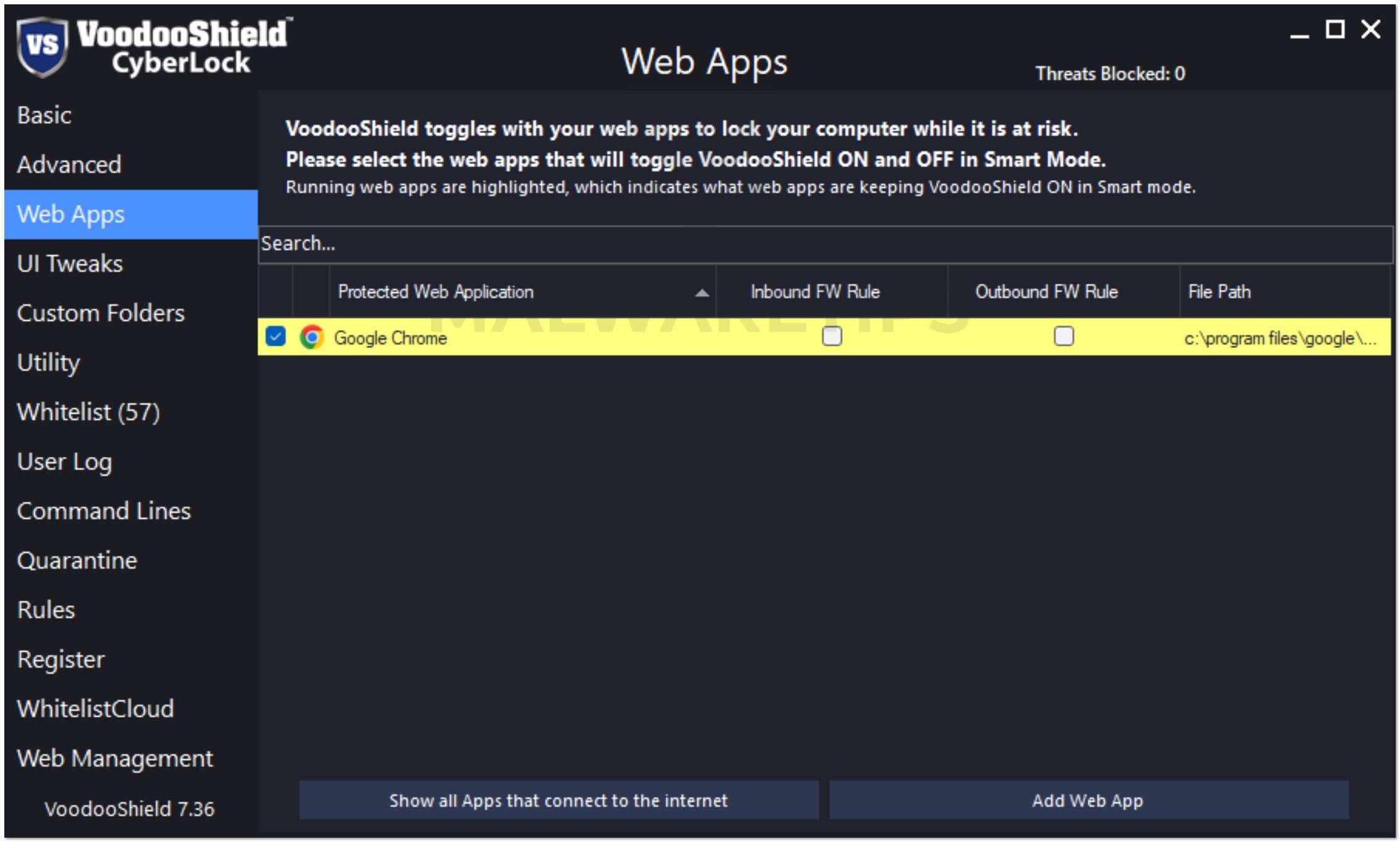
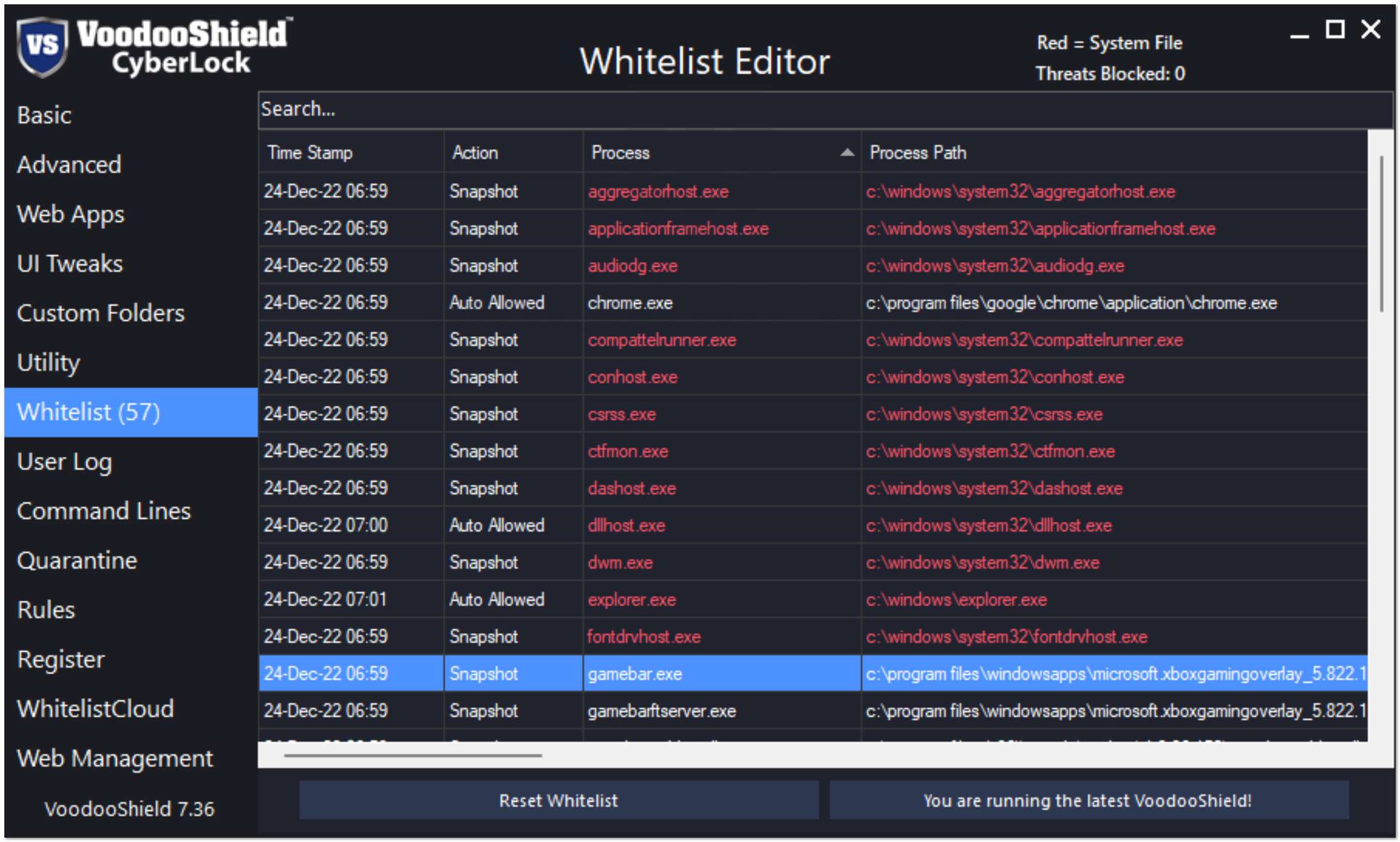
CyberLock is the only patented tangible toggling computer lock in the industry, and it is designed to complement your traditional or next-gen antivirus (including Microsoft Defender). There are other deny-by-default / zero trust products, but only CyberLock functions as an actual computer lock with dynamic levels of protection (dynamic security postures). If it does not toggle, it is not a lock.

OFF Mode (Unlocked): Your computer is unlocked, and VoodooShield is learning which programs to allow so it will not block them once VoodooShield locks your computer. You can also change to this mode if you need to install or allow additional software. Your computer is partially protected in this mode.

ON Mode (Locked): Your computer is locked and you are protected. When VoodooShield automatically toggles to ON Mode, it takes a snapshot of the currently running software, and automatically allows everything in this snapshot. VoodooShield also automatically allows currently installed software and specific critical Windows system files. Any software that was not allowed when VoodooShield was OFF is blocked.
There is only one thing to keep in mind when using VoodooShield...
If VoodooShield blocks something that you would like to run, then allow it after it is automatically scanned.
Otherwise, if VoodooShield blocks something out of the blue, then just ignore it and assume it was a virus or malware.
To enter our VoodooShield CyberLock Pro giveaway:
Here are the basic giveaway rules:
We are thrilled to announce that we are partnering with the VoodooShield team to give away 20 VoodooShield CyberLock Pro license keys, thanks to @danb. Don't miss out on this exciting opportunity to secure your digital devices with the VoodooShield CyberLock Pro! We've added below some of the main features of VoodooShield CyberLock Pro, however, we recommend checking the VoodoShield official website to have a more in-depth view of this great anti-malware product.

What is VoodooShield CyberLock Pro?
VoodooShield CyberLock Pro is a revolutionary computer protection tool that goes beyond traditional antivirus solutions. Its dynamic security posture adjusts on the fly based on the user's current activity and behavior, offering a tighter and more robust lock than any other product.
In addition, the Antimalware Contextual Engine examines the context of every feature of every possible attack chain event, allowing benign events and blocking potentially malicious ones. This enables VoodooShield to provide top-notch protection against ransomware, script, LOLBins, and fileless malware.
WhitelistCloud, a patent-pending advanced file reputation service, continuously monitors all running processes to ensure only safe items are running at any given time. Instead of scanning for malicious files like traditional antivirus solutions, WhitelistCloud scans for safe files to keep administrators and users aware of the safety of their networks.




How VoodooShield CyberLock Pro is different?
CyberLock is the only patented tangible toggling computer lock in the industry, and it is designed to complement your traditional or next-gen antivirus (including Microsoft Defender). There are other deny-by-default / zero trust products, but only CyberLock functions as an actual computer lock with dynamic levels of protection (dynamic security postures). If it does not toggle, it is not a lock.- The Achilles’ heel of all cybersecurity products is that they are only able to offer a single static level of protection, so at any given time their security posture is likely either too aggressive or too relaxed, resulting in false positives and breaches. CyberLock solves this issue by dynamically adjusting its security posture on the fly, based on the end-user’s current activity and behavior. Because of our dynamic security postures feature, CyberLock is able to offer a tighter and more robust lock than is possible with any other product.
- Cybersecurity experts agree that application whitelisting is by far the most effective security mechanism on the market, but no one ever bothered to make this technology user-friendly enough for the masses, until we created CyberLock. Before CyberLock, all application whitelisting products were active full-time, often when it did not make sense to be active, which most users and Administrators found to be annoying and untenable, so they would choose to forgo application whitelisting altogether. Our patented snapshot technology automatically builds the tiny, customized whitelist for the end-user, resulting in the smallest possible whitelist and attack surface in the industry.
- CyberLock does not force the end-user to respond to dangerous affirmative user prompts, which eliminates the possibility the end-user inadvertently allows an unknown item. Instead, CyberLock displays a mini prompt prior to asking the end-user to make a decision on whether to allow a new item or not.
- Through our WhitelistCloud technology, CyberLock scans its tiny, customized whitelist specifically for safe / clean files and automatically creates firewall rules for unknown items. In other words, traditional and next-gen antivirus scans for malware while WhitelistCloud scans for safe / clean files. As a result, Administrators are continually aware that only safe items are running on the endpoints. With traditional and next-gen antivirus, Administrators are somewhat certain that malware is not executing on the endpoints, but with WhitelistCloud, they are essentially certain that only safe items are executing at any moment in time.
- Our unique Antimalware Contextual Engine considers the entire attack chain in the parent / child process creation relationship. Not only does this make CyberLock more secure, our mechanism is flexible so that blacklisting vulnerable items globally is not required. For example, CyberLock is not required to blacklist PowerShell globally in order to protect against PowerShell attacks. In other words, CyberLock considers the entire attack chain so that benign scripts that need to execute are able to do so, while blocking malicious PowerShell attacks.
- CyberLock includes extremely robust ransomware, script, LOLBins and fileless malware protection capabilities.
- LOLBins (Living Off the Land Binaries) have become an increasingly common attack vector in the cybersecurity landscape. Other endpoint protection products typically only protect 5-50 vulnerable process (for example, powershell, cmd, cscript, regsvr32, forfiles, scheduled tasks, bcedit), while CyberLock protects 1,000’s of vulnerable processes system wide, all automatically, all with zero configuration. If a new vulnerable process is discovered, CyberLock automatically updates each endpoint in 4 hours or less.
- CyberLock created the anti-exploit mechanism that many vendors utilize today, but chose not to patent it. CyberLock is also the only deny-by-default product that protects the entire Windows system, as opposed to only protecting the Windows components that are currently being exploited by malware authors. With CyberLock, there is no need to update our mechanism when malware authors discover a new Windows component to exploit, which tends to happen every 3-4 months.
- CyberLock utilizes ML/Ai (VoodooAi) and reputation based file insight (WhitelistCloud) that provides the end-user with file insight so they are able to make an informed decision, while offering an end-user recommendation based on the provided file insight.
- Unlike products that utilize legacy / deprecated Software Restriction Policy (SRP) that operates in user-mode, CyberLock utilizes a modern kernel-mode monolithic blocking mechanism that does not require patches, hacks or tweaks to protect against new or undiscovered vulnerabilities and threats. In addition, unlike other products in its class, CyberLock is refined to the point that it does not require vendor co-management of the Web Management Console.
- CyberLock is highly customizable through its settings, allowing Administrators to fine tune the overall security posture for each end-user.
- CyberLock trains itself automatically and adapts to each endpoint very quickly. Users might notice a few unwanted blocks the first day or two as it automatically customizes itself to their system, but will soon experience just how silent zero trust can be. Some users prefer to put CyberLock on AutoPilot with the Relaxed Security Posture for a couple of days while it is customizing itself to their system, then switch to Smart or Always ON mode and the Aggressive Security Posture.
VOODOOSHIELD WILL TOGGLE BETWEEN ON AND OFF, DEPENDING ON WHETHER YOU ARE AT RISK OR NOT

OFF Mode (Unlocked): Your computer is unlocked, and VoodooShield is learning which programs to allow so it will not block them once VoodooShield locks your computer. You can also change to this mode if you need to install or allow additional software. Your computer is partially protected in this mode.

ON Mode (Locked): Your computer is locked and you are protected. When VoodooShield automatically toggles to ON Mode, it takes a snapshot of the currently running software, and automatically allows everything in this snapshot. VoodooShield also automatically allows currently installed software and specific critical Windows system files. Any software that was not allowed when VoodooShield was OFF is blocked.
There is only one thing to keep in mind when using VoodooShield...
If VoodooShield blocks something that you would like to run, then allow it after it is automatically scanned.
Otherwise, if VoodooShield blocks something out of the blue, then just ignore it and assume it was a virus or malware.
About The VoodooShield Giveaway
To enter our VoodooShield CyberLock Pro giveaway:
- Answer the poll question correctly.
- Like or follow MalwareTips and VoodooShield on Facebook or Twitter.
- Like MalwareTips and VoodooShield on Facebook
- Follow MalwareTips and VoodooShield on Twitter
- (Recommended!) Share the link to the giveaway on Facebook or Twitter -
Don't miss your chance to win a free license key for VoodooShield CyberLock Pro! Enter the @VoodooShield Giveaway at @MalwareTipscom now: https://malwaretips.com/competitions/voodooshield-cyberlock-pro-giveaway-protect-your-computer-with-a-computer-lock.9
- Like MalwareTips and VoodooShield on Facebook
Here are the basic giveaway rules:
- Our forum policy has always been one account per person, anyone detected by our giveaway system entering using multiple accounts will be automatically disqualified.
- Members that are using programs that hide the real IP address are asked to temporarily turn it off when entering this giveaway. If we detect that a member has entered this giveaway from a VPN service the post will be removed, and the member banned from our future giveaways.
- These license keys are for personal use only. By entering this giveaway, you agree not to trade, give away, or resell your product key.
We would like to extend our heartfelt thanks to the VoodooShield team and @danb for providing these free license keys. We know that our readers and members will greatly benefit from this giveaway, and we are grateful for the opportunity to offer it to them.
Thank you, and happy surfing!
Thank you, and happy surfing!



